Real-time protection method and device
A real-time protection and rule technology, applied in the computer field, can solve problems such as hidden security risks and poor user experience, achieve good scalability, reduce the number of choices, and improve the experience.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
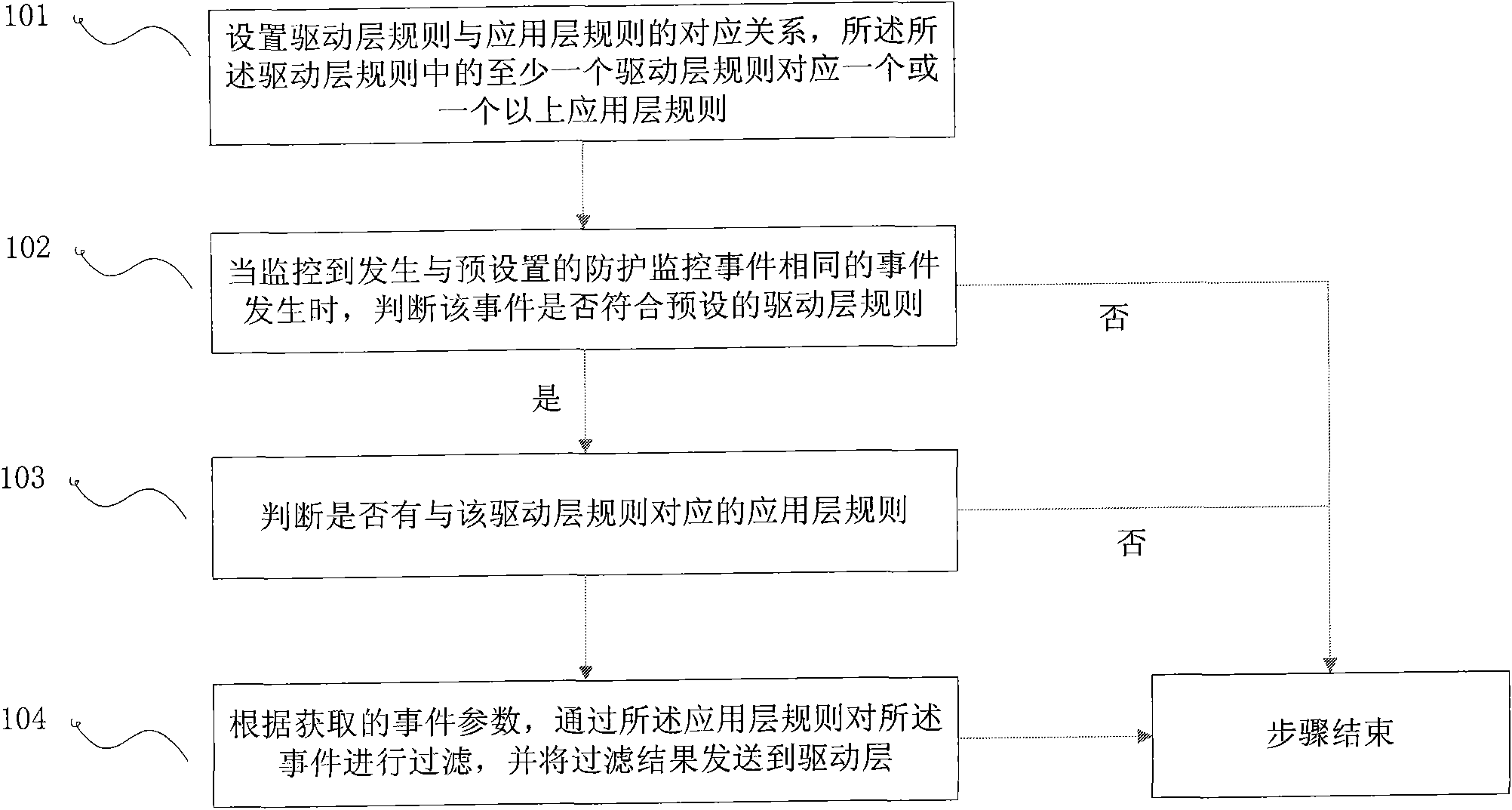
[0048] Step 101, setting the corresponding relationship between driver layer rules and application layer rules, at least one driver layer rule in the driver layer rules corresponds to one or more application layer rules;
[0049] Step 102, when monitoring the occurrence of the same event as the preset protection monitoring event, judge whether the event complies with the preset driver layer rules; if not, the step ends;
[0050] Step 103, judging whether there is an application layer rule corresponding to the driver layer rule; if not, the step ends;
[0051] Step 104 , according to the acquired event parameters, filter the event through the application layer rules, and send the filtering result to the driver layer.
[0052]The embodiment of the present invention proposes a real-time protection method, which can filter events by adopting a secondary detection method when a predetermined event occurs. The embodiments of the present invention can filter through preset applicati...
