Mobile terminal and junk information effectively filtering method and device thereof
A spam and spam technology, applied in special data processing applications, instruments, electrical digital data processing, etc., can solve problems such as unrecognizable spam keywords
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
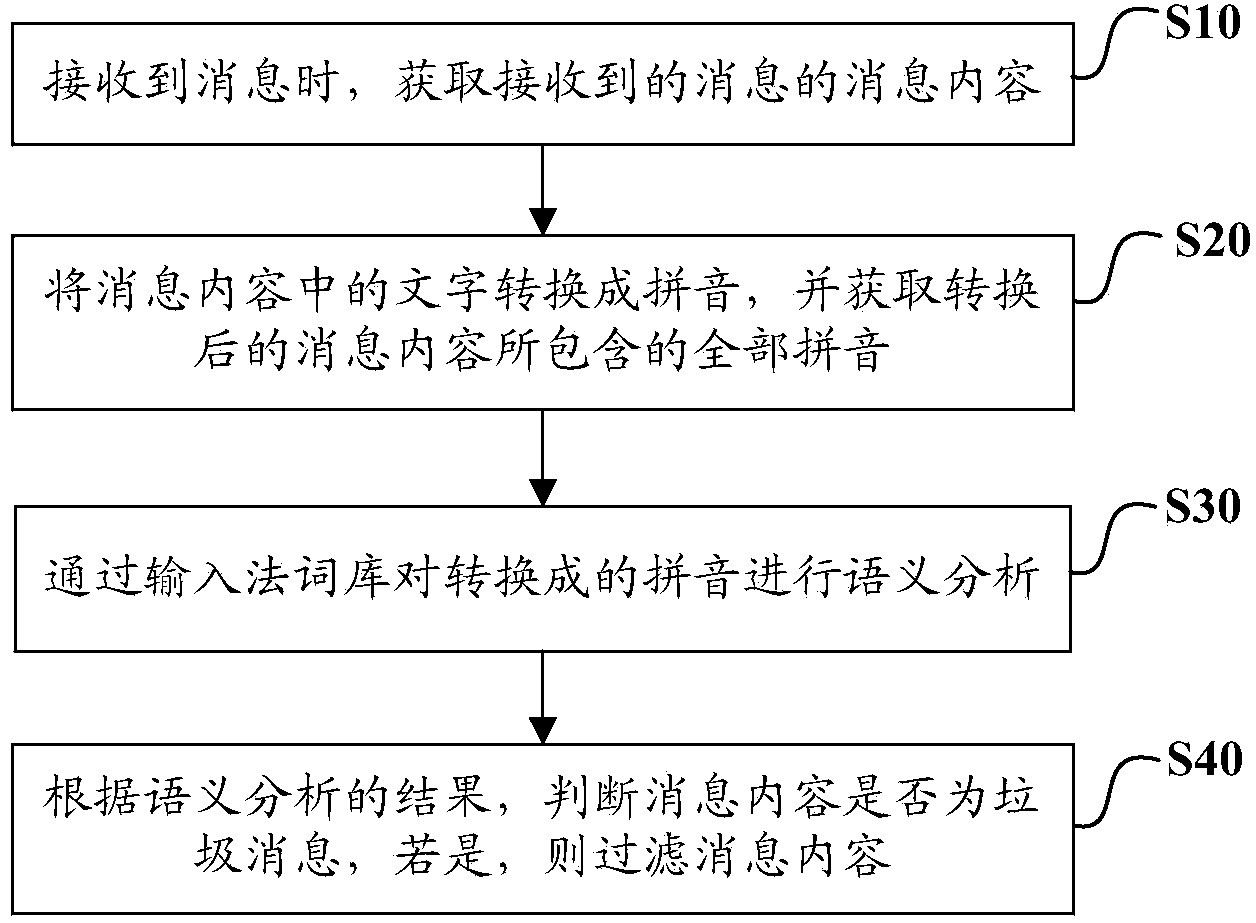
[0026] figure 1 It is a flow chart of a method for effectively filtering junk information according to an embodiment of the present invention, combined below figure 1 To describe a method for effectively filtering junk information according to an embodiment of the present invention, such as figure 1 As shown, in order to prevent spam pushers from editing part of the text in the message into pinyin to avoid identification of spam keywords, the method includes the following steps:
[0027] S10. When a message is received, acquire the message content of the received message;
[0028] S20. Convert the text in the message content into pinyin, and obtain all the pinyin included in the converted message content;
[0029] S30. Perform semantic analysis on the converted pinyin through the input method lexicon;
[0030] S40. According to the result of the semantic analysis, determine whether the message content is spam, if so, filter the message content, otherwise, display the messag...
