Patents
Literature
32results about How to "Avoid the risk of being leaked" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
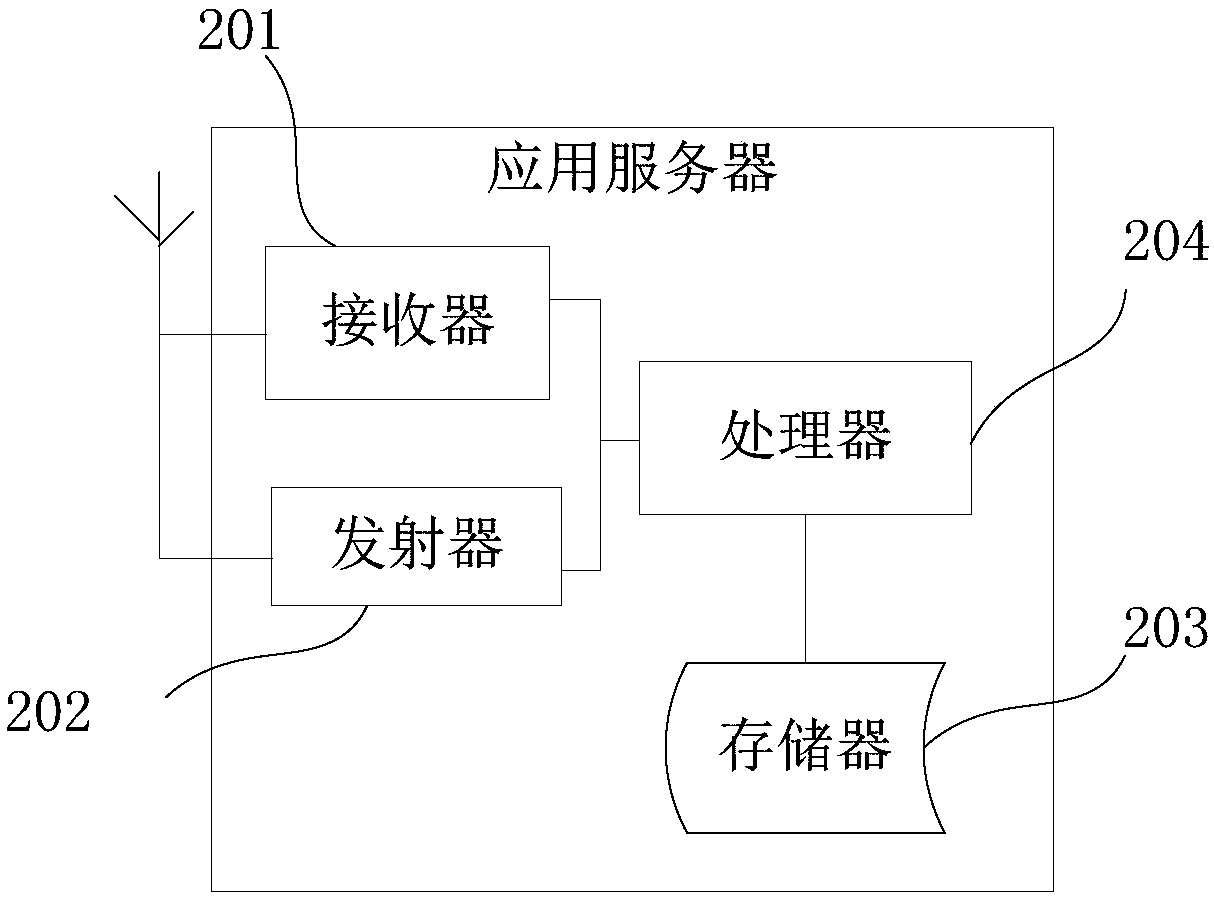
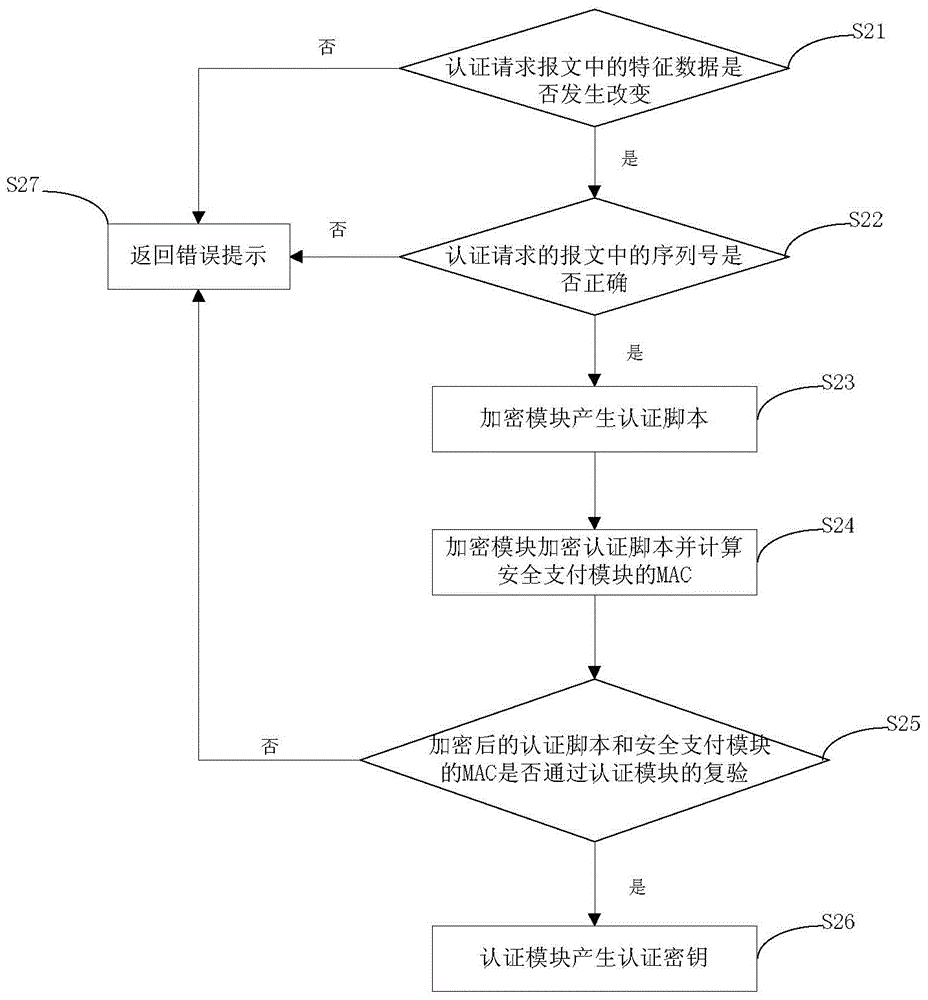
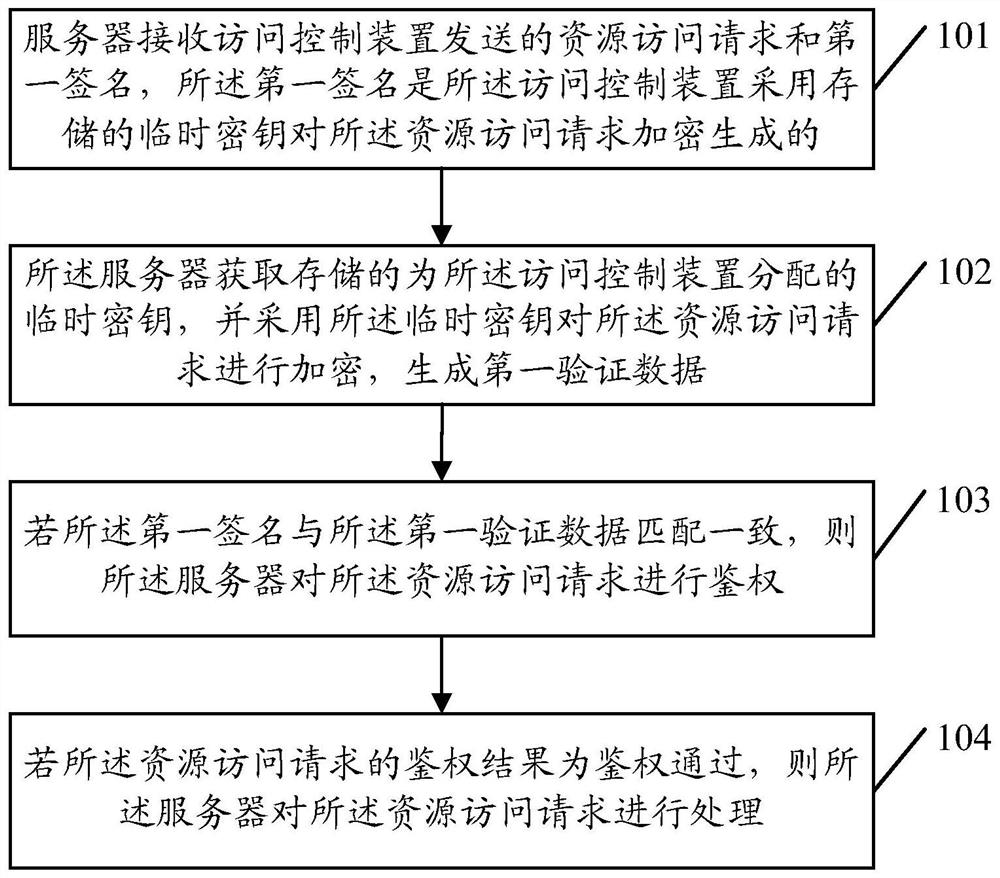
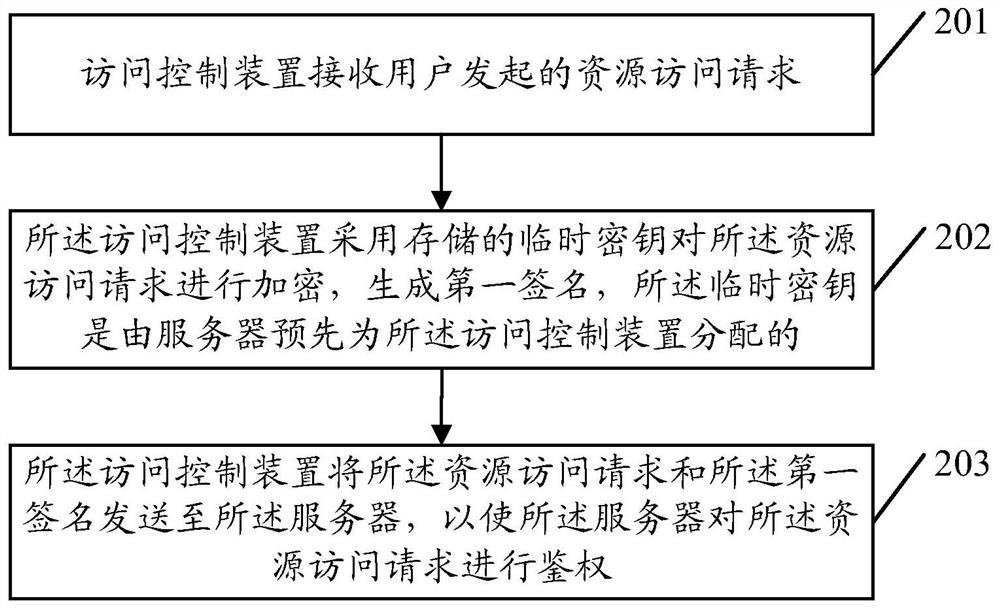
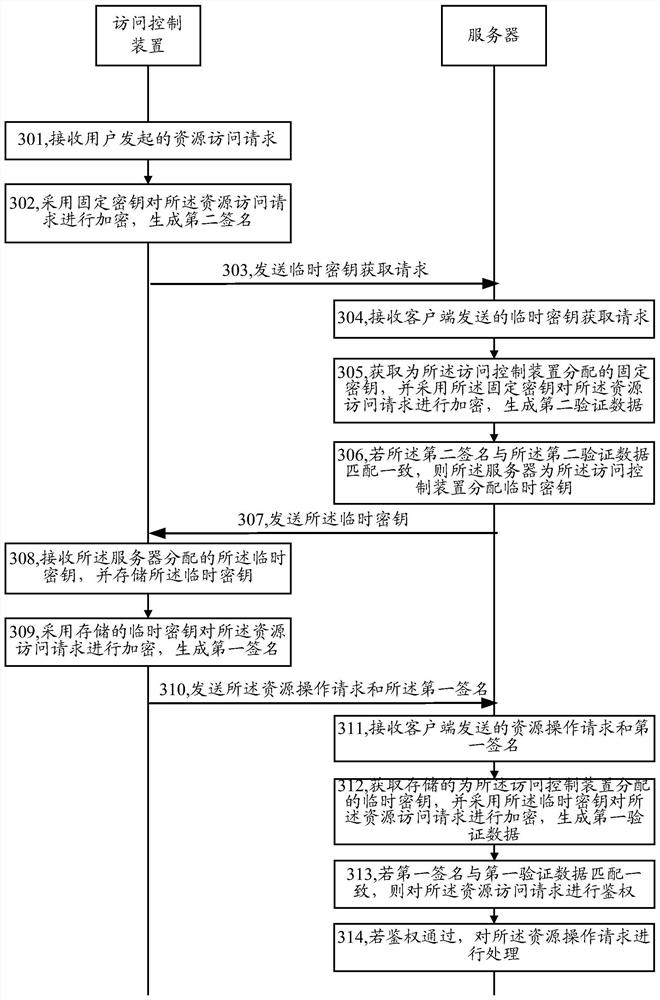
Authentication method, server and access control device
ActiveCN106657152AAvoid the risk of being leakedEnsure safetyUser identity/authority verificationAuthentication systemData matching
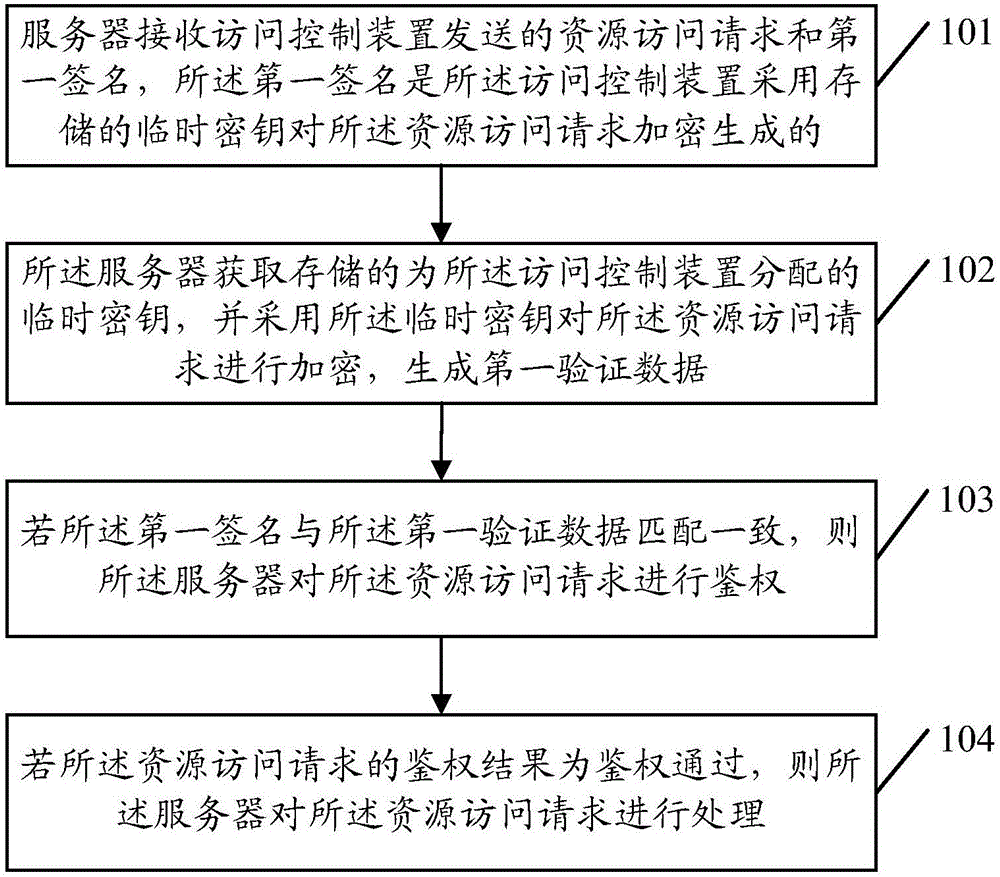
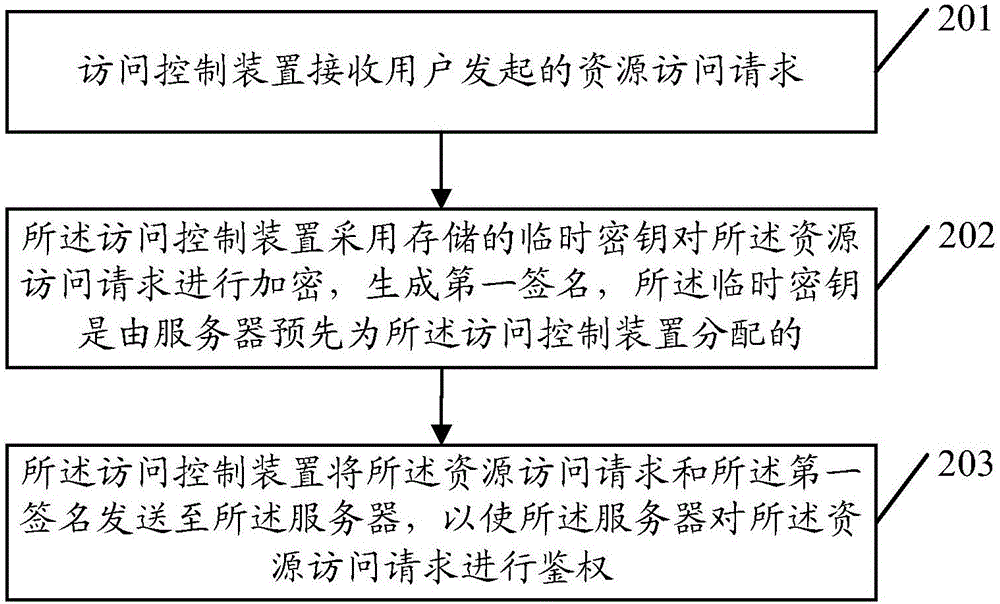
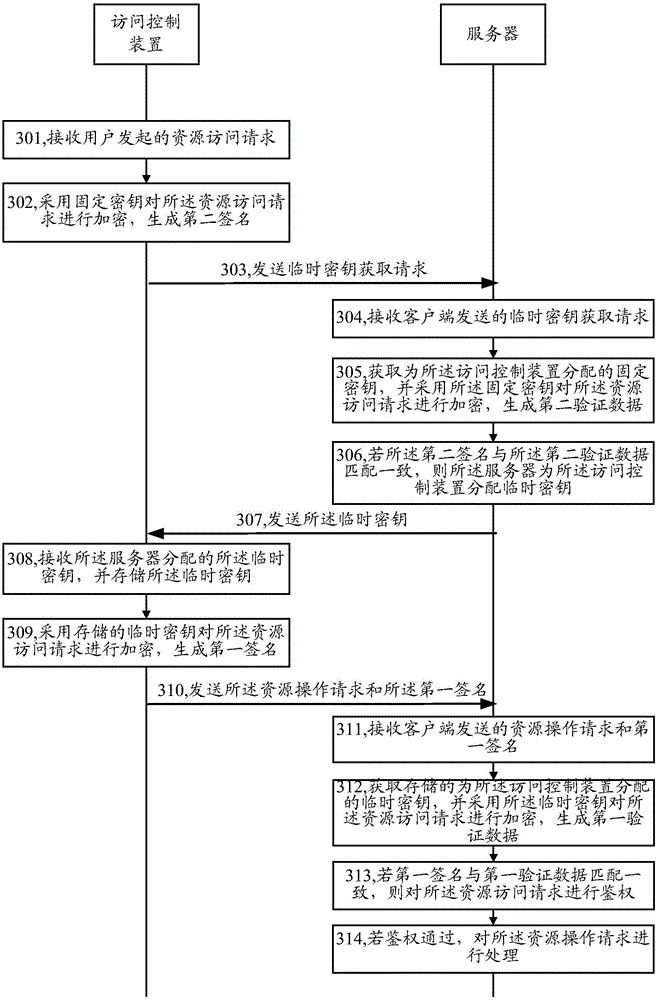
An embodiment of the invention provides an authentication method, a server and an access control device. The method comprises the following steps: receiving a resource access request and a first signature which are transmitted by the access control device by using the server, wherein the first signature is generated by encrypting the resource access request through the access control device by using a stored temporary key; acquiring the stored temporary key distributed for the access control device by using the server, and encrypting the resource access request by using the temporary key to generate first verification data; if the first signature is consistent to the first verification data, carrying out authentication on the resource access request by using the server; and if an authentication result of the resource access request is authentication passing, processing the resource access request by using the server. By the method, the signature is generated by the temporary key to carry out authentication, the risk of leaking of an intrinsic private key can be avoided, and the safety of the intrinsic private key is guaranteed.
