Method for executing security-relevant and non-security-relevant software components on a hardware platform
A technology related to software and hardware platforms, applied in this field, can solve the problems of complex and expensive integration of non-critical functions
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
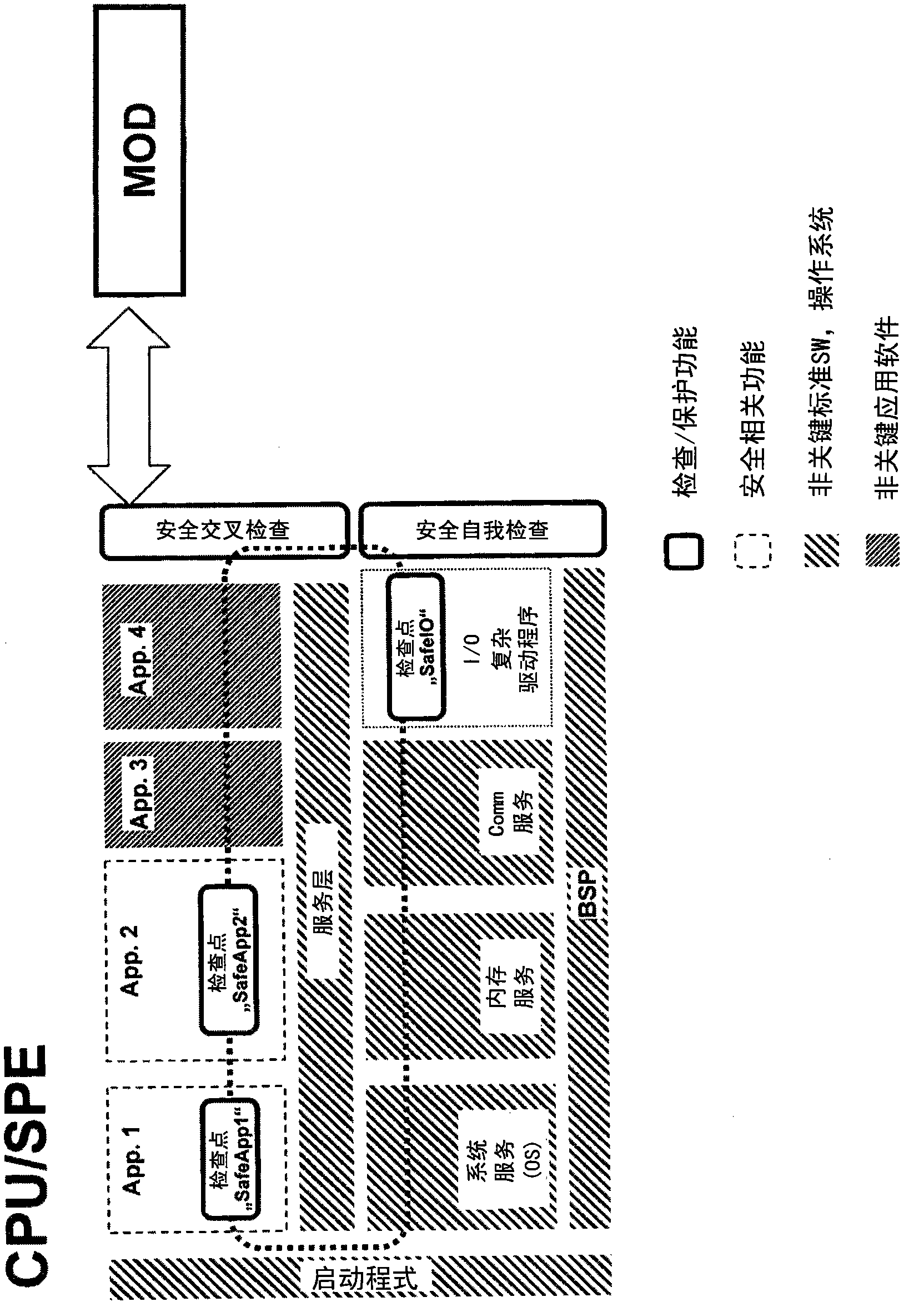
[0023] The invention is based on the combination of several features and methods:
[0024] 1. Implement memory protection on the memory of the CPU to block misdirected memory access (detection) from non-critical functions.
