A method for encrypting and decrypting data packets
A data packet, encryption and decryption technology, applied in the field of information security, can solve complex encryption and decryption processing, difficult data packet encryption and decryption processing, etc., to achieve the effect of increasing network adaptability and simplifying development difficulty
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
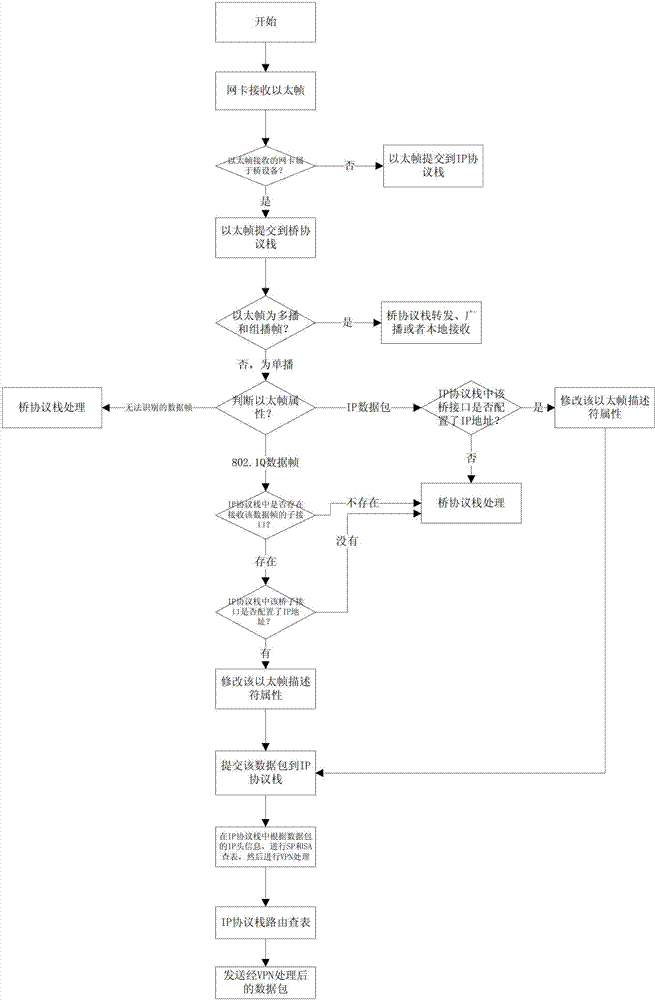
[0014] As attached to the manual figure 1 The flow chart of the method for encrypting and decrypting data packets in the present invention is shown. The invention discloses a method for encrypting and decrypting data packets, which specifically includes the following steps:
[0015] Step 1, the physical network card receives the ether frame, and judges whether the network card received by the ether frame belongs to a bridge device, if so, then submits the ether frame to the bridge protocol stack, if not, then submits the ether frame to the IP protocol stack;
[0016] Step 2, the bridge protocol stack identifies the Ethernet frame, if the Ethernet frame is a unicast frame, then identifies the attributes of the Ethernet frame, and the non-unicast frame is directly processed by the bridge protocol stack;
[0017] Step 3, when the attribute of Ethernet frame is IP packet, judge whether this bridge interface in the IP protocol stack is configured with IP address, if yes, then revi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com