Owner:TENCENT TECH (SHENZHEN) CO LTD
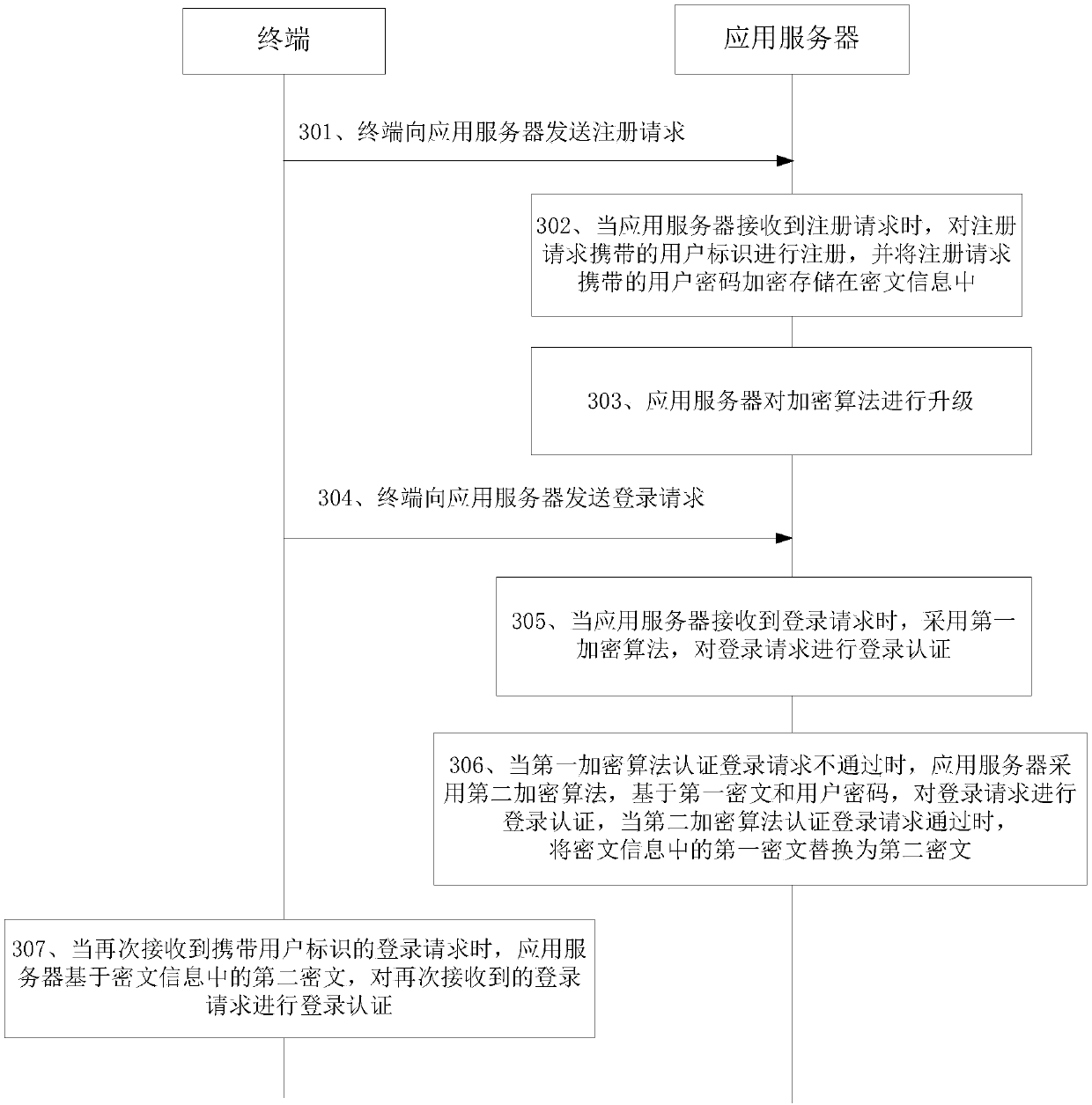
Login authentication method and device
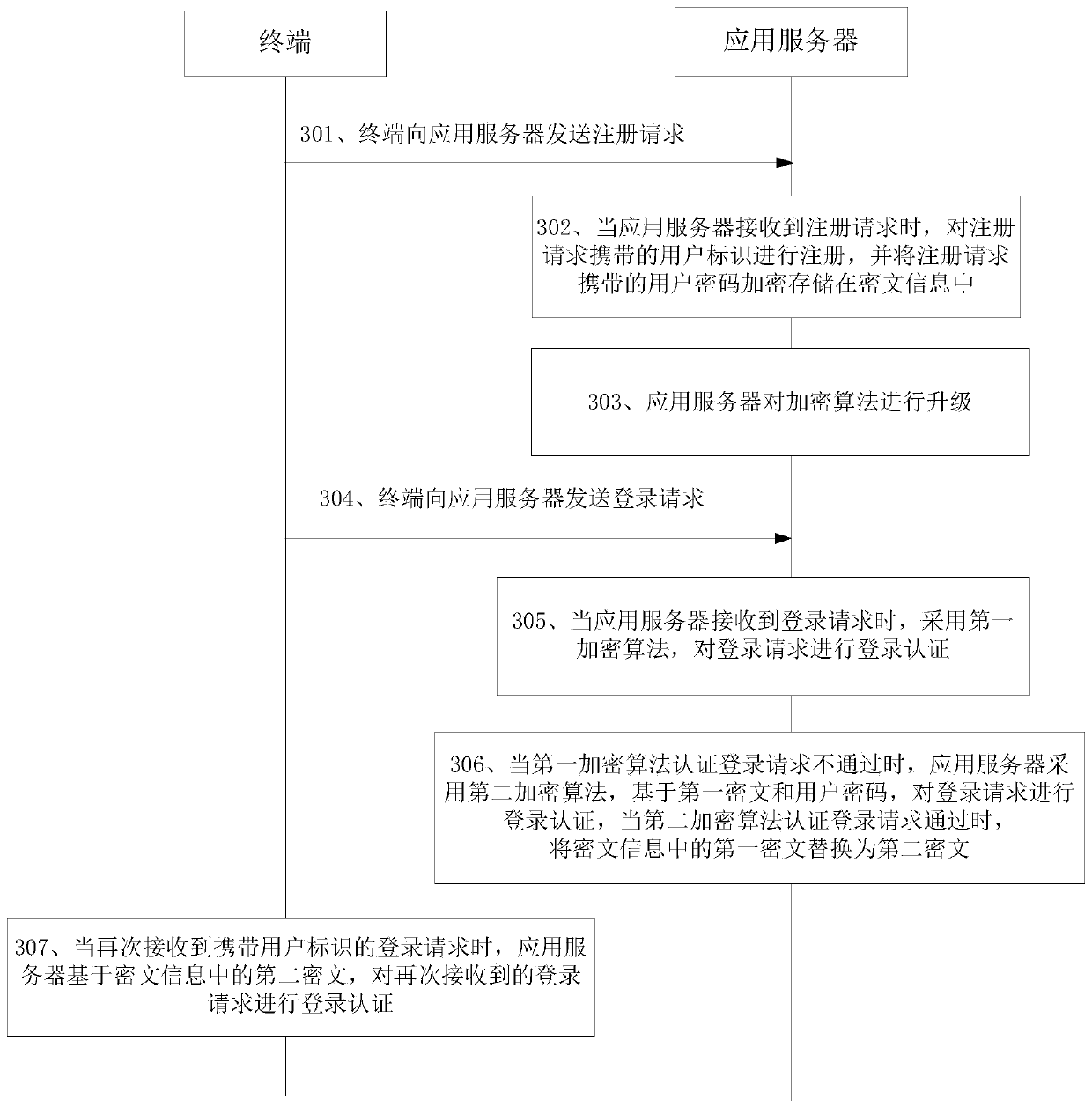
ActiveCN107920081AImprove securityAvoid the risk of being leakedMultiple keys/algorithms usagePasswordCiphertext
The invention provides a login authentication method and device, and belongs to the technical field of the network. The method comprises the following steps: acquiring ciphertext corresponding to a user identifier from ciphertext information when receiving a login request carrying the user identifier and use password, thereby obtaining the first ciphertext; performing login authentication based onthe first ciphertext and the user password by using a first encryption algorithm; when the first encryption algorithm authenticates that the login request is not passed, performing the login authentication on the login request based on the first ciphertext and the user password by adopting a second encryption algorithm; when the second encryption algorithm authenticates that the login request ispassed, replacing the first ciphertext in the ciphertext information with the second ciphertext; and performing the login authentication on the login request received again based on the second ciphertext in the ciphertext information when receiving the login request carrying the use identifier again. Based on the login authentication scheme provided by the invention, the current service is unnecessary to interrupt when upgrading the encryption algorithm.
Owner:SUZHOU XIQUAN SOFTWARE TECH CO LTD
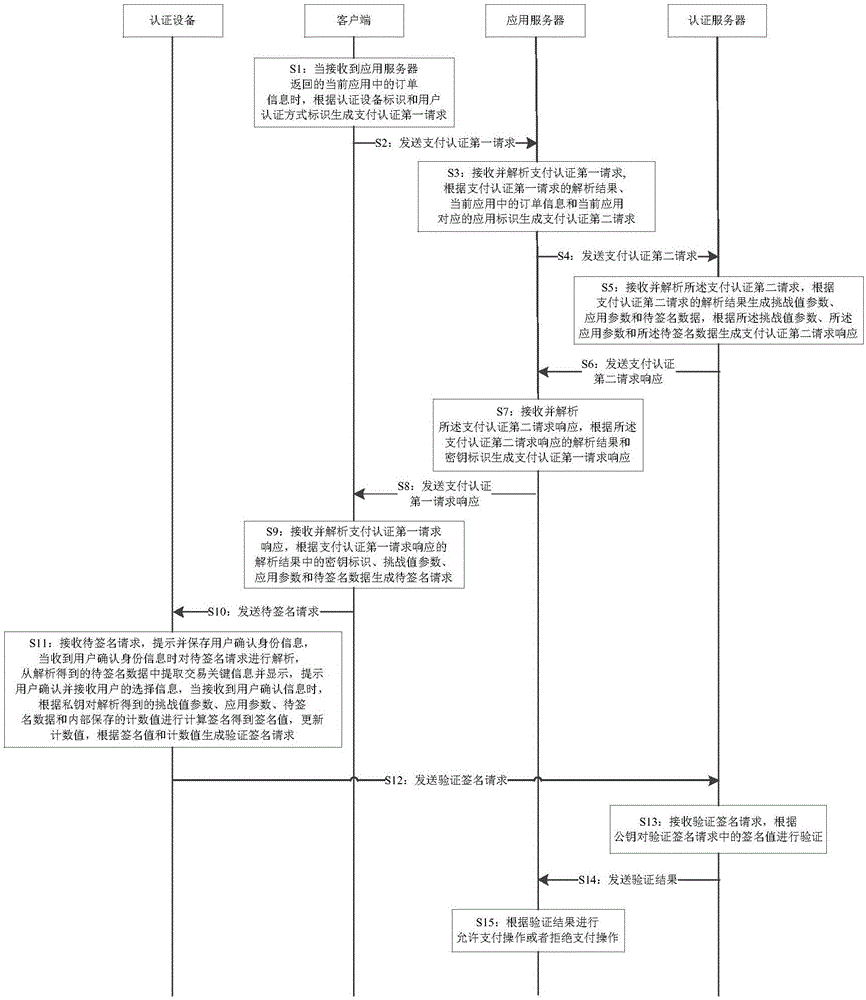
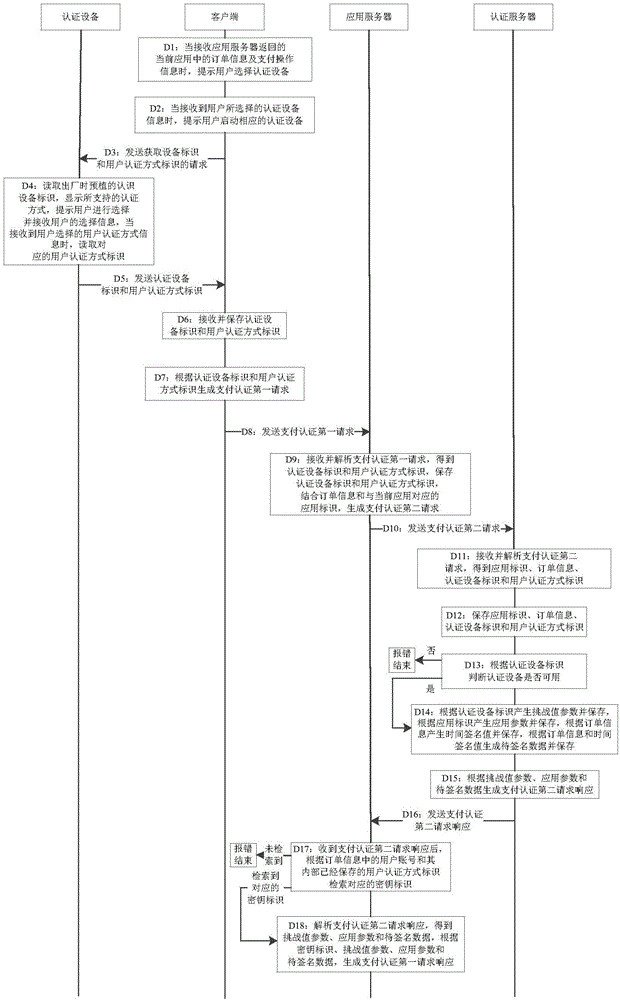
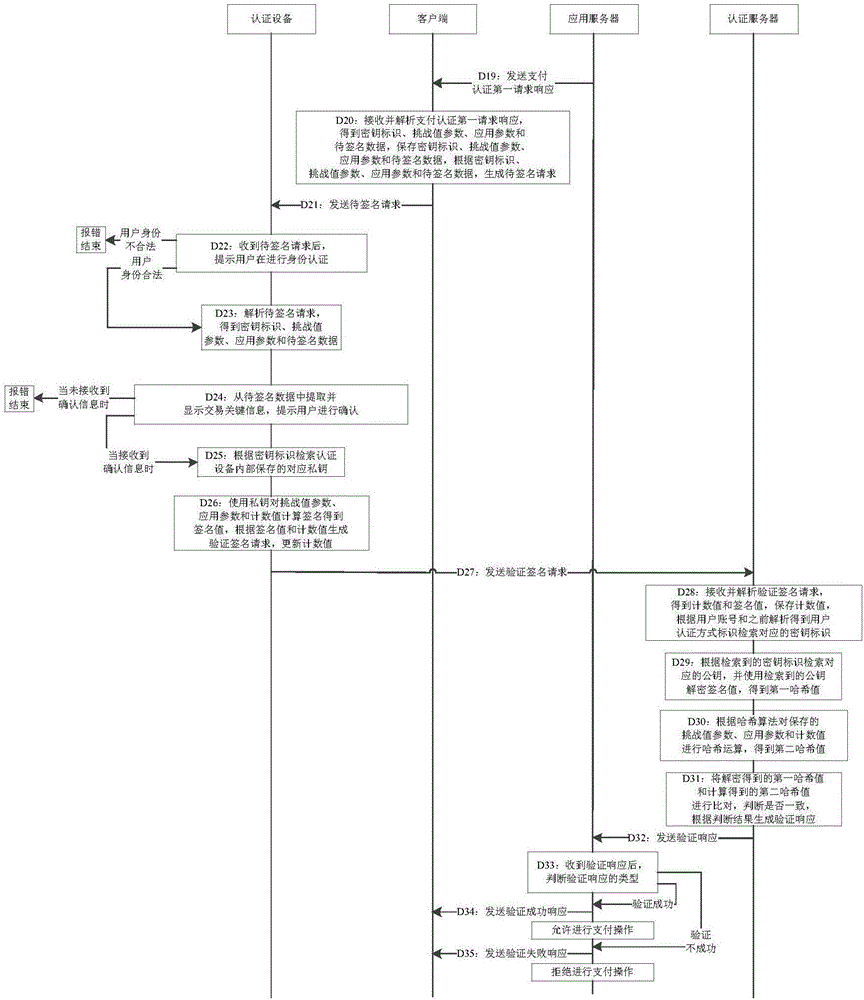
Payment authentication method and payment authentication system
InactiveCN106529948AImprove securityAvoid the risk of being leakedProtocol authorisationPaymentApplication server
The invention discloses a payment authentication method and a payment authentication system. The method comprises the steps of generating a payment authentication first request and transmitting the payment authentication first request to an application server by a client; generating a payment authentication second request by the application server according to an analysis result, order information and an application identification of the payment authentication first request and transmitting the payment authentication second request to an authentication server by the application server; generating a payment authentication second request response according to the payment authentication second request and transmitting the payment authentication second request response to the application server by the authentication server; generating a payment authentication first request response according to the analysis result of the payment authentication second request response and transmitting the payment authentication first request response to the client by the application server; generating a to-be-signed request according to the analysis result of the payment authentication first request response and transmitting the to-be-signed request to authentication equipment by the client; generating a signature verification request and transmitting the signature verification request to the authentication server by the authentication equipment; transmitting the verification result of a signature value in the signature verification request to the application server by the authentication server; and performing a payment allowing operation or a payment refusing operation on the application server according to the verification result.
