File bag tamper-evident device
A file bag and tamper-proof technology, which is applied to computer parts, record carriers used by machines, instruments, etc., can solve the problem that the file bag cannot be tamper-proof
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
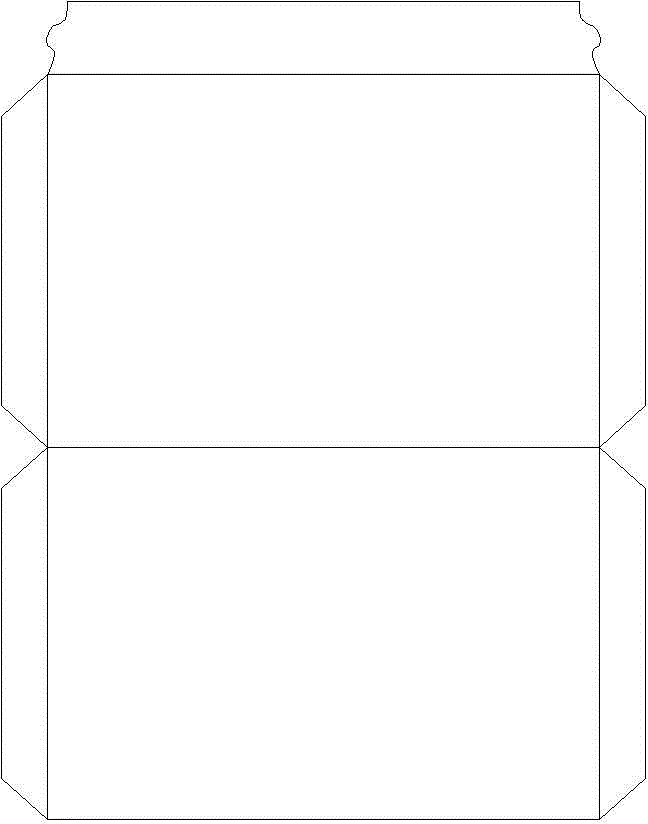
[0024] Such as Figure 4 As shown, the RFID tag 100 includes an antenna loop composed of a metal foil 101 with a line width of 1-5 mm and an RFID chip 102 . The metal foil 101 is connected to both ends of the RFID chip 102 to form an antenna loop, and the antenna loop is clamped between two pieces of PET film and fixed. In the antenna loop, the line spacing between adjacent metal foils 101 is generally 1-5 mm.
[0025] During the manufacturing process, the outer contour size of the RFID tag 100 is the size of the entire bag wall of the file bag. The RFID tag 100 can be embedded in the bag wall in advance, and then the bag wall is assembled into the file bag through processing technology. The line width of the metal foil 101 and the line spacing of adjacent metal foils 101 are preferably equal, so that when forming the folded edge on each side, the metal foil inside the folded edge can be aligned with the metal foil of the bag wall. Figure 5 It is a schematic diagram of the ...
Embodiment 2
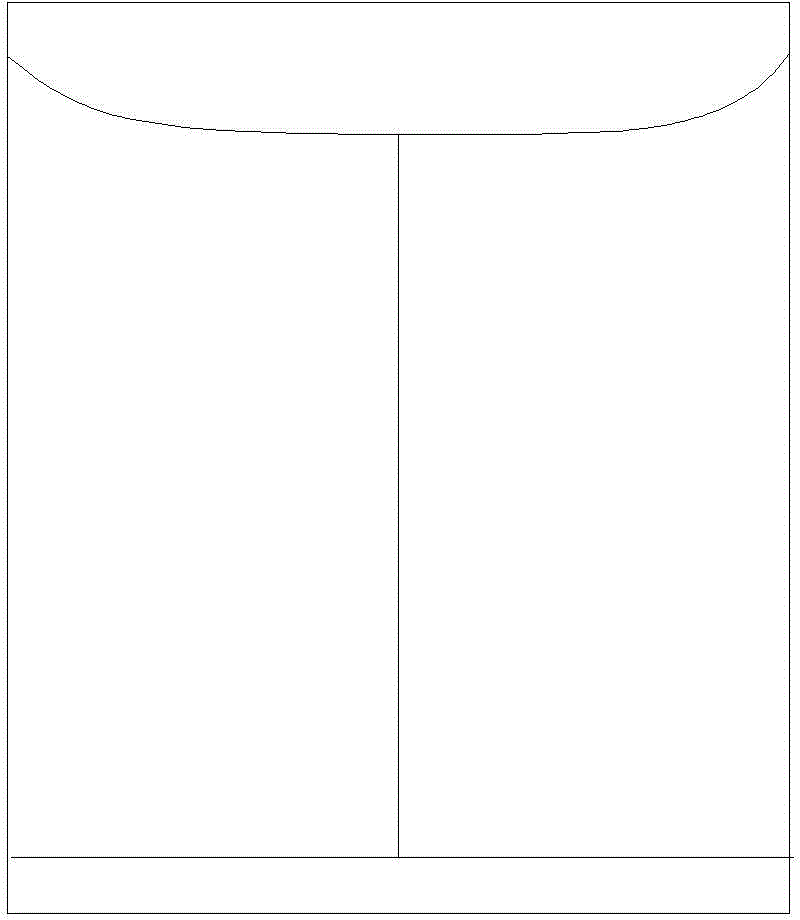
[0027] Figure 6 It is another RFID tag design solution. The RFID tag 100 includes an antenna loop formed by an RFID chip 102 and a metal foil 101 connected to the RFID chip 102 . The RFID tag is designed in the shape of the sidewall of the file bag before it is formed, and can be bent along the dotted line 1, the dotted line 2, the dotted line 3 and the dotted line 4 into the shape of the file bag. Figure 7 It is a schematic diagram of the combination of RFID tags and file bags. Such as Figure 7 As shown, there is an antenna loop at a position not far from the final document bag. When criminals cut any part of the document bag to steal documents, the antenna loop will be cut off, and any part of the antenna loop will be broken. If it is opened, it will cause the RFID chip to be unrecognizable, so as to realize the function of anti-tampering.
[0028] In addition, in order to strengthen the safety of the opening of the file bag (such as the upper folded edge), the edge of...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com