A kind of qr code encryption method
An encryption method, QR code technology, applied in the field of QR code encryption, can solve problems such as poor security, low efficiency, and no consideration of QR code coding rules and graphic characteristics, and achieve high compatibility, security and flexible encryption.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
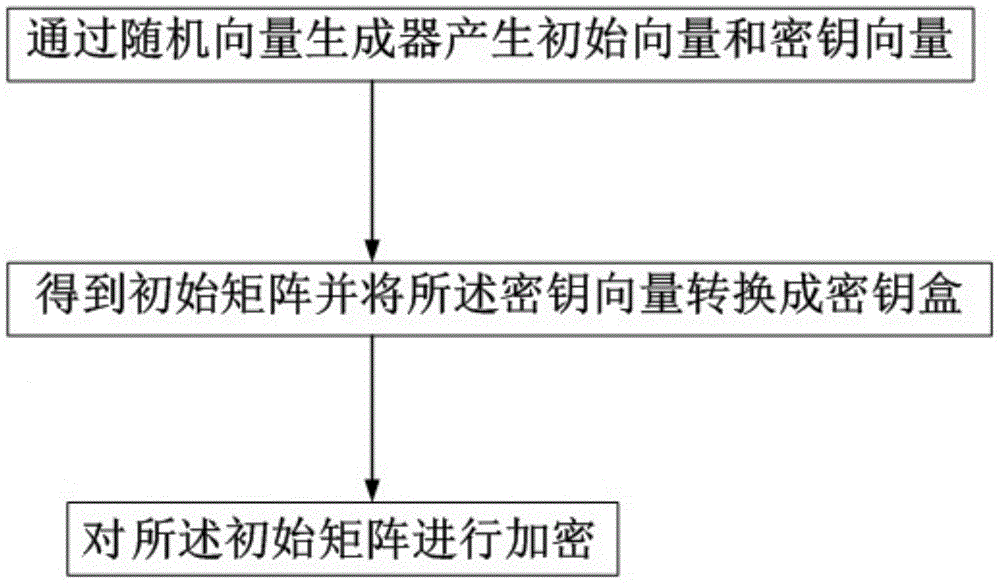
[0046] Embodiment one, such as figure 1 Shown, a kind of QR code encryption method comprises the following steps:
[0047] Step 1, generating an initial vector and a key vector by a random vector generator; both the initial vector and the key vector are 1×256 row vectors;
[0048] Step 2, the initial vector is cyclically filled with an m×m matrix to obtain an initial matrix C 0 , m is a positive integer; convert the key vector into a key box S 1 , S 2 , S 3 ......S j , where S j is a 1×16 vector, j∈[1,16];
[0049] Step 3, for the matrix C 0 Perform 2×m rounds of encryption to obtain the encryption matrix E, and the initial matrix C 0 Encryption proceeds as follows:
[0050]A0. Carry out the R round of encryption, and select the key box according to the current number of encryption rounds R, where the initial value of R is 1, and R≤2×m;
[0051] A1. Obtain matrix C sequentially R-1 The binary values of the upper, lower, left, and right elements of the element P to...
