Communication method for improving security of radio frequency identification system
The technology of a radio frequency identification system and communication method is applied in the field of communication to improve the security of the radio frequency identification system, and can solve problems such as low security of the key system, long time required for accessing keys, and large number of keys, etc., to achieve The effect of saving key storage resources, occupying less resources, and fast access speed
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
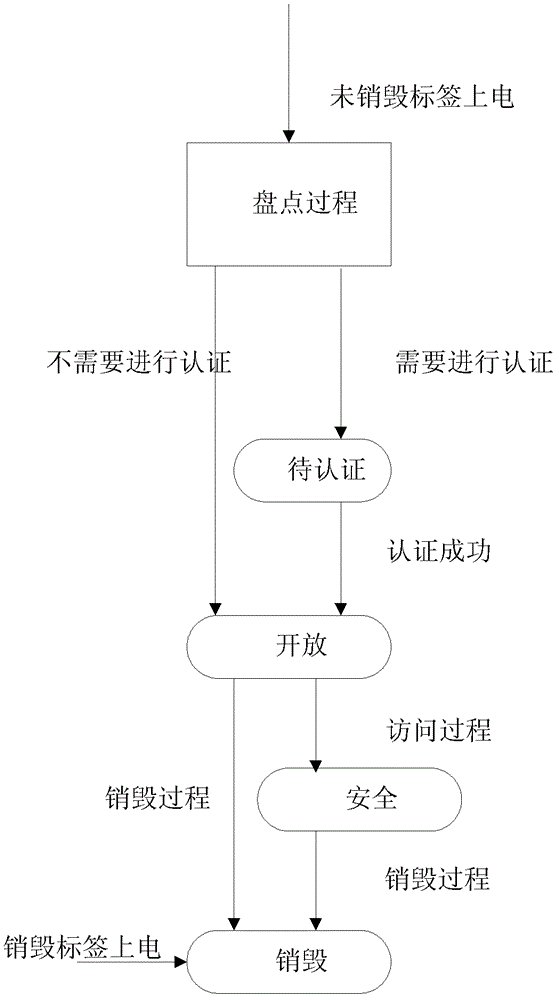
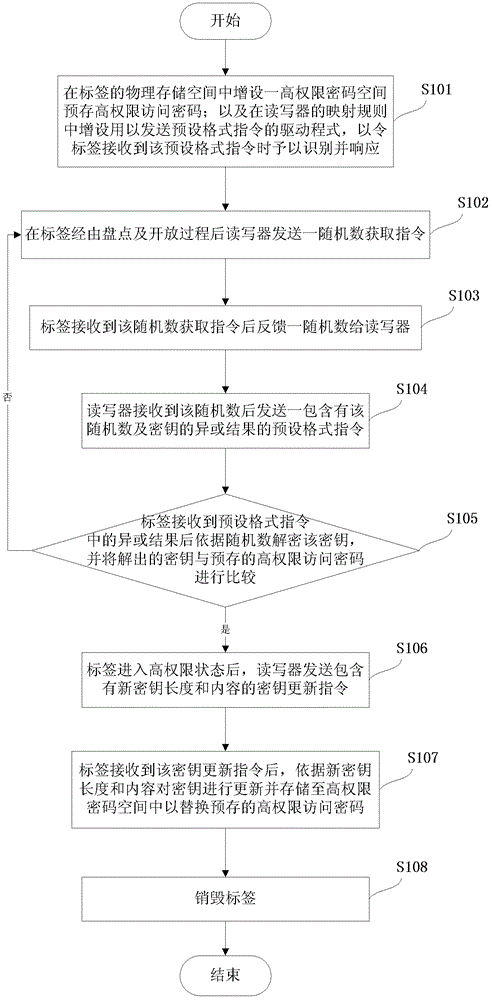
[0031] The invention provides a communication method for improving the security of a radio frequency identification system, the radio frequency identification system at least includes a tag, a reader-writer communicating with the tag, and an application for controlling the reader-writer and processing the data information of the tag system (not shown). In this example, see Figure 2 to Figure 5 , the communication method for improving the security of the radio frequency identification system of the present invention adds a high-authority access process and a high-authority state, and the tag in the open state can enter the high-authority state through the high-authority access process. In this state, the reader The content and length of the key can be modified to improve the security of the system, such as image 3 As shown, the communication method for improving the security of the radio frequency identification system at least includes the following steps:
[0032] Such as...
Embodiment 2
[0043] In this example, see Figure 6 , showing that the label can only enter the high-privilege state through the high-privilege access process in the secure state, that is, the label in the open (open) state must enter the secure (secure) state through an effective access process, and can pass the high-privilege state only in the secure state The access process enters a high-privilege state. As shown in the figure, compared with Embodiment 1, the communication method for improving the security of the radio frequency identification system of the present invention adds a tag. The access key needs to be detected through the access process, so Figure 6 The high-privilege state is the most secure. In the specific implementation process, in the step S102, after the tag has gone through the inventory and opening process, it needs to go through a security access process to enter the security state, and then the reader sends a random number Obtain instructions and request to ente...
Embodiment 3
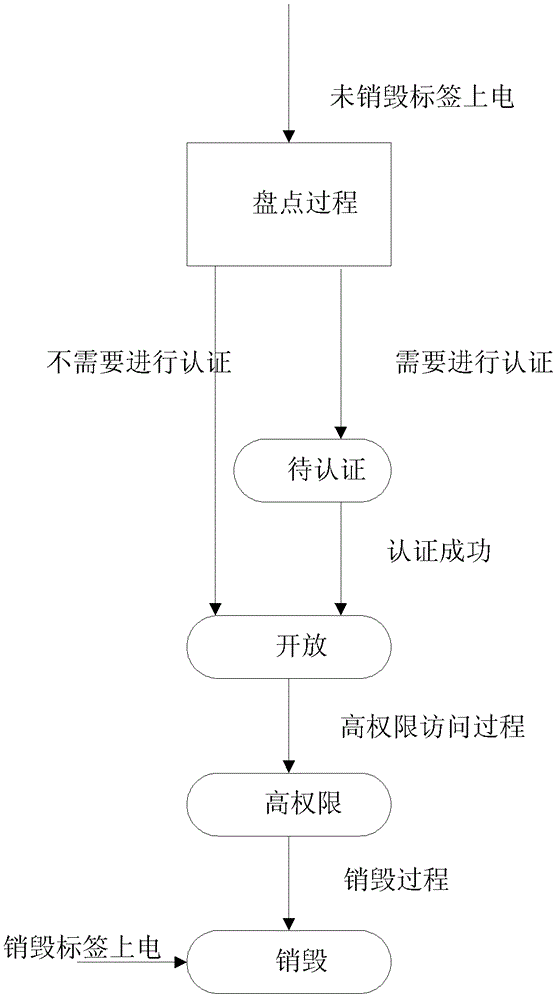
[0045] In this example, see Figure 7 , showing that tags in the open and secure states can enter the high-privilege state through the more secure high-privilege access process. In the state of high-privilege access, the reader can modify the content and length of the key. Thereby improving the security of the system. In other words, in the open (open) or secure (secure) state, the reader and tag go through a high-privilege access process to make the tag enter a high-privilege state. In this state, the reader can modify the relevant information by sending a key. The method of instruction modifies the content and length of the key, and after the tag returns the message of successful modification, the new key replaces the old key and is stored in the corresponding key storage location. It should be noted that the process of the tag requesting to enter the high-privilege access is the same as that described in Embodiment 1 and Embodiment 2, and will not be repeated here.
[004...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com