Application file system access
A file system and application access technology, applied in special data processing applications, user interface execution, instruments, etc., can solve problems such as defects and changes in reliability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0017] overview
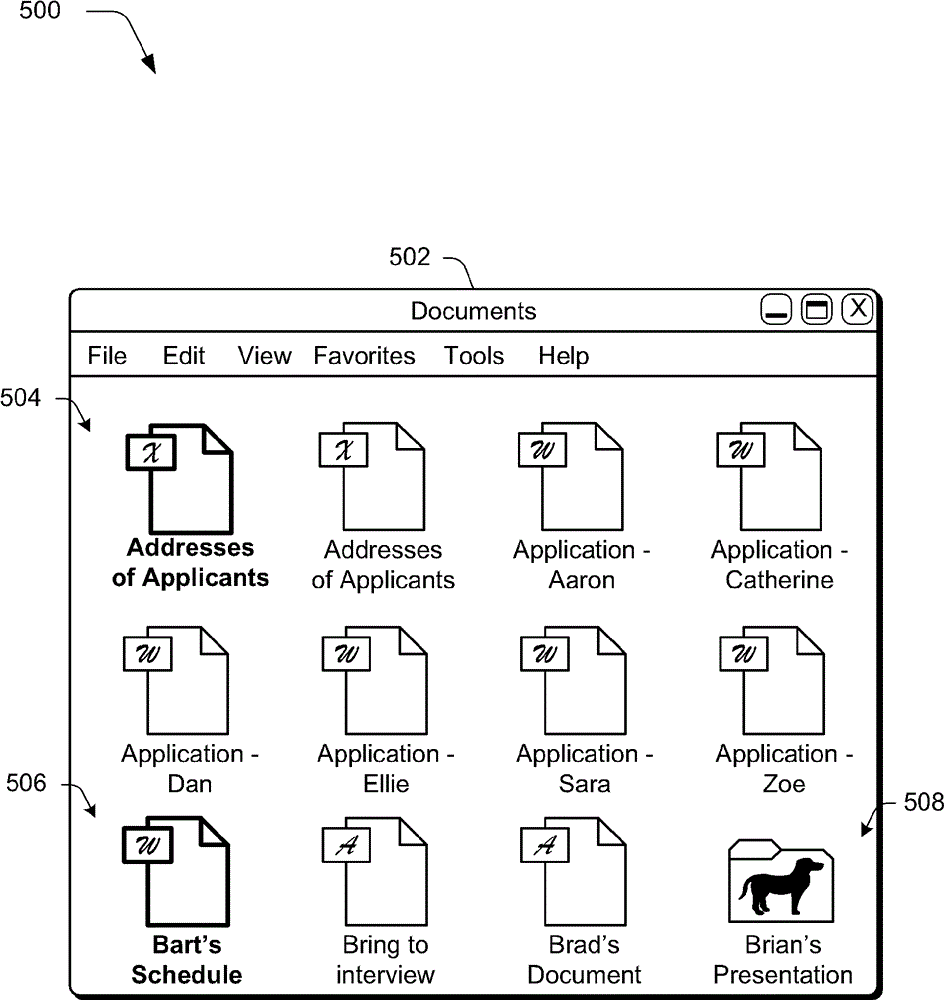
[0018] With the proliferation of application developers, users of computing devices are exposed to an increasing number of applications. However, the trustworthiness of these applications varies widely, as do the developers who write them. Thus, traditional file systems that have historically permitted unimpeded access may expose computing devices to flawed and even malicious applications.
[0019] Application file system access techniques are described. In an implementation, the proxy module is utilized to manage application access to the file system to access local files, networked computers, and / or peripherals communicatively coupled to the computing device. For example, an agent module may be configured to facilitate the output of a user interface. Via the user interface, the user can authenticate the application's request for access to the file system. In this way, the proxy module can help users manage the access to be granted to applications execut...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com