Malicious message cloud detection method and server
A server and cloud detection technology, applied in the communication field, can solve problems such as low coverage rate and slow response speed, and achieve the effect of improving processing speed
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
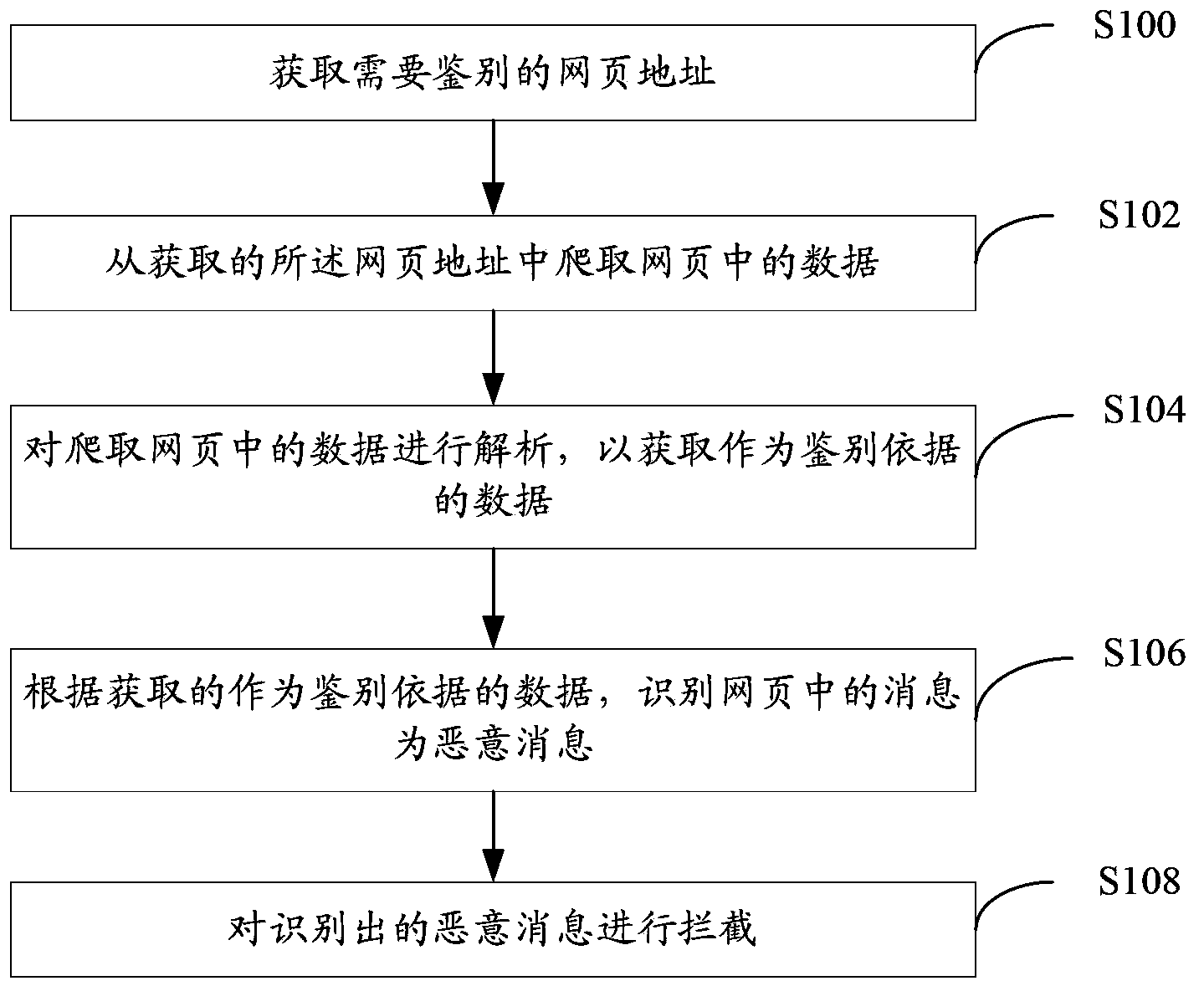
[0037] An embodiment of the present invention provides a method for detecting a malicious message cloud, wherein the malicious message in this embodiment may specifically be a malicious advertisement, but is not limited to the advertisement. Such as figure 1 As shown, the method includes:
[0038] Step S100, obtaining the address of the webpage that needs to be authenticated. Specifically, the web page address may be a Uniform Resource Locator (URL, Uniform / Universal Resource Locator). The server may receive the URL sent by other devices and needs to identify whether it is a malicious message, or obtain the address of the webpage in other ways. Usually, the server may acquire a lot of webpage addresses at the same time, so the method may preferably include prioritizing the acquired webpage addresses, and the server may subsequently perform priority identification processing on webpage addresses with high priority.