Owner:FEITIAN TECHNOLOGIES
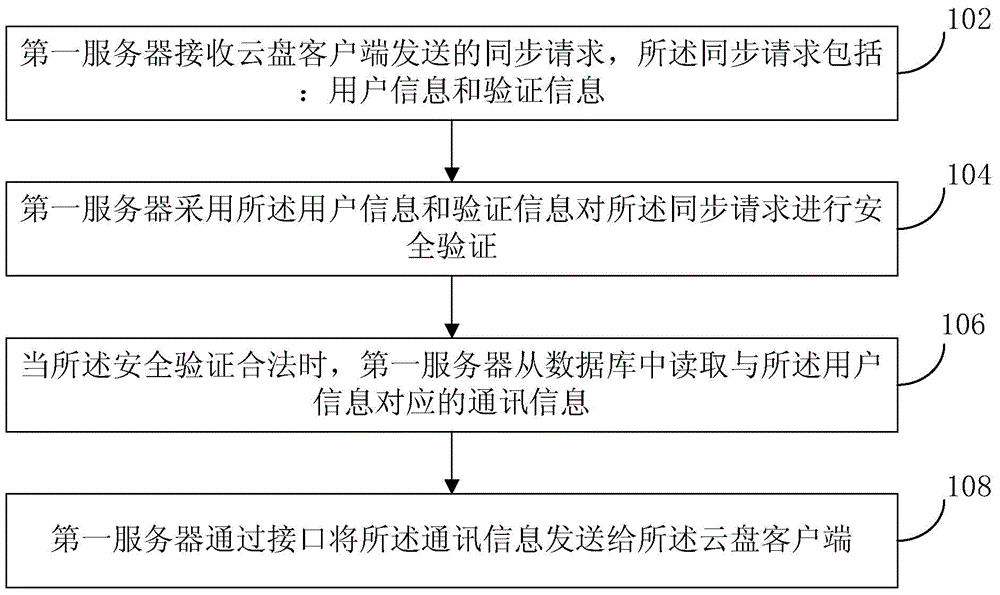
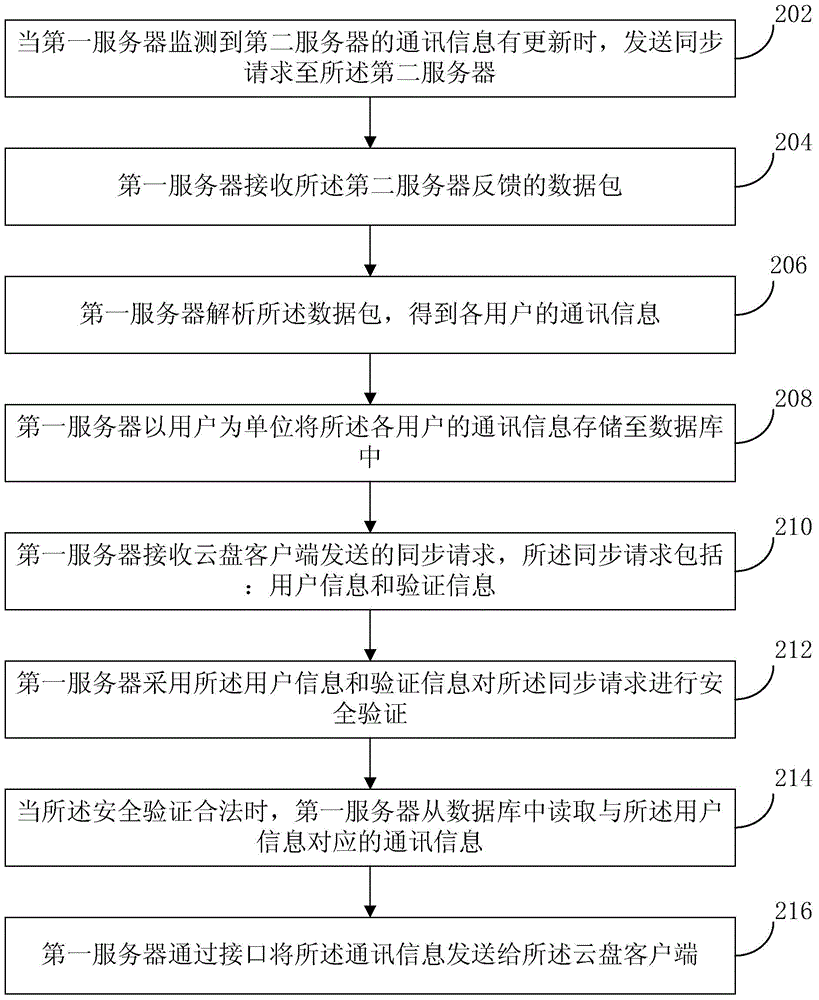
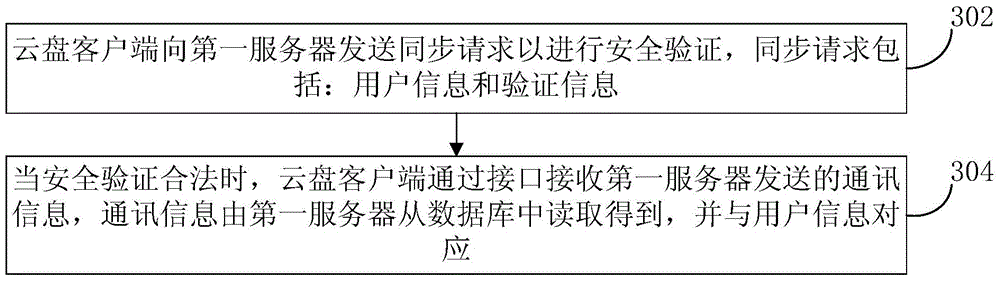
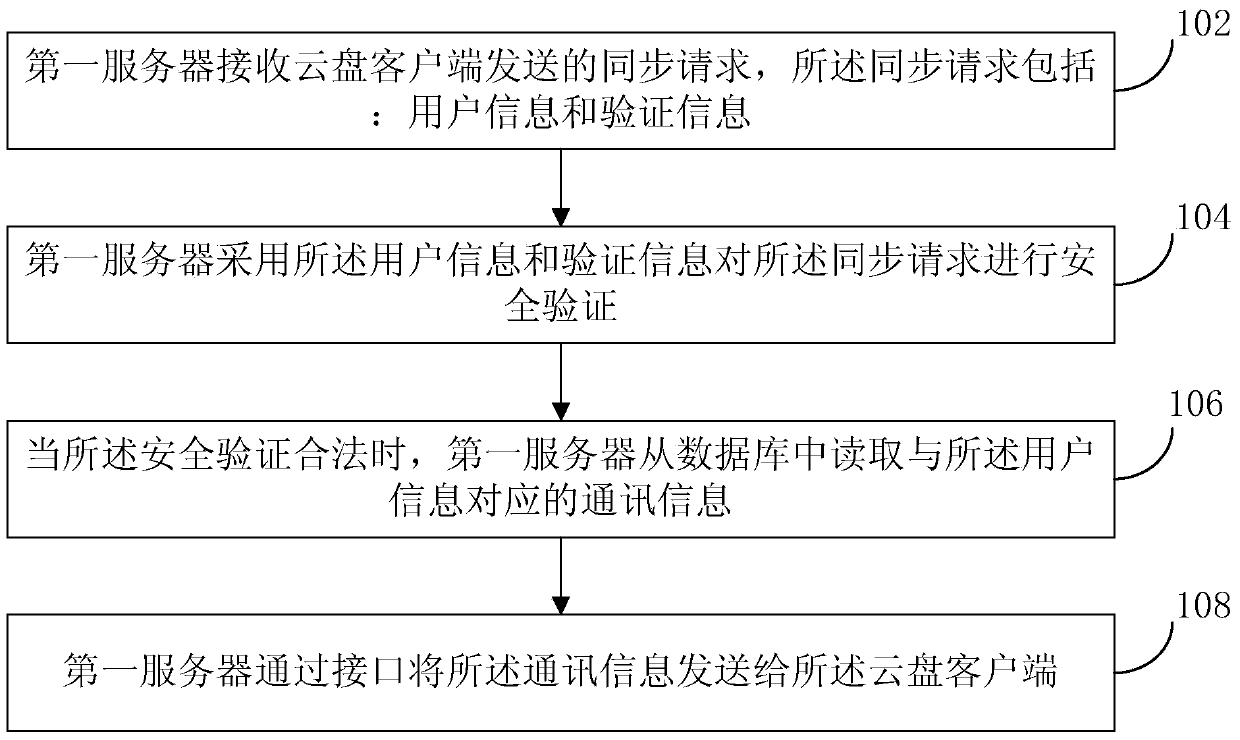
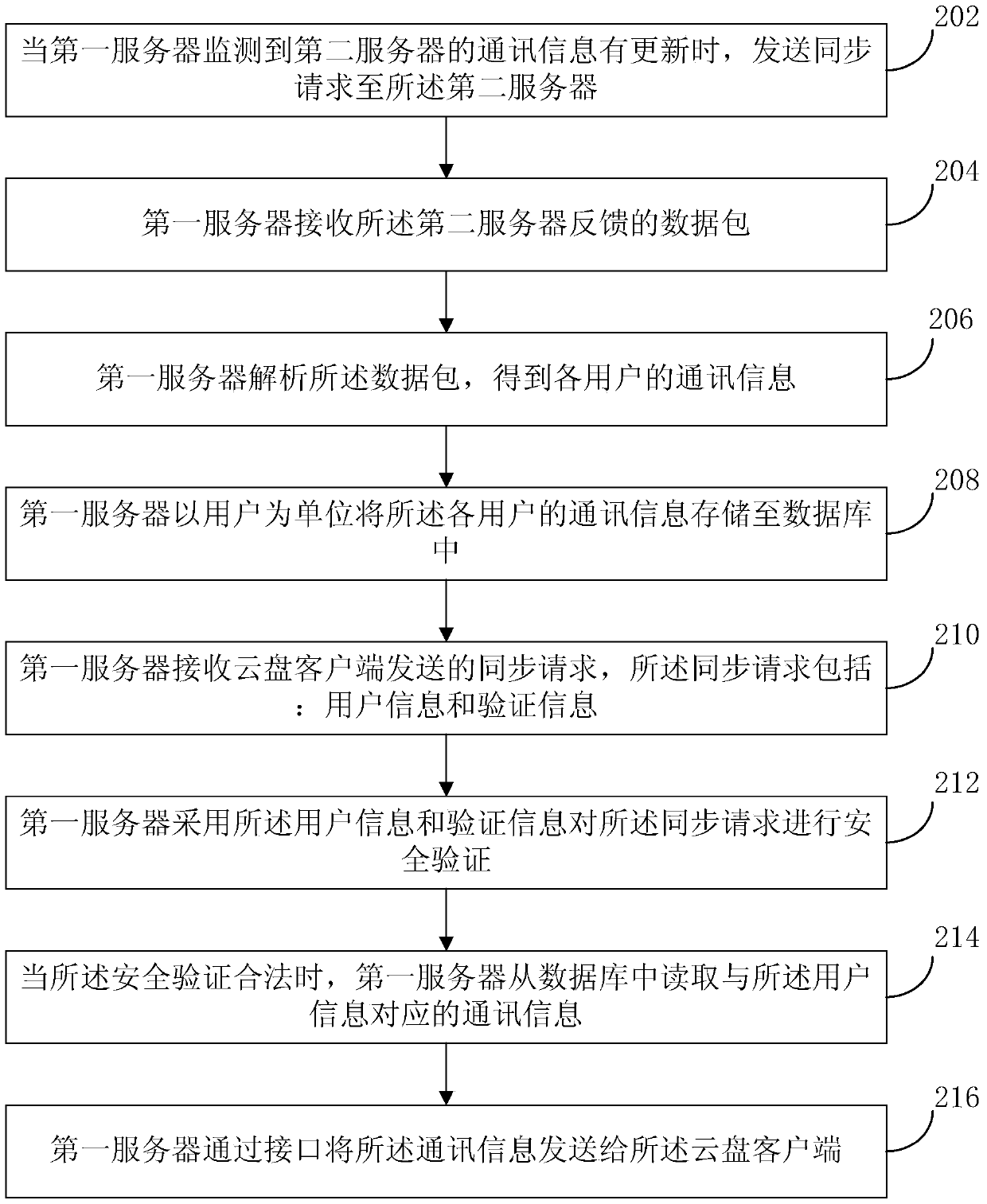
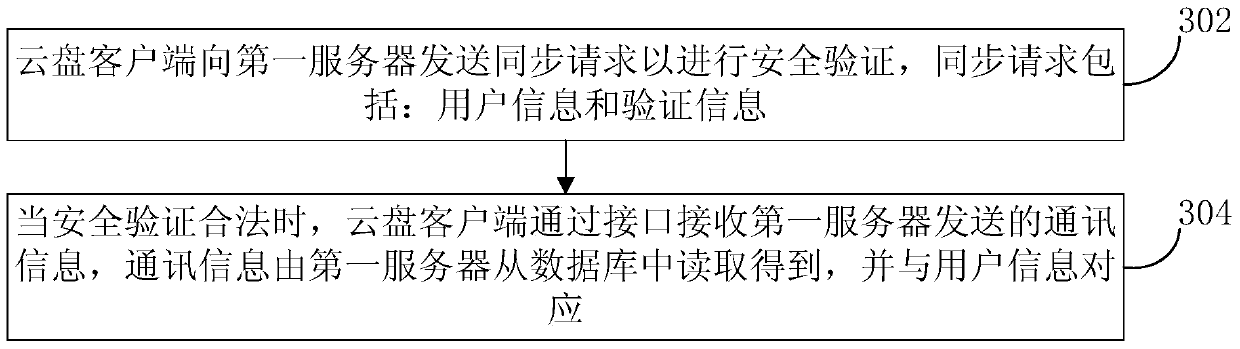
Method for loading communication information, server and cloud disk client
ActiveCN104580429AEnsure safetySolve the problem that communication information cannot be loadedTransmissionClient-sideSecurity validation
The invention provides a method for loading communication information, a server and a cloud disk client. The method comprises the steps that a first server receives a synchronization request sent by the cloud disk client, wherein the synchronization request comprises user information and verification information; the first server carries out security verification on the synchronization request according to the user information and the verification information; when the synchronization request is legal through the security verification, the first server reads the communication information corresponding to the user information from a database; the first server sends the communication information to the cloud disk client through an interface. According to the method, the security of the communication information is guaranteed, and the risk that the communication information serving as privacy leaks is avoided; furthermore, the time of loading the communication information is shortened, and the efficiency of loading the communication information is improved.
Owner:BEIJING QIHOO TECH CO LTD
Digital signature processing method and device, computer equipment and storage medium
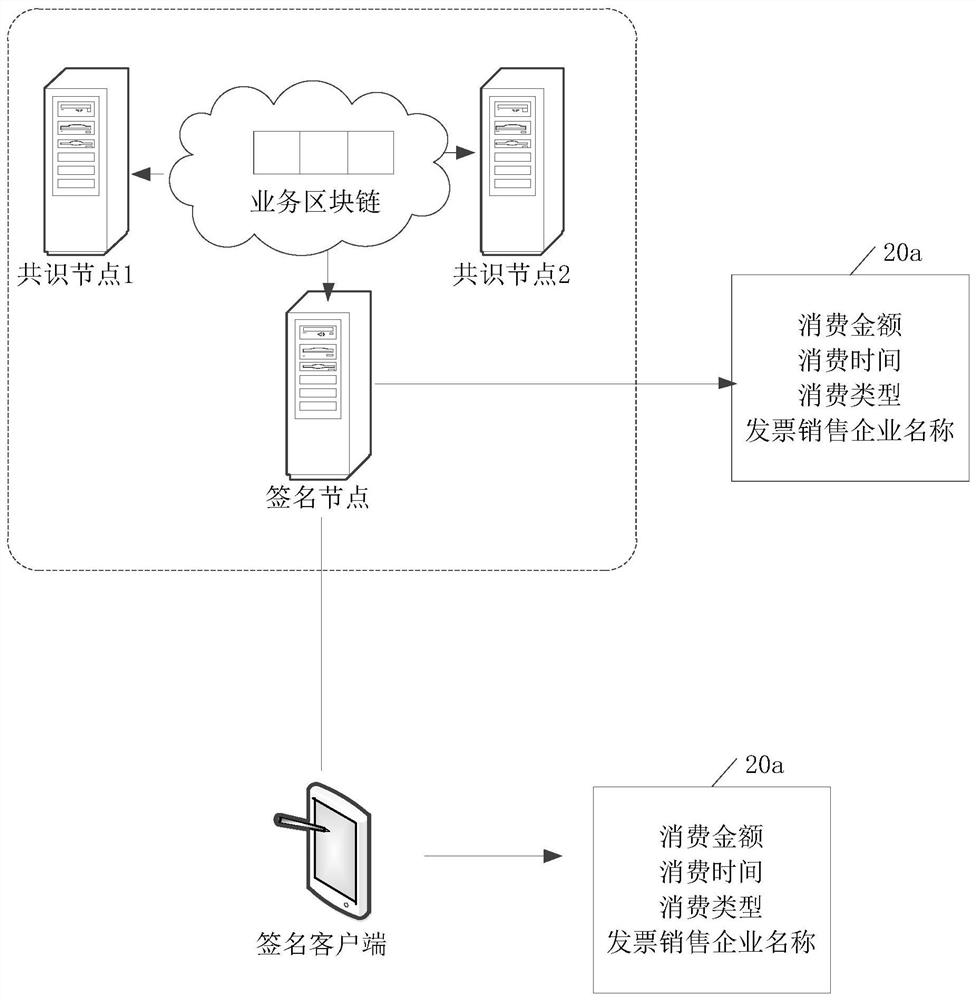
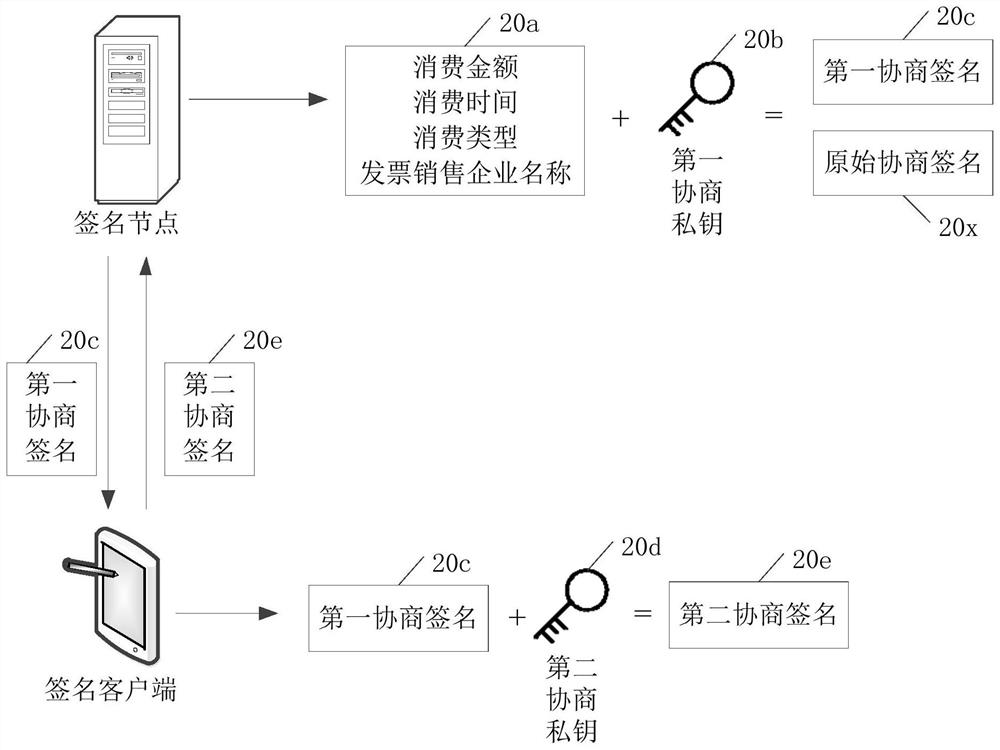
ActiveCN111464315AEnhance asset securityImprove securityFinanceUser identity/authority verificationComputer networkDigital signature
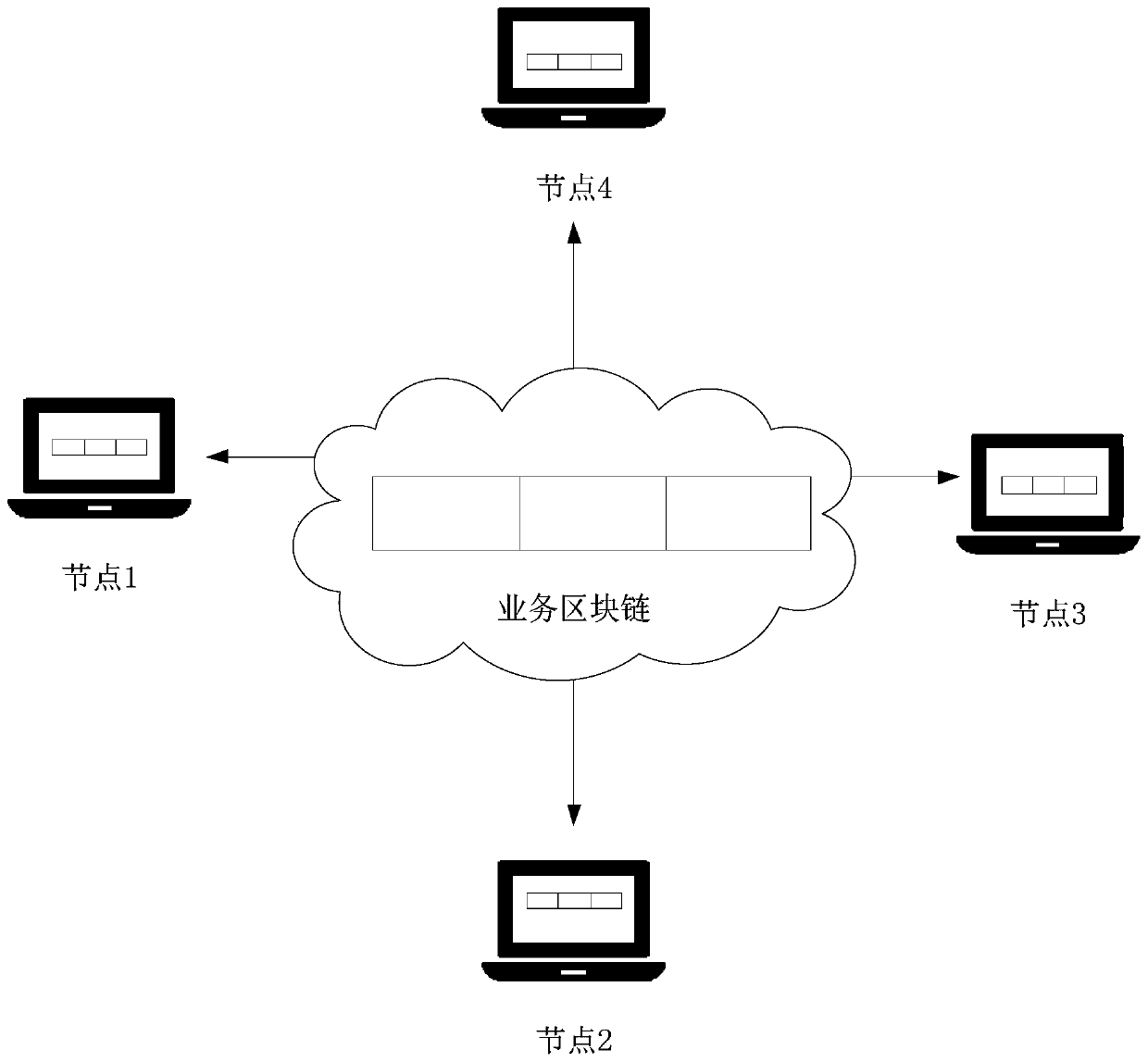
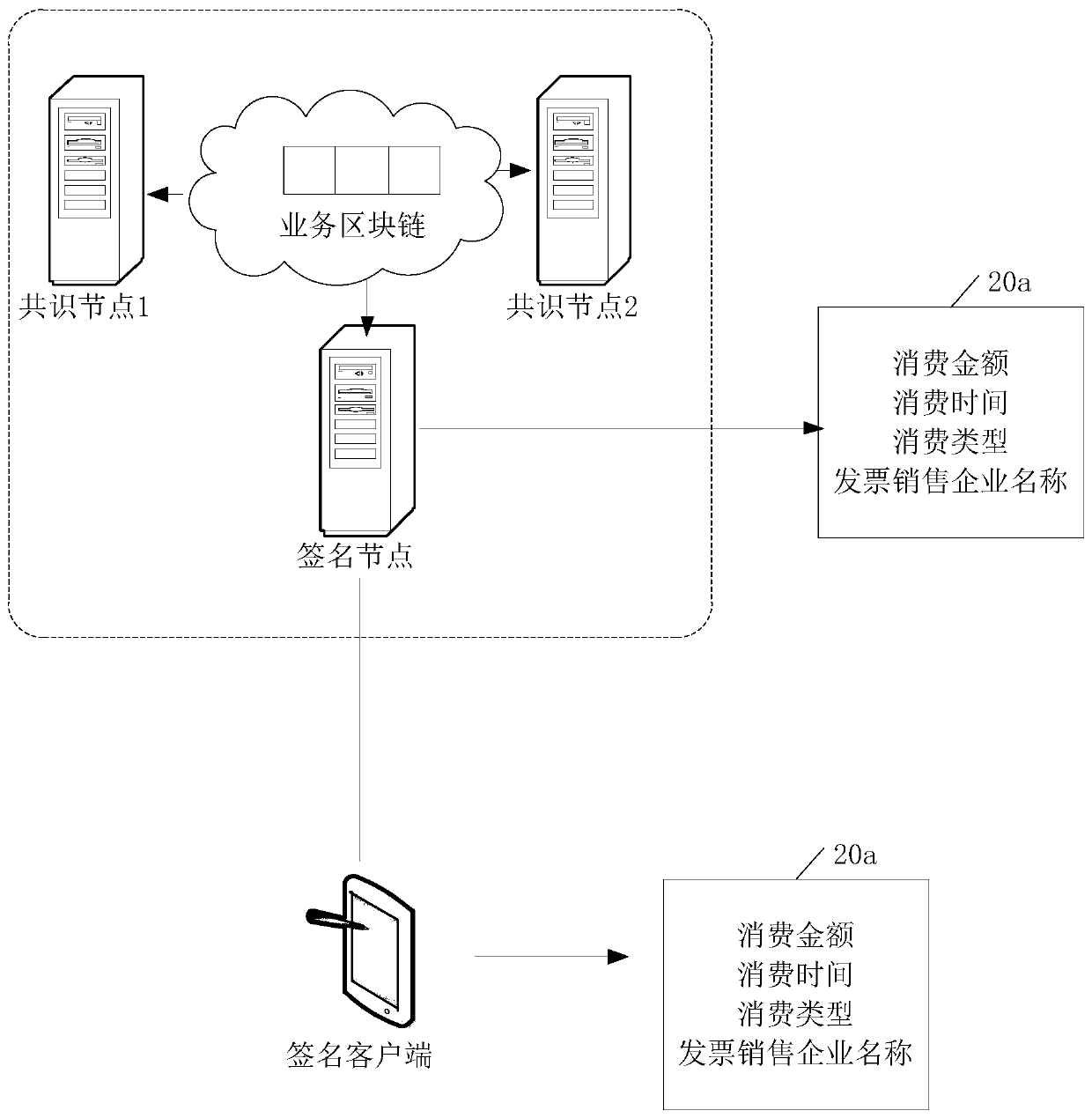
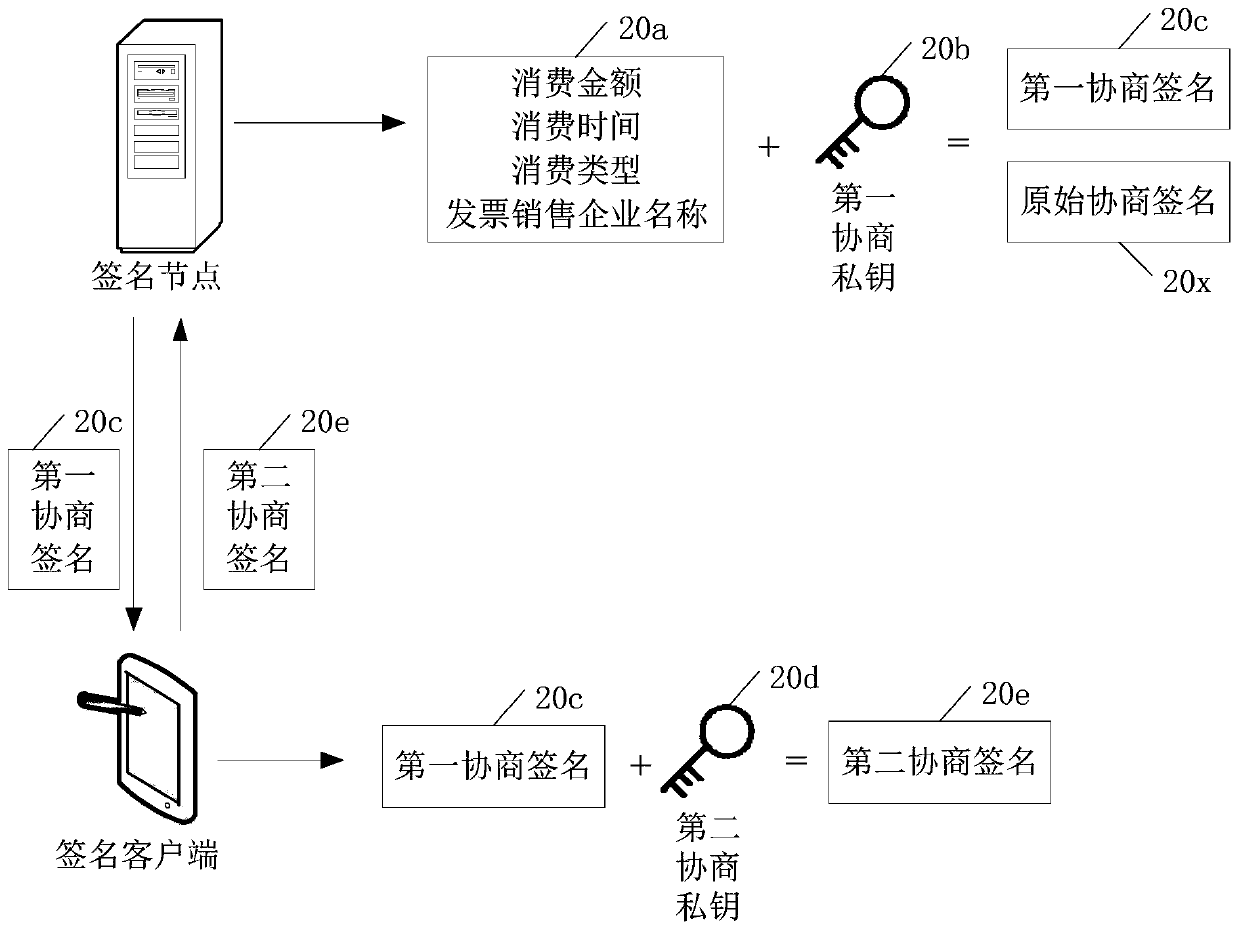
The embodiment of the invention discloses a digital signature processing method and device, computer equipment and a storage medium. The digital signature processing method comprises the steps that asignature node acquires consumption voucher information for a first voucher user and acquires the first digital signature of the consumption voucher information; the signature node adopts a private key of a second voucher user having an association relationship with the first voucher user to sign the consumption voucher information to obtain a second digital signature; and the signature node sendsthe consumption voucher information, the first digital signature and the second digital signature to a consensus node, instructs the consensus node to verify the first digital signature and the second digital signature, and enables the consensus node to add the consumption voucher information to the service block chain after the first digital signature and the second digital signature pass the verification. According to the invention, the security of the private key of the user can be enhanced.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Website security vulnerability detection method and device, medium and electronic equipment
