Injection point extracting method in SQL (Structured Query Language) injection vulnerability detection
A technology of vulnerability detection and extraction method, applied in software testing/debugging, instrumentation, electrical digital data processing, etc., can solve problems such as poor accuracy, and achieve the effect of improving accuracy, improving coverage, and solving false negatives.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
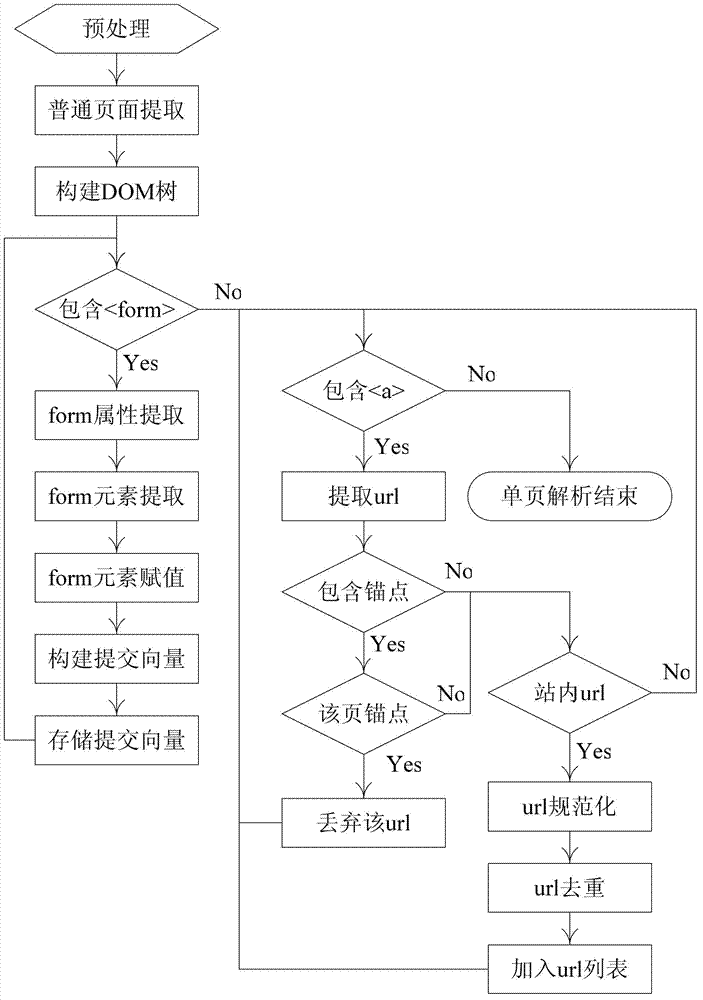
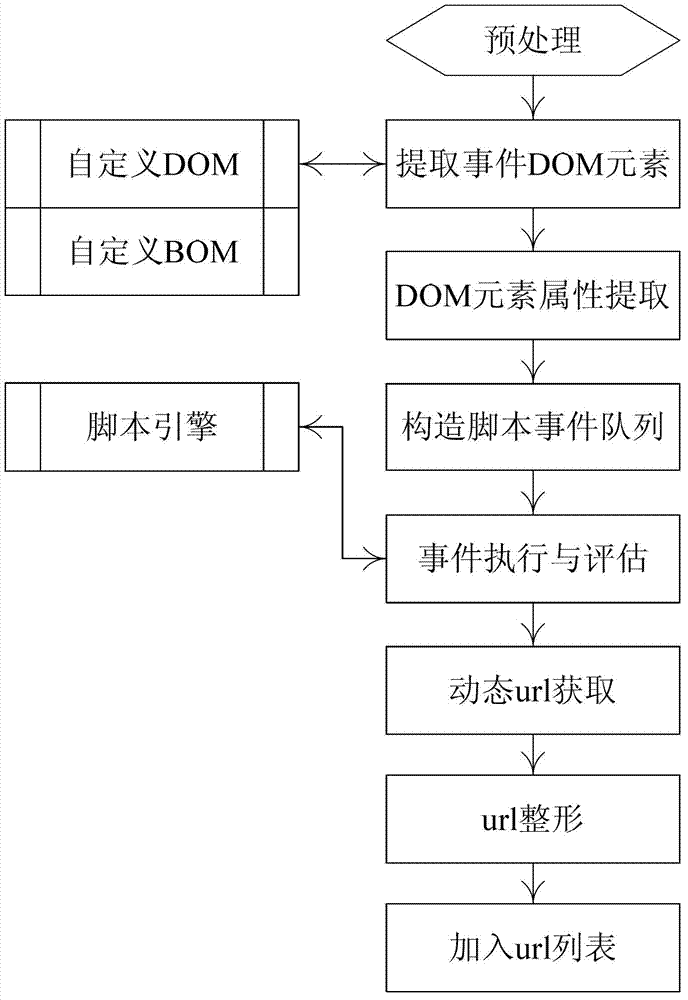
[0026] The specific steps of the injection point extraction method in the SQL injection vulnerability detection of the present invention are as follows:
[0027] 1. Pretreatment.
[0028] Download web pages according to the starting URL of the tested website, and preprocess the downloaded web pages. The purpose of preprocessing is to reduce the complexity of subsequent steps, while providing data needed for subsequent processing. The preprocessing work includes two parts: analyzing the Frame page and obtaining Cookies. If the web page contains a frame set, the pages in the frame set are downloaded together. At the same time, the cookies set by the web application system are saved, and the saved cookies are used as materials for constructing HTTP data packets in subsequent tests.
[0029] 2. Distinguish the types of web pages.
[0030] In order to simplify processing, this method is based on whether the HTML source code of the web page contains " when processing web pages. "Tag pa...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com