[0039] Step S102, crawling data in the webpage from the ac...
Embodiment 2
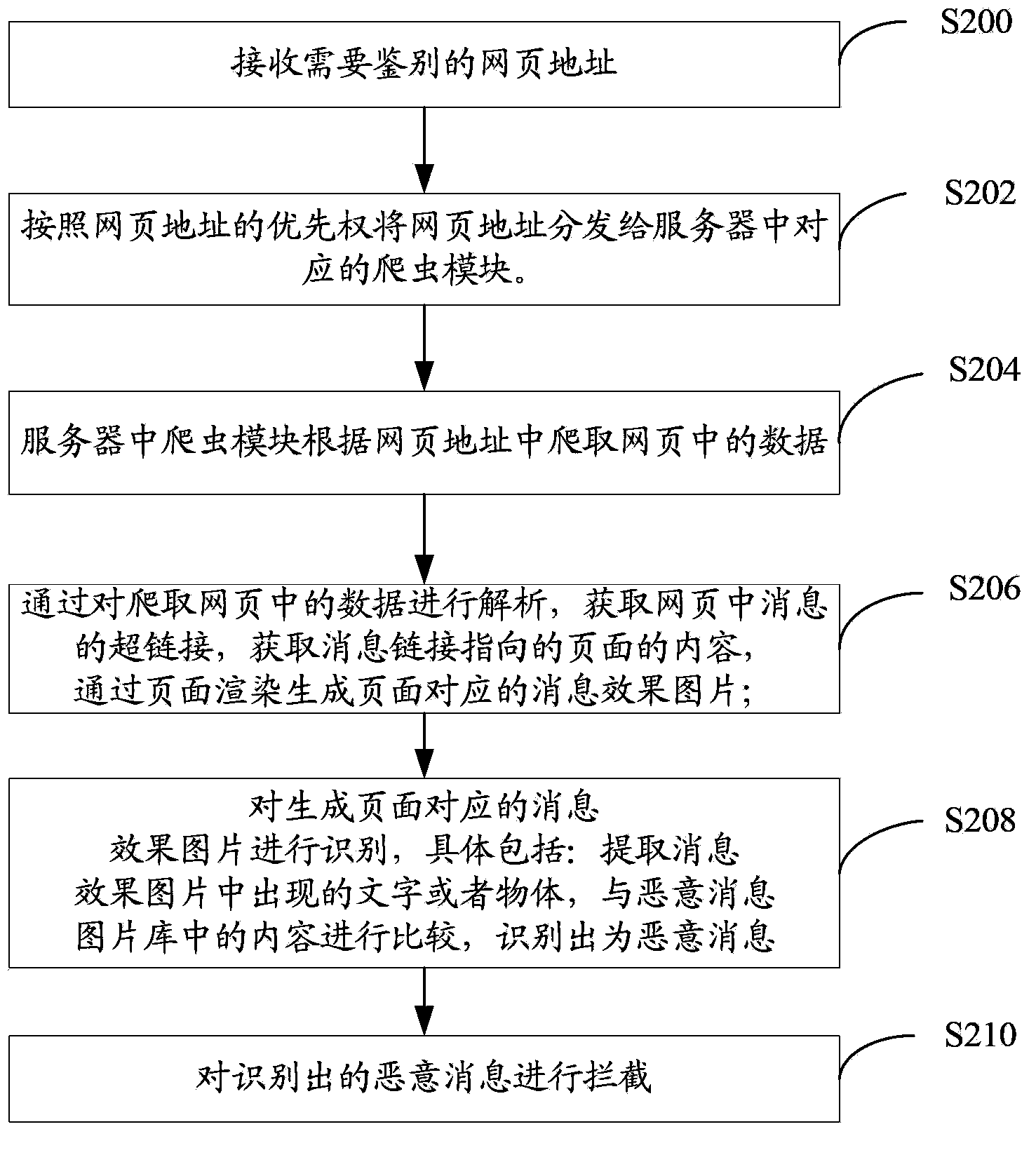
[0053] The embodiment of the present invention provides a malicious message cloud detection method, which is similar to the first embodiment and is based on the same inventive concept. The difference is that a specific method for identifying a message in a URL as malicious is described in this embodiment. The scheme of the message is easy to understand. Such as figure 2 As shown, the method includes:
[0054] Step S200, receiving the address of the webpage that needs to be identified (it can be specifically the receiving URL);
[0055] Step S202, distributing the webpage address to the corresponding crawler module in the server according to the priority of the webpage address. The server may include multiple crawler modules, and each crawler module may independently analyze data in the webpage.
[0056] Step S204, the crawler module in the server crawls the data in the webpage according to the address of the webpage. Among them, the data in the crawled web pages can at le...
