Communication encryption method based on communication network
An encryption method and communication network technology, applied in the field of communication encryption, can solve the problems of low confidentiality of encrypted communication methods, communication eavesdropping, etc., and achieve the effects of convenient generation, flexible and simple negotiation, and high confidentiality.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
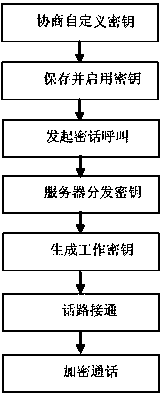
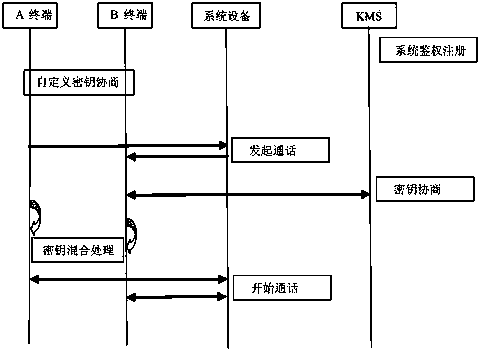
[0025] Embodiment one, see figure 1 As shown, this embodiment discloses a communication encryption method based on a communication network, comprising the following steps:
[0026] S1. Before performing encrypted communication, the terminal first completes the initialization of local data, and then the terminal performs system-side authentication and registration;
[0027] S2. Select a custom key mode, negotiate a custom key between terminals, and save the custom key in each terminal;
[0028] S3. Steps for enabling the terminal custom key, selecting to enable the negotiated custom key;
[0029] S4. Communication encryption steps:
[0030] S41. One terminal initiates an encrypted call request with an encryption type identifier to another terminal;
[0031] S42. According to the encrypted identification, if the called party terminal determines that the communication is encrypted with a custom key, find out the custom key enabled and stored in the local terminal, and use an a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com