Security information interaction method based on customizable browser
A technology of security information and interactive methods, applied in data exchange networks, digital transmission systems, electrical components, etc., can solve problems such as inconvenient use, hidden safety hazards, and high costs, and achieve the effects of convenient use, enhanced security, and low cost
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
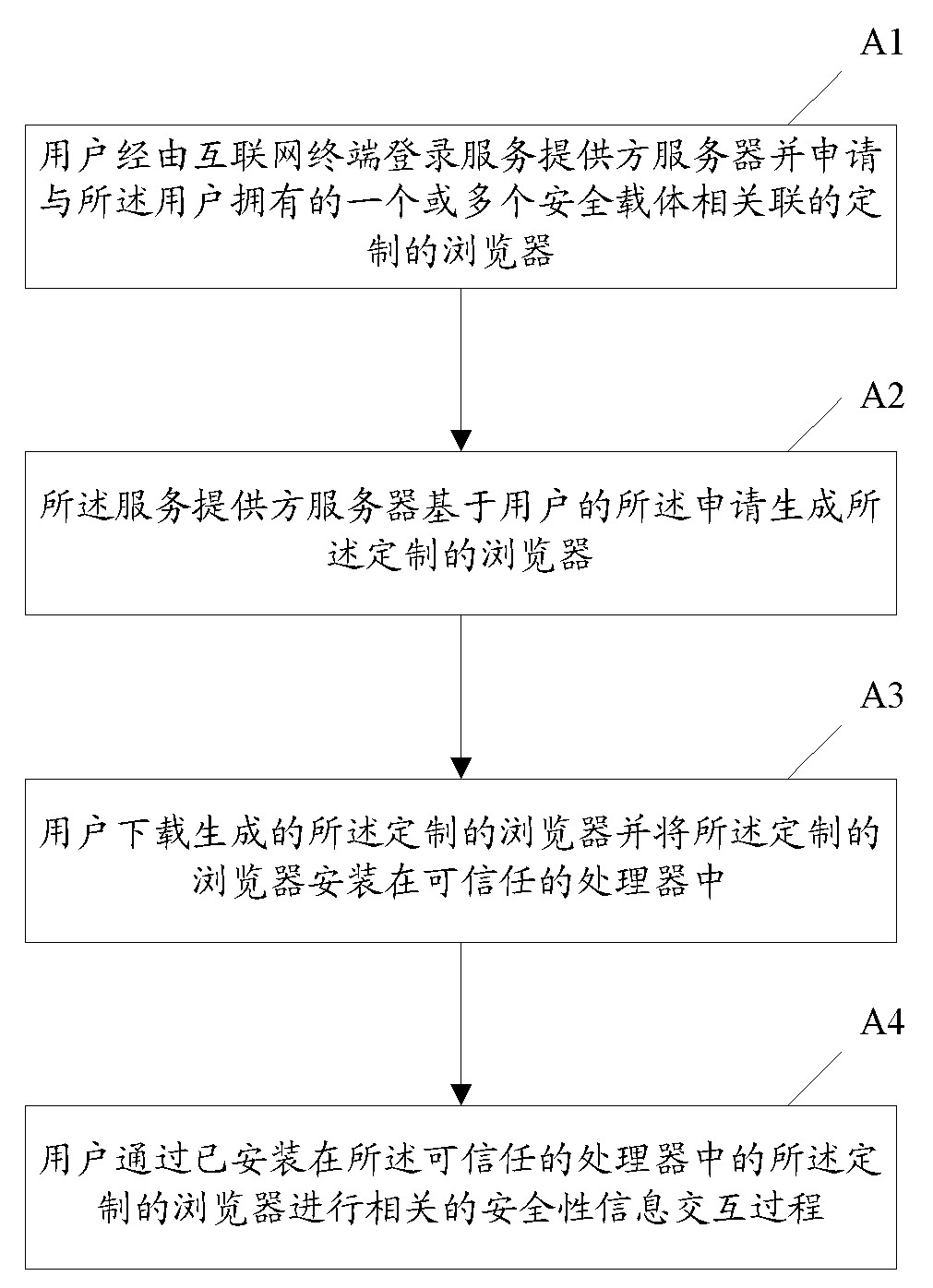
[0020] figure 1 It is a flow chart of a customizable browser-based security information interaction method according to an embodiment of the present invention. like figure 1 As shown, the customizable browser-based security information interaction method disclosed in the present invention includes the following steps: (A1) The user logs in to the server of the service provider via an Internet terminal (such as a computer as a network node, a mobile terminal, etc.) and Apply for a customized browser associated with one or more security carriers (such as financial IC cards) owned by the user; (A2) the service provider server generates the customized browser based on the user's application; (A3) The user downloads the generated customized browser and installs the customized browser in a trusted processor; (A4) The user passes the customized browser installed in the trusted processor to The browser performs related security information interaction process (such as payment transa...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com