Web application safety detection method with white-box and black-box combined
A security detection and web application technology, applied in the field of information security, can solve the problems of high false alarm rate and inability to locate the source code location of the vulnerability, etc., and achieve the effect of solving the high false positive rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0035] Characters are defined as follows:
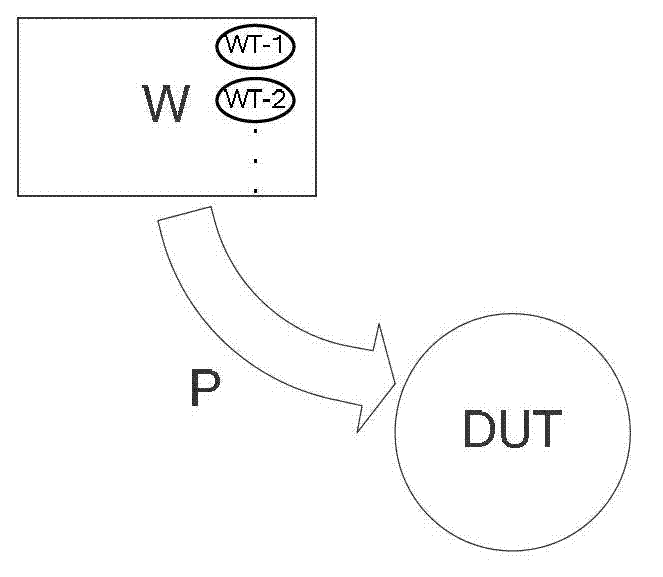
[0036] W: White box testing.
[0037] WT: A collection of technologies used in white-box testing, one of which is represented by WT-n (n=1, 2, 3...).
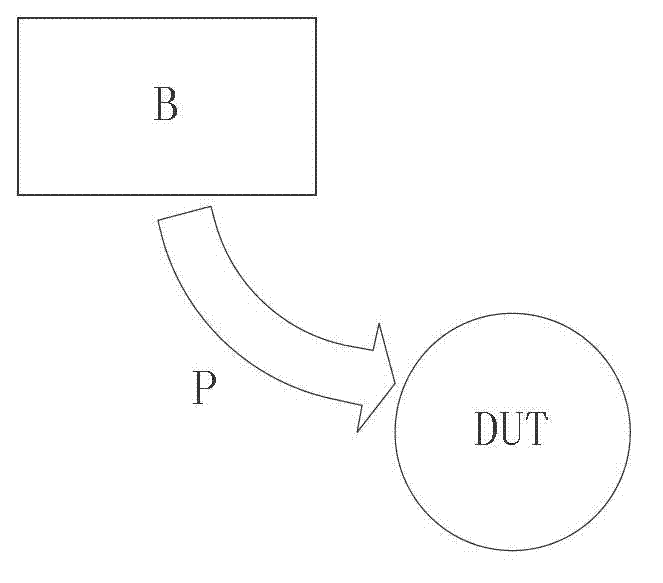
[0038] B: Black box testing.
[0039] P: Detection process.
[0040] DUT: the target Web application system under test.
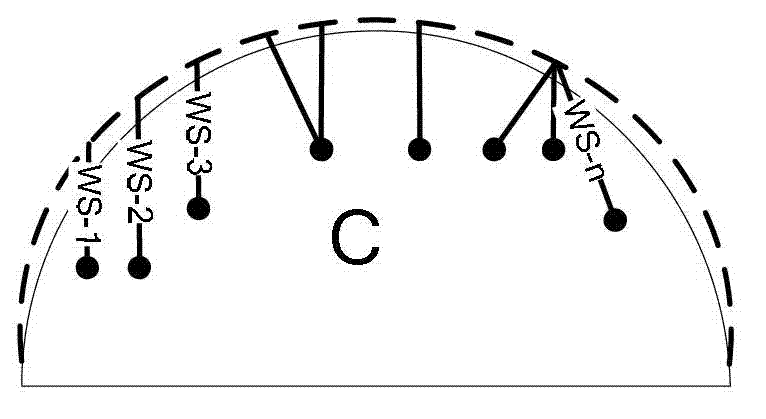
[0041] C: Web application system source code.
[0042] PF: a collection of source code files of the Web application system, and a certain result is represented by PF-n (n=1, 2, 3...).
[0043] WS: the result set of the white-box test, and one of the results is represented by WS-n (n=1, 2, 3.....).
[0044] BS: the result set of the black-box test, and one of the results is represented by BS-n (n=1, 2, 3...).
[0045] LS: Vulnerability set, one of the results is represented by LS-n (n=1, 2, 3...).
[0046] WS-nF: The file where a vulnerability in the white box test results resides.
[0047] BS-nF: The file containing a vulnerability in the black box test res...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com