An access method, device and system
An access method and a technology of an access device, applied in the field of communication, can solve problems such as network congestion, and achieve the effect of avoiding network congestion
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0076] This embodiment will be described from the perspective of a second network node. The second network node may be a user terminal, which may support CA, and may communicate with one site or communicate with two or more sites at the same time.
[0077] An embodiment of the present invention provides an access method, including:
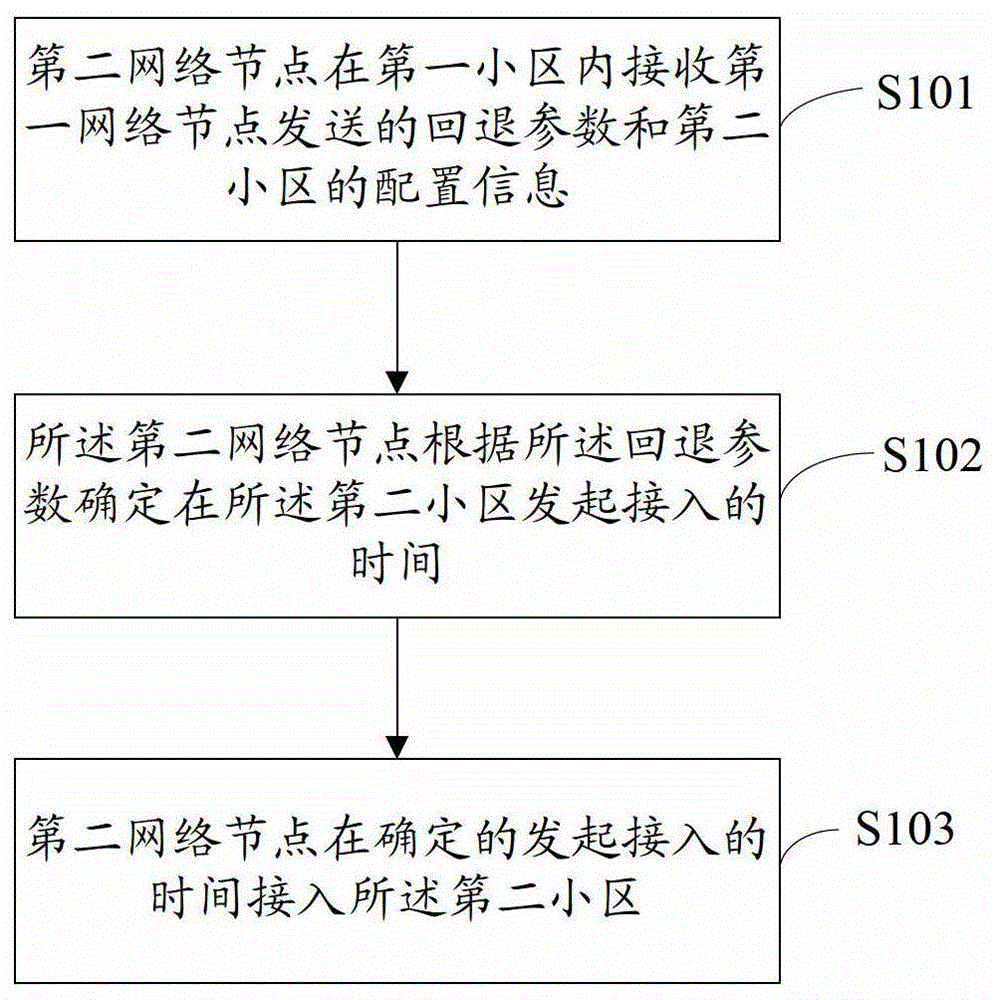
[0078] The second network node receives the fallback parameter sent by the first network node and the configuration information of the second cell in the first cell;
[0079] The second network node determines the time to initiate access in the second cell according to the fallback parameter, and accesses the second cell at the determined time to initiate access.
[0080] It should be noted that the above-mentioned first network node may specifically be an evolved base station (evolved Node B, referred to as eNB), or a mobile base station (Node B, referred to as NB), or a control base station (Donor eNB, referred to as DeNB), or a home base statio...
Embodiment 2
[0116] This embodiment will be described from the perspective of the first network node.
[0117] An embodiment of the present invention provides another access method, including:
[0118] The first network node sends the fallback parameter and the configuration information of the second cell to the second network node in the first cell, so that the second network node determines the time to initiate access to the second cell according to the fallback parameter, and access the second cell at the determined time for initiating access.
[0119] The configuration information of the second cell includes at least one of the following: the operating frequency of the carrier corresponding to the second cell, the random access time-frequency resource of the carrier corresponding to the second cell, and the time-frequency resource of the carrier corresponding to the second cell. bandwidth;
[0120] Wherein, the first network node may put the fallback parameter and the configuration i...
Embodiment 3
[0134] This embodiment provides another access method, including:
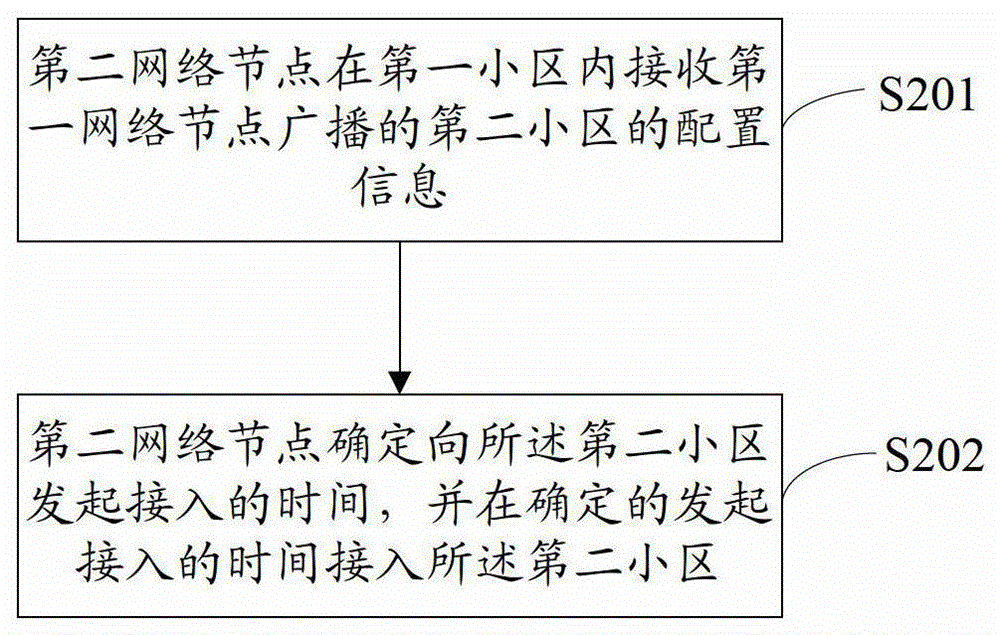
[0135] The second network node receives the configuration information of the second cell broadcast by the first network node in the first cell; in each embodiment of the present invention, it is described in the form of broadcast, of course the second network node receives the configuration information of the second cell in the first cell The configuration information of the second cell sent by a network node may also be a dedicated message sent by the first network node to the second network node, which is not limited here. Various embodiments of the present invention will not be described repeatedly.
[0136] The second network node determines the time to initiate access to the second cell, and accesses the second cell at the determined time to initiate access.
[0137] Embodiment 3 is different from Embodiment 1 and Embodiment 2 in that what the second network node receives is a broadcast message from the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com