Login method and device based on terminal identification
A technology of terminal identification and login method, which is applied in the field of login methods and devices based on terminal identification, can solve the problems of wasting user time, reducing user experience, increasing user operation complexity, etc., so as to save time and reduce operation complexity. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
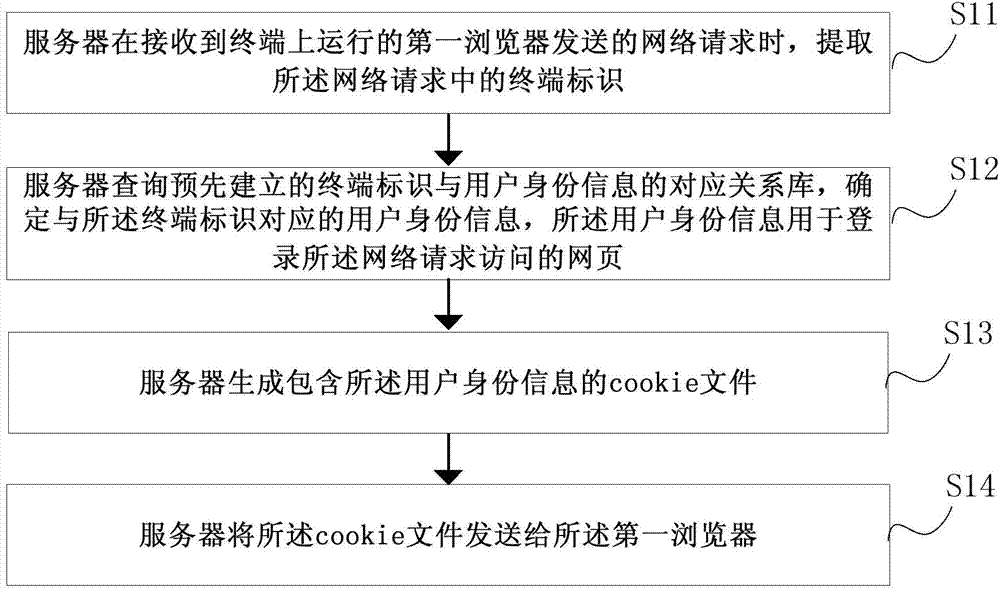
[0074] figure 1 It is a flow chart of a login method based on terminal identification shown according to an exemplary embodiment, as shown in figure 1 as shown, figure 1 The terminal identification-based login method shown can be used in terminals. The terminal identification-based login method provided by the present disclosure can enable users to automatically log in without re-entering identity information when switching web browsers to access websites with identity verification, thereby saving users' time and reducing operational complexity. Improve user experience. The method includes the following steps.
[0075] In step S11, when the server receives the network request sent by the first browser running on the terminal, it extracts the terminal identifier in the network request.
[0076] Wherein, the method provided by the present disclosure can be applied in the server of the website. The user can open the first browser on the terminal, and input the website addres...
Embodiment 2
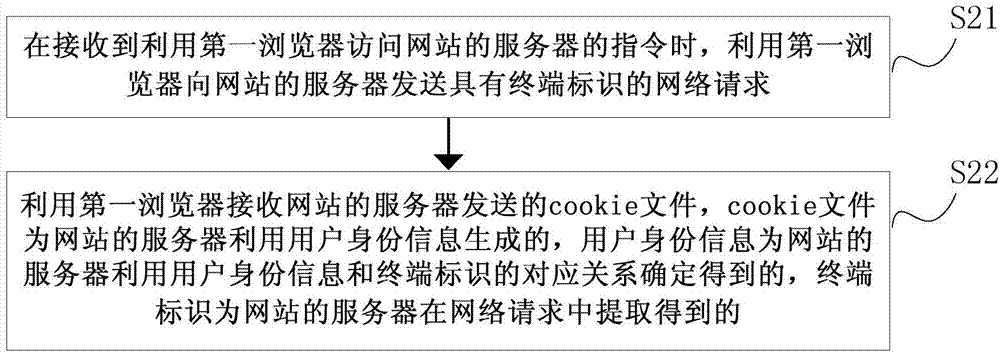
[0099] figure 2 is a flow chart of another login method based on terminal identification shown according to an exemplary embodiment, as shown in figure 2 as shown, figure 2 The terminal identification-based login method shown can be used in a terminal, and figure 2 The method shown with figure 1 The methods shown can be used in conjunction with each other. The terminal identification-based login method provided by the present disclosure can enable users to automatically log in without re-entering identity information when switching web browsers to access websites with identity verification, thereby saving users' time and reducing operational complexity. Improve user experience. The method includes the following steps.
[0100] In step S21, when receiving an instruction to access the server of the website by using the first browser, send a network request with a terminal identifier to the server of the website by using the first browser.
[0101] Wherein, the method pro...
Embodiment 3
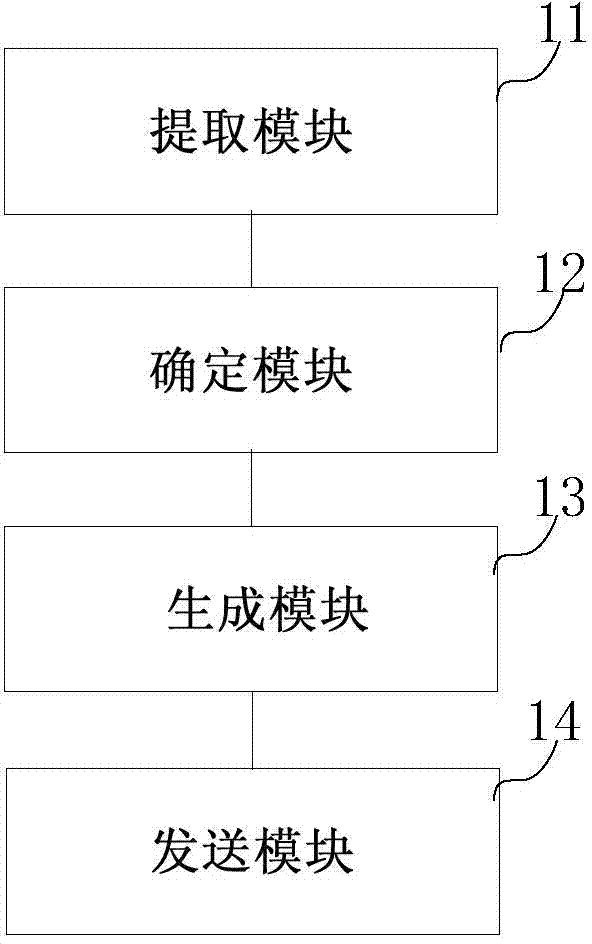
[0105] image 3 It is a schematic diagram of a terminal identification-based login device according to an exemplary embodiment. The terminal identification-based login device provided by the present disclosure can enable users to automatically log in without re-entering identity information when switching web browsers to access websites with identity verification, thereby saving users' time and reducing operational complexity. Improve user experience. refer to image 3 , the device includes an extracting module 11 , a determining module 12 , a generating module 13 and a sending module 14 . in:
[0106] An extracting module 11, configured to extract the terminal identifier in the network request when receiving the network request sent by the first browser running on the terminal;
[0107] The determining module 12 is configured to query a pre-established library of correspondence between terminal identifiers and user identity information, and determine the user identity inf...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com