ActiveCN111740992AAvoid the risk of being leakedImprove securityTransmissionVulnerability detectionComputer security
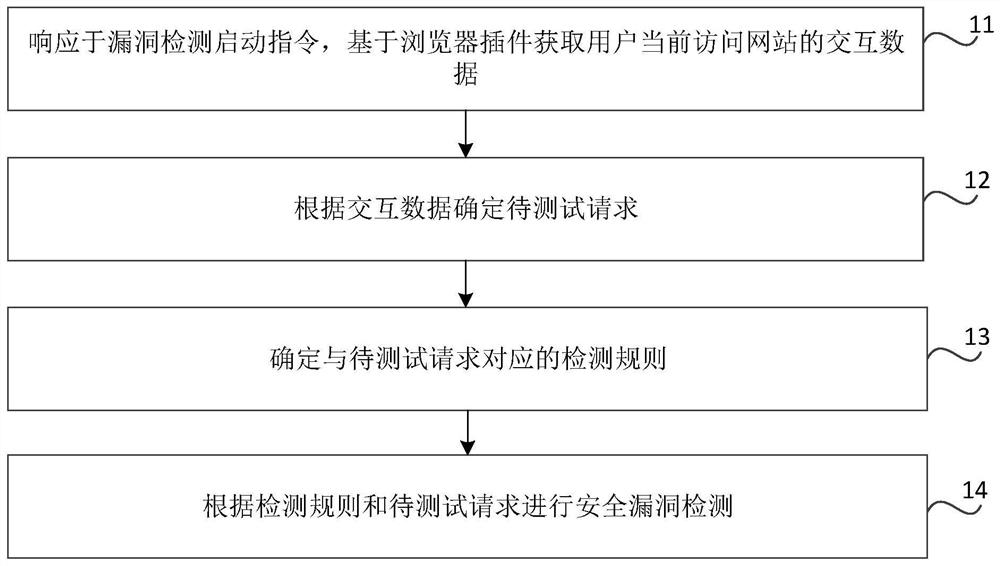
The invention relates to a website security vulnerability detection method and device, a medium and electronic equipment, and the method comprises the steps: responding to a vulnerability detection starting instruction, obtaining interaction data of a website currently accessed by a user based on a browser plug-in; determining a to-be-tested request according to the interaction data, wherein the to-be-tested request is a request initiated in a website access process of the user; determining a detection rule corresponding to the to-be-tested request; and performing security vulnerability detection according to the detection rule and the to-be-tested request. Therefore, the security of the user information data can be improved; the manual workload required for obtaining the request list canbe reduced; the security vulnerability detection method can be applied to a scene of business updating iteration, the application range of the security vulnerability detection method is widened, and the method can be applied to a browser plug-in, so that the security vulnerability detection method can be operated under the condition that a browser is installed, other detection software does not need to be installed, and cross-operating system platform detection can be supported.
Owner:BEIJING BYTEDANCE NETWORK TECH CO LTD
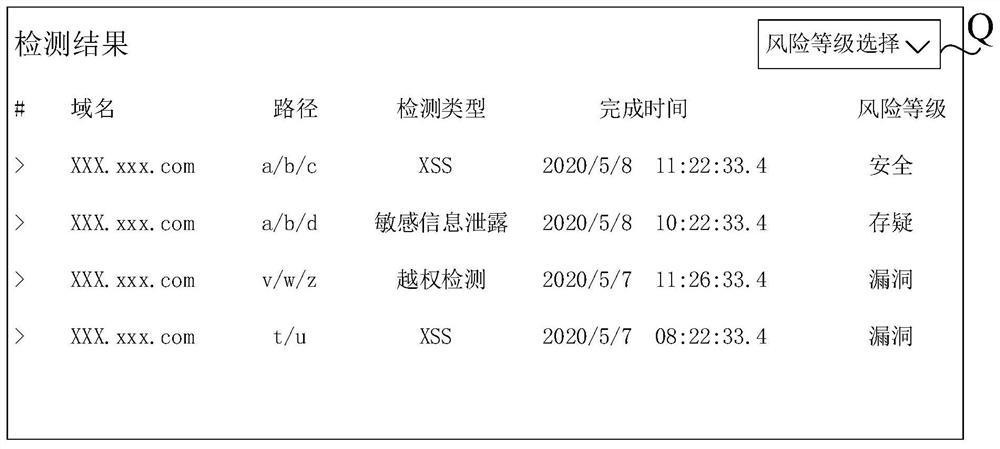
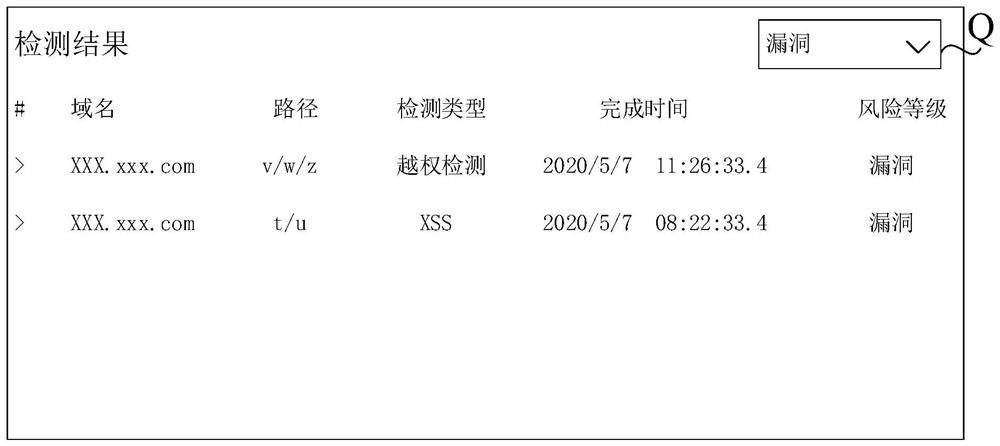
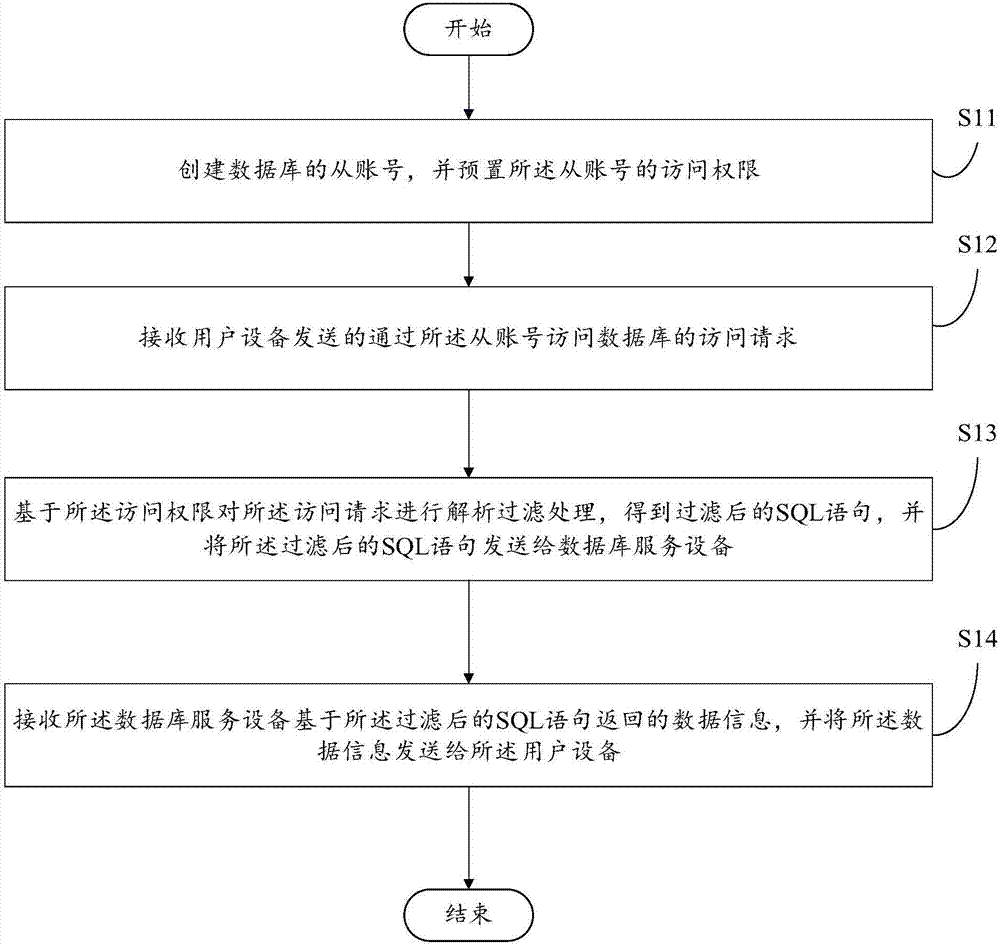
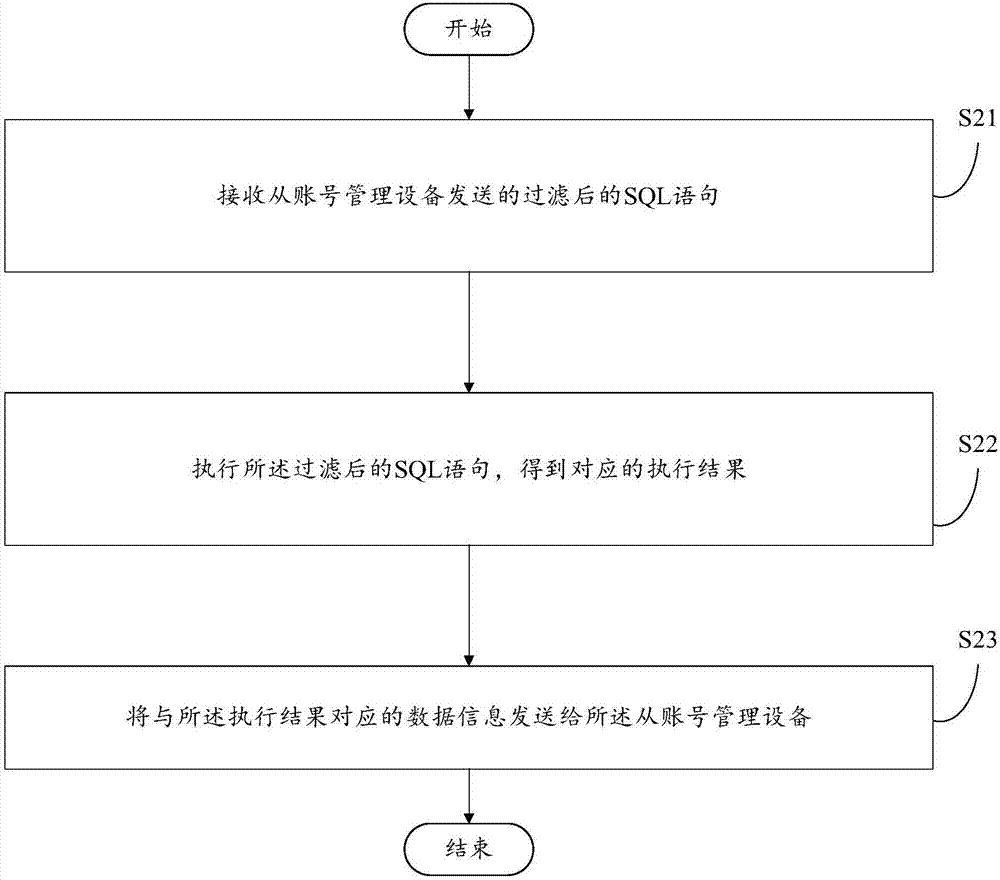
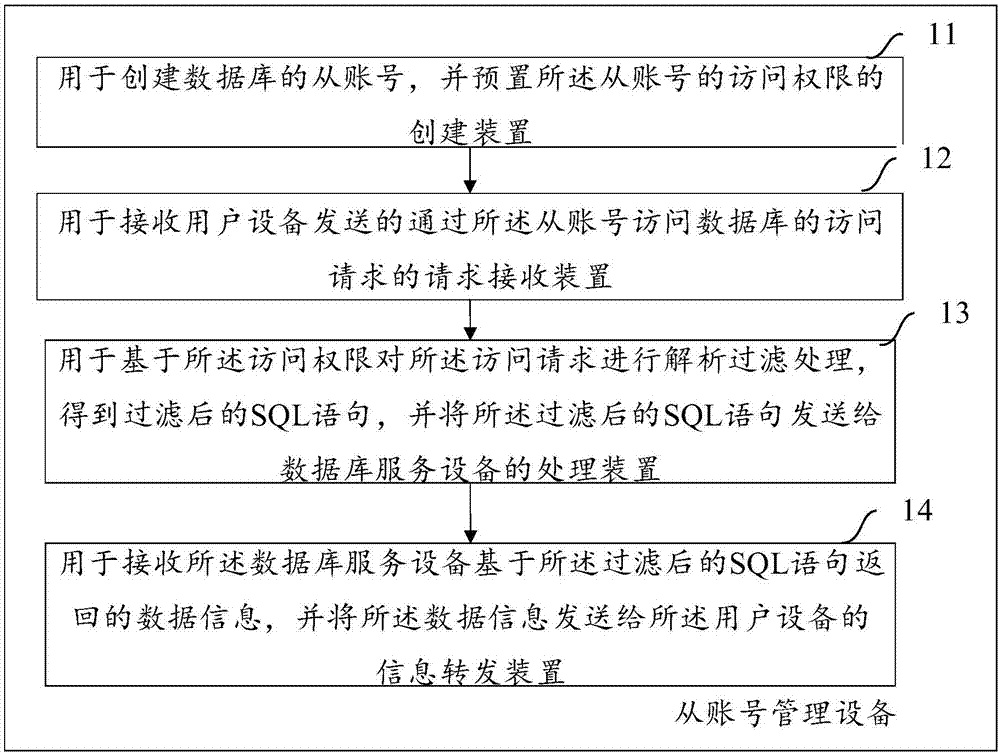
Database access method and device
InactiveCN107273758AAvoid the risk of being leakedEnsure safetyDigital data protectionUser needsData information
The invention aims to provide a database access method and device. The method comprises the steps of creating a slave account of a database and presetting an access permission of the slave account; when a user needs to access the database through the slave account, receiving an access request used for accessing the database through the slave account and sent by user equipment; performing analysis and filtration processing on the access request based on the access permission to obtain a filtered SQL statement, and sending the filtered SQL statement to a database service device; and receiving data information returned by the database service device based on the filtered SQL statement, and sending the data information to the user equipment. By utilizing the created slave account of the database and the access permission of the slave account, access requests of different users are met, the risk of leakage of the data information of the database possibly caused by sharing or changing a master account of the database is avoided, the security and high efficiency of accessing the data information of the database are ensured, and the security of the master account of the database is further ensured.
