Combining a mobile device and computer to create a secure personalized environment
A technology of mobile devices and computers, applied in various digital computer combinations, platform integrity maintenance, instruments, etc., can solve problems such as endangering security, vulnerability of enterprise networks, and management.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
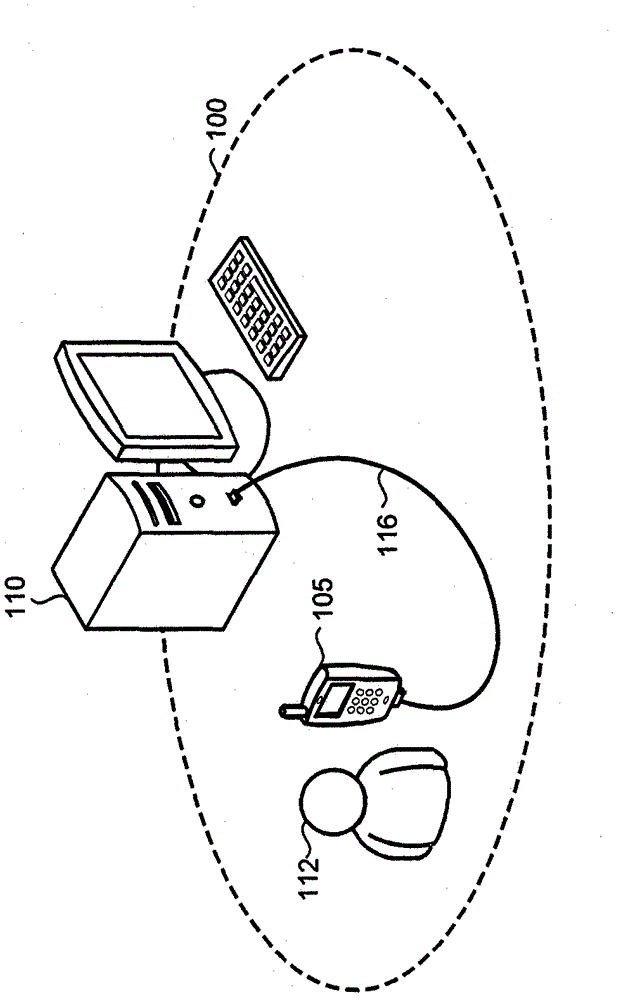
[0015] figure 1 An exemplary computing environment 100 including a mobile device 105 and a PC 110 is shown. The mobile device 105 may be selected from one of a number of different devices including, for example, mobile phones, smart phones, pocket PCs, PDAs (Personal Digital Assistants), such as MP3 (Moving Picture Experts Group, MPEG-1, audio Layer 3) Players Personal media players, digital cameras, digital video recorders, handheld gaming devices, devices that incorporate one or more of the above functions, etc. Typically, mobile device 105 will be compact and lightweight, enabling it to be conveniently carried by user 112 from one place to another. An on-board power source, such as a battery in the mobile device 105, is also typically provided to further increase the usefulness and functionality of the device.
[0016] PC 110 represents a computing platform such as a desktop PC, laptop PC, workstation, and the like. In this particular example, computing environment 100 a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com