System and method for securing virtual computing environments
一种环境、计算机的技术
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
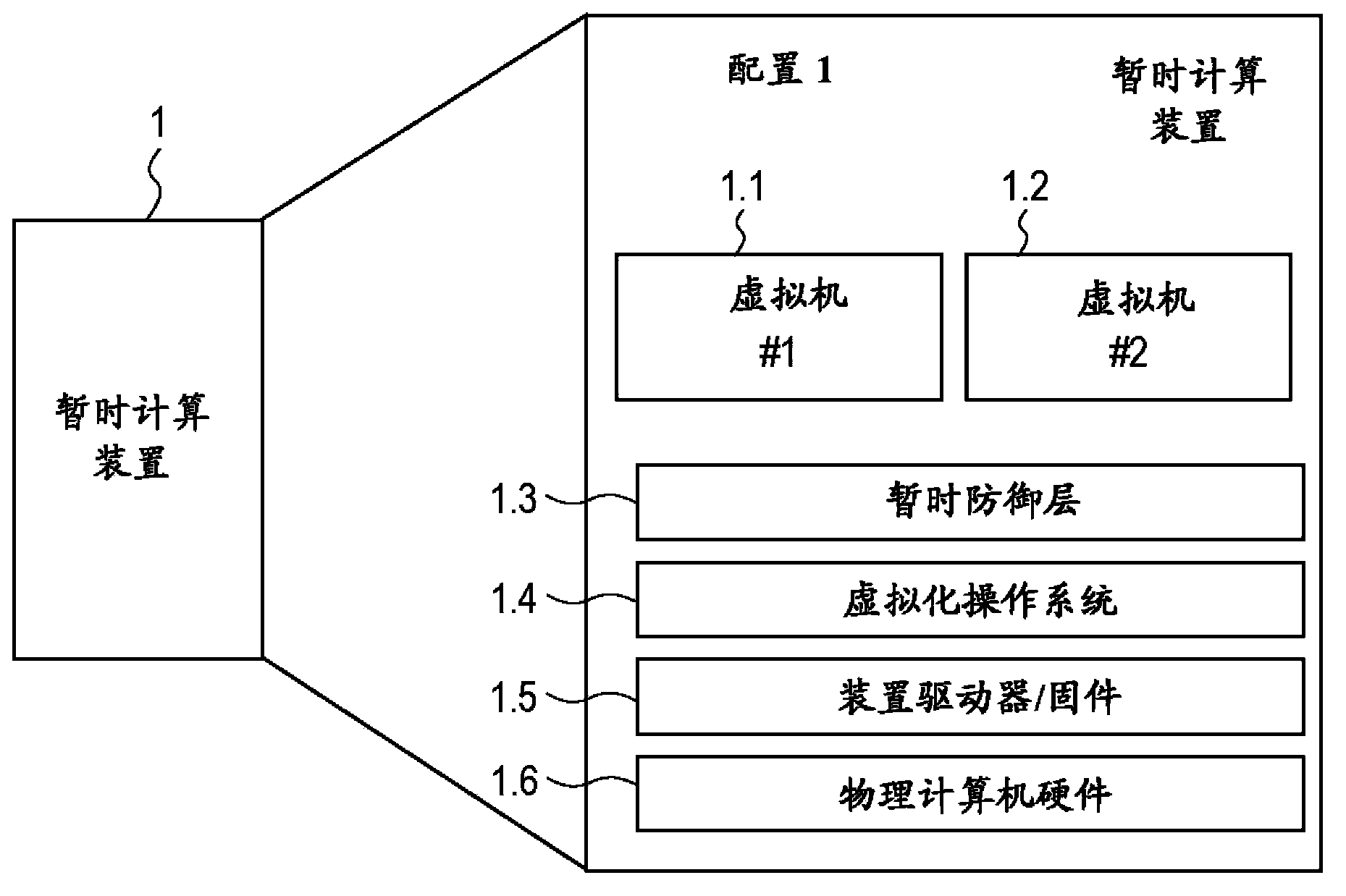
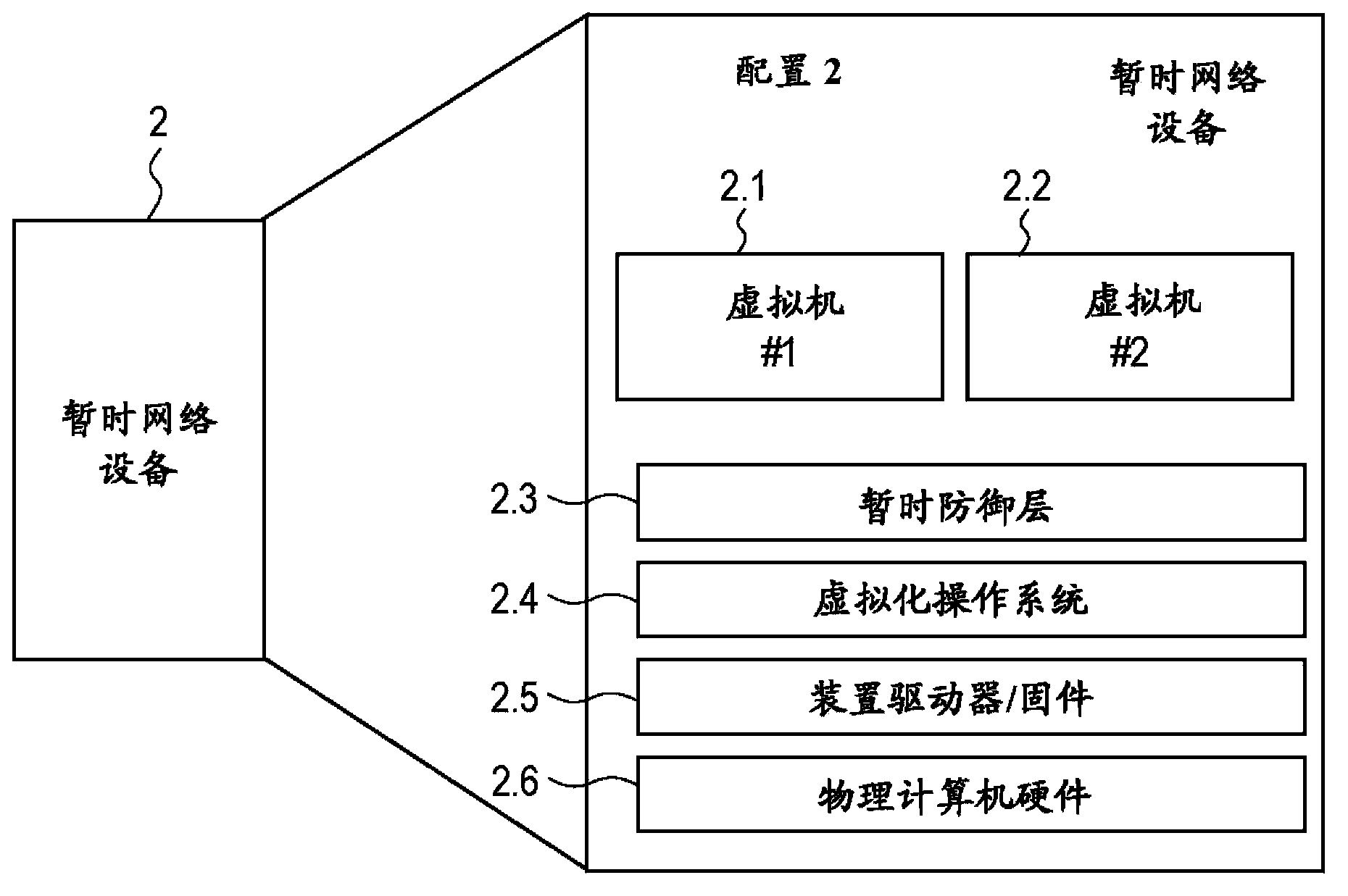
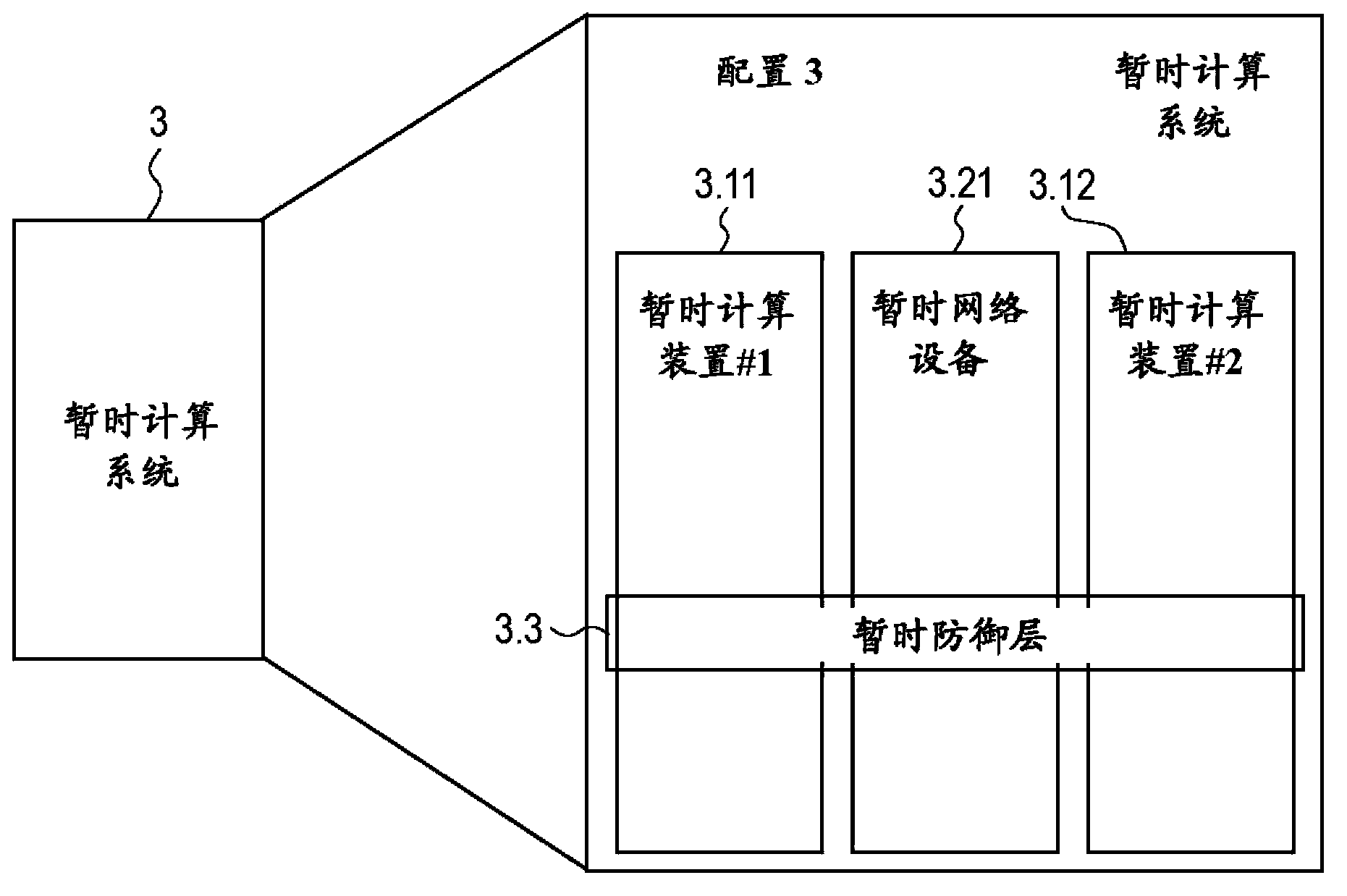
[0028] The present invention is designed to create a transient computing environment where usage of authorized processes occurs in a robust, stable computing environment and usage of unauthorized processes experiences an unfriendly, unstable, ever-changing computing environment. Furthermore, the present invention provides a mechanism for obscuring, obfuscating or obfuscating system specifications to unauthorized or compromised computing processes and their controllers (either a person or a remote agent who initiates or controls the process).
[0029] Furthermore, the present invention provides a technique for integrity verification of virtual and physical system instances that detects system compromise. In addition, the present invention provides a method of isolating an infected system to prevent virus propagation, preventing access to mission-critical commands, and a method of profiling that demonstrates, or warns of, viruses, The fact that unauthorized spy code or unauthori...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com