Owner:SUNINFO INFORMATION TECH
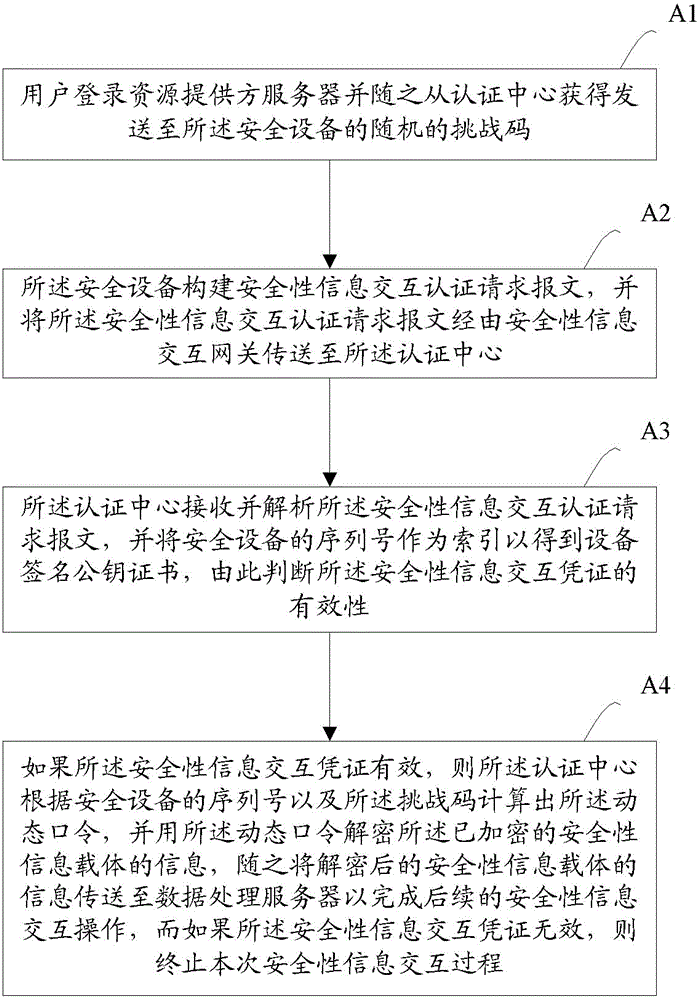
Identity authentication method for security information interaction
ActiveCN104980276AAvoid the risk of being leakedImprove securityUser identity/authority verificationService provisionSecurity information
The invention provides an identity authentication method for security information interaction. The method comprises the following steps: a user acquiring security equipment containing a security chip from a service provider and executing an initialization operation to activate the security equipment; the user initiating and finishing the security information interaction process in virtue of the activated security equipment. The identity authentication method for security information interaction disclosed by the invention is high in security and convenient for use.
Owner:CHINA UNIONPAY
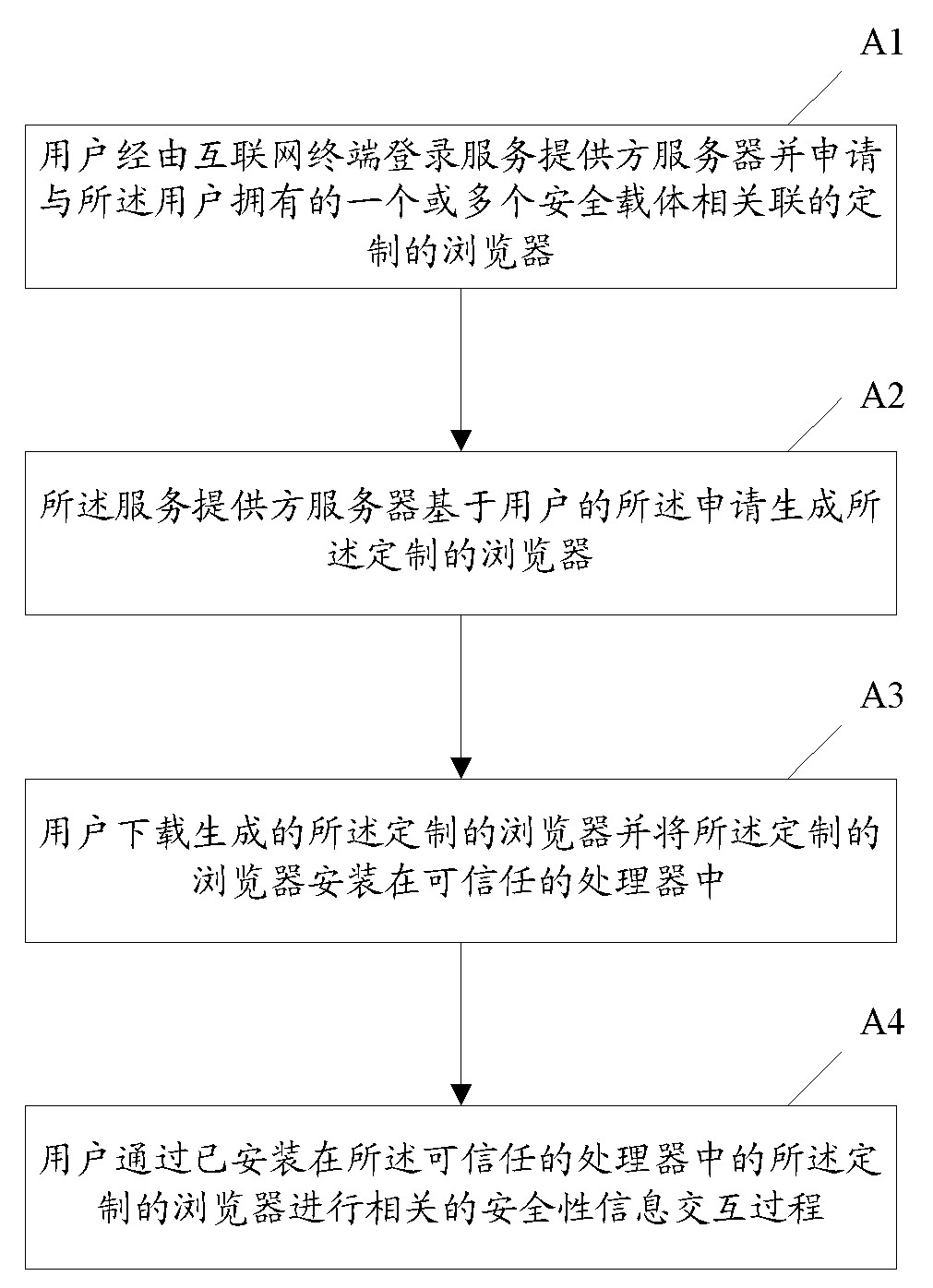
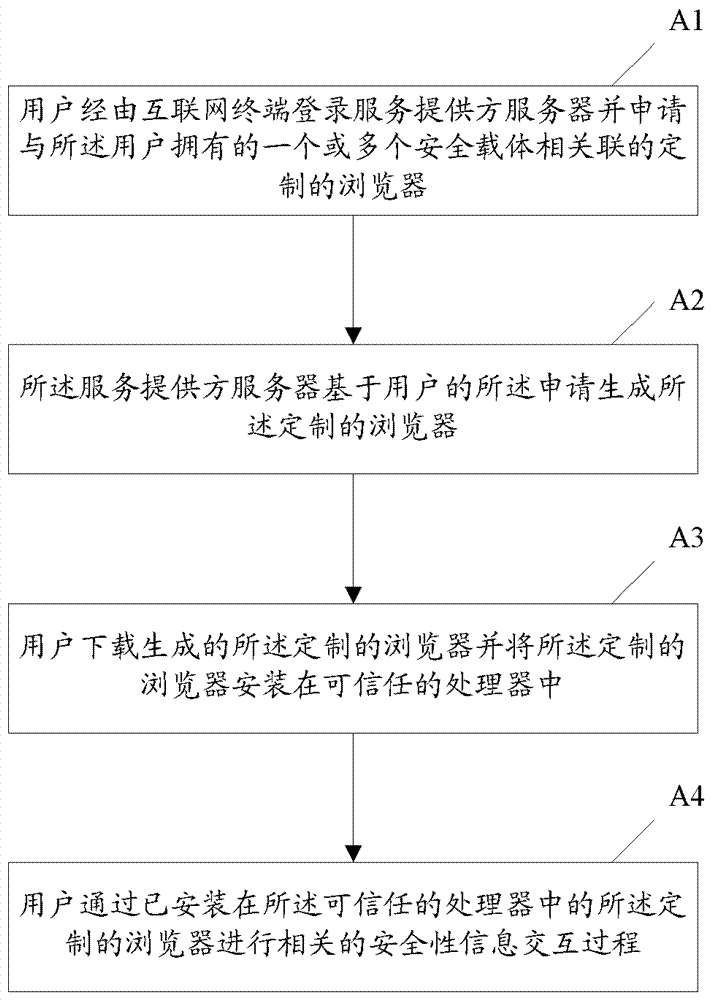
Security information interaction method based on customizable browser
ActiveCN104348807AAvoid the risk of being leakedImprove securityData switching networksInternet privacyThe Internet
The invention brings forward a security information interaction method based on a customizable browser. The method comprises the steps that a user logs in a service provider server via an internet terminal and applies for a customized browser which is related to one or multiple security carriers possessed by the user; the customized browser is generated by the service provider server based on the application of the user; the user downloads the customized browser and installs the customized browser in a trusted processor; and the user performs the related security information interaction process via the customized browser installed in the trusted processor. The security information interaction method based on the customizable browser has enhanced security and is convenient to use.
Owner:CHINA UNIONPAY
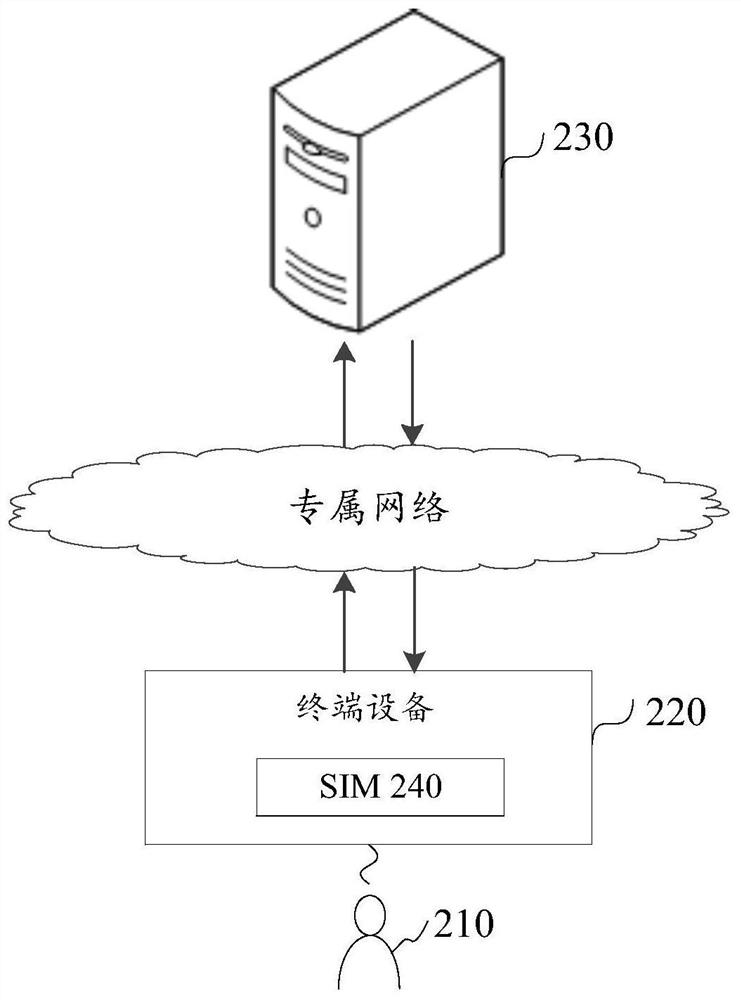
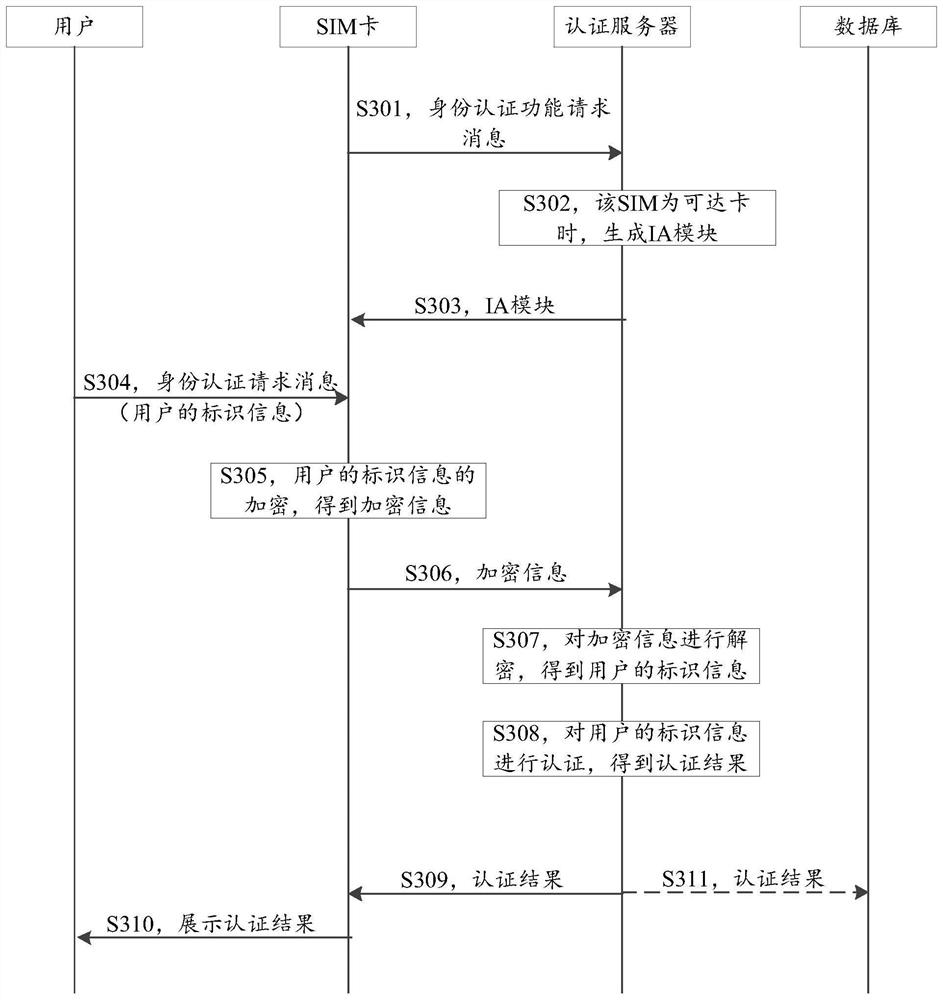
Identity authentication method and system based on telecommunication smart card
PendingCN114666786AAvoid the risk of being leakedImprove securitySecurity arrangementTelecommunicationsUser privacy
The invention provides an identity authentication method and system based on a telecommunication smart card. According to the technical scheme, the identification information of the user is encrypted through the SIM card, so that the risk that privacy information of the user, such as an identity card number, a name and the like, is leaked in a general identity authentication process is avoided; besides, the identity authentication method is realized by the user through the SIM card, and the SIM card is carried in the user handheld terminal, so that the problem that an intelligent card for identity authentication needs to be additionally carried is solved.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD +1
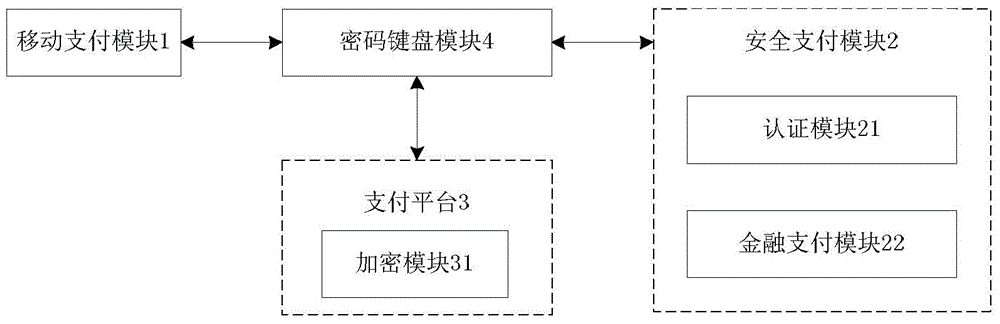
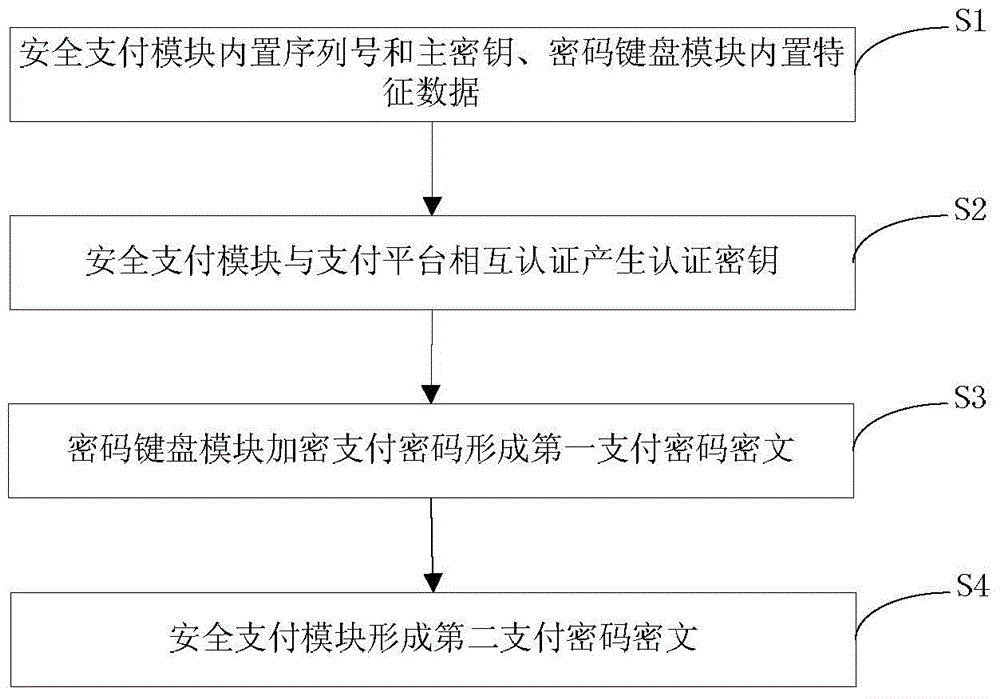
Mobile terminal?payment password?transmission system and method
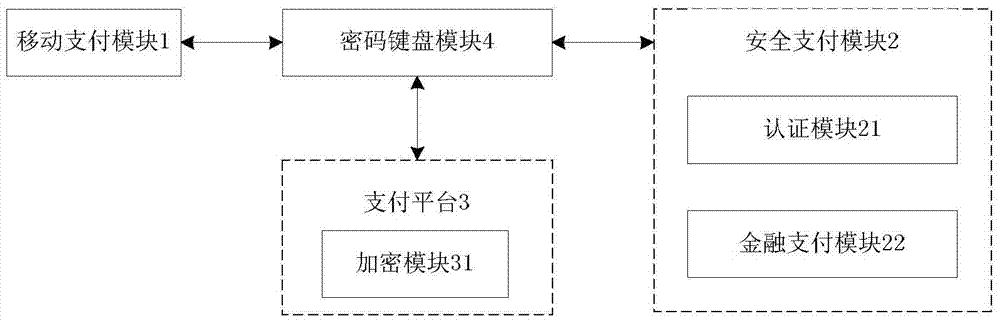
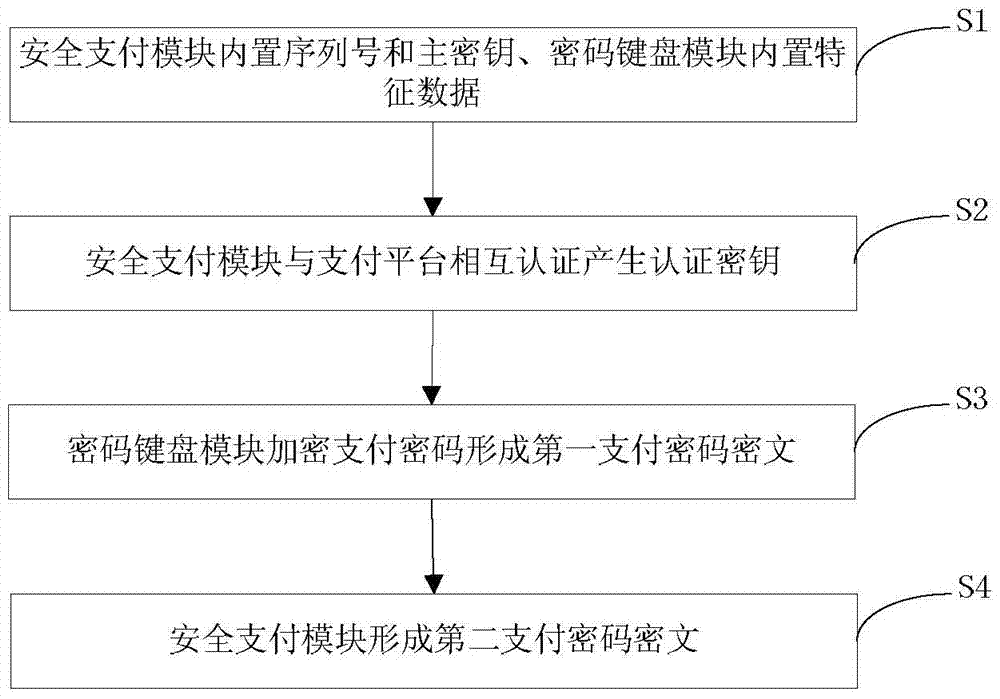
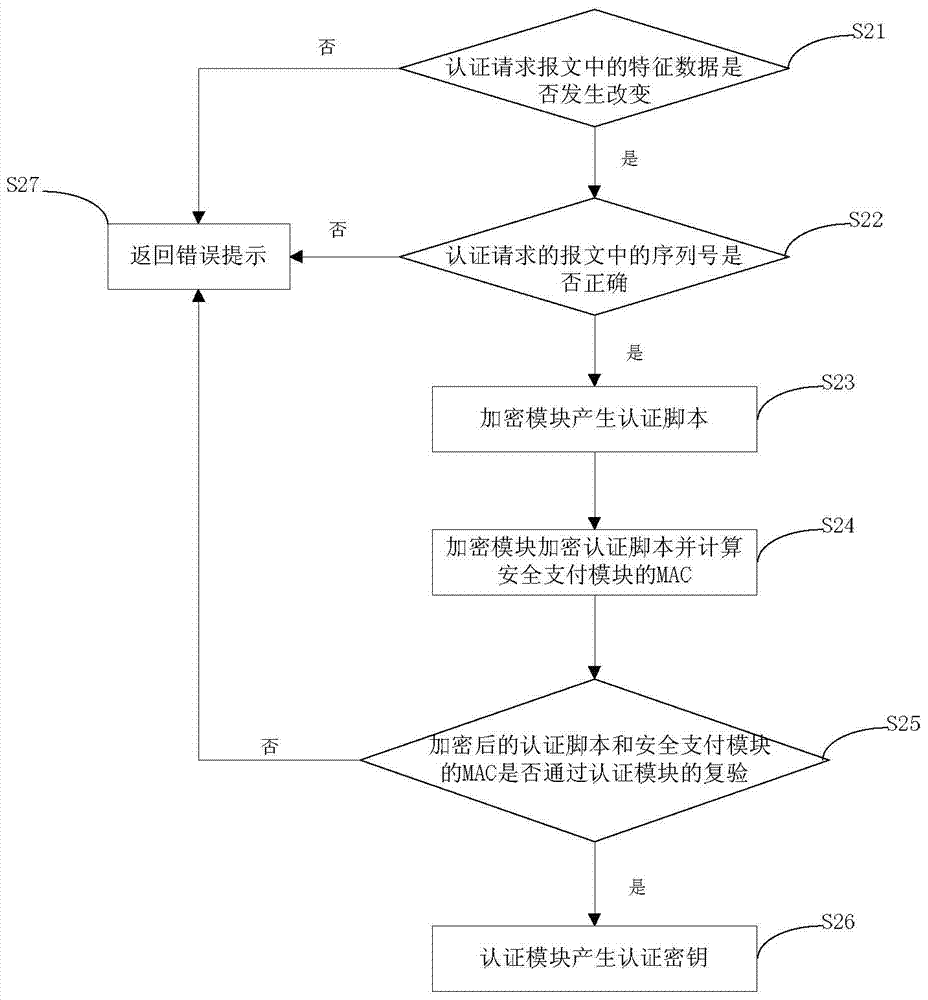
InactiveCN103825740AAvoid the risk of being leakedEnsure safetyUser identity/authority verificationProtocol authorisationPlaintextPassword
The invention discloses a mobile terminal?payment password?transmission system and a method, and relates to the field of mobile payment. The payment password?transmission system comprises a mobile payment?module,?a payment platform, a safety payment?module, and a password keyboard module for inputting a payment password. According to the payment password?transmission method, the safety payment?module and the payment platform are mutually authenticated and an authentication key is generated; the payment password is inputted via the password keyboard module and uses the authentication key for encryption; decryption and encryption again are carried out via the safety payment?module, a payment password ciphertext is formed to be transmitted to the password keyboard module, and the password keyboard module transmits the payment password ciphertext to the mobile payment?module for use. During the payment password use process, the mobile payment?module can not touch a payment password plaintext, and the risk that the payment password is leaked can thus avoided.
