Device, terminal and method for preventing illegal updating of terminal
A terminal and equipment technology, applied in the field of mobile terminal software version upgrade, can solve the problems of destroying the terminal and end market harm, and achieve the effect of protecting vital interests and protecting the terminal market
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
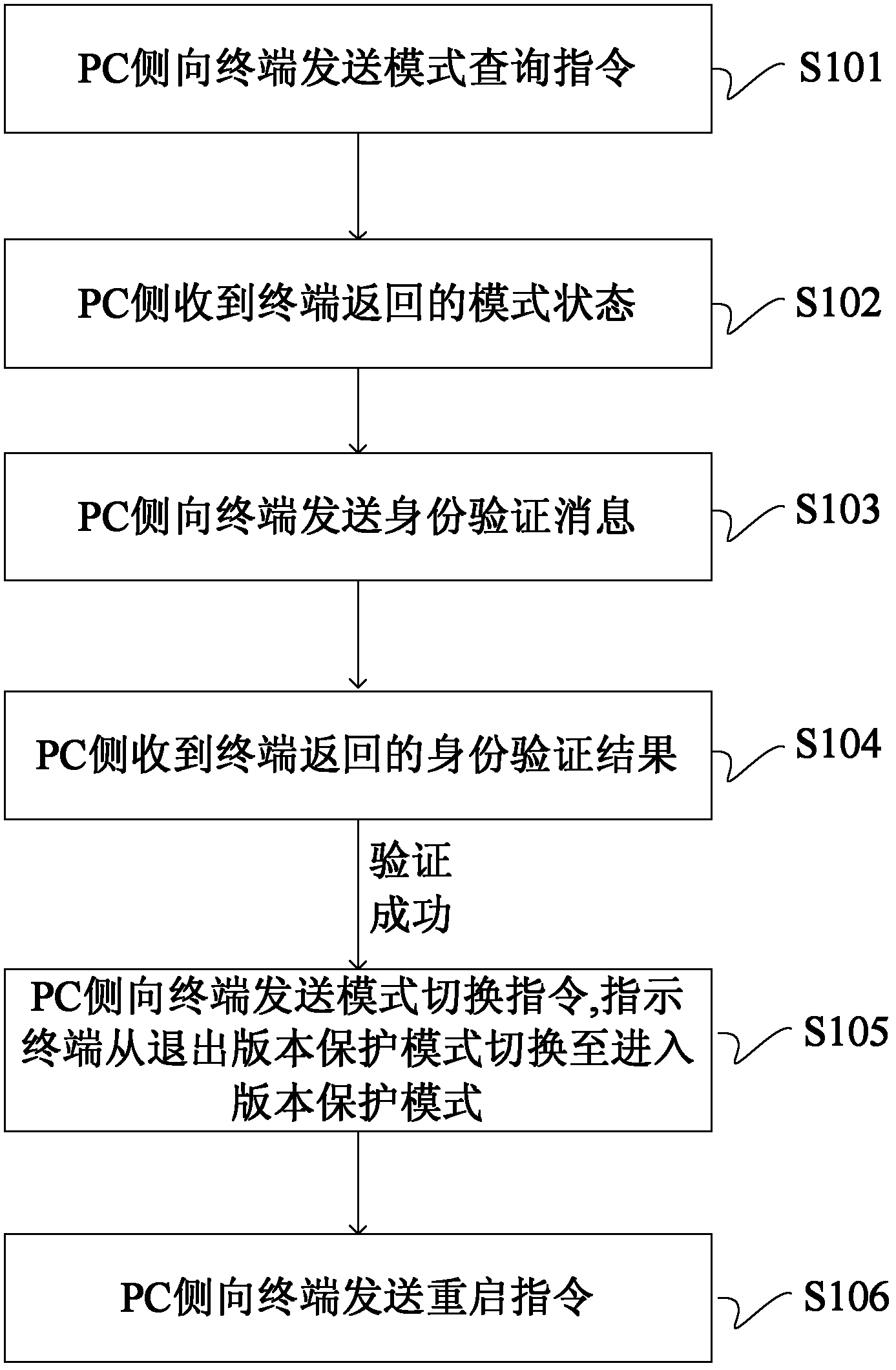
[0049] Such as figure 1 Shown is a flow chart of the device side entering the version protection mode according to the embodiment of the present invention.
[0050] S101: The PC sends a mode query command to the terminal, and the command may be a diag command for mode query; the modes to be queried include entering a version protection mode and exiting a version protection mode.
[0051] S102: The PC side receives the mode status returned by the terminal. If the terminal has entered the version protection mode, exit and return successfully; if the terminal has not entered the version protection mode, execute S103.
