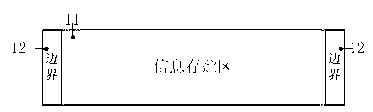Embedded type software security memory management method
A memory management and embedded system technology, applied in the field of computer software memory management, can solve the problems of not being able to allocate memory slices, less memory usage, and no debris collection method, and achieve the effect of efficient dynamic memory management
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
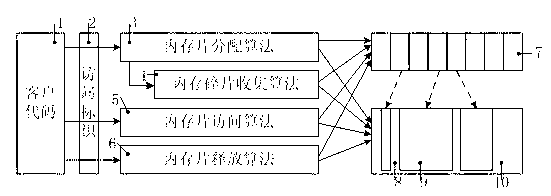
[0028] Such as figure 1 As shown, a method for secure memory management of embedded software includes: fixed access identifiers are fixed addresses and constants defined in the embedded software, which are constants that do not change during code running.
[0029] The memory management method based on fixed access identifiers is a set of algorithms for managing memory slices. These algorithms allocate memory slices in the memory pool and manage them through index tables. Client code uses fixed access identifiers to apply, access and release and so on.
[0030] Memory pool, statically allocated storage space in RAM, is used to store memory slices allocated to client codes.
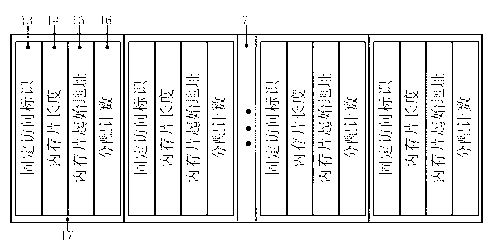
[0031] Index table, statically allocated storage space in RAM, used to store memory slice index.
[0032] The memory pool is a piece of storage space statically allocated in the embedded system RAM, and its size is pre-configured during programming of the embedded software. The memory slices that need to ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com