A method for authentication in sensor network and sensor network
A sensor network and network technology, applied in the field of methods and sensor networks, can solve the problems of large Merkle tree, limited sensor network resources, and inability to authenticate the validity of message packets, and achieve the effect of saving storage space.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
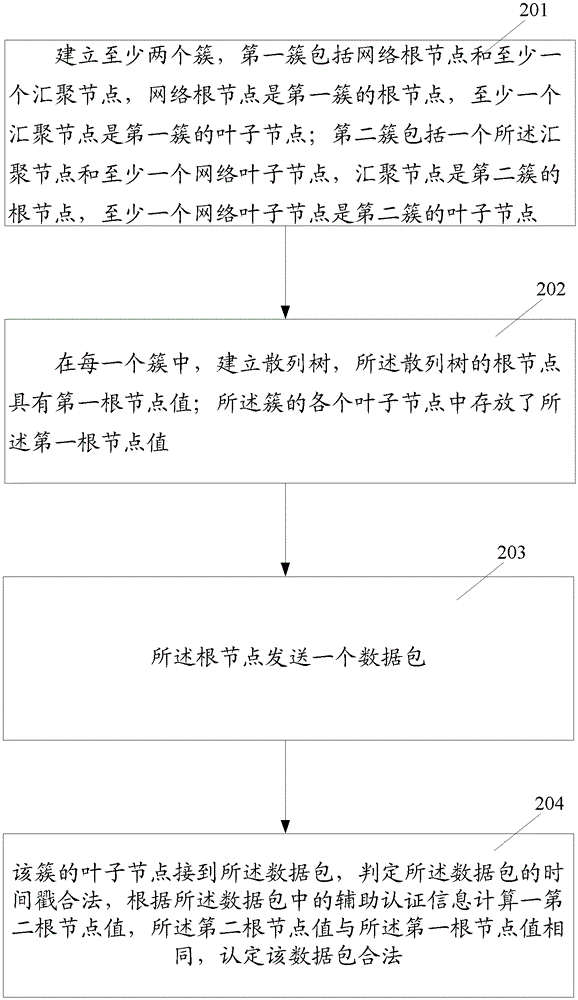
[0024] In order to make the technical problems, technical solutions and advantages to be solved by the present invention clearer, the following will describe in detail with reference to the drawings and specific embodiments.
[0025] The present invention aims to realize the two-way authentication between the sensor nodes and the aggregation nodes in the network containing a large number of sensor nodes.
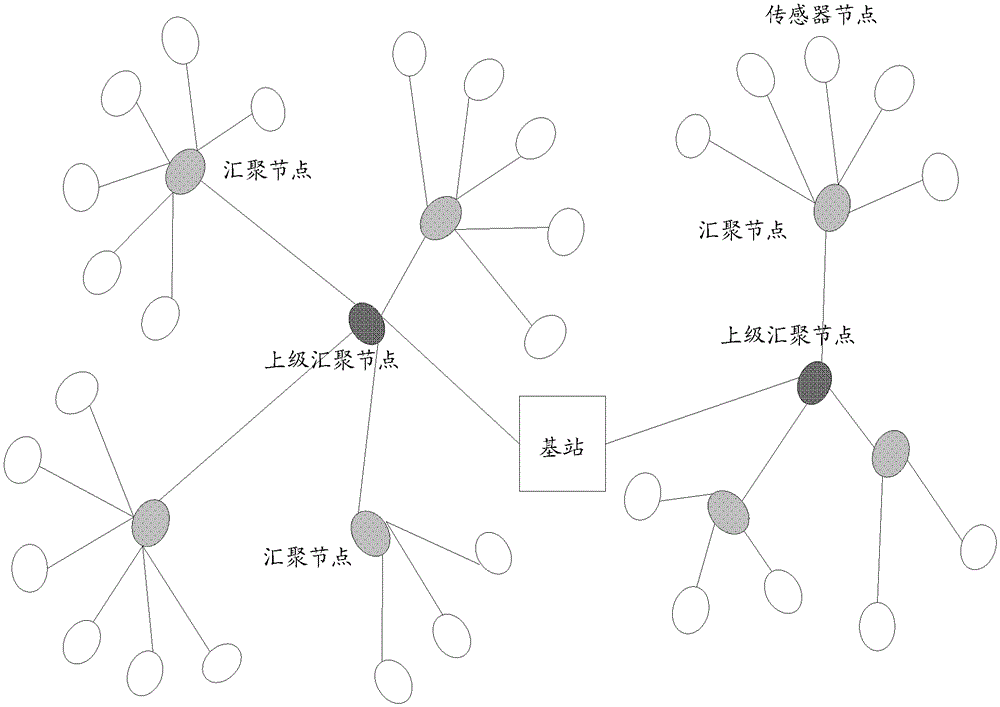
[0026] In a sensor network with a large number of sensor nodes, such as figure 1 As shown, the information collected by the sensor nodes is usually transmitted to the base station in a multi-hop manner, and the base station also transmits instructions to the sensor nodes in a multi-hop manner, for example, figure 1 The sensor nodes in the network need to go through two levels of sink nodes to transmit information to the base station.
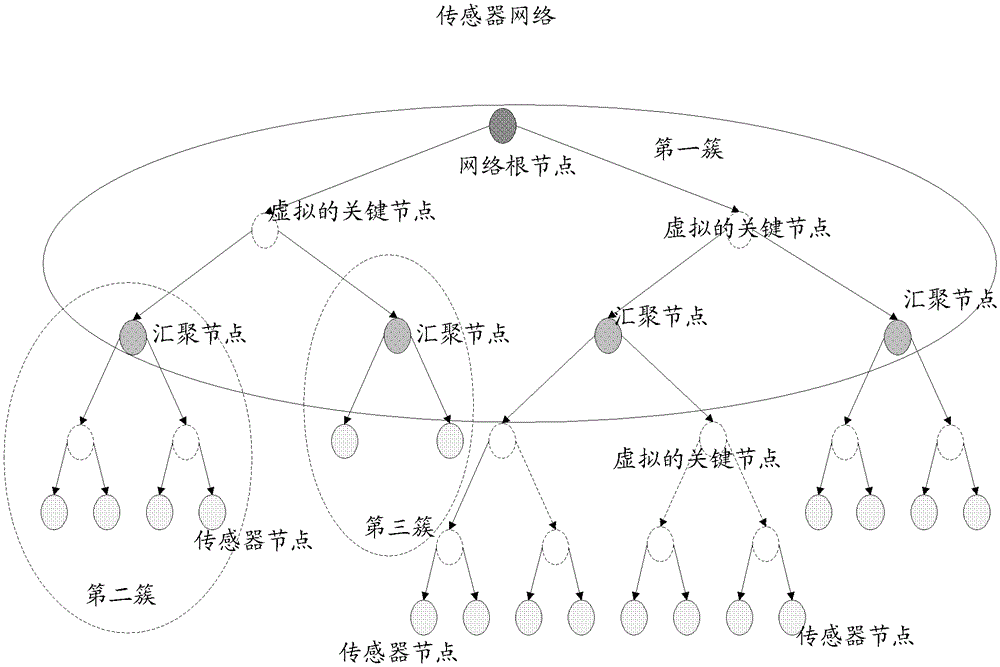
[0027] The hash tree in the embodiment of the present invention is a kind of complete binary tree, and the node value on each node of comple...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com