[0052] S103: the PC sends an identity verification message to the terminal;
[0053] S104: The PC receives the identity verification result returned by the terminal. If the verification fails, it exits and returns failure; if the identity verification succeeds, it executes S105.
[0054] S105: The PC sends a mode switching instruction to the terminal, instructing...
Embodiment 2
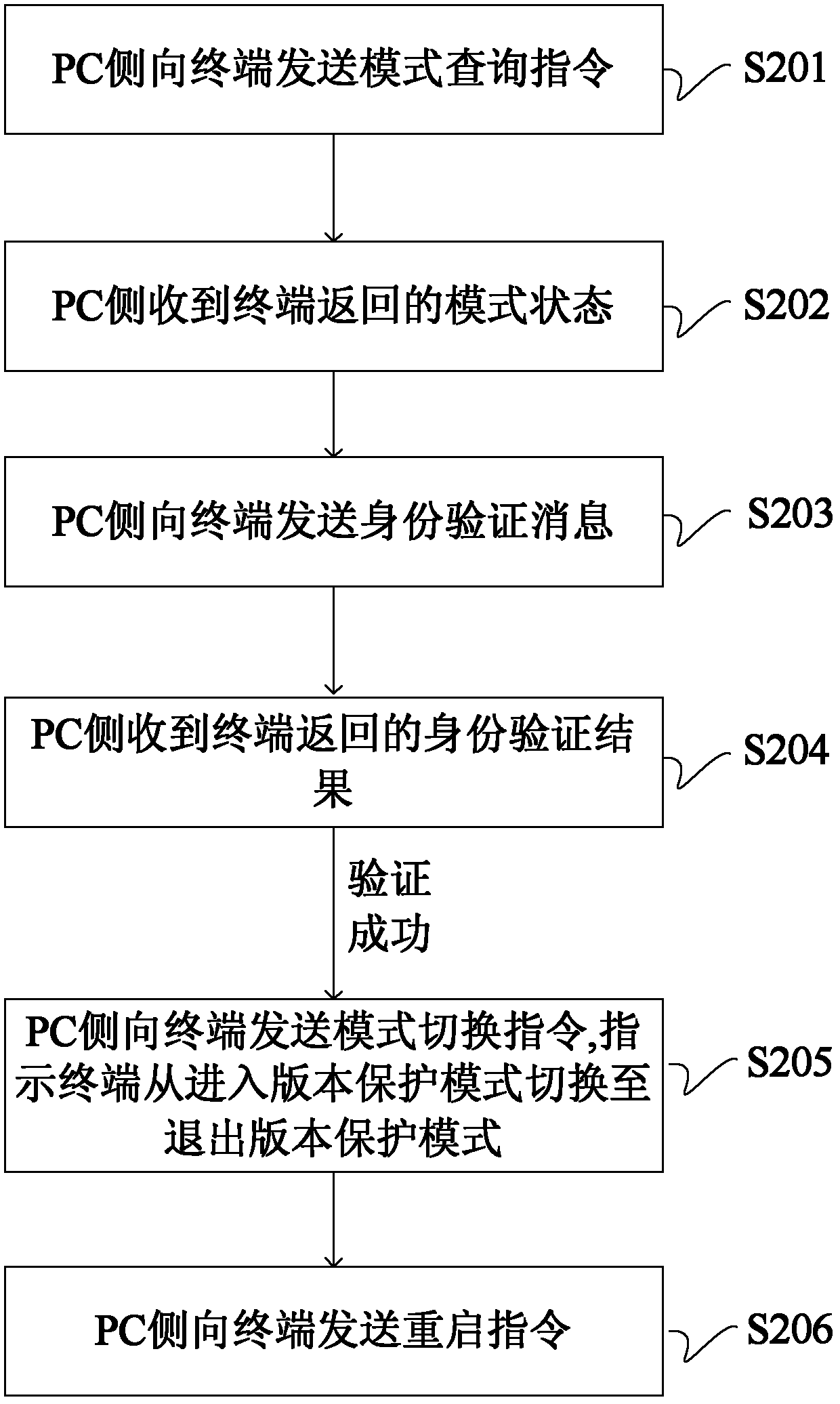
[0057] Such as figure 2 Shown is a flow chart of exiting the version protection mode according to the embodiment of the present invention.
[0058] S201: The PC sends a mode query command to the terminal, and the command may be a diag command for mode query; the modes to be queried include entering a version protection mode and exiting a version protection mode.
[0059]S202: The PC side receives the mode status returned by the terminal. If the current status of the terminal is that it has exited the version protection mode, exit and return successfully; if the terminal has not exited the version protection mode, execute S203.
[0060] S203: the PC sends an identity verification message to the terminal;
[0061] S204: The PC receives the identity verification result returned by the terminal. If the identity verification fails, it exits and returns failure; if the identity verification succeeds, it executes S205.
