Website access request parameter legal range analysis method and device
A technology of request parameters and access requests, applied in the field of network security, can solve the problems of unrecognizable, inflexible, and not fully utilizing the rich information of log files, etc., and achieve the effect of accurate identification and interception
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
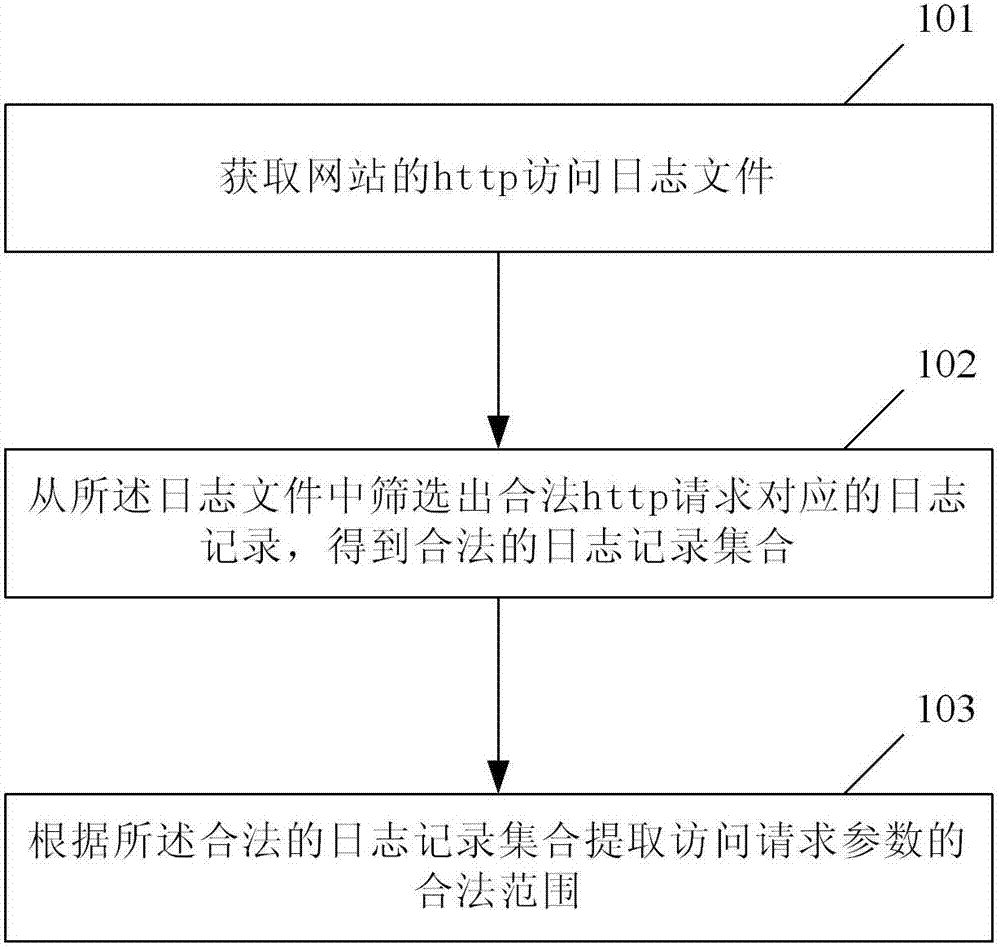
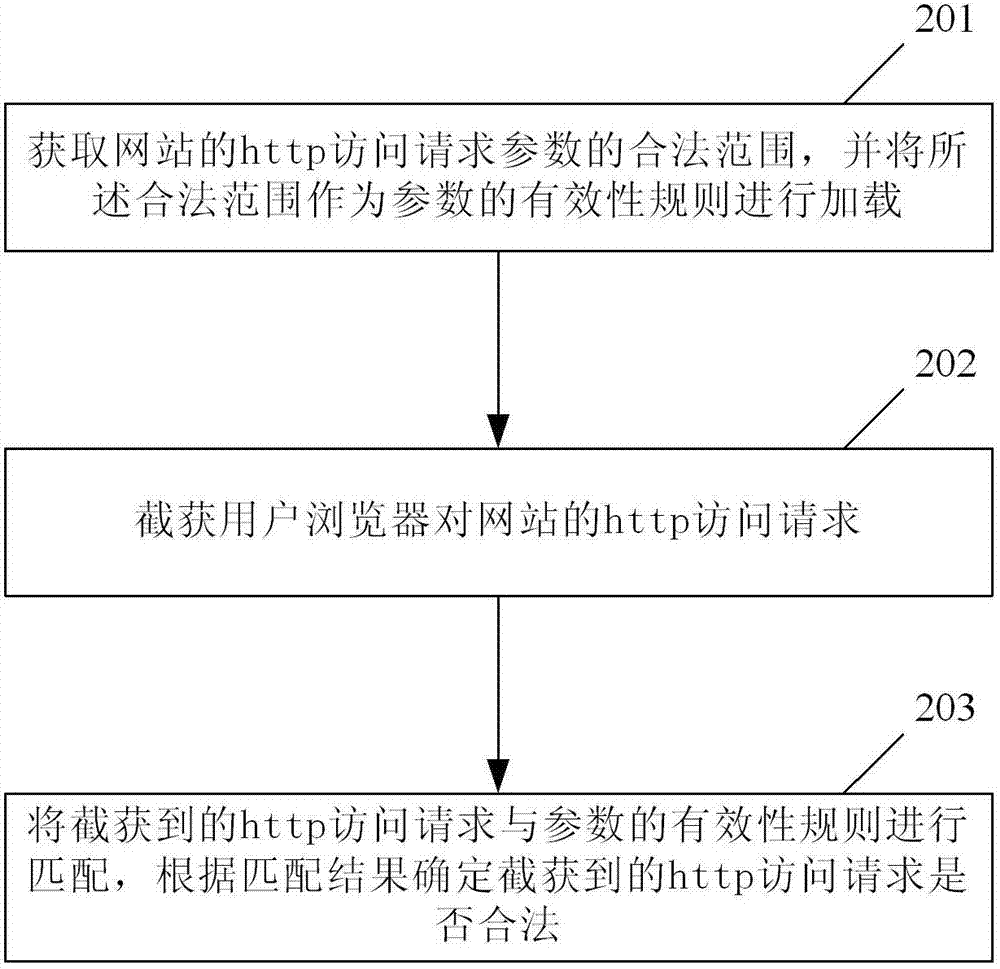
[0037] To facilitate a better understanding of the present invention, a brief introduction to the access log files of the website is firstly given here.
[0038] IIS is the abbreviation of Internet Information Server, which means Internet Information Service. The WEB log of IIS is the operation record of the website under IIS. Every time a visitor sends an http request to the website, no matter whether the visit is successful or not, the log file will record it.
[0039] The logs include information such as who visited the site, what the visitor viewed, and when the information was last viewed. Since IIS faithfully records all related records of accessing Web services, making full use of the logs can perform intrusion detection, traffic statistics analysis, solve IIS server failures, and solve page failures.
[0040] The default storage location of the WEB log files of IIS6.0 is %systemroot%\system32\LogFiles, and there is one log per day by default. If the log file is not p...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com