Embodiment 3
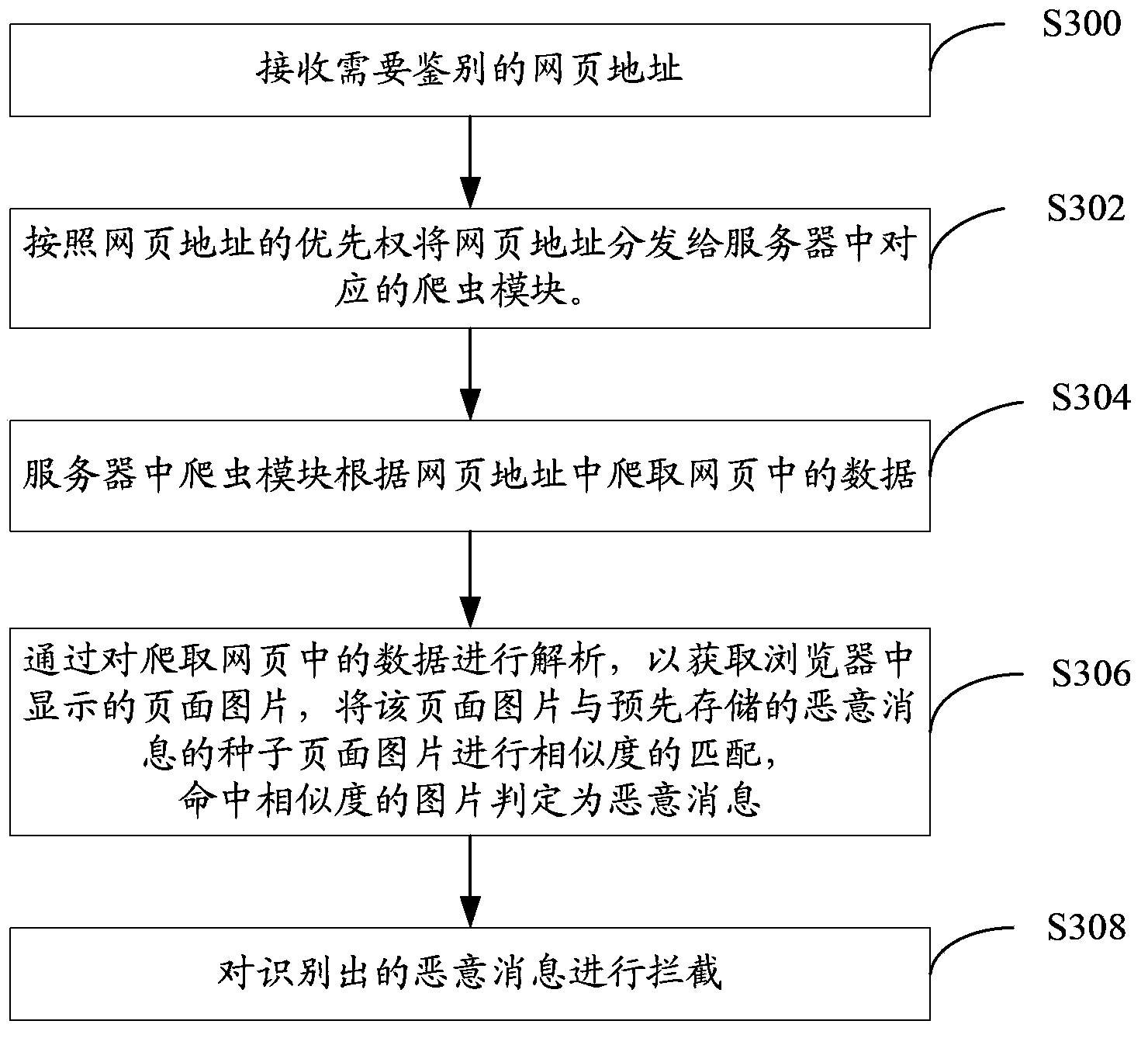
[0062] The embodiment of the present invention provides a malicious message cloud detection method. This method is similar to Embodiments 1 and 2 and is based on the same inventive concept. The difference is that another specific method for identifying URLs in the URL is described in this embodiment. Scenarios in which the message is malicious. Such as image 3 As shown, the method includes:
[0063] Step S300, receiving the address of the web page that needs to be identified (it can be specifically the receiving URL);
[0064] Step S302, distributing the webpage address to the corresponding crawler module in the server according to the priority of the webpage address. The server may include multiple crawler modules, and each crawler module may independently analyze data in the webpage.
[0065] Step S304, the crawler module in the server crawls the data in the webpage according to the address of the webpage. Among them, the data in the crawled web pages can at least inclu...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com