Method and device for detecting intrusion
An intrusion detection and data flow technology, applied in the field of information management, can solve the problems of untraceable attack behaviors of unknown types, and inability to detect misuse detection type IDS.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
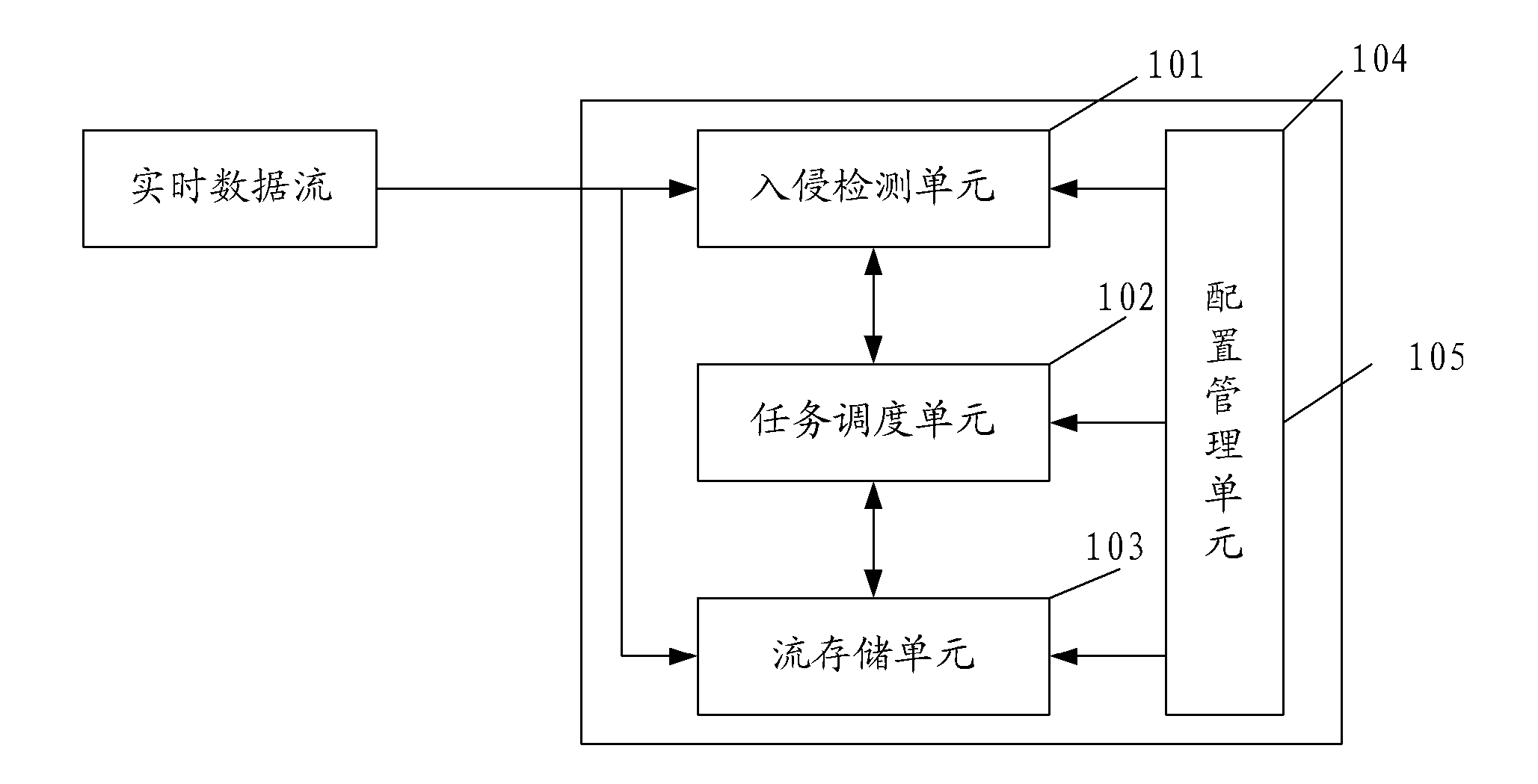
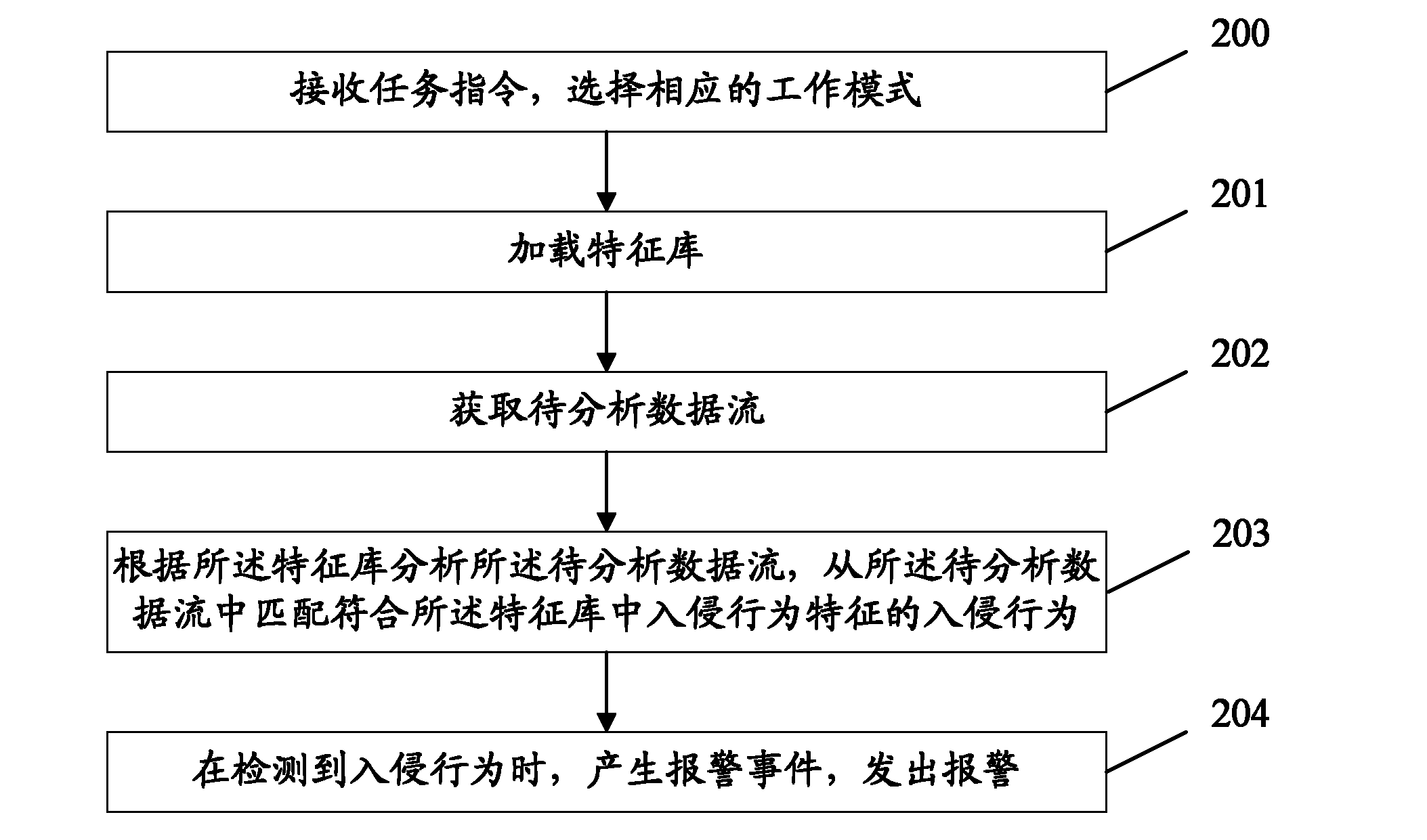
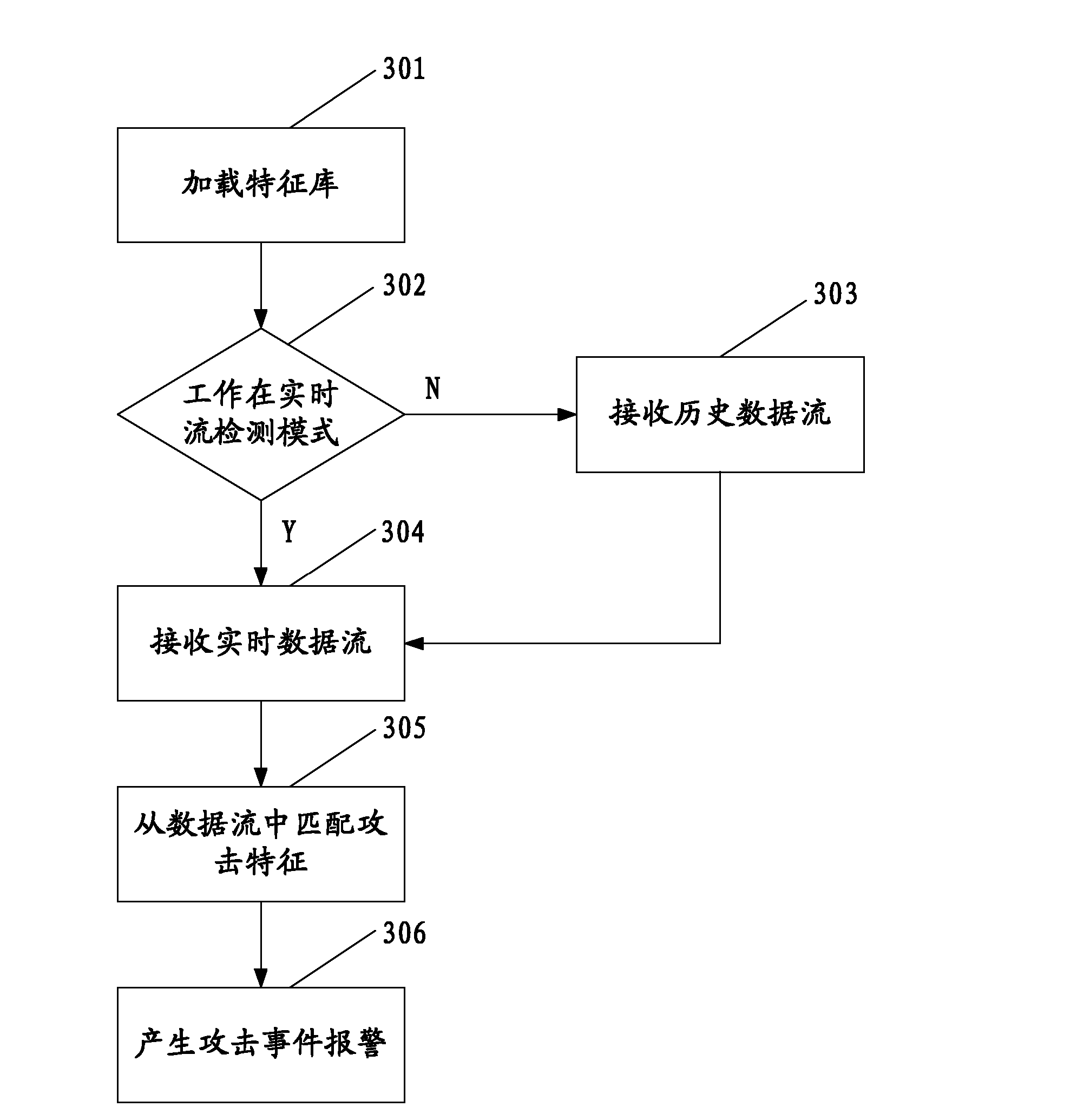
Image
Examples
Embodiment Construction
[0041] The current misuse detection IDS has the following deficiencies:
[0042] 1. Unable to detect unknown types of attacks. Because the misuse detection IDS always detects based on the characteristics of known attacks, when a new attack method appears, before it is mastered by IDS vendors, IDS vendors will not be able to extract the characteristics of this type of attack and analyze the IDS The feature database of the product is upgraded, so that the IDS product does not have the ability to detect this new type of attack, so even if the host is found to be attacked, it cannot detect the source and type of the attack.
[0043] 2. Unable to trace the underreported attacks. Since the misuse detection IDS always detects attacks based on the traffic captured in real time, it is impossible to trace back the attack behaviors that are not detected in real time. There are many reasons for false negatives. For example, it may be because the real-time traffic exceeds the processing ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com