Embodiment 2
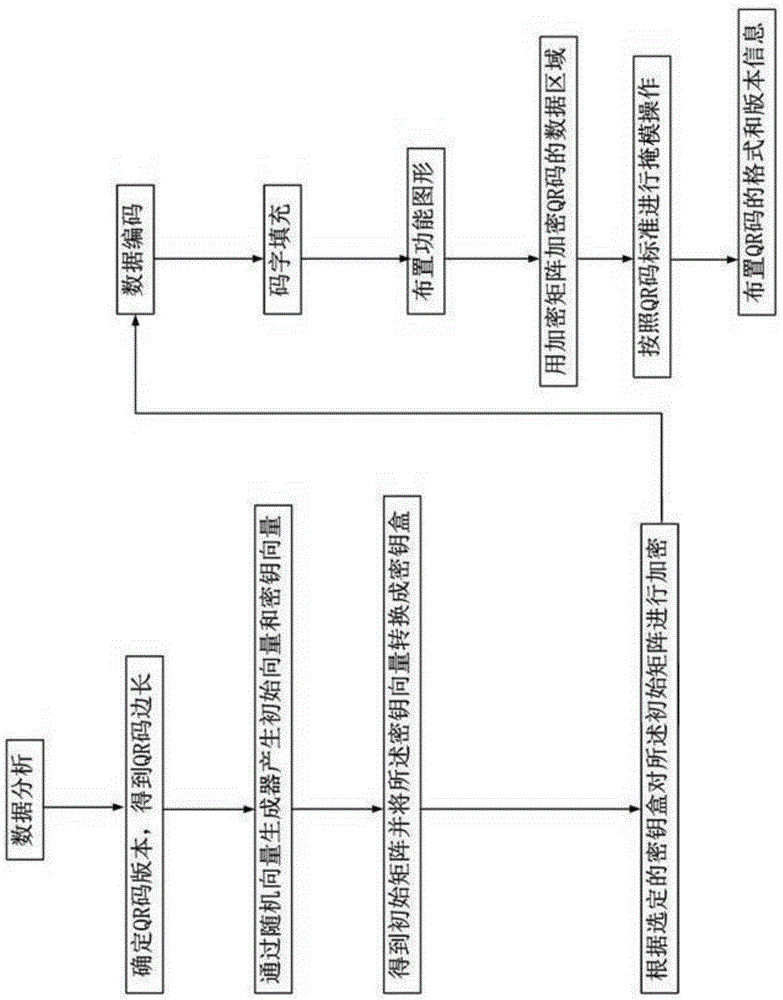
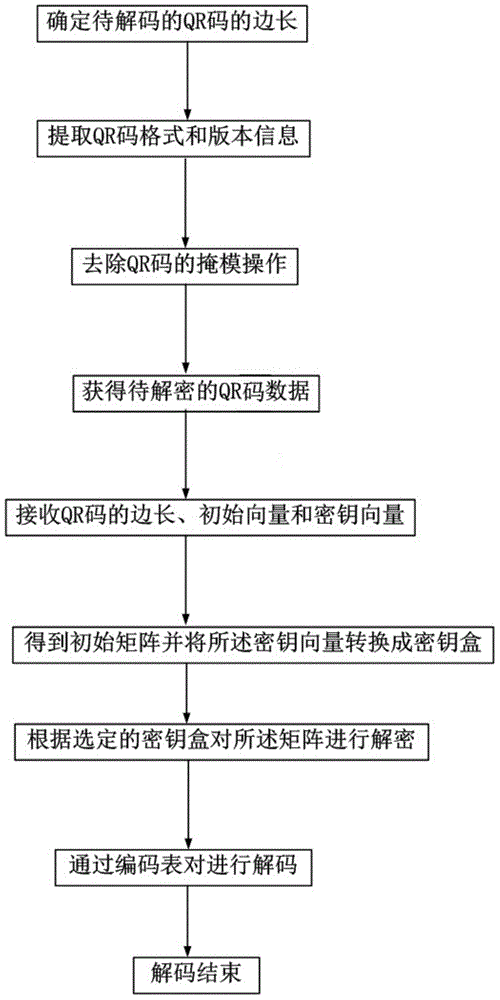
[0058] Embodiment two, such as figure 2 and image 3 As shown, the flow process of this embodiment is basically the same as that of Embodiment 1, the difference is that it also includes the steps of QR code generation and QR code decryption, and Embodiment 2 is executed according to the following steps:
[0059] S1. Data analysis;
[0060] S2. Determine the version of the QR code, and obtain the side length of the QR code;
[0061] S3. Generate an initial vector and a key vector by a random vector generator; both the initial vector and the key vector are 1×256 row vectors;
[0062] S4. The initial vector is cyclically filled with an m×m matrix to obtain an initial matrix C 0 , m is a positive integer; convert the key vector into a key box S 1 , S 2 , S 3 ......S j , where S j is a 1×16 vector, j∈[1,16];
[0063] S5, for the matrix C 0 Perform 2×m rounds of encryption to obtain the encryption matrix E, and the initial matrix C 0 Encryption proceeds as follows:
[0...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com