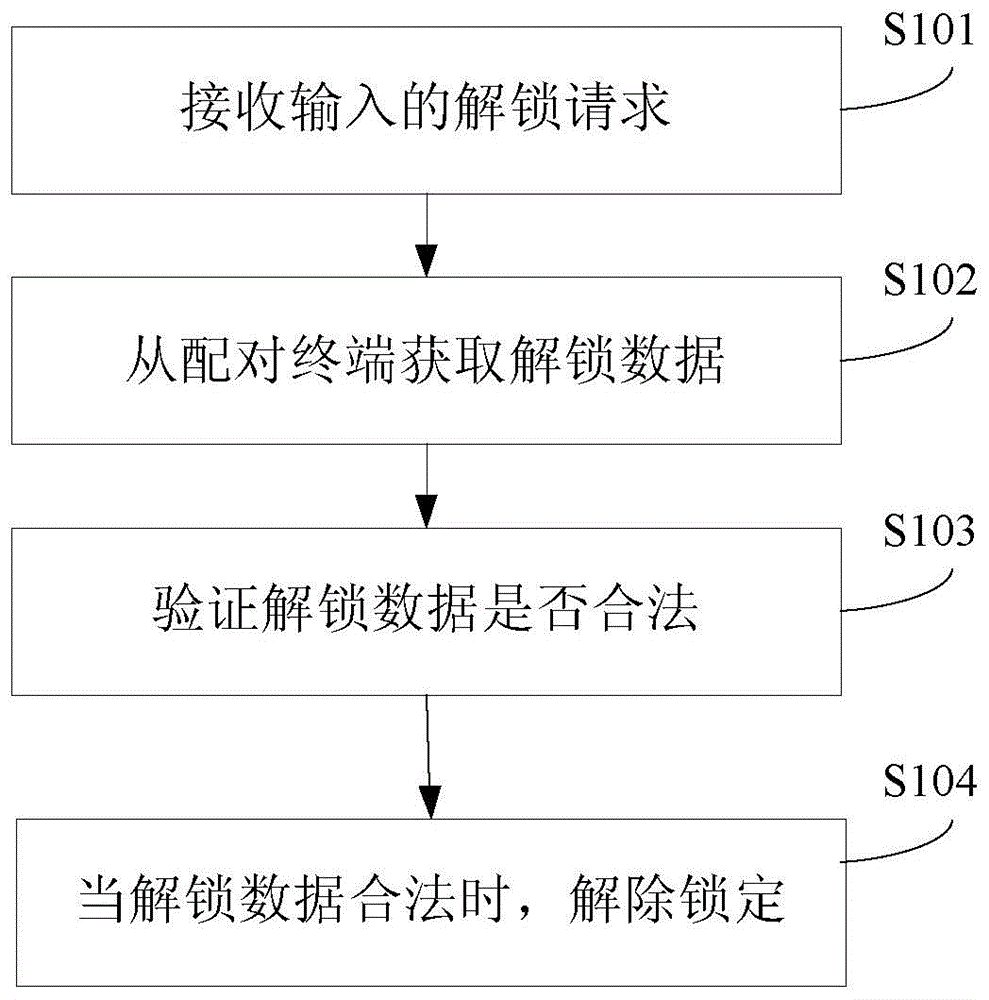
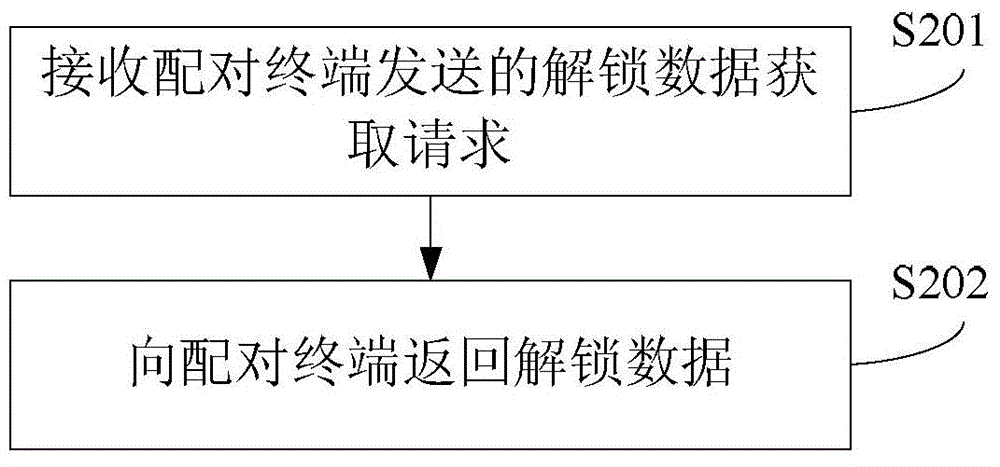
Unlocking method and device
An unlocking and unlocking technology, applied in the direction of telephone communication, nan, electrical components, etc., can solve problems such as damaging user experience, cumbersome user operations, and inability to unlock, so as to improve user experience, ensure safe unlocking, and simplify user operations.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
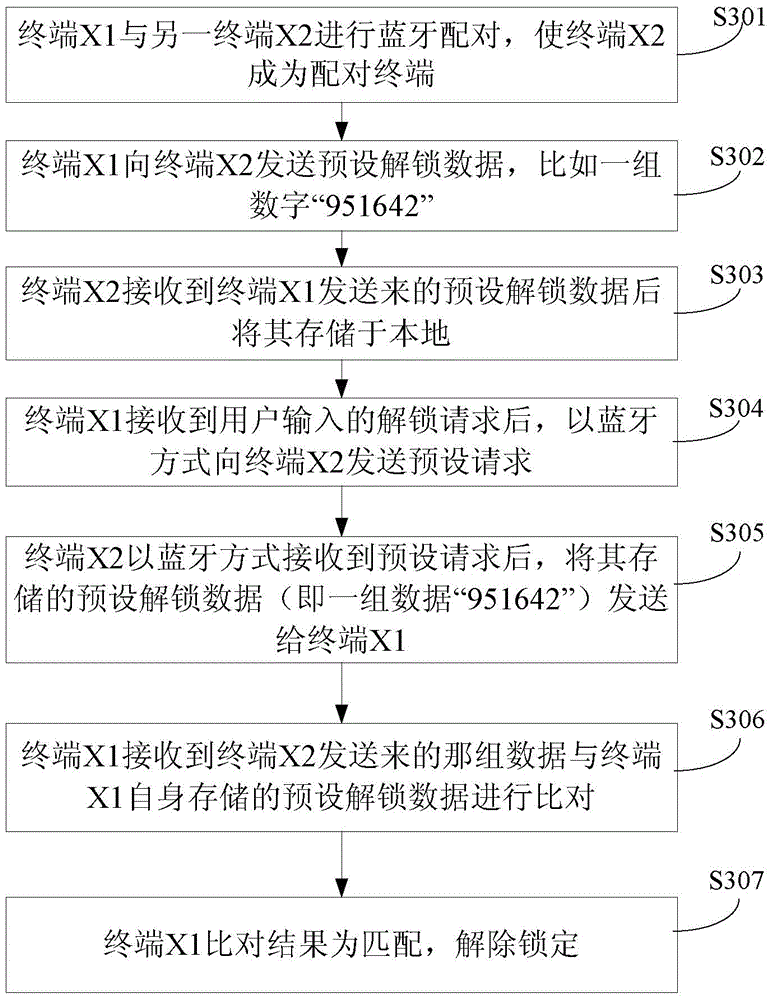
[0113] In Embodiment 1, the unlocking data is implemented as preset unlocking data sent by the terminal to the paired terminal in advance, and the communication method between the terminal and the paired terminal is implemented as a Bluetooth method, such as image 3 Shown, embodiment one comprises the following steps:
[0114] In step S301, the terminal X1 performs Bluetooth pairing with another terminal X2, so that the terminal X2 becomes a paired terminal.
[0115] In step S302, the terminal X1 sends preset unlocking data to the terminal X2, such as a set of numbers "951642".
[0116] In step S303, the terminal X2 stores the preset unlocking data locally after receiving the preset unlocking data sent by the terminal X1.
[0117] In step S304, after receiving the unlocking request input by the user, the terminal X1 sends a preset request to the terminal X2 via Bluetooth.
[0118] In step S305, after receiving the preset request via Bluetooth, the terminal X2 sends the stor...
Embodiment 2
[0124] In Embodiment 2, the unlocking data is implemented as encrypted unlocking data generated by the paired terminal using a key to encrypt random numbers, and the communication method between the terminal and the paired terminal is implemented as a mobile network communication method, such as Figure 4 As shown, embodiment two comprises the following steps:
[0125] In step S401, the terminal X3 performs a pairing and binding operation with another terminal X4, so that the terminal X4 becomes a paired terminal.
[0126] In step S402, the terminal X3 sends the key to the terminal X4.
[0127] In step S403, the terminal X4 stores the key locally after receiving the key sent by the terminal X3.
[0128] In step S404, after receiving the unlocking request input by the user, the terminal X3 generates a random number such as "88", and sends the random number to the terminal X4 through mobile network communication.
[0129] In step S405, after terminal X4 receives the random num...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com