A Remote Authentication Protocol Method Based on Password
A technology of remote authentication and protocol, applied in the field of password-based remote authentication protocol, it can solve problems such as hidden dangers, unstoppable favor, small data volume, etc., and achieve the effect of resisting replay attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
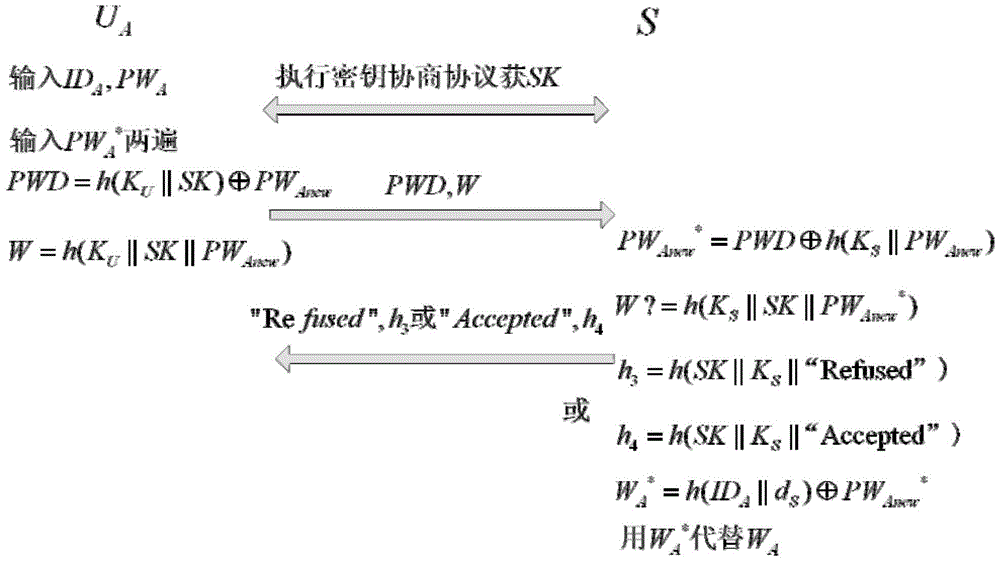
[0037] The present invention is realized based on the elliptic curve cryptographic algorithm. In the system initialization sub-protocol, the user negotiates with the server the parameters of the elliptic curve cryptographic system that need to be used for authentication;
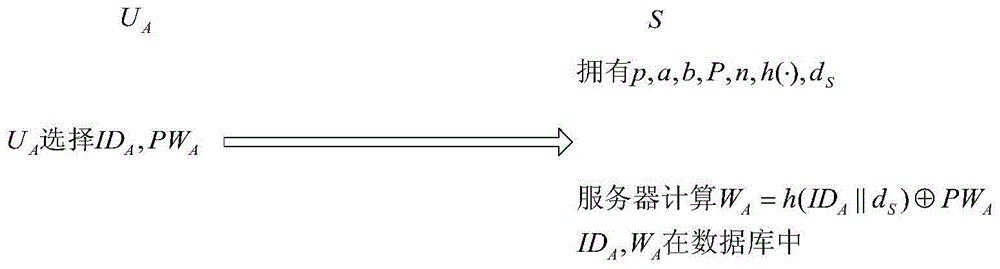
[0038] (1) User registration sub-agreement:
[0039] At the time of initial registration, by user U A Choose your own identity and user password PW A , and then submitted to the server S in a secure manner;
[0040] Server S receives new user U A The ID submitted by the registration A and user password PW A ; later, calculate Then put the data (ID A ,W A ) is saved in the authentication database of the server, in the above formula, d S Indicates the private key of the server, and h indicates the one-way hash function.
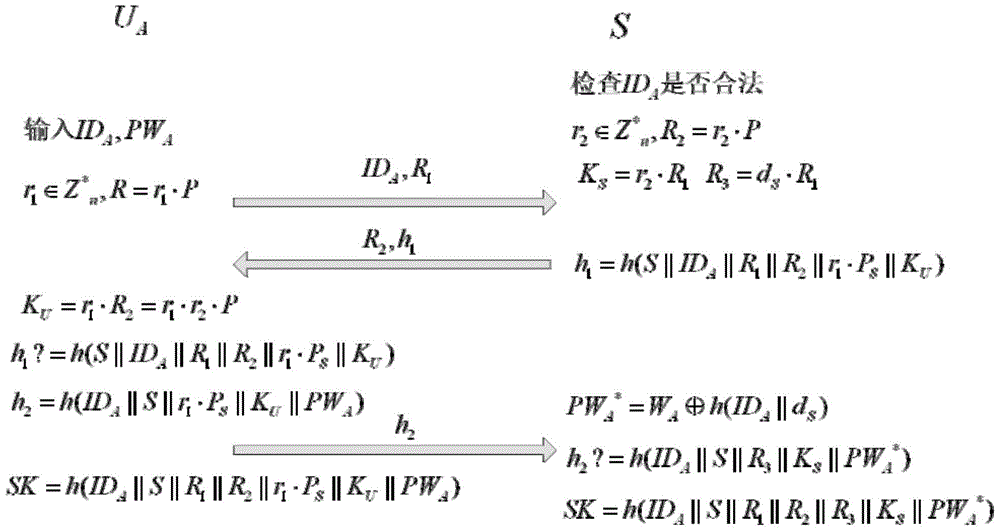
[0041] (2) Authentication and key agreement sub-protocol:
[0042] 1) User U A First enter your ID A and user password PW A ; The user freely chooses a random number r 1 ,r 1 ...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap