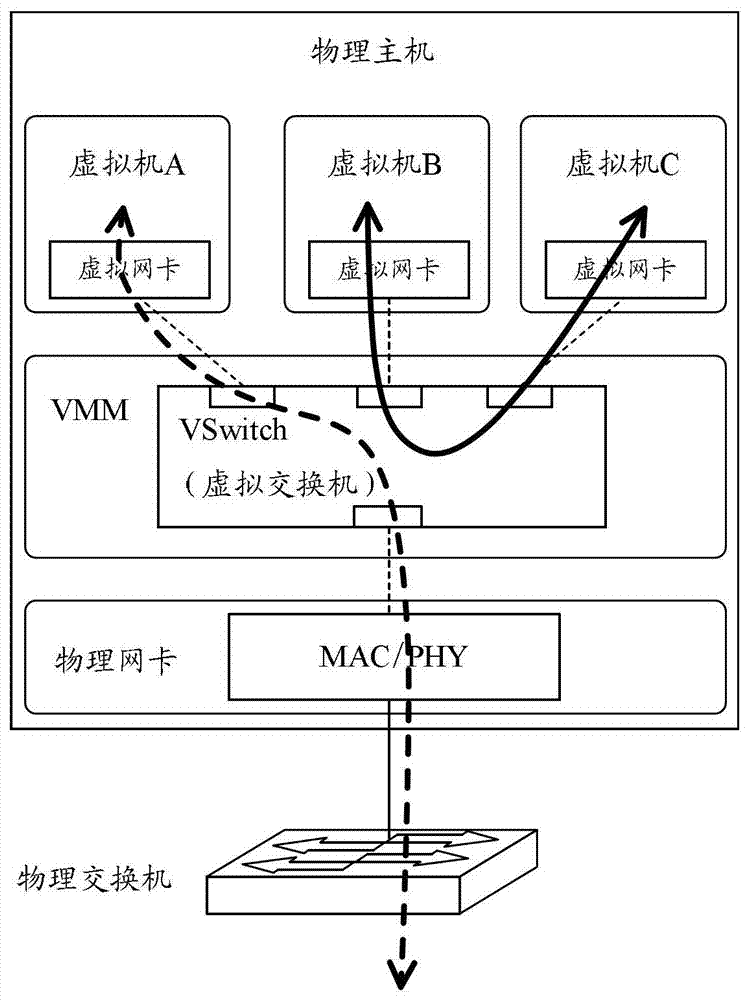
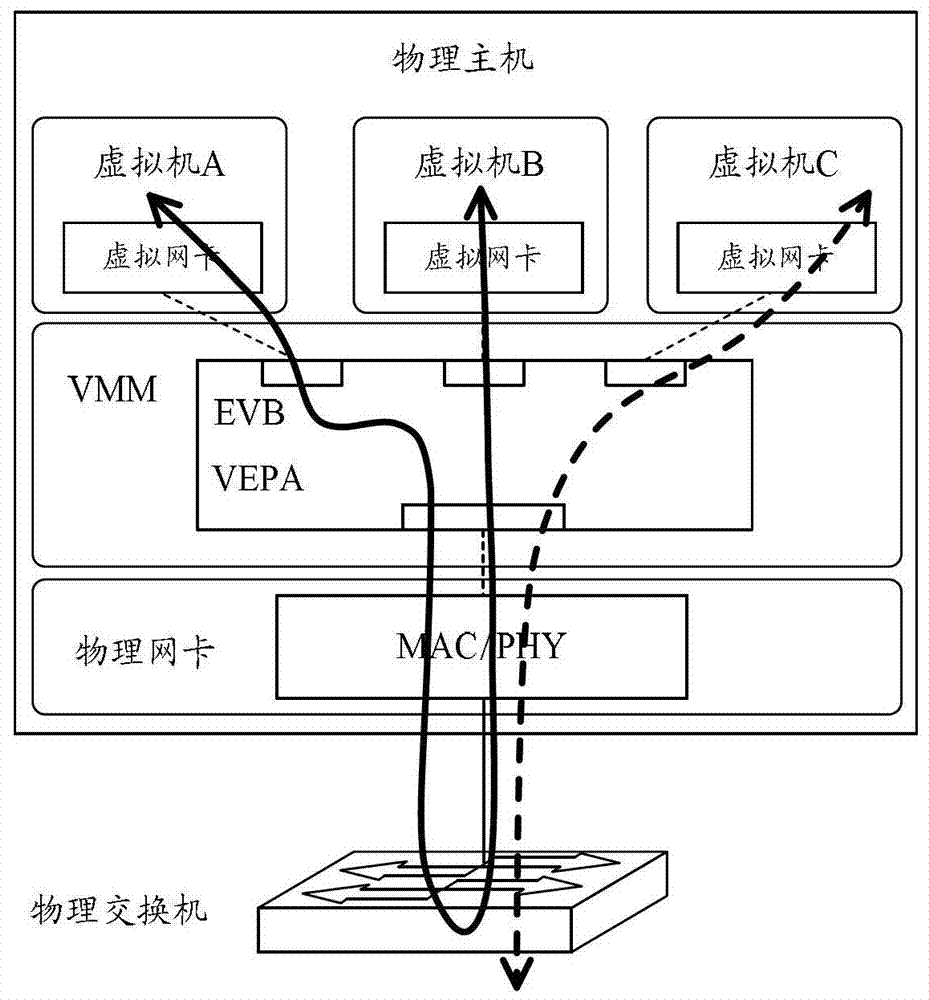
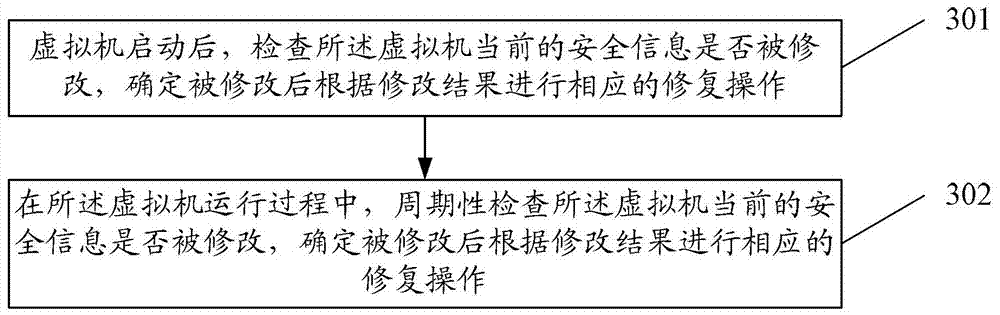
A detection method and device for network security in a cloud computing network
A cloud computing network and network security technology, applied in the field of cloud computing, can solve problems such as attack, threat VMM, virtual machine infection virus, etc., to achieve the effect of ensuring security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0071] The detection method of network security in the cloud computing network of this embodiment, such as Figure 4 shown, including the following steps:
[0072] Step 401: When it is necessary to apply for a virtual machine, the user sends a service request to the cloud computing operation management platform through the self-service portal of the cloud computing operation management platform;
[0073] Step 402: the cloud computing operation and management platform receives the service request and, after reviewing the received service request, issues an instruction to allocate resources to the resource pool management platform through the management interface;
[0074] Step 403: After receiving the instruction, the resource pool management platform allocates a corresponding virtual machine to the user;
[0075] Here, the specific implementation of steps 401-403 is the prior art, and will not be repeated here.
[0076] Steps 404-405: The resource pool management platform tr...
Embodiment 2
[0107] The detection method of network security in cloud computing in this embodiment, such as Figure 5 shown, including the following steps:
[0108] Step 501: When it is necessary to apply for a virtual machine, the user sends a service request to the cloud computing operation management platform through the self-service portal of the cloud computing operation management platform;
[0109] Step 502: the cloud computing operation and management platform receives the service request and, after reviewing the received service request, issues an instruction to allocate resources to the resource pool management platform through the management interface;
[0110] Step 503: After receiving the instruction, the resource pool management platform allocates a corresponding virtual machine to the user;
[0111] Here, the specific implementation of steps 501-503 is the prior art, and will not be repeated here.
[0112] Steps 504-505: the resource pool management platform triggers the c...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com