Third party application centralized safety management method and system and corresponding communication system
A technology of security management and centralized management, applied in the field of centralized security management, it can solve the problems of abusing network APIs and illegally accessing users
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
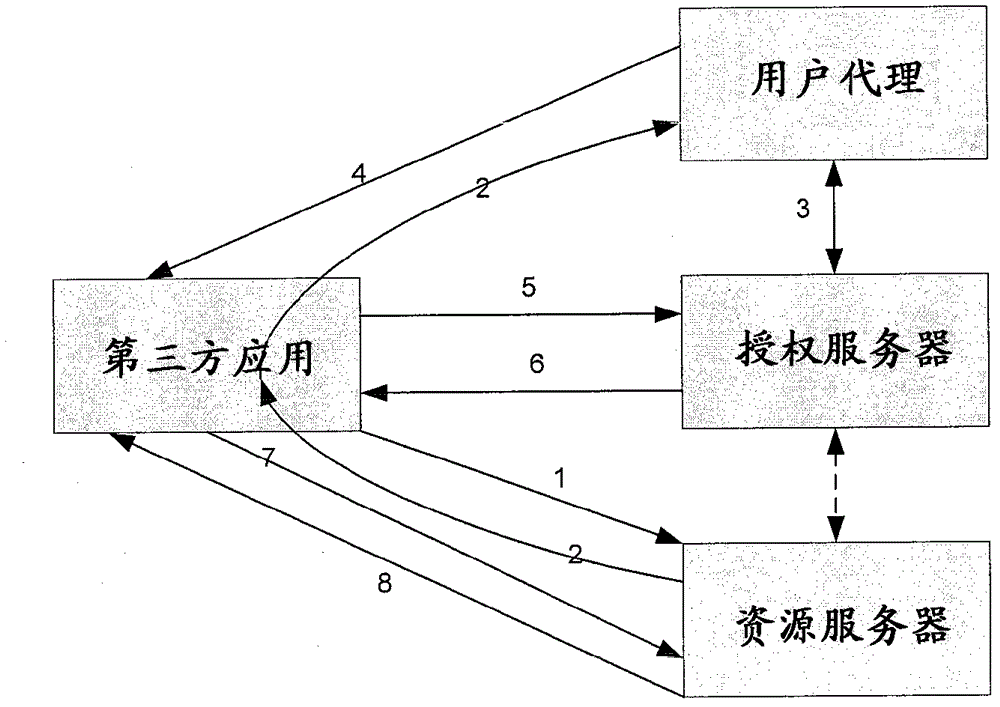
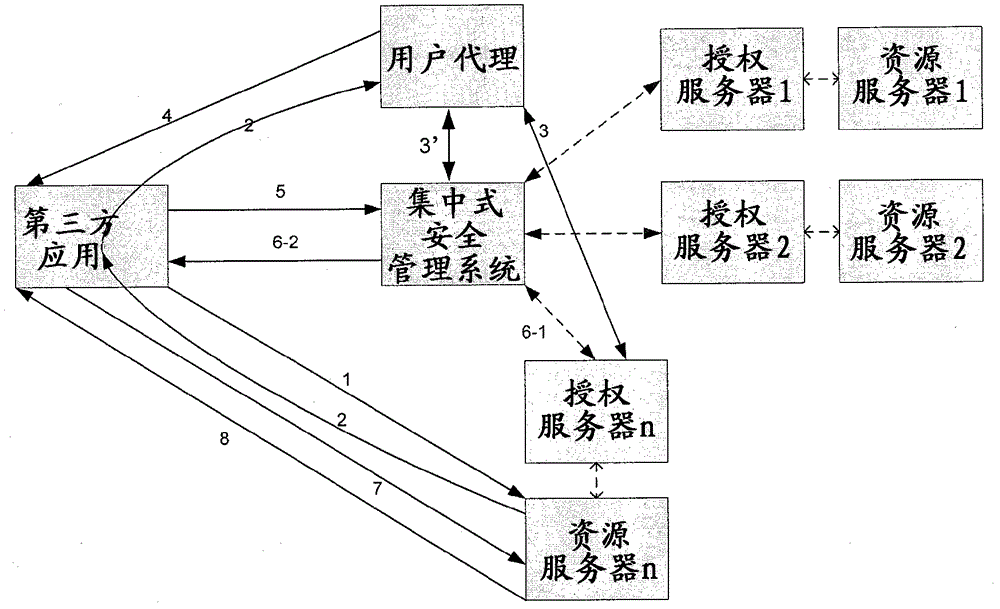
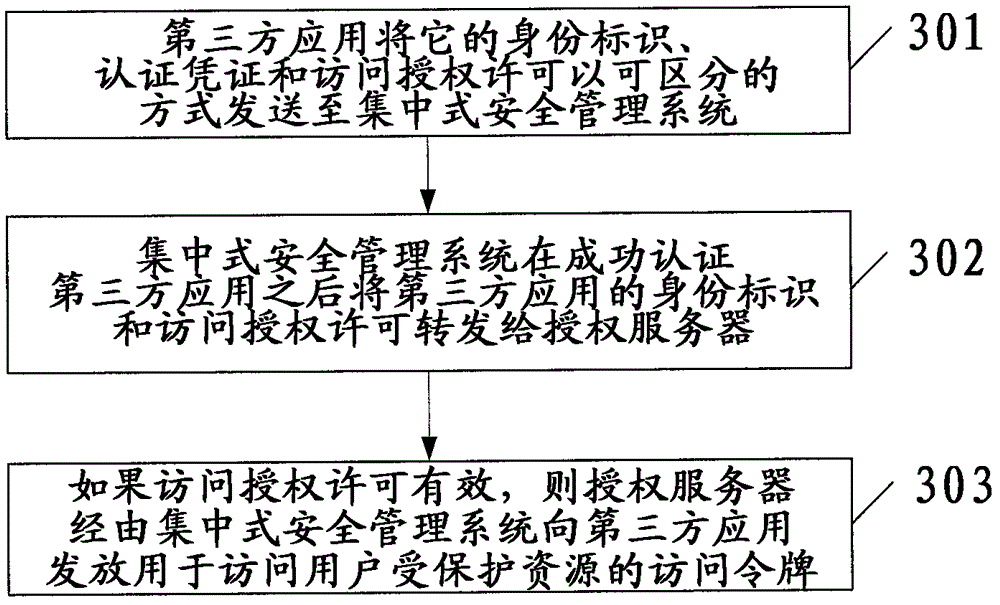
[0034] The basic idea of the invention is centralized security management for third party applications / clients that want to access the user's protected resources stored in the resource server. For the sake of brevity, "third-party applications / clients" are collectively referred to as "third-party applications" hereinafter. figure 2 A system and workflow of centralized security management for third-party applications are schematically shown. Such as figure 2 shown, with figure 1 Compared with the existing technical solutions in , a centralized security management system is added, which can perform the following functions:
[0035] - Before the official release of third-party apps:
[0036] ◆Use the digital certificate of the individual developer or service provider to authenticate the individual developer
[0037] or service provider's private key to sign the third-party application to ensure the traceability of the third-party application;
[0038] ◆ Verify that the t...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap