Method and device for identifying whether remote file contains vulnerability or not
A remote file and identification method technology, applied in the field of computer networks, can solve problems such as false positives and missed negatives, and achieve the effect of solving false positives and missed negatives
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
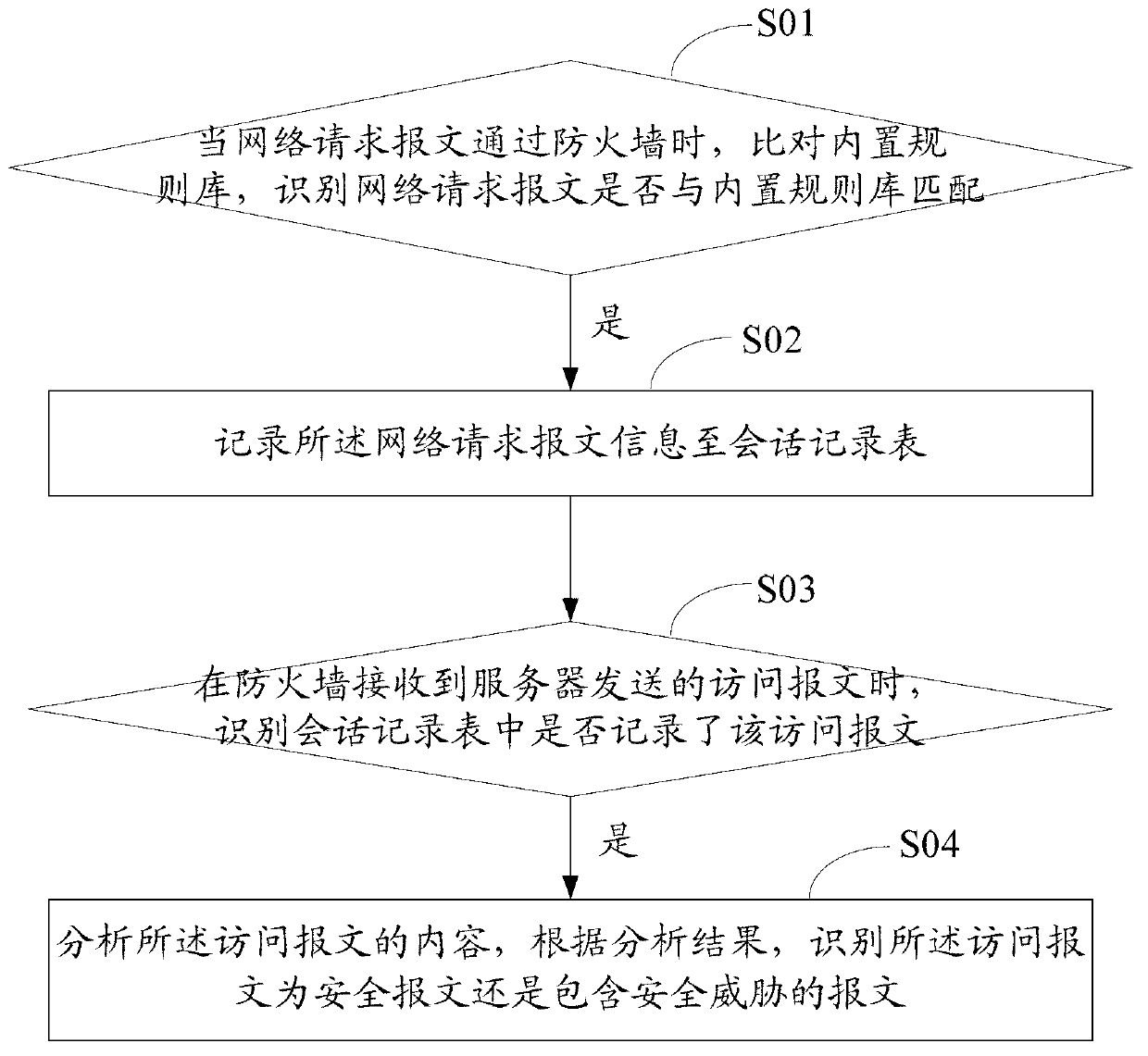
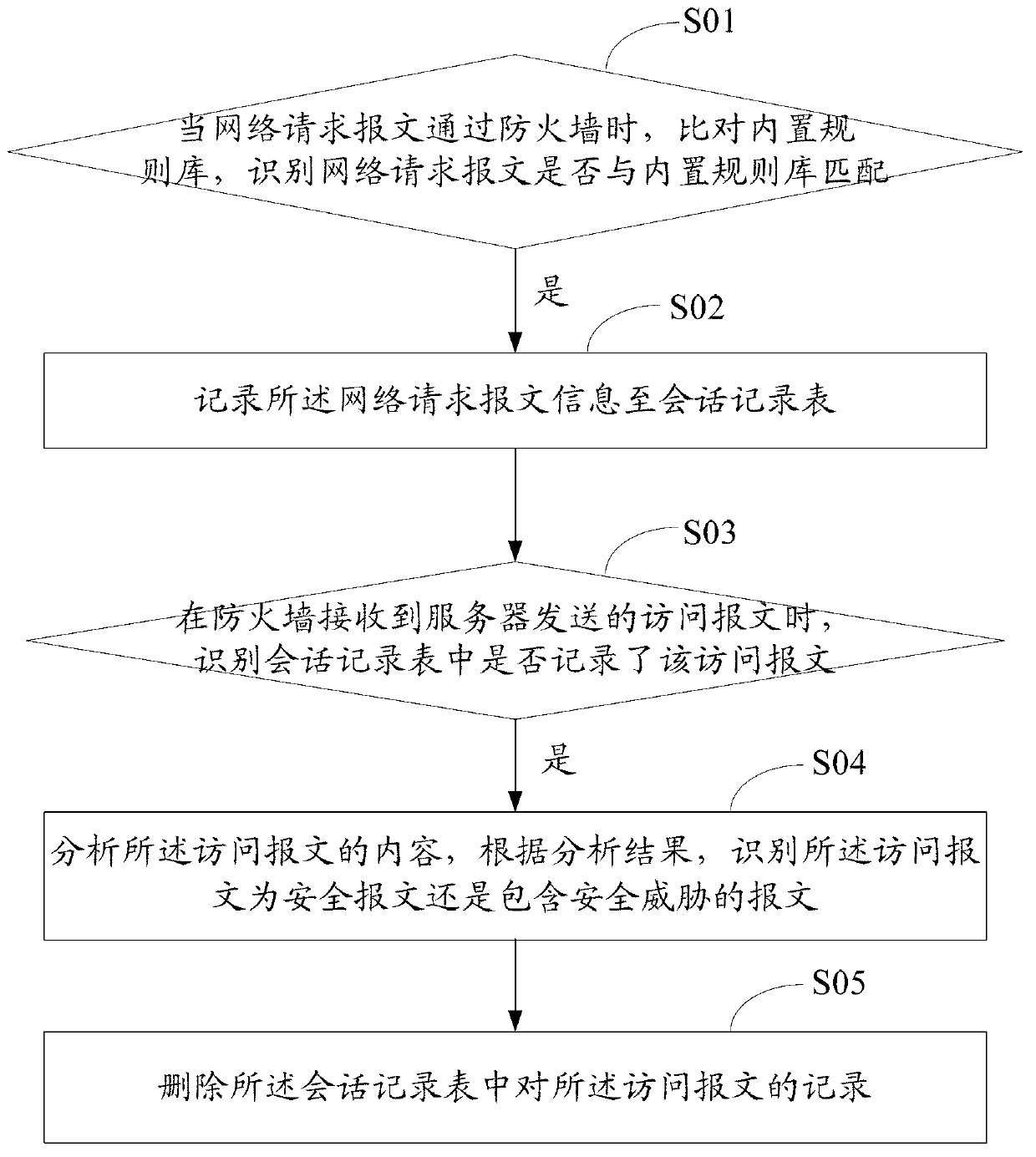
[0050] The technical solutions of the present invention will be further described below in conjunction with the accompanying drawings and specific embodiments. It should be understood that the specific embodiments described here are only used to explain the present invention, not to limit the present invention.
