Access detecting method and device
A detection device and a technology for accessing terminals, applied in the network field
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
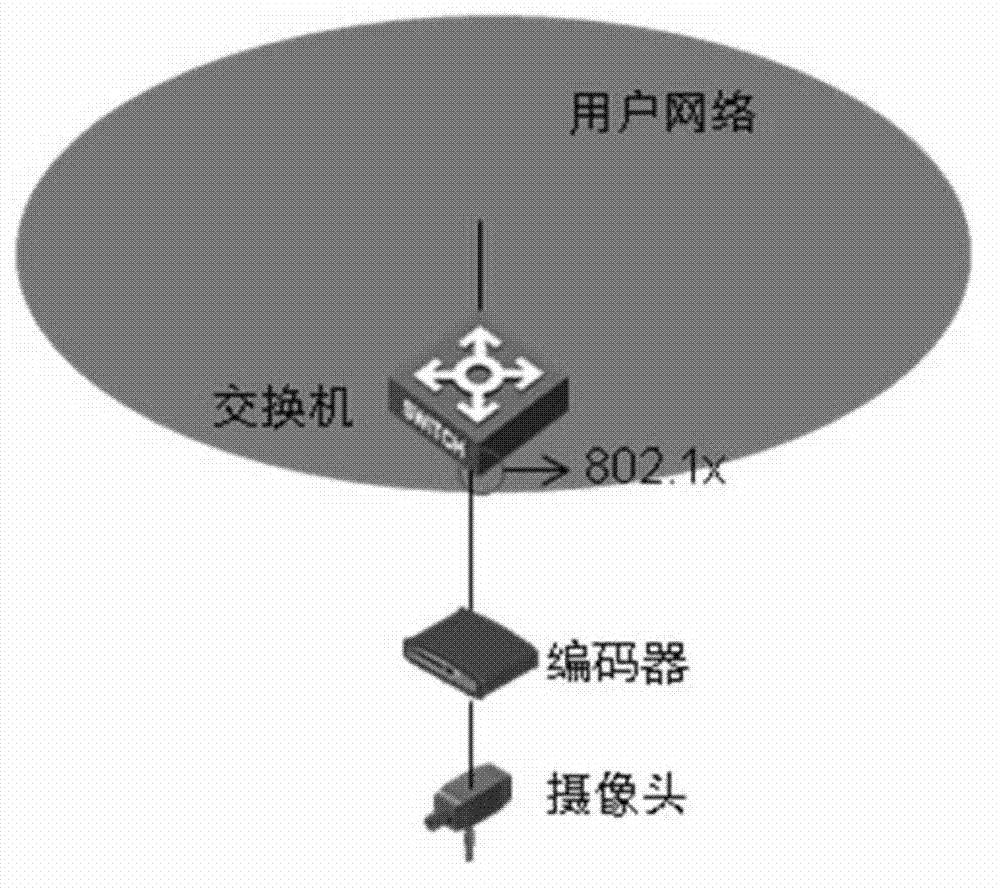
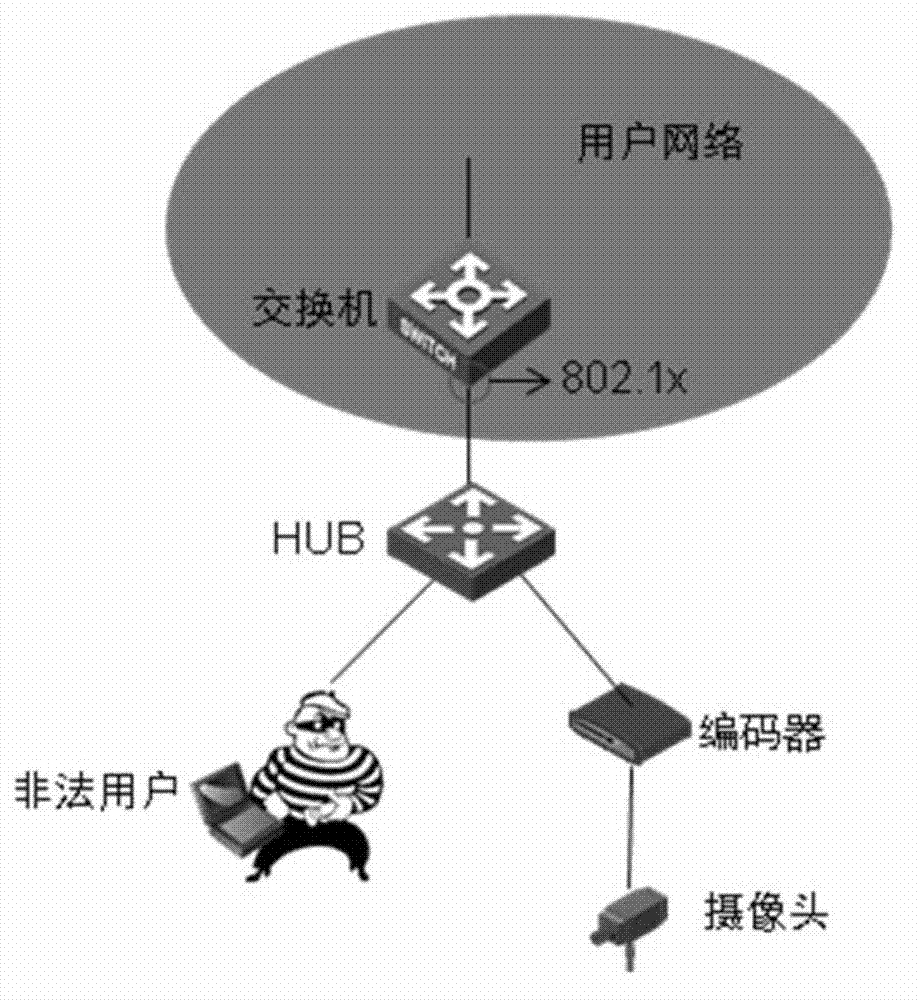
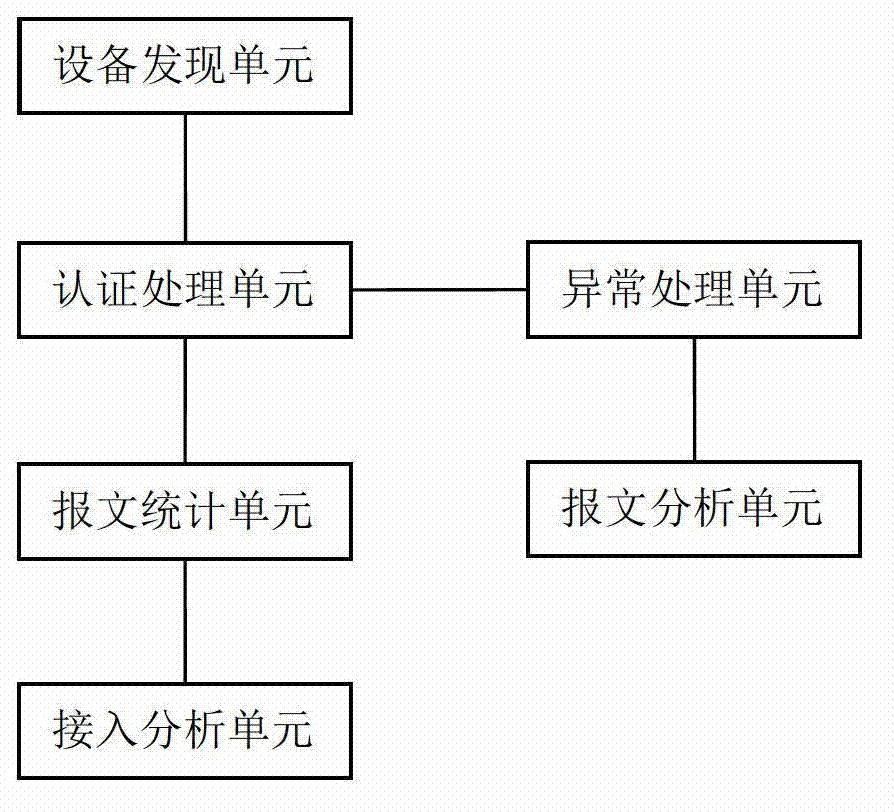
[0019] The present invention discovers the existence of illegal users by identifying the abnormal behavior of users, and takes certain countermeasures to reduce the security risk caused by the access of illegal users. The following uses computer program implementation as an example for introduction, but the present invention does not exclude other implementation manners. In one embodiment of the present invention, an access detection device is provided at an access terminal (taking an encoder as an example), and the access device includes: a device discovery unit, an authentication processing unit, a packet statistics unit, an access analysis unit, and an access analysis unit. Unit, exception processing unit and message analysis unit, the device cooperates with the switch to perform the following steps when running.
[0020] In step 101, the device discovery unit uses a neighbor discovery protocol to interact with an authentication switch to complete neighbor discovery.
[00...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com