User authentication method of electronic device
A user authentication and electronic equipment technology, applied in the field of electronic equipment user authentication, can solve the problems of user memory, low security, overlapping authentication speed of fingerprint authentication, etc., to achieve ease of use and fun, high security, novel use The effect of experience
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0026] Such as Figure 1 to Figure 3 As shown, this embodiment provides an electronic device user authentication method, including the following steps:
[0027] S11 pre-stores authorized color information;
[0028] S12 input color information to be certified;
[0029] S13 compares the color information to be authenticated with the pre-stored authorized color information, and when the two are the same, execute the operation that passes the authentication; when the two are different, execute the operation that does not pass the authentication.
[0030] This embodiment provides a user authentication method of an electronic device through color information verification. As long as the color information to be authenticated input by the user is consistent with the pre-stored authorized color information, authentication can be implemented and the operation passed the authentication can be performed. Those skilled in the art can understand that the operation through authentication c...
Embodiment 2
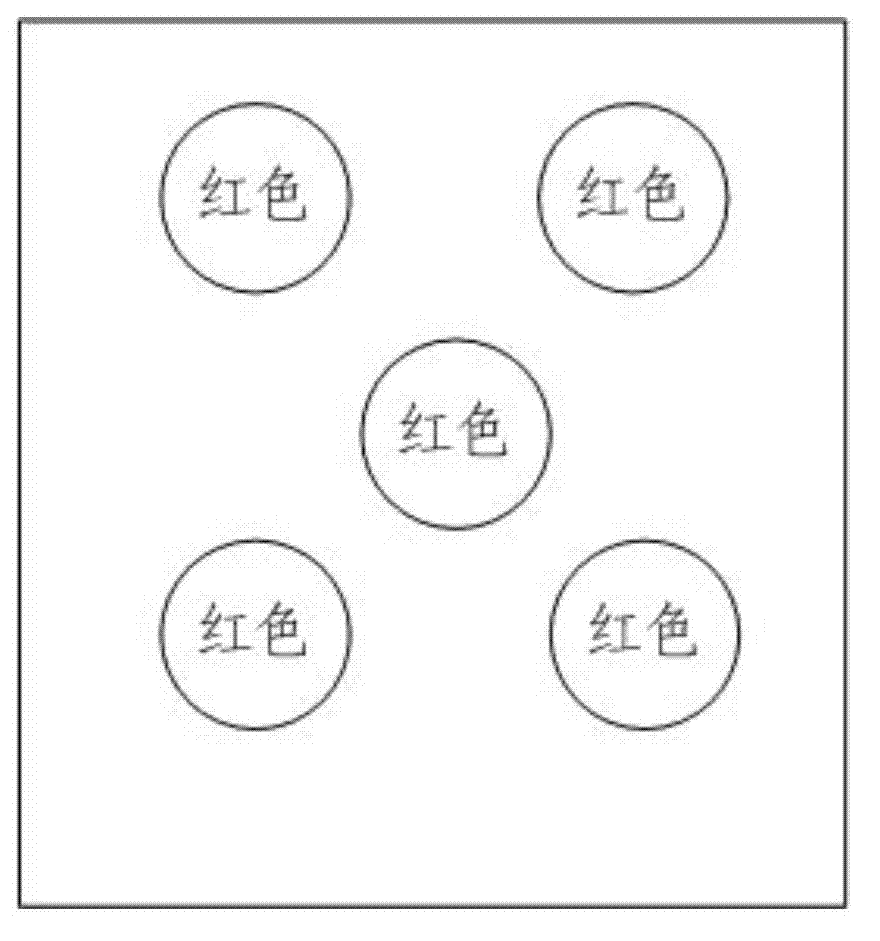
[0041] Such as Figure 4 to Figure 6 As shown, this embodiment provides an electronic device user authentication method, including the following steps:
[0042] S21 pre-stores authorized quantity information and authorized color information;
[0043] S22 input quantity information to be certified and color information to be certified;
[0044] S23 compares the color information to be authenticated with the pre-stored authorized color information, and when the two are the same, execute step S24;
[0045] S24 compares the quantity information to be authenticated with the pre-stored authorized quantity information, and when the two are the same, execute the operation that passes the authentication; when the two are not the same, execute the operation that does not pass the authentication;
[0046]This embodiment provides an electronic device user authentication method through color information and quantity information, which not only requires that the color information to be au...
Embodiment 3
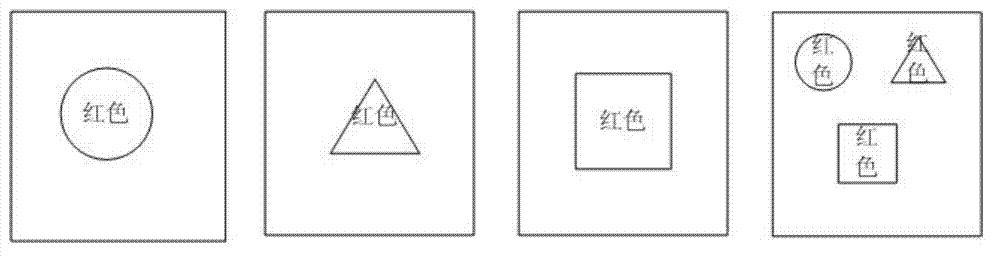
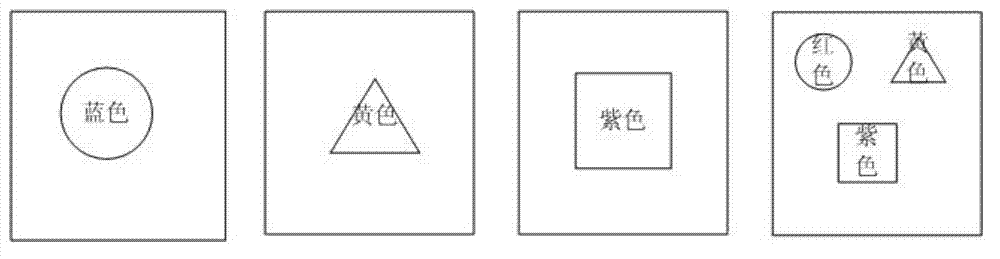
[0057] Such as Figure 7 to Figure 9 As shown, this embodiment provides an electronic device user authentication method, including the following steps:
[0058] S31 pre-stores authorized shape information and authorized color information;
[0059] S32 input shape information to be certified and color information to be certified;
[0060] S33 compares the color information to be authenticated with the pre-stored authorized color information, and when the two are the same, execute step S34;
[0061] S34 compares the shape information to be authenticated with the pre-stored authorized shape information, and when the two are the same, execute the operation that passes the authentication; when the two are different, execute the operation that does not pass the authentication;
[0062] This embodiment provides an electronic device user authentication method through color information and shape information, which not only requires that the color information to be authenticated input...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com