A method and device for processing terminal vulnerabilities
A terminal and vulnerability technology, applied in the computer field, can solve problems such as reducing terminal performance and affecting the fluency of using the terminal, and achieve the effect of ensuring fluency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
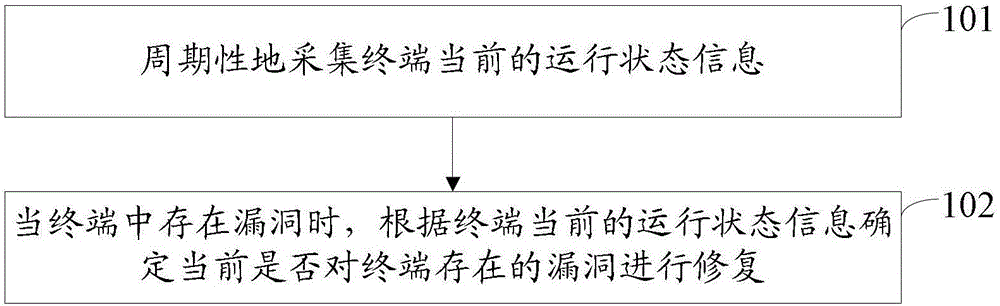
[0073] Such as figure 1 As shown, the embodiment of the present invention provides a method for processing terminal vulnerabilities, including:
[0074] Step 101: Periodically collect current operating status information of the terminal;
[0075] Step 102: When there is a loophole in the terminal, determine whether to repair the loophole existing in the terminal according to the current running state information of the terminal.
[0076] In the embodiment of the present invention, the current running state information of the terminal is periodically collected; when there is a loophole in the terminal, it is determined whether to repair the loophole existing in the terminal according to the current running state information of the terminal. In this way, when the user is using the terminal and occupies more resources of the terminal, the operation status of the terminal can be determined according to the current operation status information of the terminal, and it can be determ...
Embodiment 2
[0078] Such as figure 2 As shown, the embodiment of the present invention provides a method for processing terminal vulnerabilities, including:
[0079] Step 201: Periodically collect current operating state information of the terminal, the operating state information at least including CPU usage, proportion of available memory space, and network connectivity;
[0080] Specifically, a preset timer is started, and the timer is counted. When the timer overflows, the timer is set to count again, and the current operating state information of the terminal is collected.
[0081] Wherein, the current running state information of the terminal may be collected periodically when the terminal is started. When the timer overflows each time, an API (Application Programming Interface, application programming interface) function for collecting running state information can be called from the operating system of the terminal, and the running state information of the terminal can be collect...
Embodiment 3
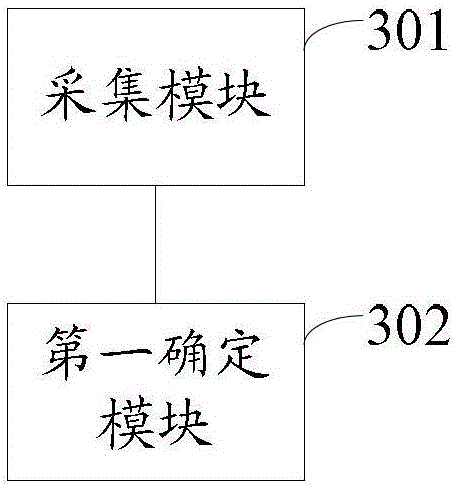
[0132] Such as image 3 As shown, the embodiment of the present invention provides a device for processing terminal vulnerabilities, including:
[0133] A collection module 301, configured to periodically collect current operating status information of the terminal;
[0134] The first determination module 302 is configured to determine whether to repair the existing vulnerabilities of the terminal according to the current running state information of the terminal when there are vulnerabilities in the terminal.
[0135] Among them, see Figure 4 , the collection module 301 includes:
[0136] The starting unit 3011 is used to start a preset timer and make the timer count;
[0137] The collection unit 3012 is configured to set the timer to count again when the timer overflows, and to collect current operating status information of the terminal.
[0138] Wherein, the operating status information of the terminal includes at least the CPU usage rate, the proportion of available ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com