[0025] 2. Use of a checking component in a separate unit functioning as a monitoring module to detect faulty execution of safety-related functions.
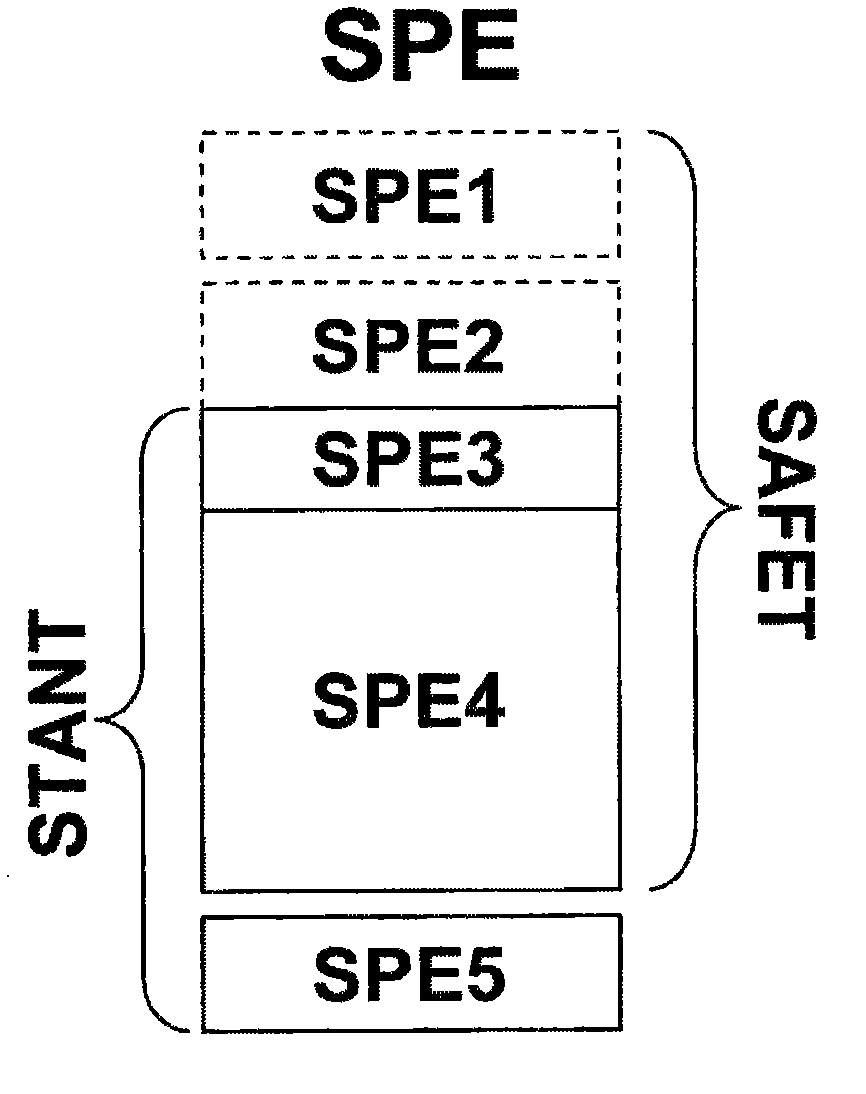
[0026] This approach utilizes these two technologies to enable reliable monitoring of safety-related functions. The working memory SPE of the CPU of the control unit is in accordance with figure 1 Some segments (segments).
[0027] These safety-related function SAFETs can read and write the entire working memory SPE (or the main area SPE1-SPE4 of the memory SPE), while these non-critical functions STANT can only read and write to a certain part of the working memory SPE SPE3-SPE5 for reading and writing. A portion of the memory SPE, SPE3, which is assigned to a non-critical area, is defined as a swap are...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com