Owner:武汉擎动网络科技有限公司
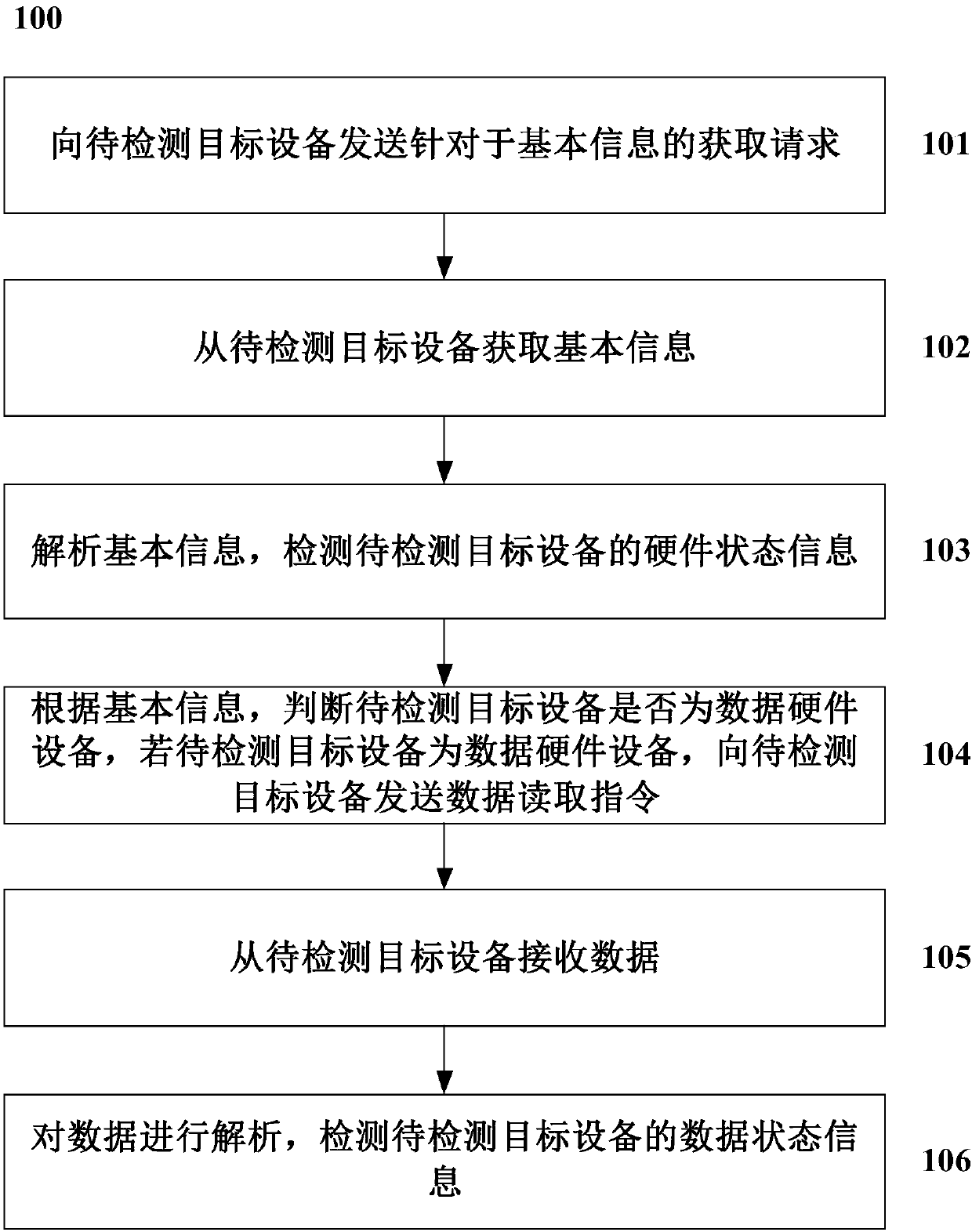
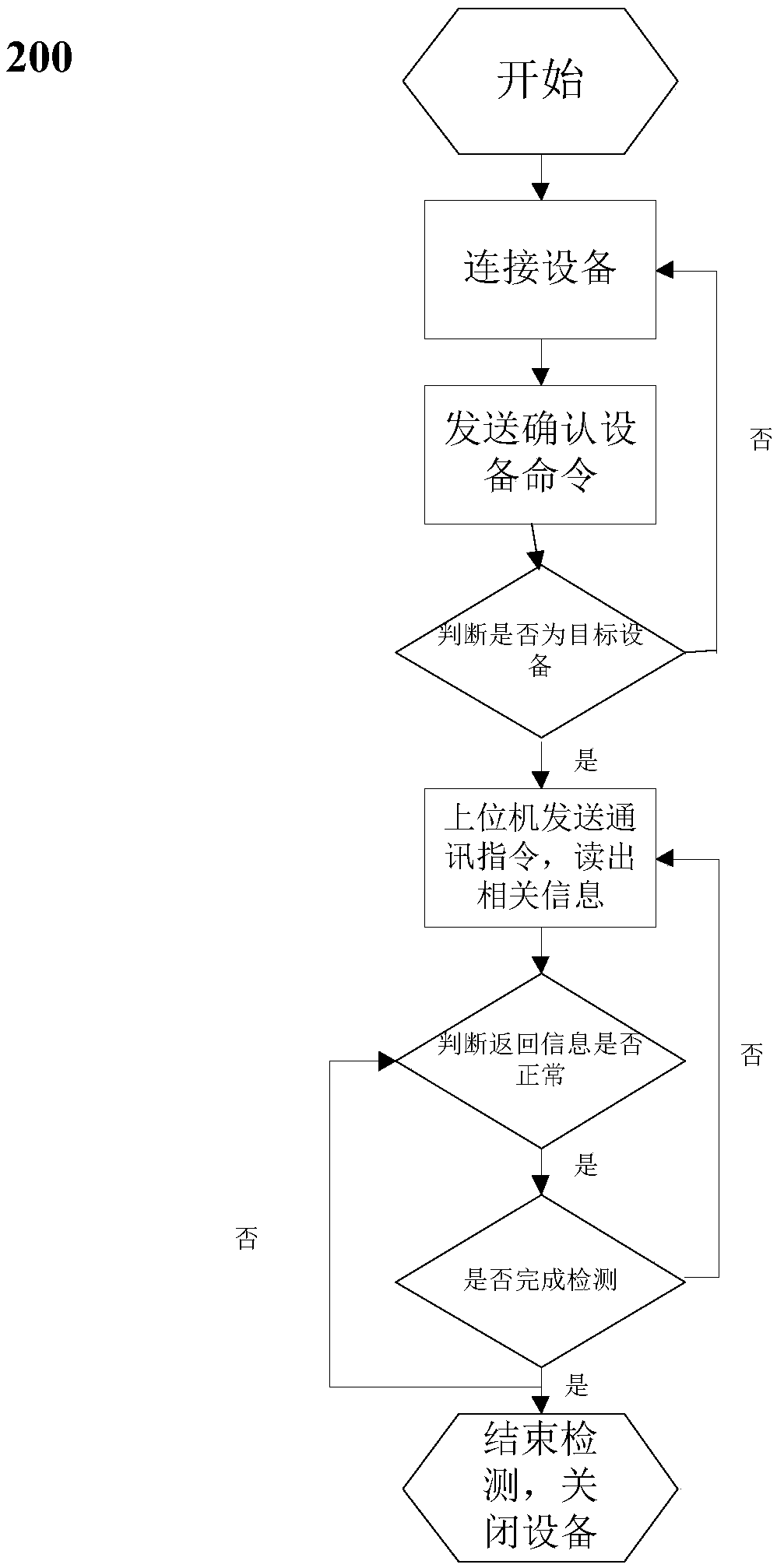
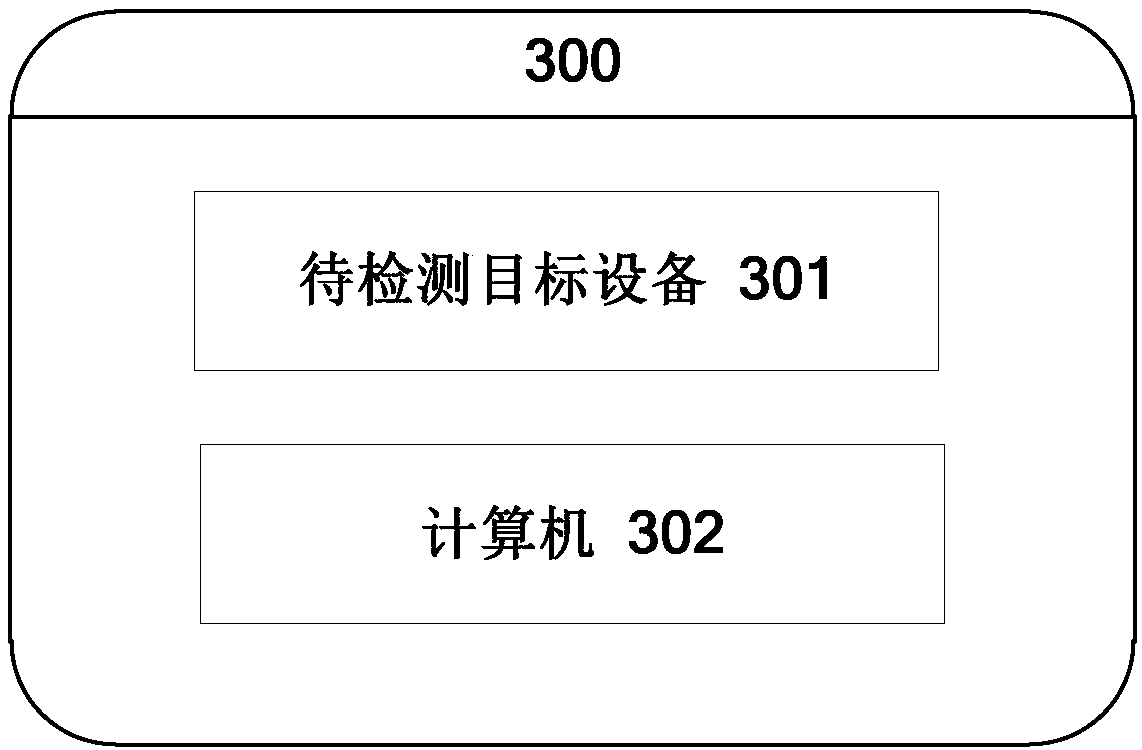
A method and a system for detecting target equipment
PendingCN109684137AReduce dependenceAvoid the risk of being leakedFaulty hardware testing methodsComputer hardwareEquipment use
Owner:AEROSPACE INFORMATION
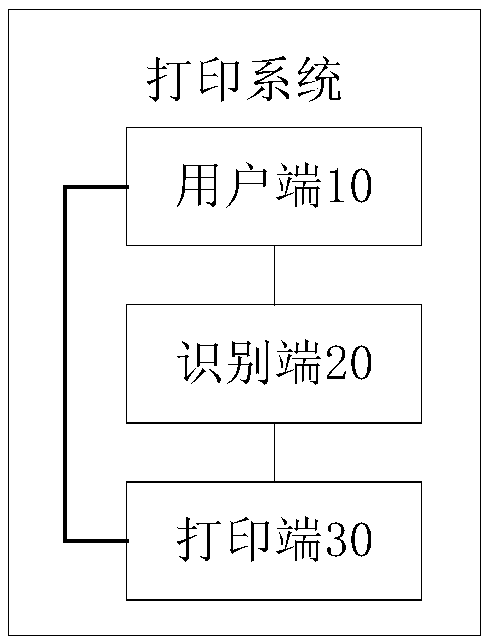
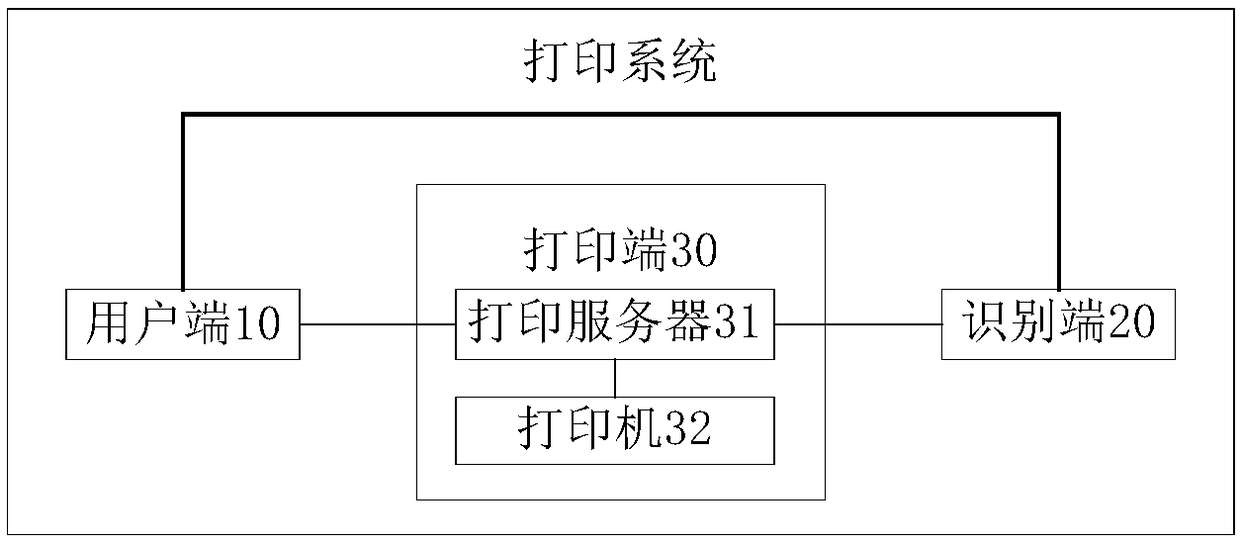
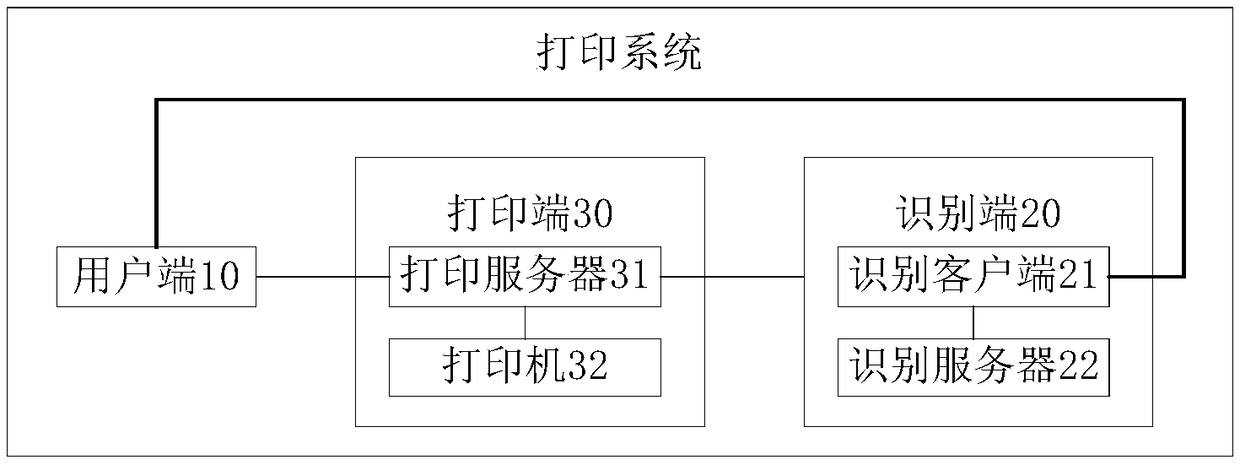
Printing processing method and apparatus, and printing system
InactiveCN109375885AEasy to operateEnsure safetyDigital data protectionDigital output to print unitsImage matchingDatabase
A print processing method and apparatus and a printing system are provided, wherein the system includes a user terminal for transmitting print information to a printing terminal; Wherein the print information is used for indicating a print job to be executed and a user account for initiating the print job; The recognition end is used for acquiring print information sent from the user end to the print end, collecting user images, and performing face recognition on the user images according to the face features corresponding to the user accounts indicated by the print information to determine whether the face features match the user images; a notification message is sent to the printing end if the face feature matches the user image; The printing end is configured to determine a print job tobe executed according to the print information sent by the user end, and execute the print job initiated by the user account indicated by the notification message when the notification message sent by the identification end is received. The system completes the printing task by face recognition, which can simplify the user's operation and ensure the security of the printed document.
Owner:KINGSOFT
Login authentication method and device
ActiveCN107920081BImprove securityAvoid the risk of being leakedMultiple keys/algorithms usageCiphertextPassword
The invention provides a login authentication method and device, and belongs to the technical field of the network. The method comprises the following steps: acquiring ciphertext corresponding to a user identifier from ciphertext information when receiving a login request carrying the user identifier and use password, thereby obtaining the first ciphertext; performing login authentication based onthe first ciphertext and the user password by using a first encryption algorithm; when the first encryption algorithm authenticates that the login request is not passed, performing the login authentication on the login request based on the first ciphertext and the user password by adopting a second encryption algorithm; when the second encryption algorithm authenticates that the login request ispassed, replacing the first ciphertext in the ciphertext information with the second ciphertext; and performing the login authentication on the login request received again based on the second ciphertext in the ciphertext information when receiving the login request carrying the use identifier again. Based on the login authentication scheme provided by the invention, the current service is unnecessary to interrupt when upgrading the encryption algorithm.
