Communication method, and security policy negotiation method and system for supporting trusted network connect
A technology for security policy and network access, applied in the field of communication, which can solve the problems that policy interaction and communication solutions have not yet been proposed, and the end-to-end secure communication of heterogeneous cross-domain security policy interaction cannot be realized.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
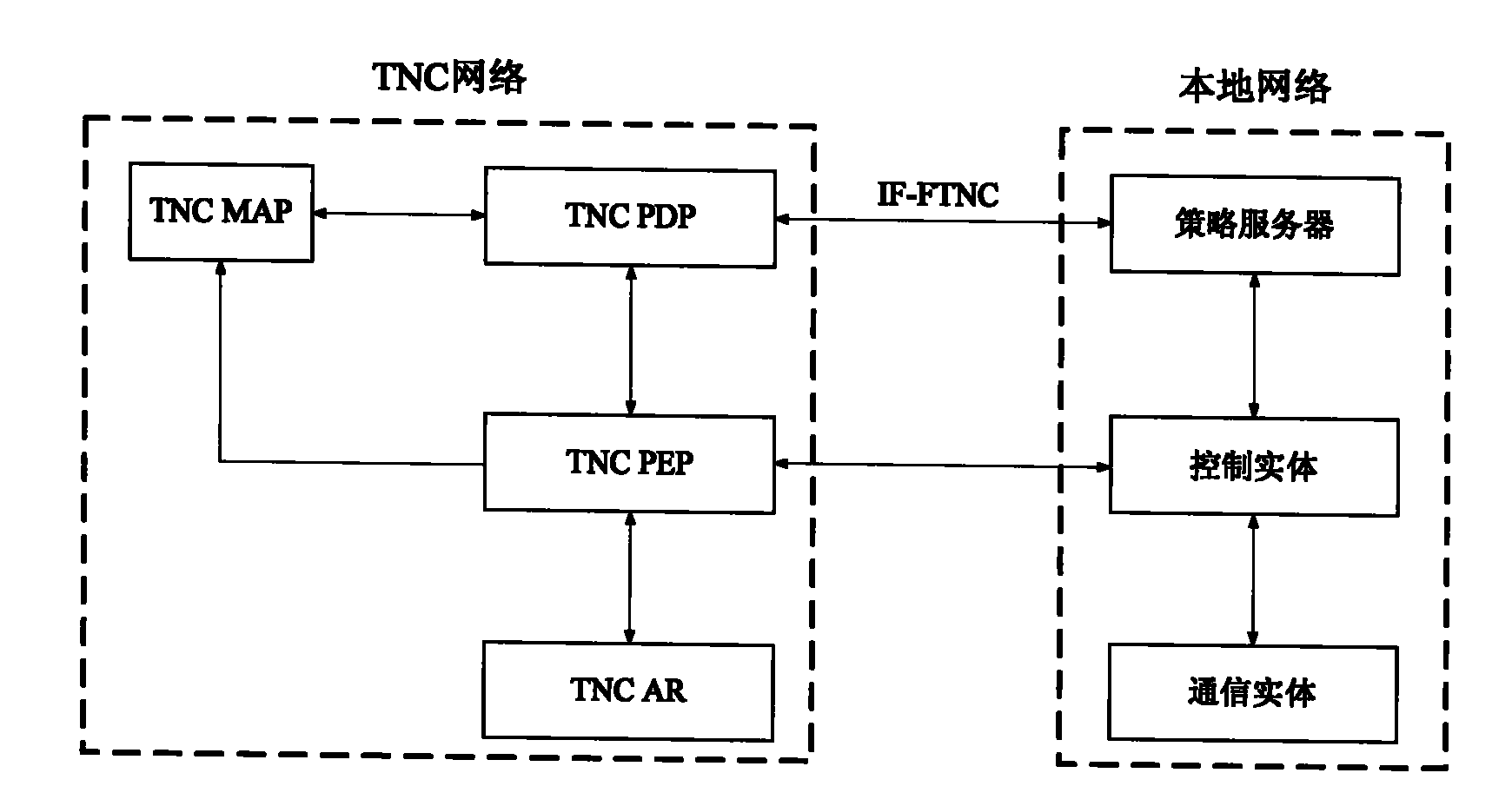
[0037] An object of the present invention is to provide a method for communication between a local network (hereinafter, unless otherwise specified, a local network refers to an untrusted network) and a trusted network, so as to realize cross-domain, heterogeneous end-to-end secure communication, Ensure the security of end-to-end communication.