Embodiment 2
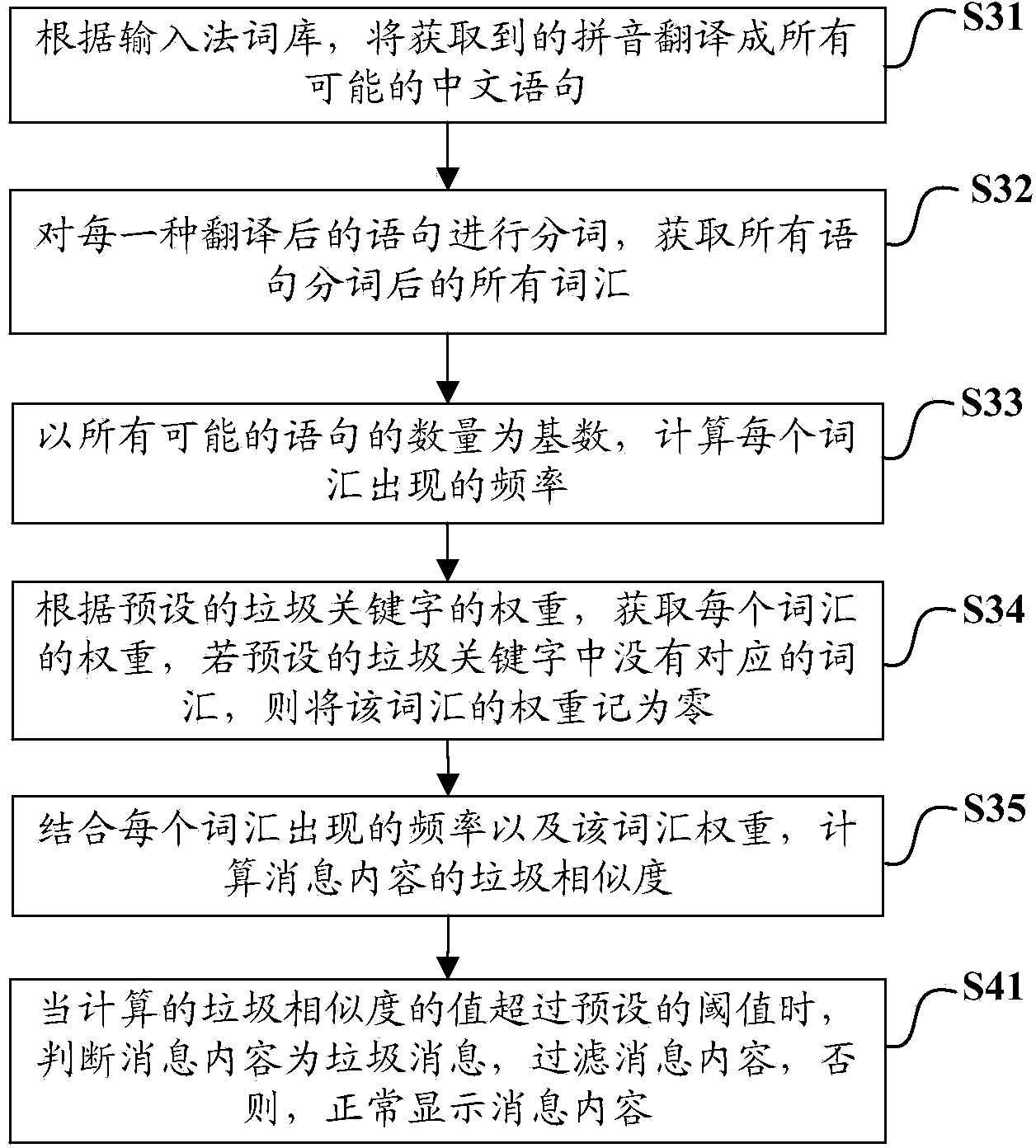
[0040] figure 2 It is a flowchart of a semantic analysis method according to an embodiment of the present invention, such as figure 2 As shown, the present invention includes the above step S10 and step S20, and the above step S30 specifically includes:
[0041] S31. Translate the acquired pinyin into all possible Chinese sentences according to the input method lexicon;
[0042] S32. Carry out word segmentation for each translated sentence, and obtain all vocabulary after word segmentation of all sentences;
[0043] S33. Based on the number of all possible sentences, calculate the occurrence frequency of each vocabulary;
[0044] S34. Obtain the weight of each vocabulary according to the weight of the preset junk keywords, and record the weight of the vocabulary as zero if there is no corresponding vocabulary in the preset junk keywords;
[0045] S35. Combining the occurrence frequency of each word and the weight of the word, calculate the spam similarity of the message c...