Owner:SUZHOU XIQUAN SOFTWARE TECH CO LTD
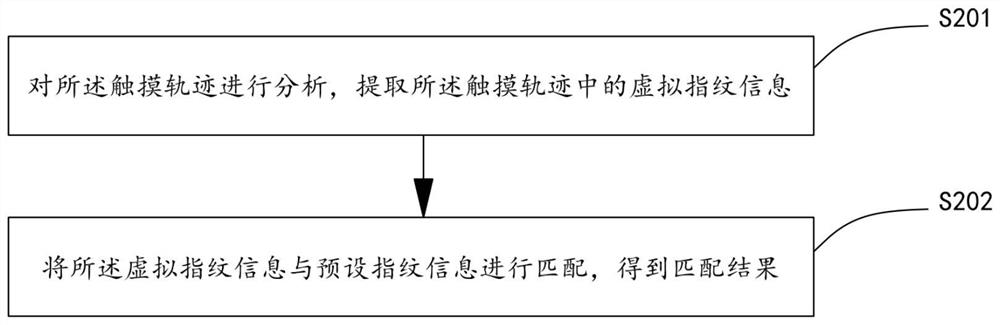
Fingerprint unlocking control method and device, terminal equipment and storage medium
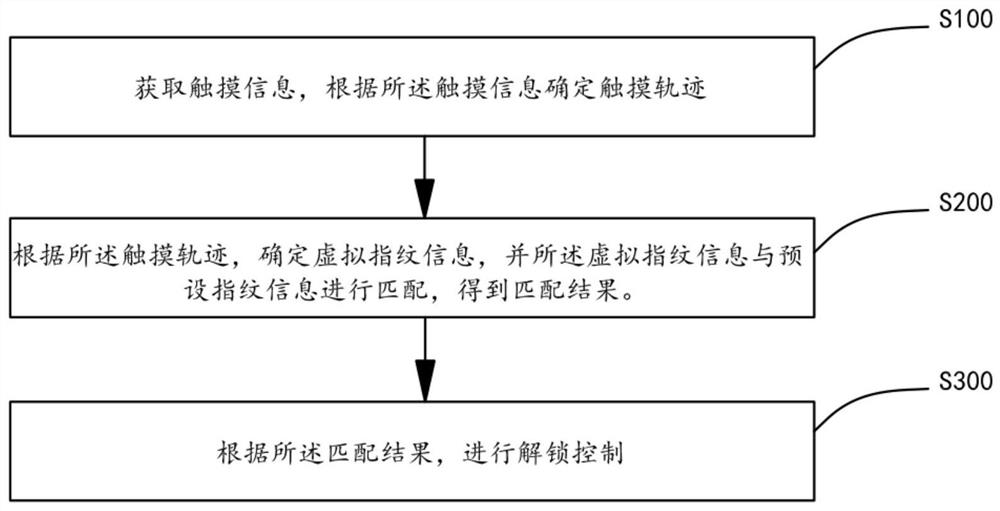
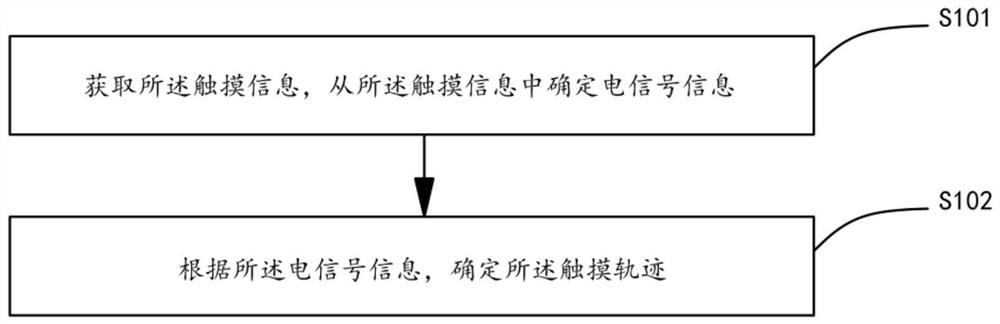
PendingCN113886788AAvoid the risk of being leakedUnlock control implementationCharacter and pattern recognitionDigital data authenticationComputer hardwareTerminal equipment
The invention discloses a fingerprint unlocking control method and device, terminal equipment and a storage medium, and the method comprises the steps: obtaining touch information, and determining a touch track according to the touch information; determining virtual fingerprint information according to the touch track, and matching the virtual fingerprint information with preset fingerprint information to obtain a matching result; and performing unlocking control according to the matching result. The fingerprint touch information for unlocking can be determined as the virtual fingerprint information, and the virtual fingerprint information is matched with the preset fingerprint information, so that unlocking control can be realized without using real fingerprint information, and the risk that the information of the terminal equipment is leaked due to the leakage of the fingerprint information of the user is effectively avoided.
Owner:HUIZHOU TCL MOBILE COMM CO LTD
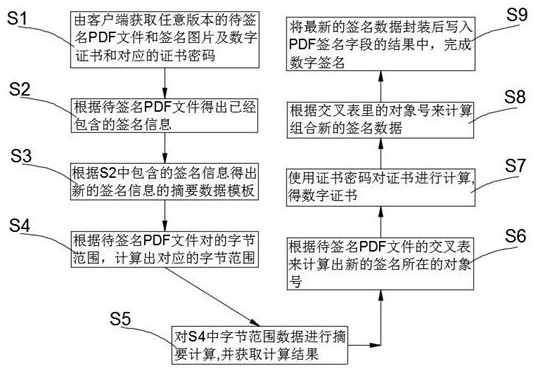
Decentralized multi-digital signature/electronic signature method
PendingCN111723405AAvoid the risk of being leakedReduce riskDigital data protectionDigital identitySignature file
The invention relates to the technical field of network security, in particular to a decentralized multi-digital signature / electronic signature method, which comprises the following steps of: acquiring a PDF file and a signature picture to be signed of any version, a digital certificate and a corresponding certificate password by a client; obtaining an abstract data template of the new signature information; calculating a corresponding byte range and carrying out abstract calculation to obtain an object number where a new signature is located; calculating the certificate to obtain a digital certificate; calculating and combining new signature data according to the object number in the cross table; packaging the latest signature data and writing the packaged signature data into a result ofthe PDF signature field; according to the method, cross-version and cross-platform compatibility of multiple signatures can be realized, offline signature of the to-be-signed data at the local terminal is ensured, and the risk that the to-be-signed data is leaked in transmission and the risk that the digital identity is illegally used and stolen are avoided. Therefore, the development process is more convenient, the electronic signature cannot be tampered, and the data privacy is fully guaranteed.
Owner:上海黔易数据科技有限公司
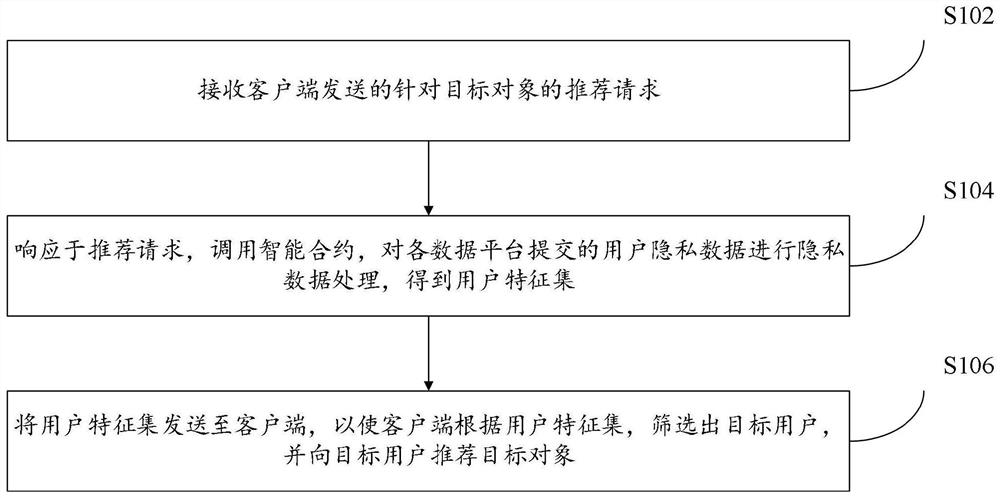
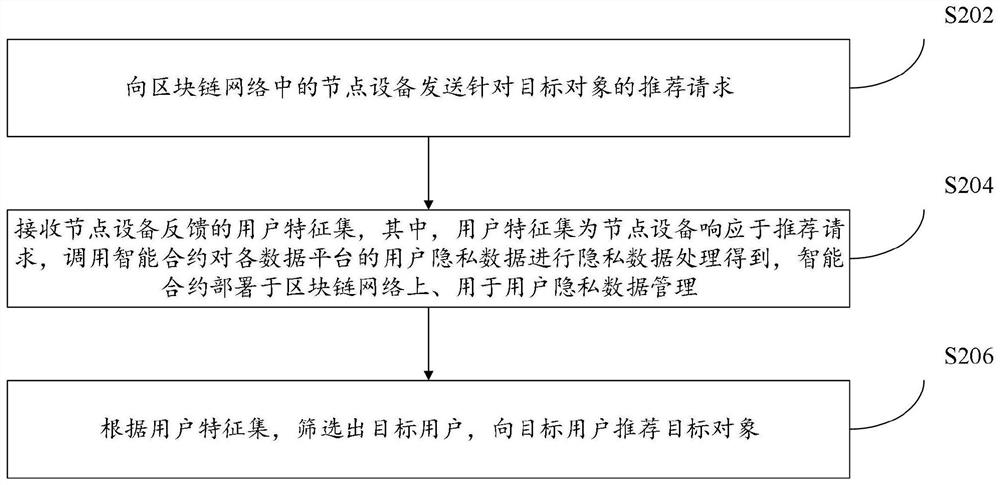
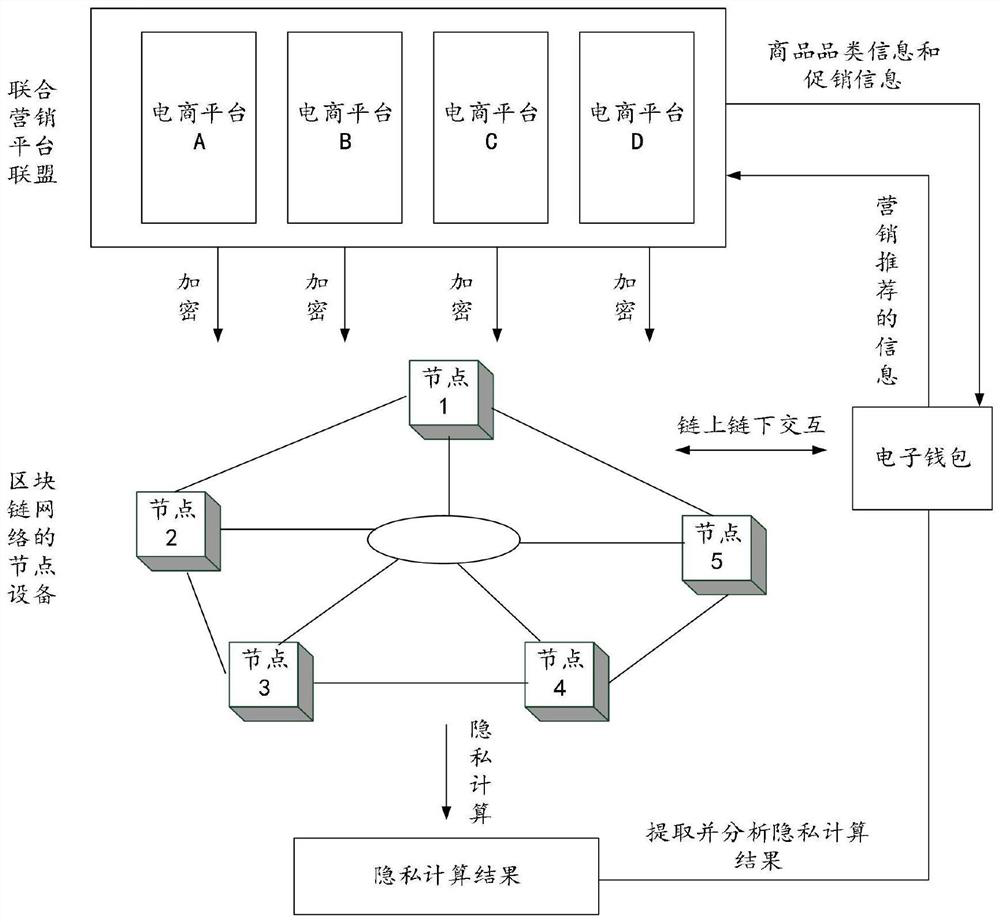
Object recommendation method, device and system based on block chain
PendingCN114579857AEnsure safetyAvoid the risk of being leakedDigital data information retrievalDigital data protectionFeature setData platform
The embodiment of the invention provides an object recommendation method, device and system based on a block chain, and the method is applied to a node device in a block chain network, and comprises the steps: receiving a recommendation request for a target object sent by a client; in response to the recommendation request, calling an intelligent contract, and performing privacy data processing on user privacy data submitted by each data platform to obtain a user feature set; and sending the user feature set to the client, so that the client screens out a target user according to the user feature set, and recommends a target object to the target user. Through the method, the user feature set can be more accurately generated while the security of the user privacy data is ensured, so that the client can recommend the target object to the target user in a more targeted manner.
Owner:ALIPAY LABS SINGAPORE PTE LTD
A systematic software-defined data center network security method
ActiveCN106453406BGuaranteed confidentialityPrevent interception and tamperingTransmissionConfidentialityData center
The invention discloses a systematic software-defined data center network security method which comprises: integration of a secret key management center and SDN (Software-Defined Networking) controllers; fusion of a secret key distribution process and an integration process between the SDN controllers and SDN switches; two-layer encryption between different layers of SDN switches; SDN south bound interface channel encryption between the SDN switches and the SDN controllers; encryption between the SDN controllers; and encryption between the SDN controllers and a management terminal. Compared with the prior art, the systematic software-defined data center network security method disclosed by the invention is related to a plurality of levels and a plurality of links, and can meet systematic software-defined data center network security requirements of protecting confidentiality of interactive data between the management terminal and the SDN controllers, protecting confidentiality of interactive data between the SDN controllers, protecting confidentiality of network databases maintained inside the SDN controllers, protecting confidentiality of channels between the SDN controllers and the SDN switches, protecting confidentiality of data interaction between virtual machines and protecting confidentiality of migration channels of the virtual machines.
Owner:NO 30 INST OF CHINA ELECTRONIC TECH GRP CORP
Method, server and device for preventing message leakage and electronic equipment
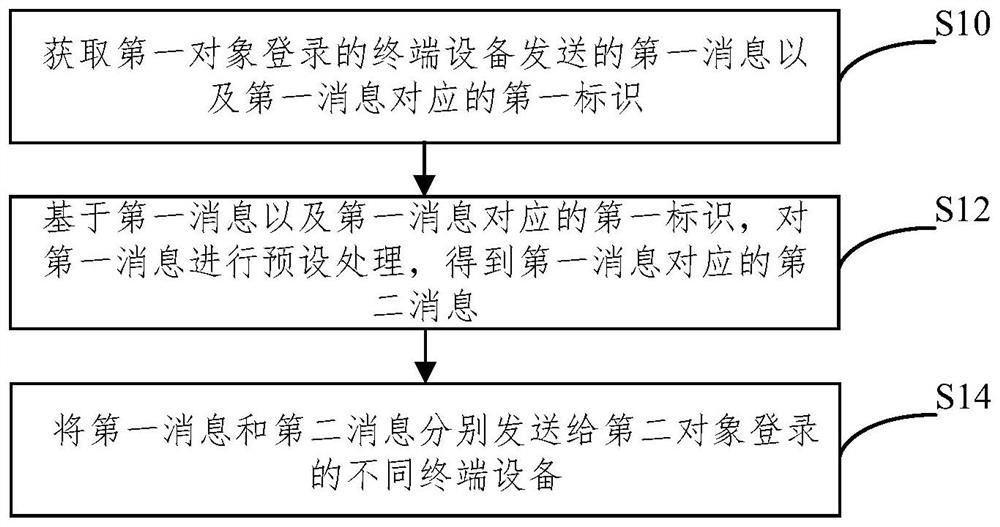
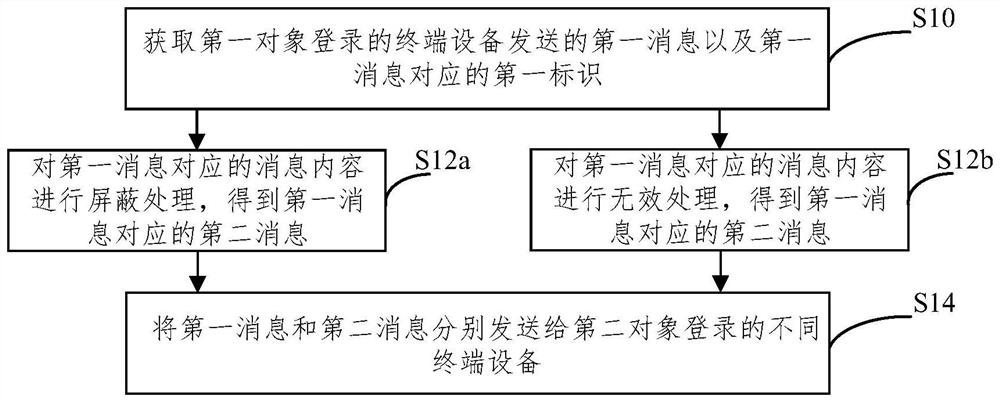
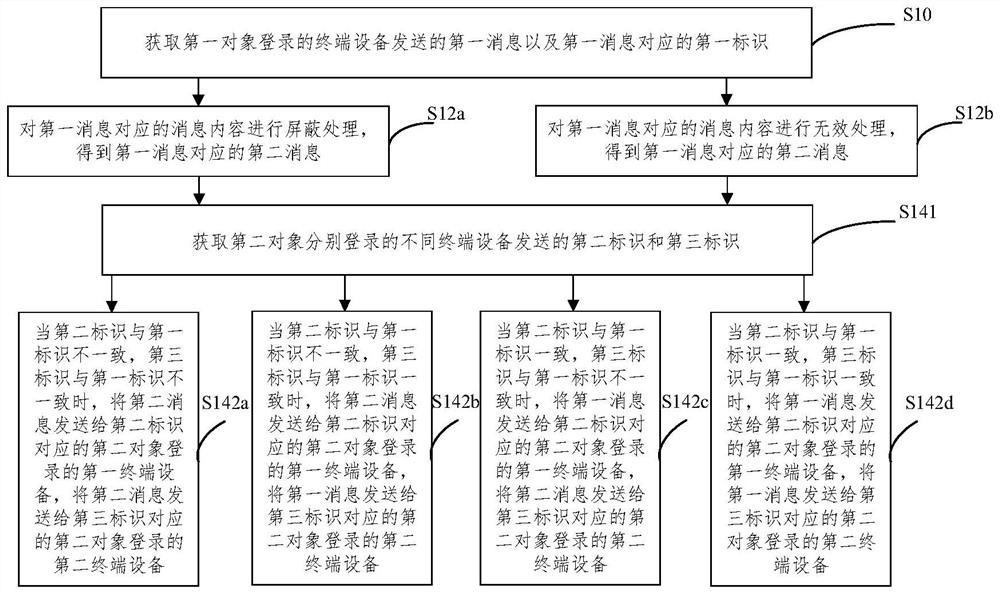
PendingCN114374545AAvoid the risk of being leakedImprove securitySecuring communicationTerminal equipmentMobile end
The invention relates to the technical field of communication, and provides a method for preventing message leakage, a server, a device and electronic equipment. The method comprises the steps that a first message sent by a terminal device logged in by a first object and a first identifier corresponding to the first message are acquired, the first identifier refers to an identifier of a terminal device logged in by a second object having authority to access the first message, and the terminal device comprises at least one of a mobile terminal device and a computer terminal device; based on the first message and a first identifier corresponding to the first message, performing preset processing on the first message to obtain a second message corresponding to the first message; and the first message and the second message are respectively sent to different terminal devices logged in by the second object, so that the risk that the transmission message is leaked can be avoided, and the security of the transmission message is improved.