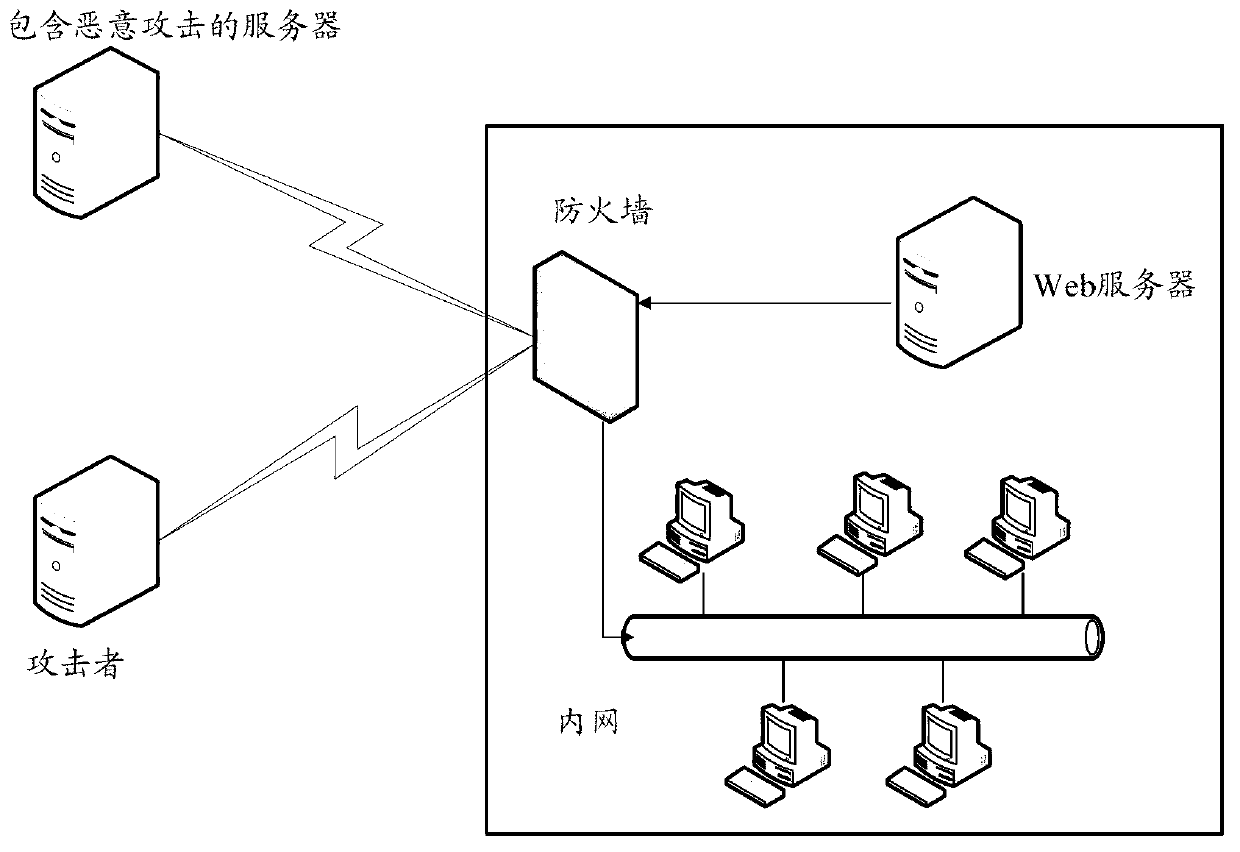
[0051] The method and device for identifying loopholes contained in remote files of the present invention combine the attacker's malicious attack request session with the web server's session requesting malicious files for analysis, and judge whether triggering the PHP remote file containment attack occurs according to the characteristics of the PHP remote file containment attack; the method It can exclude normal http (Hyper Text Transfer Protocol, hypertext transfer protocol) redirection requests, and at the same time, it can defend against undisclosed PHP remote file inclusion vulnerabilities, and effectively solve the false positives and false negatives existing in ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com