[0062] S205: The PC sends a mode switching instruction to th...
Embodiment 3
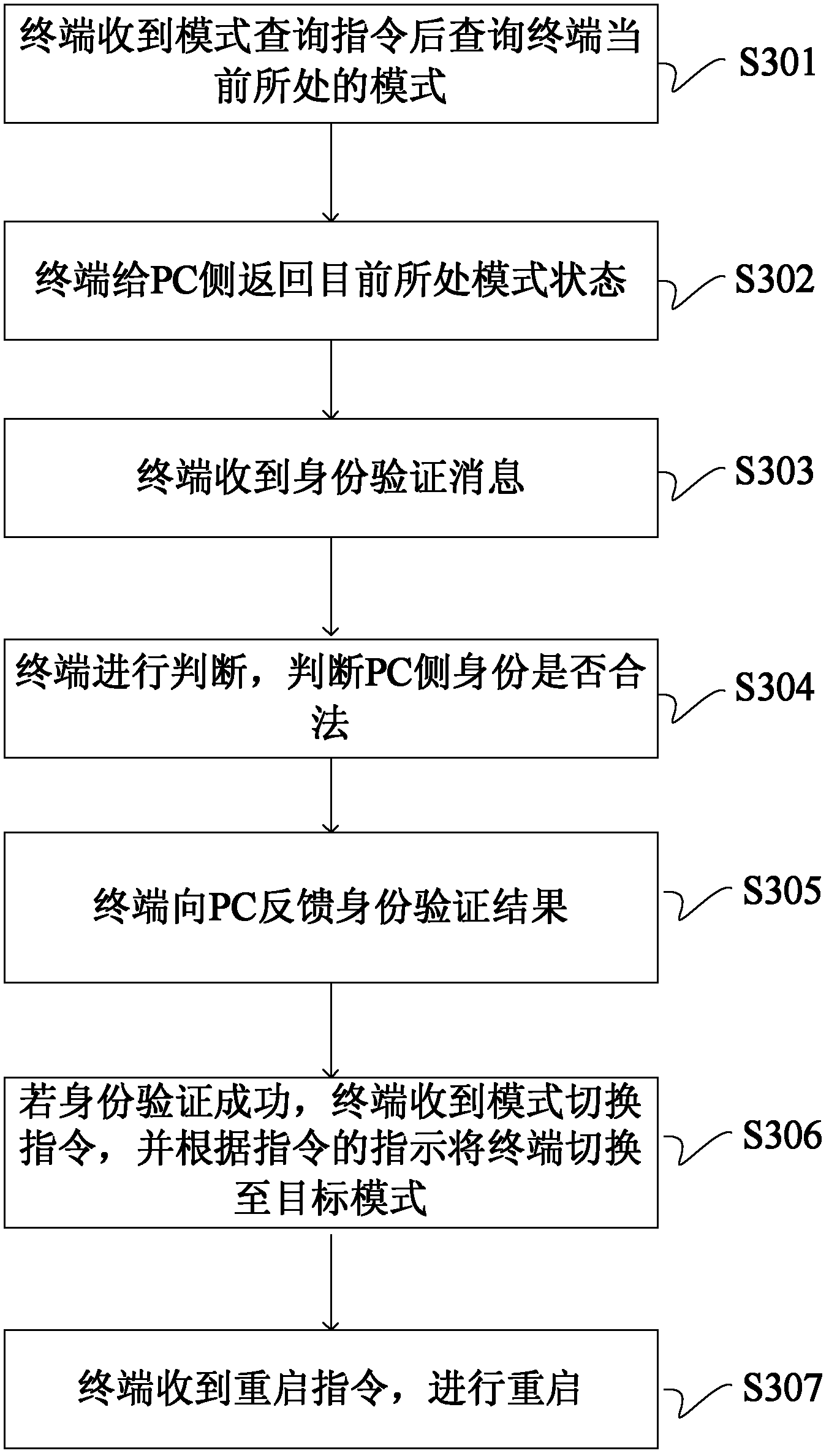
[0065] Such as image 3 Shown is a flowchart of the process of entering or exiting the version protection mode at the terminal side according to the embodiment of the present invention.
[0066] S301: After receiving the mode query instruction, the terminal queries the current mode of the terminal, and the current mode includes entering version protection or exiting version protection;
[0067] S302: The terminal returns the current mode state to the PC side.
[0068] If the current mode status needs to be switched, the following steps are required;
[0069] S303: The terminal receives an identity verification message.
[0070] S304: The terminal judges whether the identity of the PC side is legal.
[0071] S305: The terminal feeds back an identity verification result to the PC; the result includes identity verification success and identity verification failure.
[0072] S306: If the identity verification is successful, the terminal receives a mode switching instruction, a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com