DDoS (distributed denial of service) defending method based on Turing test
A technology of Turing test and graphics, applied in the field of DDoS defense
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0021] The preferred embodiments of the present invention will be specifically described below in conjunction with the accompanying drawings.
[0022] The present embodiment is a kind of DDoS defense method based on the Turing test, comprising the following steps:
[0023] 1. Intercept user request data
[0024] In this embodiment, the NDIS (Network Driver Interface Specification, ie, network driver interface specification) middle layer driver intercepts all request data entering the server, and decides whether to release the data.
[0025] Using the NDIS middle layer driver to intercept user request data does not depend on the specific network implementation scheme, and can realize cross-platform and cross-language user request data interception and processing.
[0026] 2. User identity determination
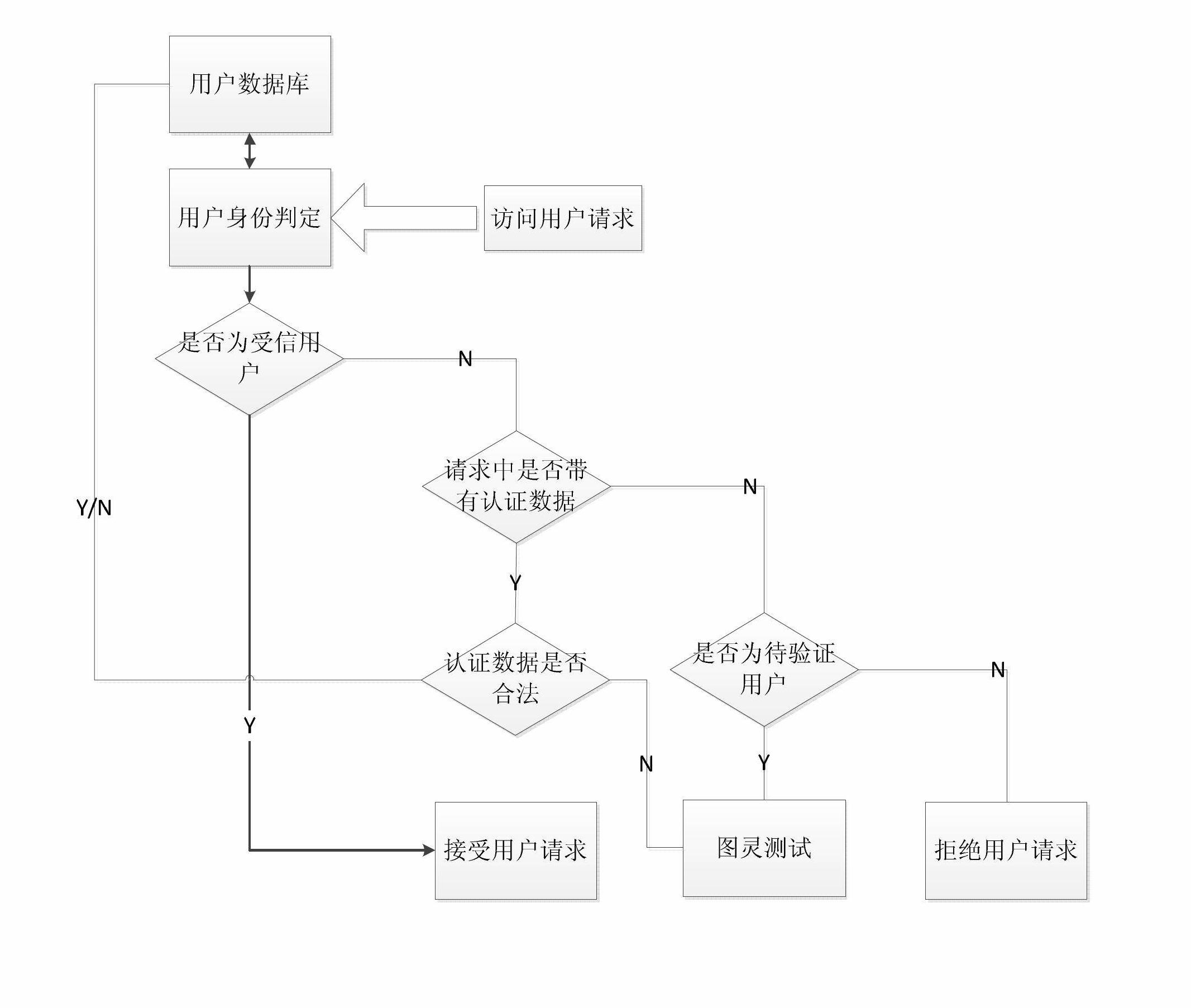
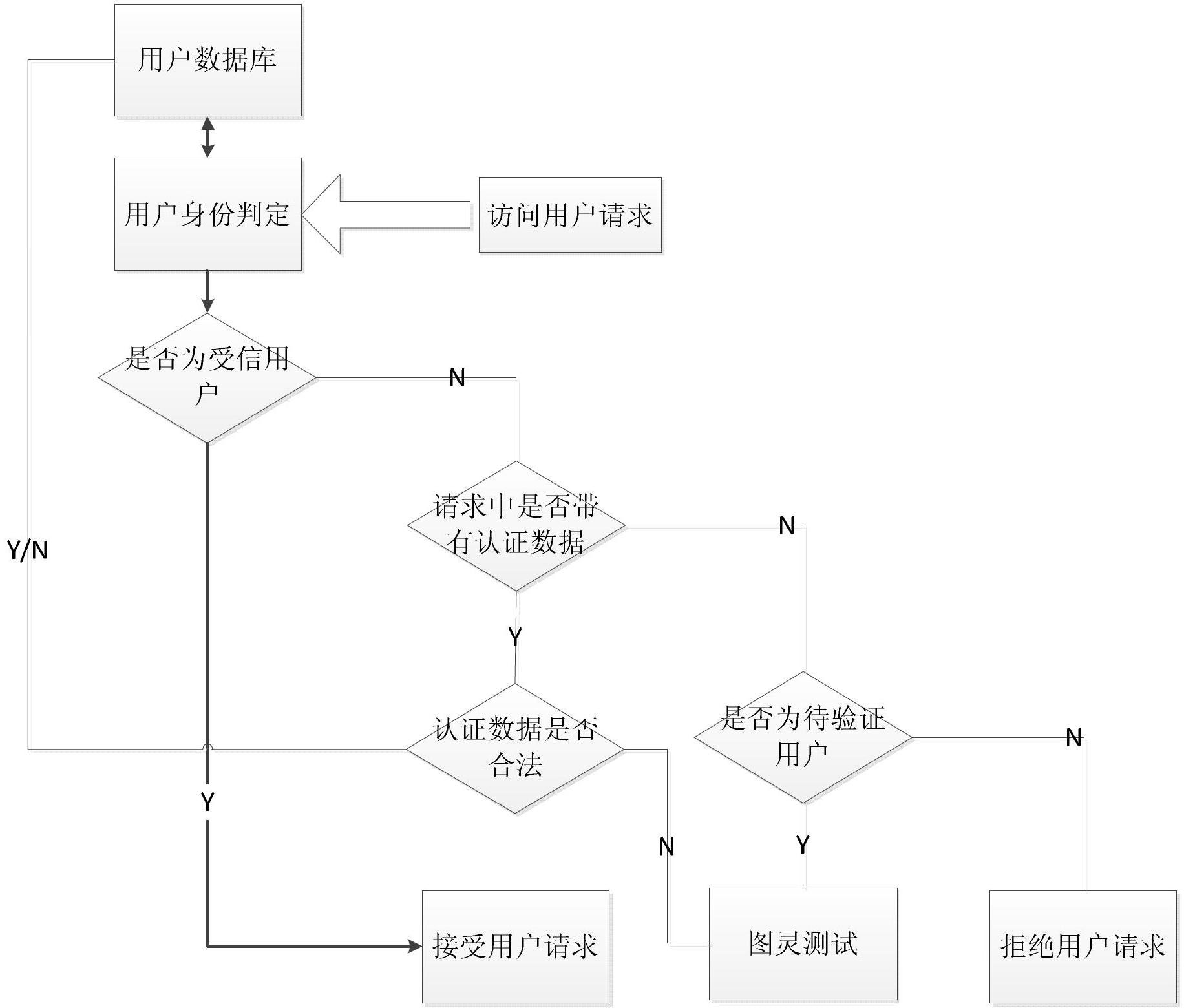
[0027] as attached figure 1 , the user identity determination steps are:
[0028] (1) Obtain the trusted level corresponding to the current request source IP and MAC by int...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com