A Infinite Key Internet Communication Encryption Method
A technology of Internet communication and encryption method, applied in the field of Internet communication encryption, can solve the problem of insufficient security, and achieve the effect of simple encryption algorithm, high security, and small calculation amount
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
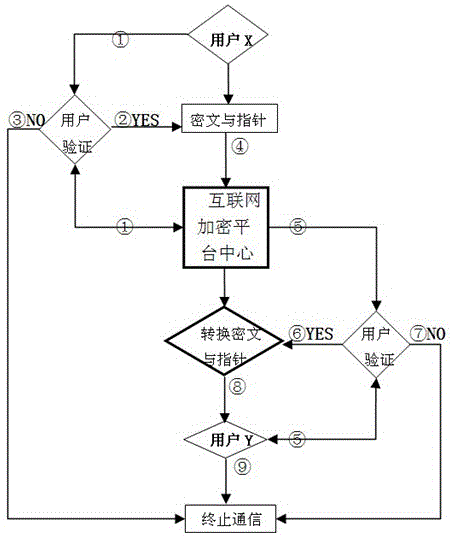
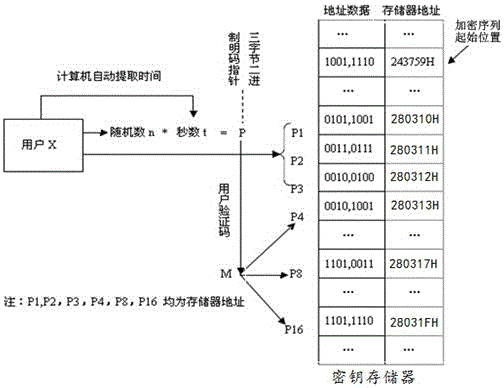
[0030] Embodiment: An infinite-length-key Internet communication encryption method in this embodiment is based on a system including a communication platform, at least one sender user, and at least one receiver user. The communication platform generates a unique unordered data sequence as a key for each user. The key has no arrangement rules but is large enough (16Mb). The communication platform sends the key to the corresponding user and saves a copy of the key.
[0031] Such as figure 1 As shown, the encryption method includes the following steps: 1. The communication platform issues a unique key to the user who needs encrypted communication, and the communication platform stores a copy of the exact same key;
[0032] 2. The sender user and the receiver user go to the communication platform for verification. If the verification passes, enter step 3. If the verification fails, the communication is terminated;
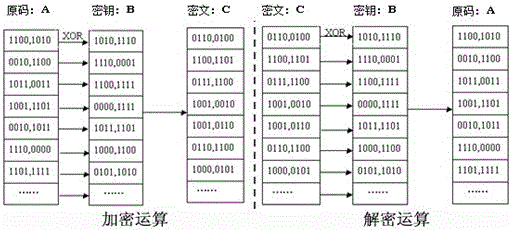
[0033] 3. The sender user uses a key to encrypt the original da...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com