An email trust service
A technology of e-mail, e-mail message, applied in the field of e-mail trust service
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
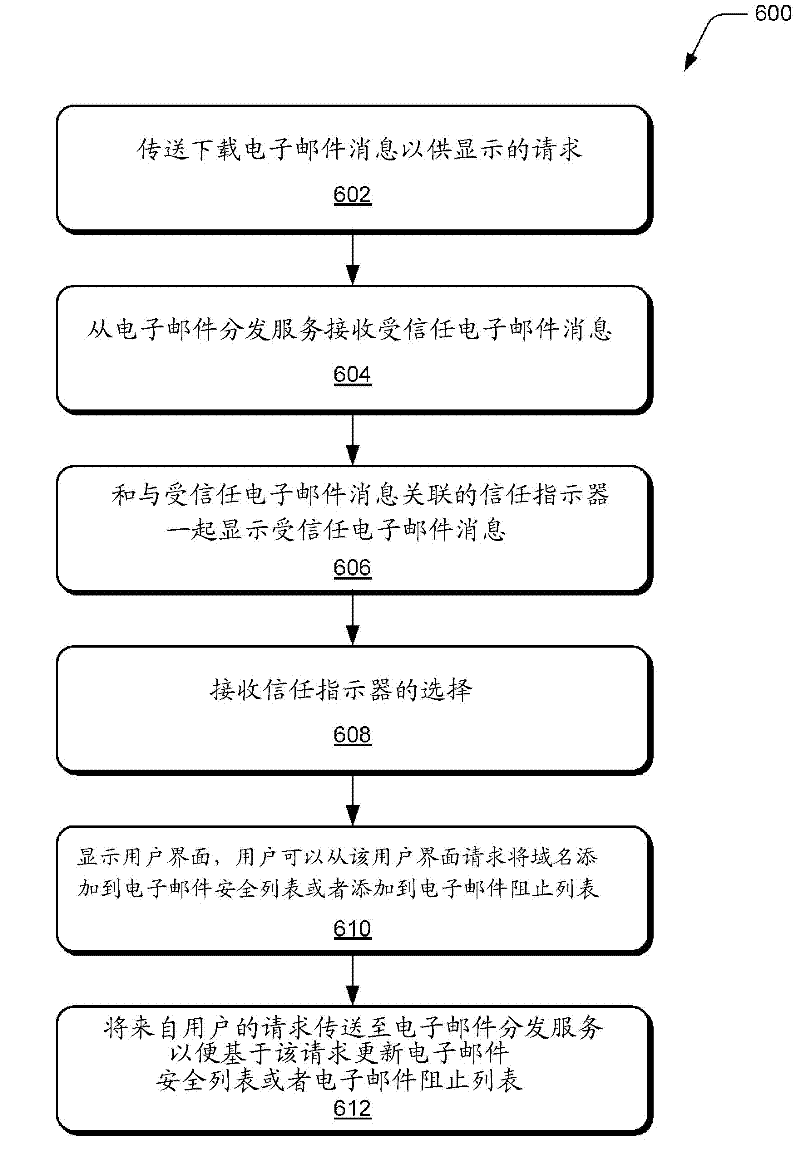
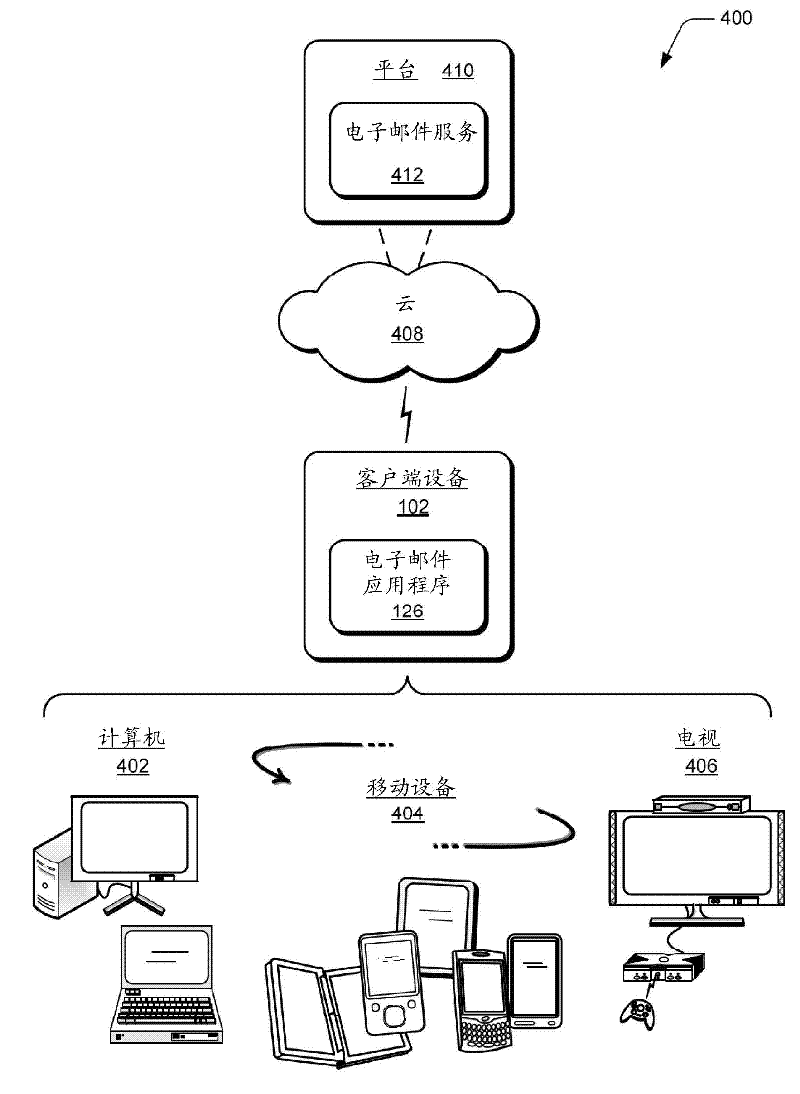
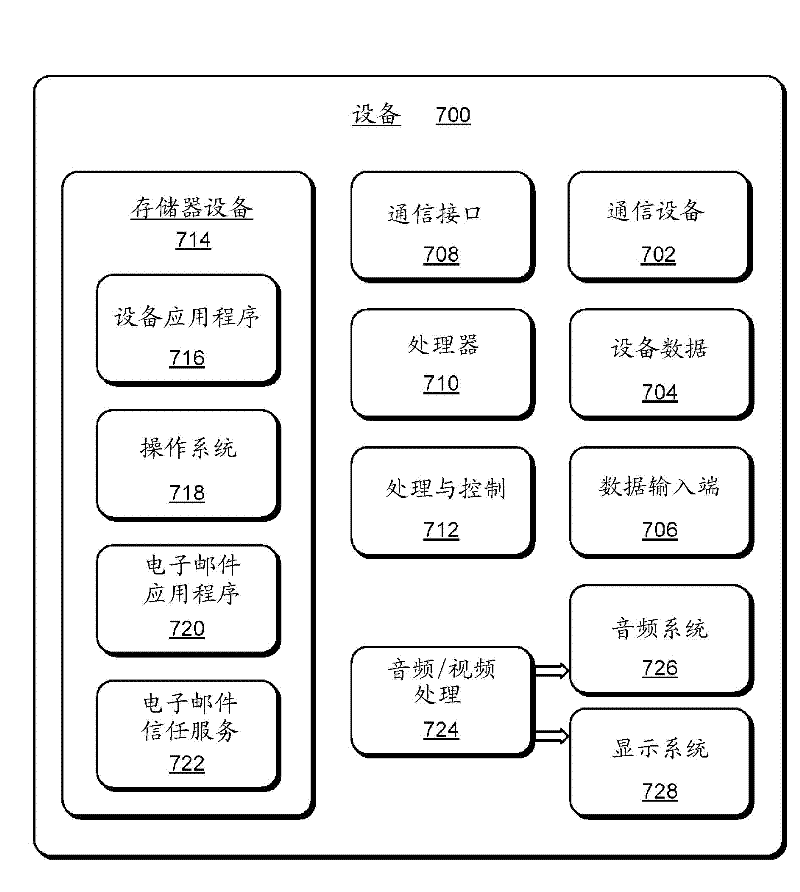
[0013] An email trust service is described. In an embodiment, an email message is received at an email distribution service for distribution to client devices corresponding to recipients of the email message. Authentication techniques may be applied to email messages to verify that the email message was received from an authorized domain as specified in the sender address field of the email message. The authentication technology may include a domain key identified mail (DKIM) authentication technology or a SenderID (sender ID) authentication technology. Authenticating an email message using DKIM or SenderID can be used to determine whether the email message was received from a sender authorized to send email messages from authorized domains.
[0014] Additionally, it can be determined whether an extended validation certificate is associated with an authorized domain in order to determine whether the authorized domain can be trusted. An Extended Validation certificate is a st...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com