Network terminal, security certification and registration activation methods thereof and server
A network terminal and security certification technology, applied in the field of network terminal security certification, can solve problems such as piracy, increased cost and complexity of network TV terminals, and loss of manufacturers and service operators, so as to reduce security certification costs and reduce counterfeiting by pirated versions The effect of risk on production
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0024] The technical solutions of the present application will be described in further detail below with reference to the drawings and embodiments.
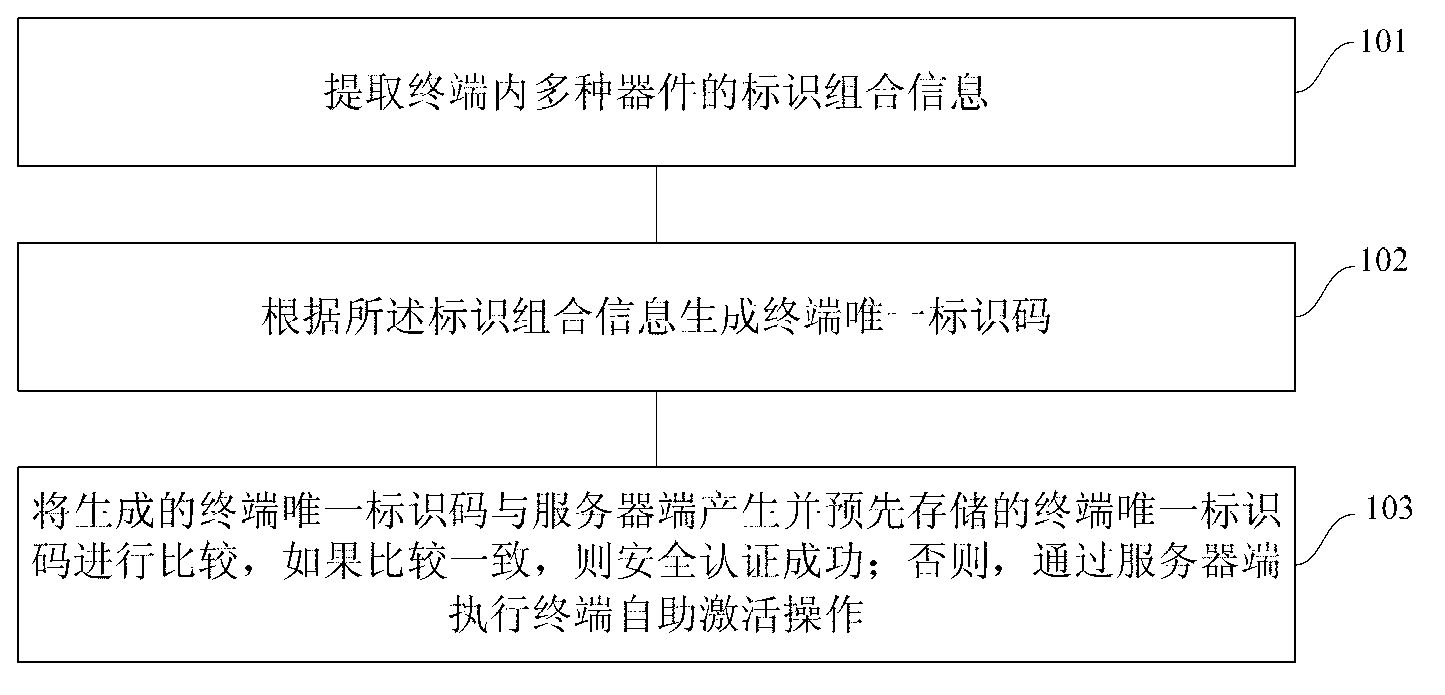
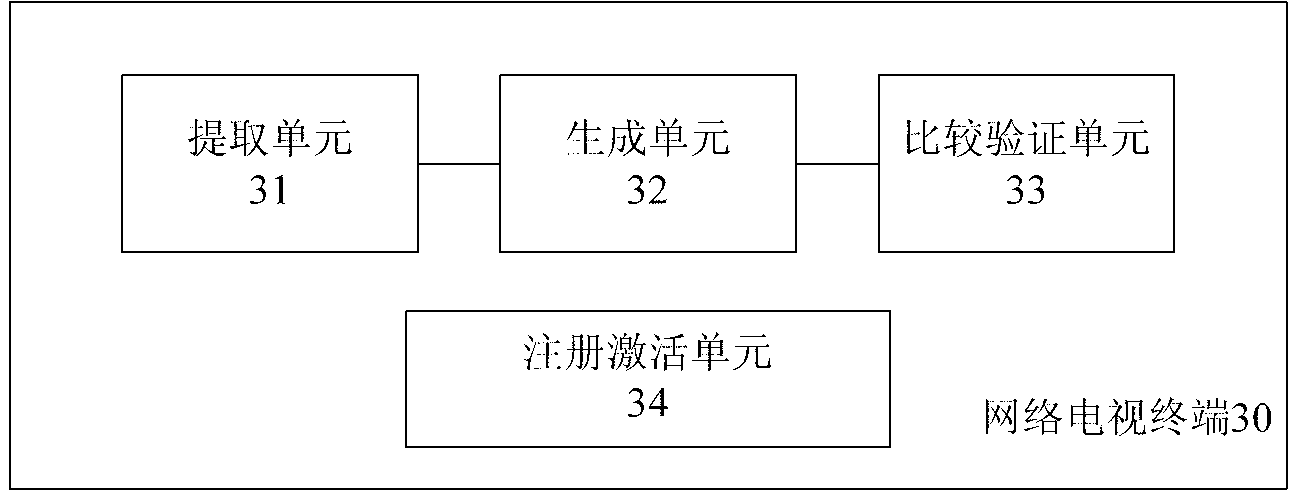
[0025] With the development of smart terminals and security technologies, IPTV terminals have a variety of built-in devices, such as CPU (Central Processing Unit, central processing unit) and FLASH (flash memory). Each chip of many CPUs and FLASH has unique identification information, and the network The MAC address of the terminal network interface and the terminal serial number pre-allocated by the television terminal also have unique identification information. The embodiment of the present invention utilizes the combination of the unique identification information of various devices built into the above-mentioned Internet TV terminal to generate a terminal unique identification code through a hash digest algorithm, and then uses the manufacturer's private key asymmetric encryption algorithm to generate a digital signature. Si...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com