[0038] To achieve the above object, the present invention adopts the following technical solutions:
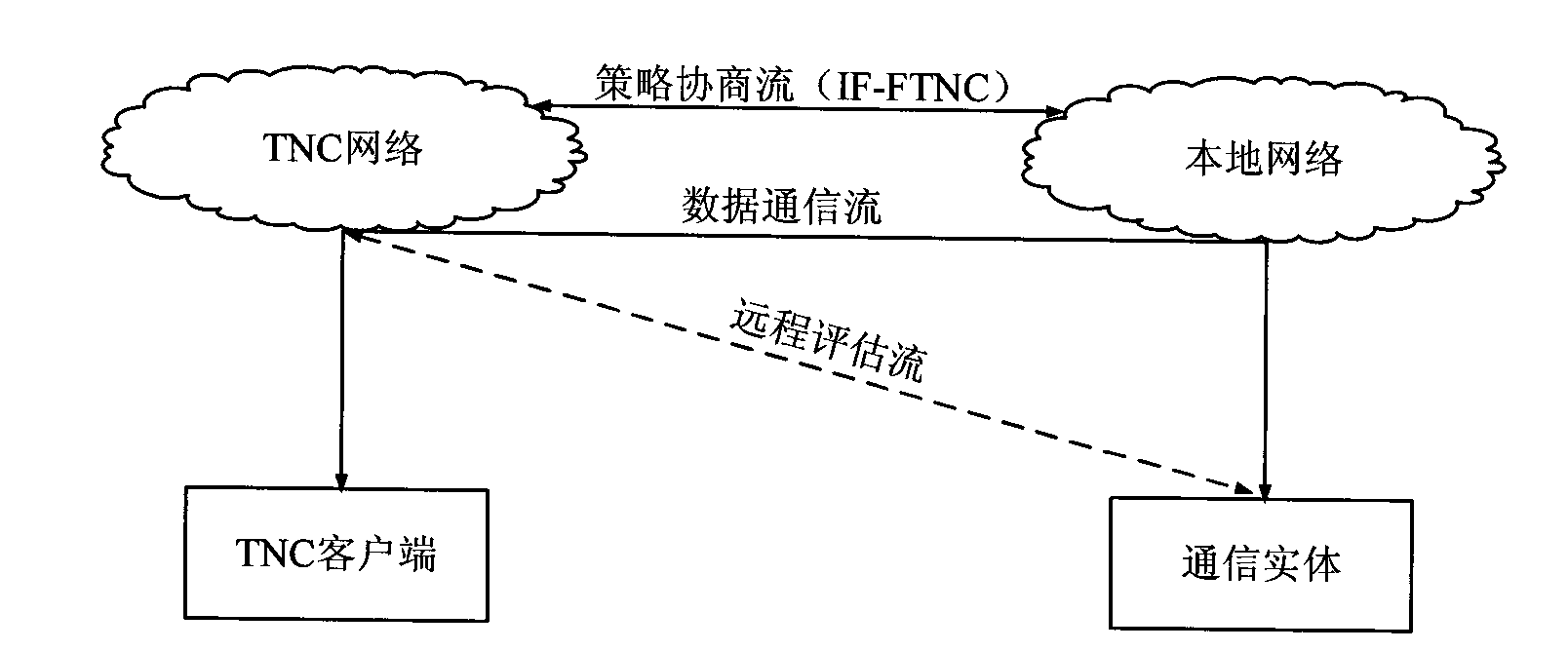
[0039] The local network supports the IF-FTNC (Federated TNC) interface issued by TCG (Trusted Computing Group, Trusted Computing Organization) for cross-domain collaborative trusted network access;
[0040] The policy negotiation between the TNC network and the local network is realized through the IF-FTNC interface.
