Peer-to-peer (P2P) network access control method
An access control and peer-to-peer network technology, applied in network-related fields, can solve problems such as the lack of a perfect network member access control mechanism, the abolition of network members, and failure to perfect it.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0081]The present invention will be described in further detail below in conjunction with the accompanying drawings and specific embodiments.
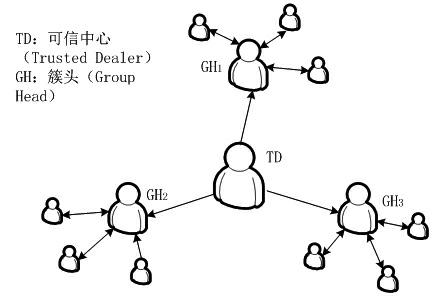
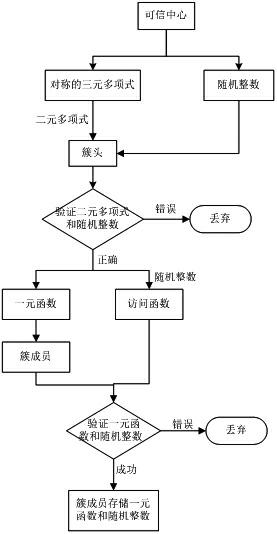
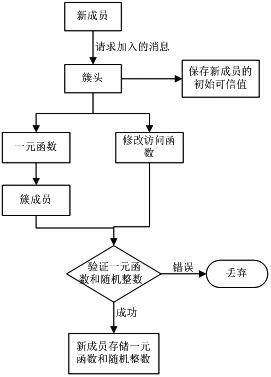
[0082] Refer to attached figure 1 . The invention is an access control mechanism in the peer-to-peer network realized based on two access control strategies of authentication and credible value evaluation. Its architecture adopts the cluster-based distributed structure, which is suitable for the distributed network environment based on the cluster structure. When the system is created, it consists of several clusters, and new members must join one of the clusters when they join the peer-to-peer network. The number of clusters can be determined according to the actual situation. In this embodiment, three clusters are used, and the cluster identifiers are G1, G2, and G3 respectively. Before the system formally accepts new members, necessary initialization is required. The system requires the existence of a trusted dealer (TD for sho...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com