Embodiment 3
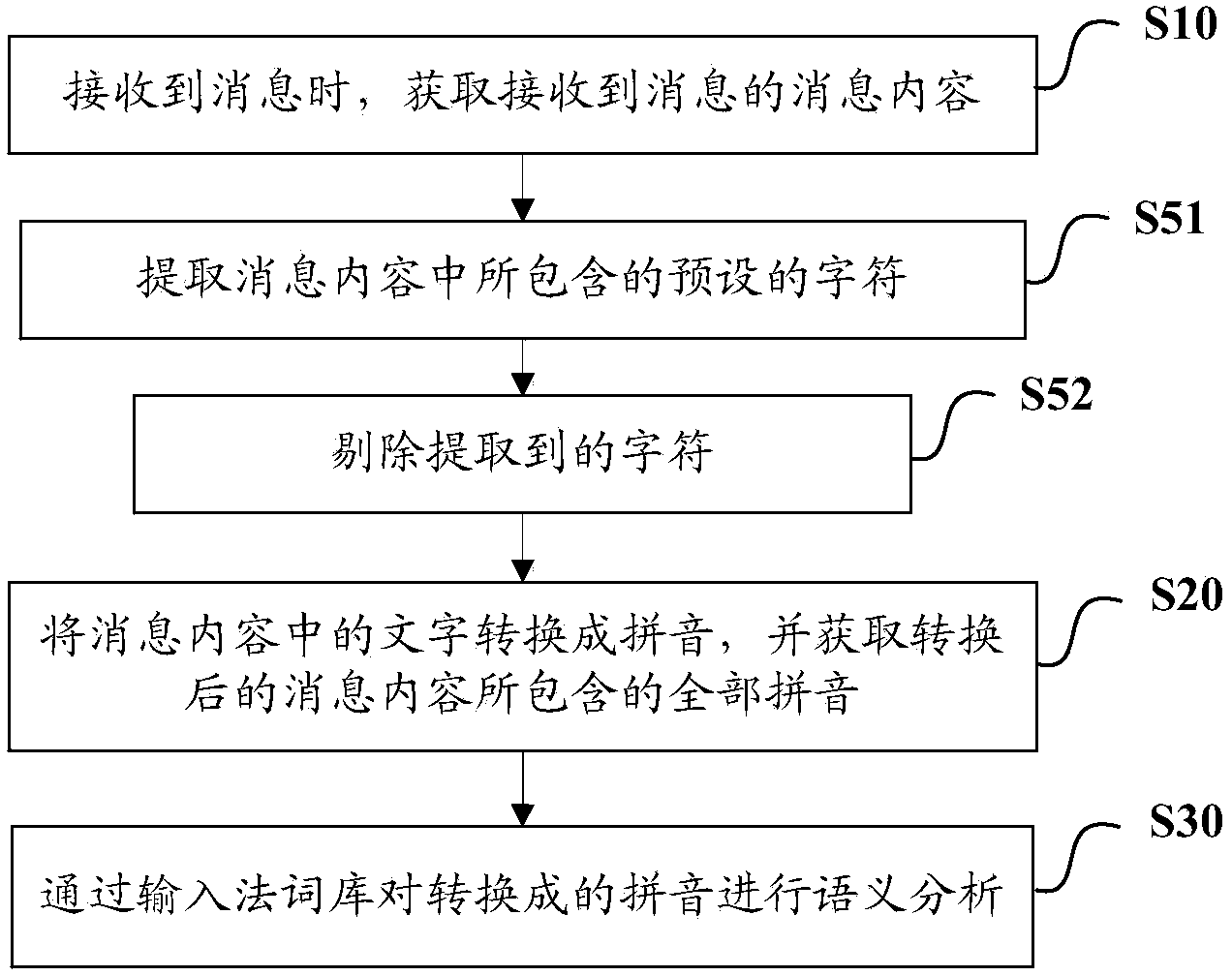
[0054] image 3 It is a flowchart of a method for removing special characters according to an embodiment of the present invention, such as image 3 As shown, in order to avoid that spam keywords are not identified due to inserting special characters when spammers edit messages, the present invention includes above-mentioned step S10, step S20, step S30, and step S40 (step S40 is in image 3 not shown), also includes:
[0055] S51. Extract preset characters included in the message content;
[0056] S52. Eliminate the extracted characters.
[0057] As an option, the above steps S51 and S52 may be between step S10 and step S20 as shown in the figure, or steps S51 and S52 may be placed between step S20 and step S30.
[0058] Wherein, the above preset characters include but not limited to special characters such as space, ",", "*", "#".
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com