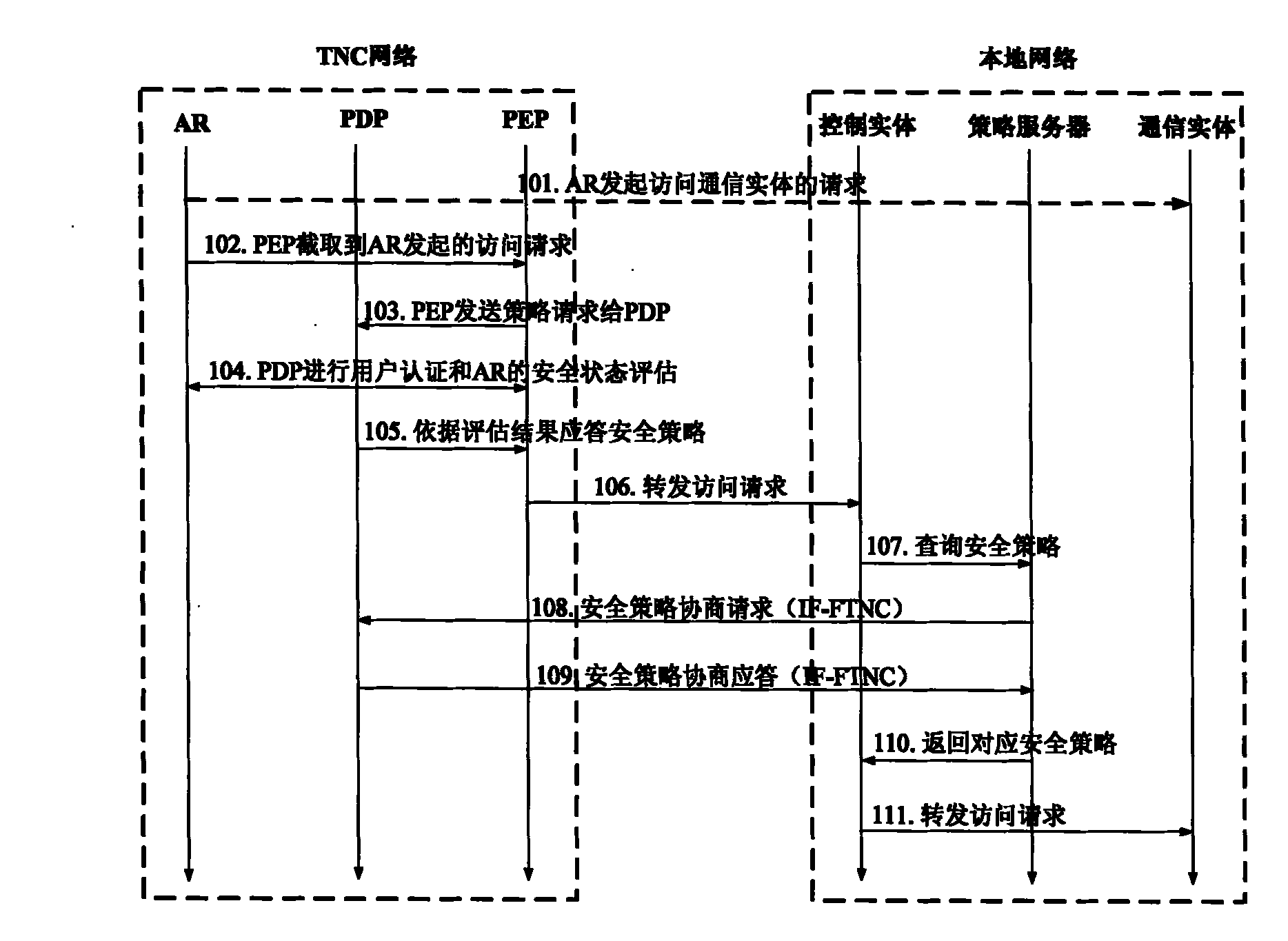
[0041]Wherein, if the local network supports the IF-FTNC interface, the TNC network can directly access the local network, and before performing communication, it first conducts policy negotiation with the local netwo...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com