Embodiment 2
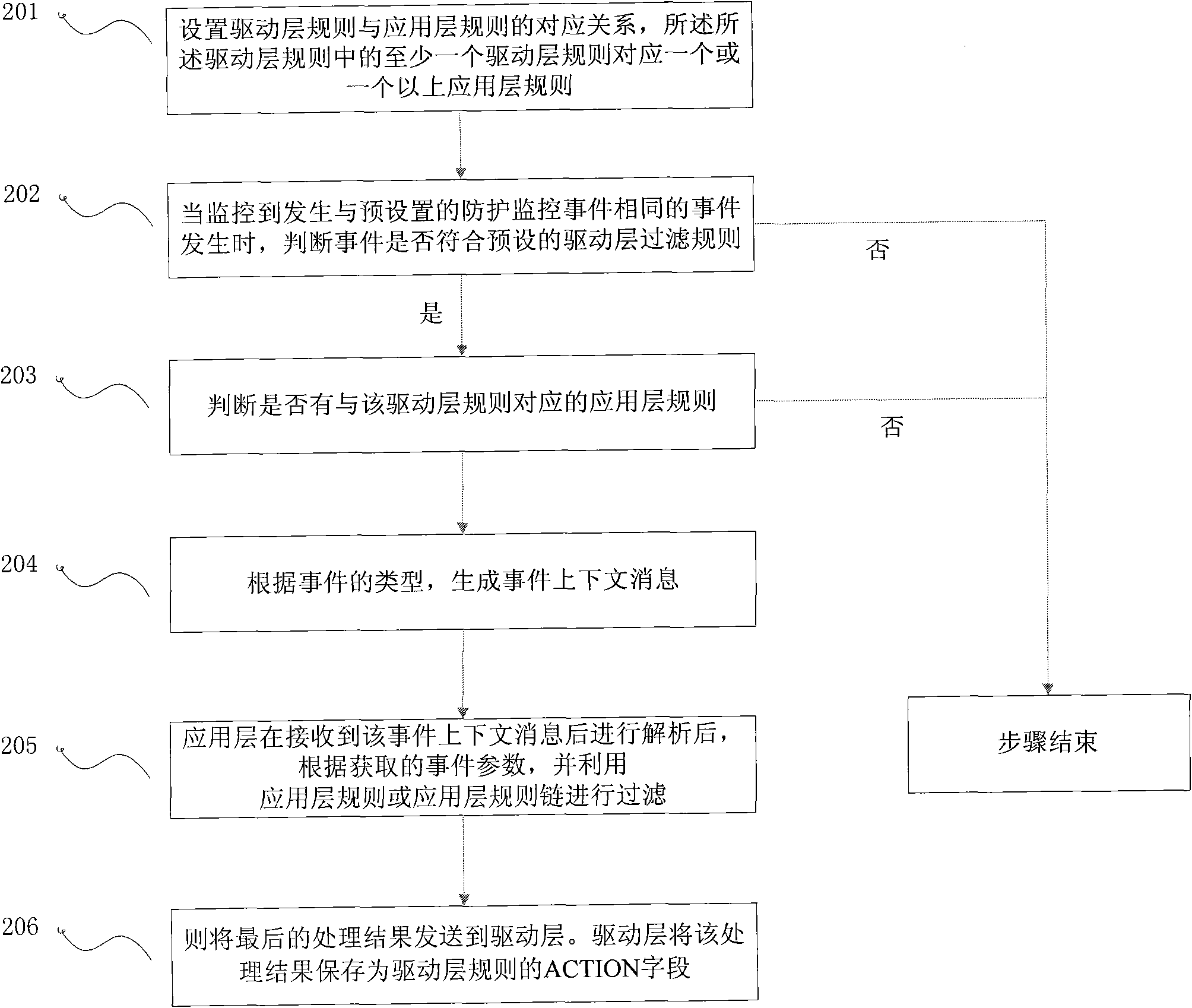
[0054] The second embodiment of the present invention proposes a real-time protection method, the process of which is as follows figure 2 shown, including:
[0055] Step 201: Set a corresponding relationship between driver layer rules and application layer rules, at least one driver layer rule in the driver layer rules corresponds to one or more application layer rules.
[0056] In the prior art, driver layer rules correspond to driver layer monitoring events. Existing driver layer monitoring events can be divided into four types: registry protection (RP) events, file protection (FP) events, program protection (AP) events, and network protection (NP) events. And each event type can correspond to one or more driver layer rules respectively. When corresponding to multiple driver layer rules, the multiple driver layer rules can be set as a driver layer rule chain.
[0057] Each driver layer rule can describe the monitoring points that need to be monitored by means of four fie...
Embodiment 3
[0078] The third embodiment of the present invention proposes a real-time protection device, the structure of which is as follows image 3 shown, including:
[0079] Correspondence setting module 1, configured to set the correspondence between driver layer rules and application layer rules, at least one driver layer rule in the driver layer rules corresponds to one or more application layer rules;
[0080]The event monitoring module 2 is used for monitoring events. When the same event as the preset protection monitoring event is monitored, it is judged whether the event complies with the preset driver layer rules; and whether there is a corresponding driver layer rule application layer rules;
[0081] The application layer filtering module 3 is configured to filter the event through the application layer rules according to the acquired event parameters, and send the filtering result to the driver layer.
[0082] The embodiment of the present invention proposes a real-time pr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com