Resource access control method
A control method and resource access technology, which is applied in the field of resource access control in B/S applications, can solve problems such as the contradiction between the granularity of permissions and the number of roles, the lack of a dynamic authorization mechanism, and the heavy workload of granting permissions to roles, etc., to achieve The effect of reducing the development burden, describing accurately and conveniently, and improving resource search efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
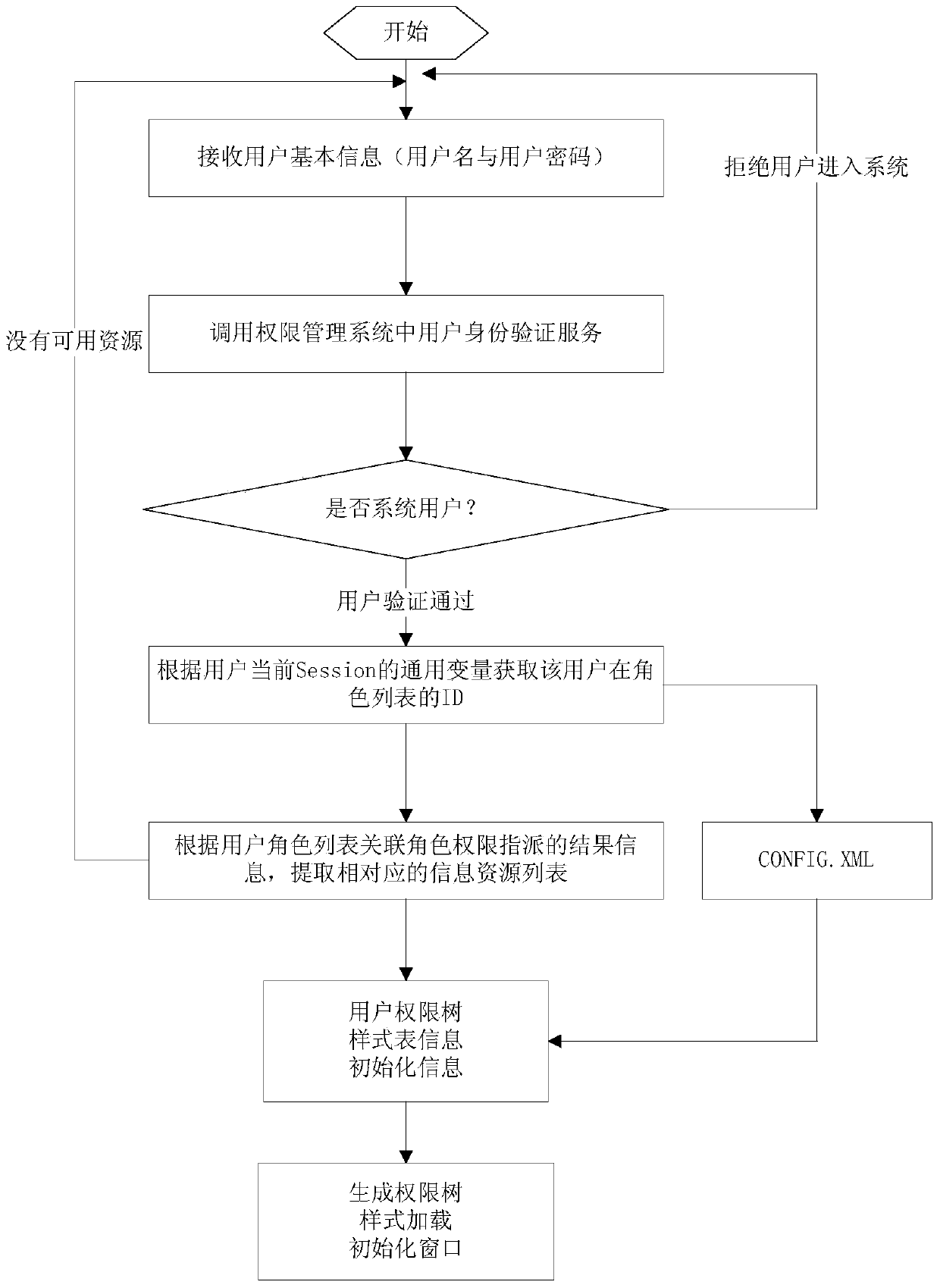
[0020] The present invention realizes centralized resource management and resource authorization more conveniently and swiftly by introducing the concepts of dynamic authority spanning tree and Linux kernel based on binary capability on the RBAC model.
[0021] In order to better understand the present invention, a basic introduction to the design idea of rights management is given below.
[0022] The RBAC (Role-based Access Control) model is currently the most widely used authority management model. This model has the characteristics of light management workload, flexible and simple, and strong scalability. It takes roles as the core and uses roles to decouple permissions and user relationships. The administrator assigns permissions to roles, and then assigns appropriate roles to users, so that users have resource permissions through the medium of roles. The present invention introduces a dynamic permission tree and the Linux kernel based on the concept of binary capabilit...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com