Owner:BEIJING VRV SOFTWARE CO LTD
A Dense Radiation Imaging System Based on Random Thickness Liquid Mask
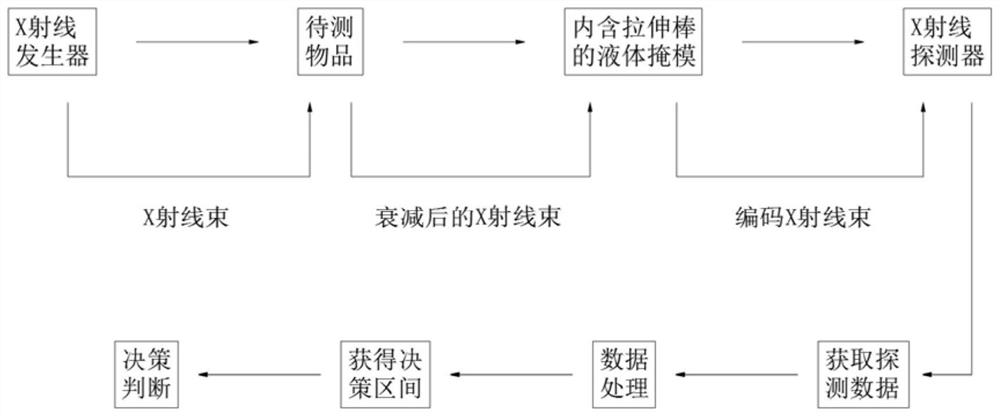
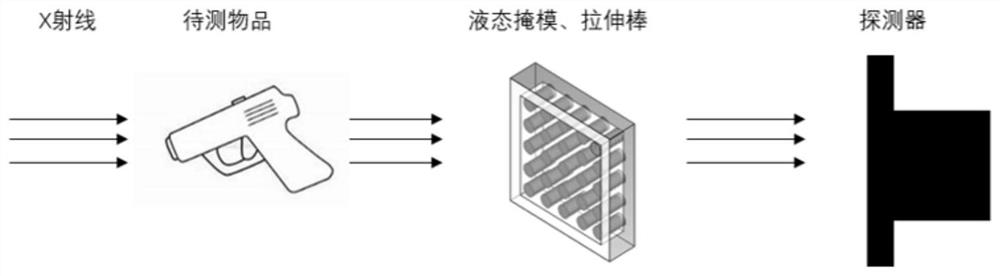
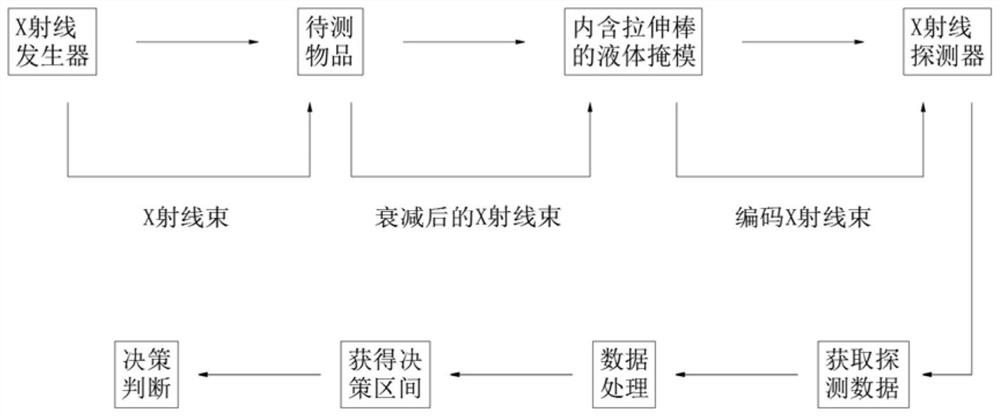
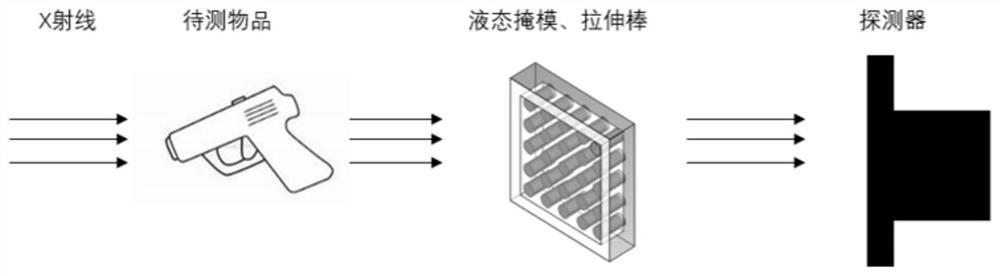
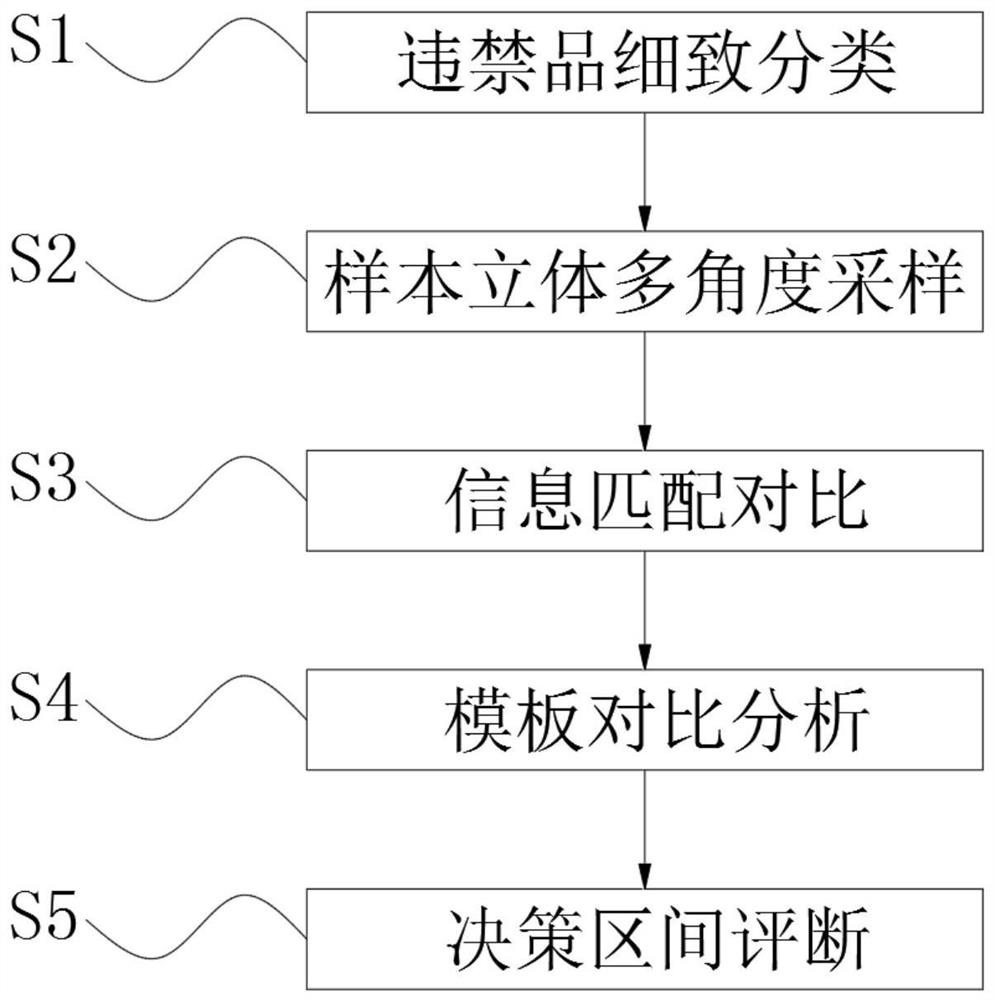
ActiveCN113466956BImplement random decayProtect Sensitive InformationCharacter and pattern recognitionNuclear radiation detectionLiquid stateRadiation imaging
The invention discloses an encrypted radiation imaging system based on a random thickness liquid mask, which includes an X-ray source, an object to be detected, a liquid metal mask, a thickness control array inside the mask, and an X-ray detector. The thickness control array randomly adjusts the thickness of the liquid mask, realizes random attenuation of the X-rays penetrating the mask, and then encrypts the sensitive information carried in the X-ray imaging, effectively protecting the sensitive information of the items to be inspected, and realizing Encryption measures of physical shielding are used for the energy and position information of the emitted particles, and the proposed security inspection technology encrypts the information carried by the emitted X-rays from the physical field, avoiding the risk of private information being leaked, and will not expose any information about the items to be inspected. For privacy information, the template comparison method is used to facilitate the confirmation of whether the items to be inspected contain contraband, and the security inspection is realized on the basis of protecting the sensitive information of the inspected items.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
Security Information Interaction Method Based on Internet
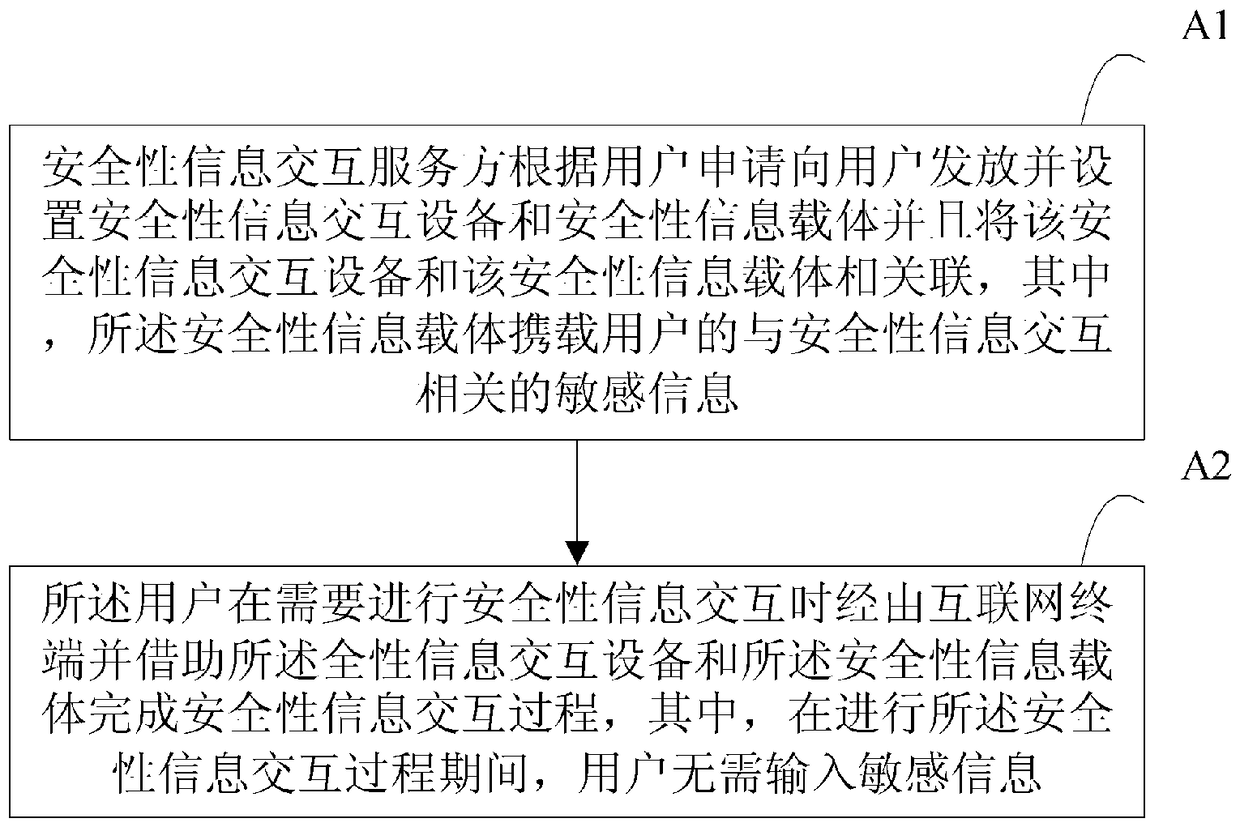
ActiveCN105592032BAvoid the risk of being leakedAvoid risk of leakageSecuring communicationUser needsInternet privacy
The present invention proposes an Internet-based security information interaction method, which includes: the security information interaction service party distributes and sets security information interaction equipment and security information carriers to users according to user applications, and uses the security information interaction equipment Associated with the security information carrier, wherein the security information carrier carries the user's sensitive information related to security information interaction; when the user needs to perform security information interaction The security information interaction device and the security information carrier complete the security information interaction process, wherein during the security information interaction process, the user does not need to input sensitive information. The Internet-based safety information interaction method disclosed by the invention has high safety and is convenient to use.
Owner:CHINA UNIONPAY
A mobile terminal payment password transmission system and method
InactiveCN103825740BAvoid the risk of being leakedEnsure safetyUser identity/authority verificationProtocol authorisationPlaintextCiphertext
The invention discloses a mobile terminal?payment password?transmission system and a method, and relates to the field of mobile payment. The payment password?transmission system comprises a mobile payment?module,?a payment platform, a safety payment?module, and a password keyboard module for inputting a payment password. According to the payment password?transmission method, the safety payment?module and the payment platform are mutually authenticated and an authentication key is generated; the payment password is inputted via the password keyboard module and uses the authentication key for encryption; decryption and encryption again are carried out via the safety payment?module, a payment password ciphertext is formed to be transmitted to the password keyboard module, and the password keyboard module transmits the payment password ciphertext to the mobile payment?module for use. During the payment password use process, the mobile payment?module can not touch a payment password plaintext, and the risk that the payment password is leaked can thus avoided.
Owner:武汉擎动网络科技有限公司
High-strength encryption system and method based on user privacy information protection
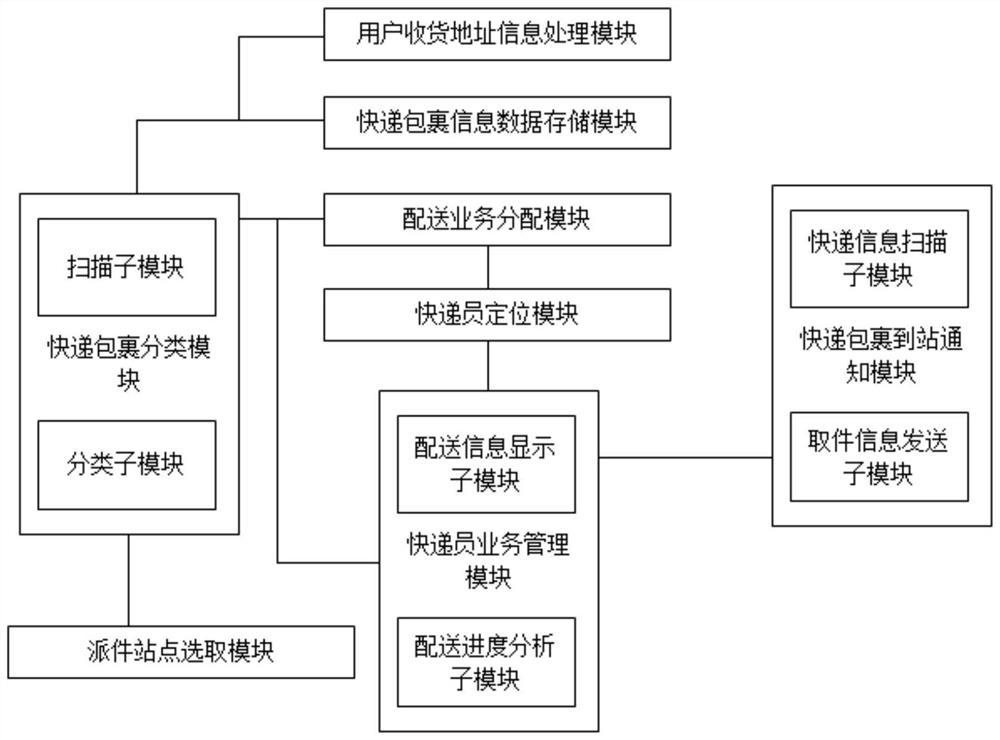
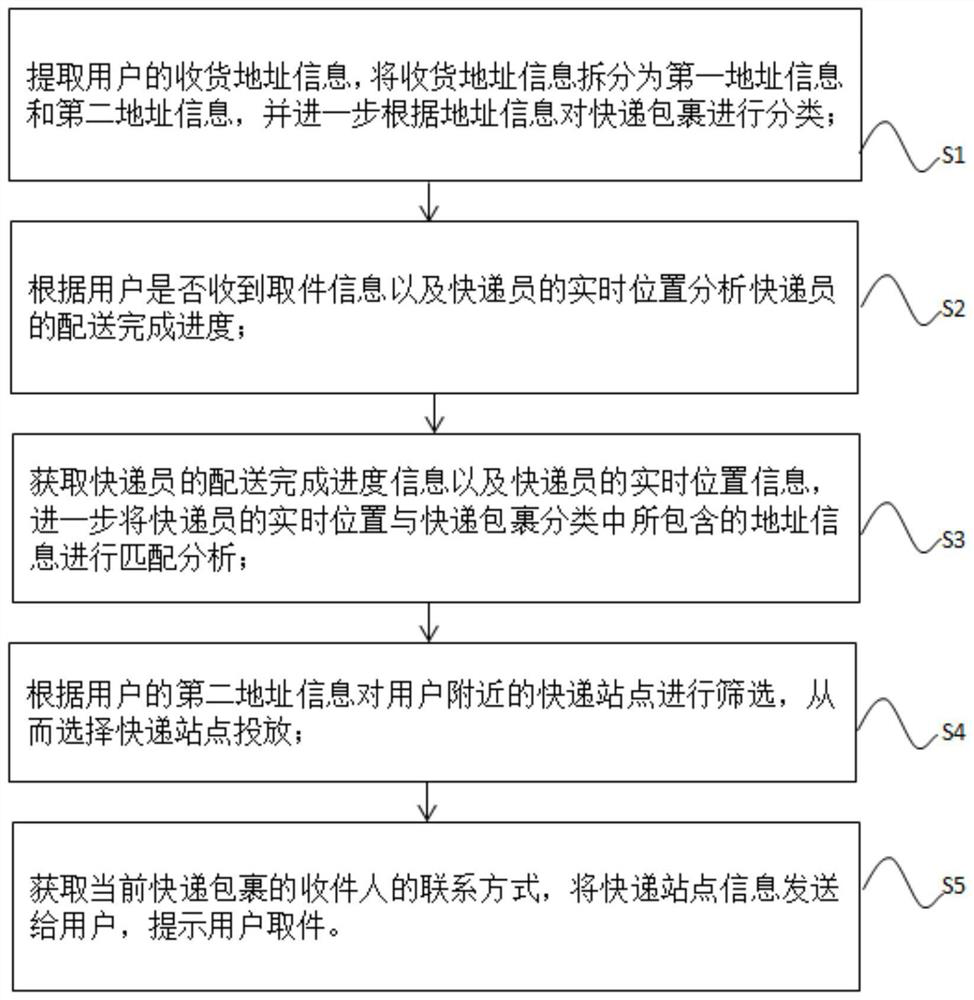
ActiveCN113111362AGuarantee privacy and securityAvoid the risk of being leakedDigital data protectionLogisticsInformation processingUser privacy
The invention discloses a high-strength encryption system and method based on user privacy information protection. The high-strength encryption system comprises an express parcel information data storage module, an express parcel classification module, a courier positioning module, a distribution service distribution module, a user delivery address information processing module, a delivery site selection module, an express parcel arrival notification module and a courier service management module. The beneficial effects of the invention are that the express parcels are classified according to the split address information by splitting the receiving address of the user, so that the risk that the address of the user is leaked is avoided, and the privacy security of the user is guaranteed; and, in addition, the delivery completion progress of the courier is analyzed and the real-time position information of the courier is acquired, so that task allocation is further performed on the courier according to the real-time position information, the delivery completion progress and the express classification, and the express delivery efficiency is improved.
Owner:四川旅投数字信息产业发展有限责任公司
Digital signature processing method, device, computer equipment and storage medium
ActiveCN111464315BEnhance asset securityImprove securityFinanceUser identity/authority verificationComputer networkDigital signature
The embodiment of the present application discloses a digital signature processing method, device, computer equipment, and storage medium. The digital signature processing method includes: the signature node acquires consumption credential information for the first credential user, and acquires the first digital signature of the consumer credential information ; The signing node uses the private key of the second credential user associated with the first credential user to sign the consumption credential information to obtain the second digital signature; the signature node sends the consumer credential information, the first digital signature and the second digital signature To the consensus node, instruct the consensus node to verify the first digital signature and the second digital signature, and make the consensus node add the consumption certificate information to the business block chain after the first digital signature and the second digital signature are both verified. By adopting the application, the security of the user's private key can be enhanced.
Owner:TENCENT TECH (SHENZHEN) CO LTD
An authentication method, server, and access control device
ActiveCN106657152BAvoid the risk of being leakedEnsure safetyUser identity/authority verificationPasswordEngineering
Owner:TENCENT TECH (SHENZHEN) CO LTD
A method, server and cloud disk client for loading communication information
ActiveCN104580429BEnsure safetySolve the problem that communication information cannot be loadedTransmissionInternet privacyClient-side
Owner:BEIJING QIHOO TECH CO LTD
Encrypted radiation imaging system based on random thickness liquid mask
ActiveCN113466956AAvoid being leakedMeet security inspection requirementsCharacter and pattern recognitionNuclear radiation detectionSecurity checkLiquid state
The invention discloses an encrypted radiation imaging system based on a random thickness liquid mask, which comprises an X-ray source, an object to be detected, a liquid metal mask, a mask internal thickness control array and an X-ray detector. According to the invention, the thickness of the liquid mask is randomly adjusted through the mask internal thickness control array, the X-ray passing through the mask is attenuated randomly, sensitive information carried in X-ray imaging is encrypted, the sensitive information of a to-be-detected object is effectively protected, physical shielding encryption measures are adopted for energy and position information of emitted particles, the proposed security check technology encrypts information carried by the emergent X-rays from the physical field, the risk that privacy information is leaked is avoided, any privacy information of the to-be-checked article is not exposed, whether the to-be-checked article contains contraband articles or not is conveniently confirmed by adopting a template comparison method, and the security check is carried out on the basis of protecting the sensitive information of the checked article.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
Personalized association method and system for vehicle setting and vehicle
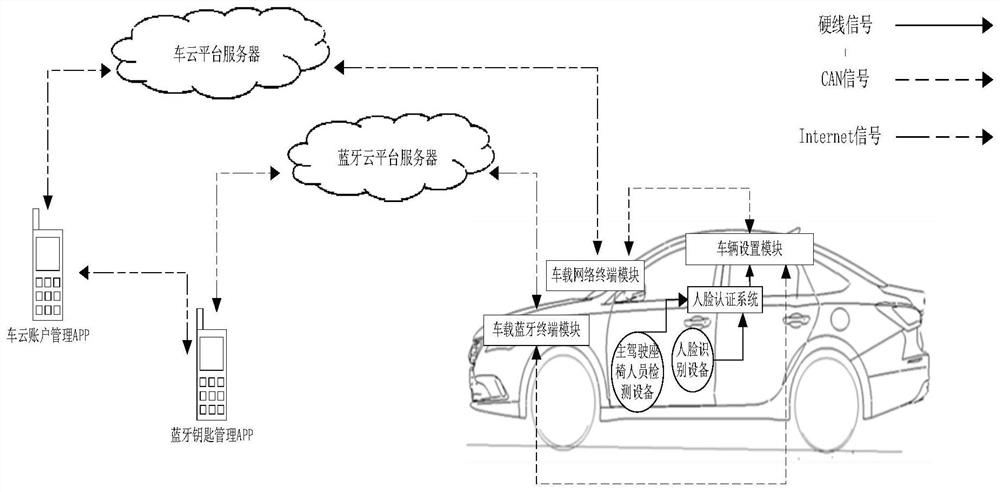
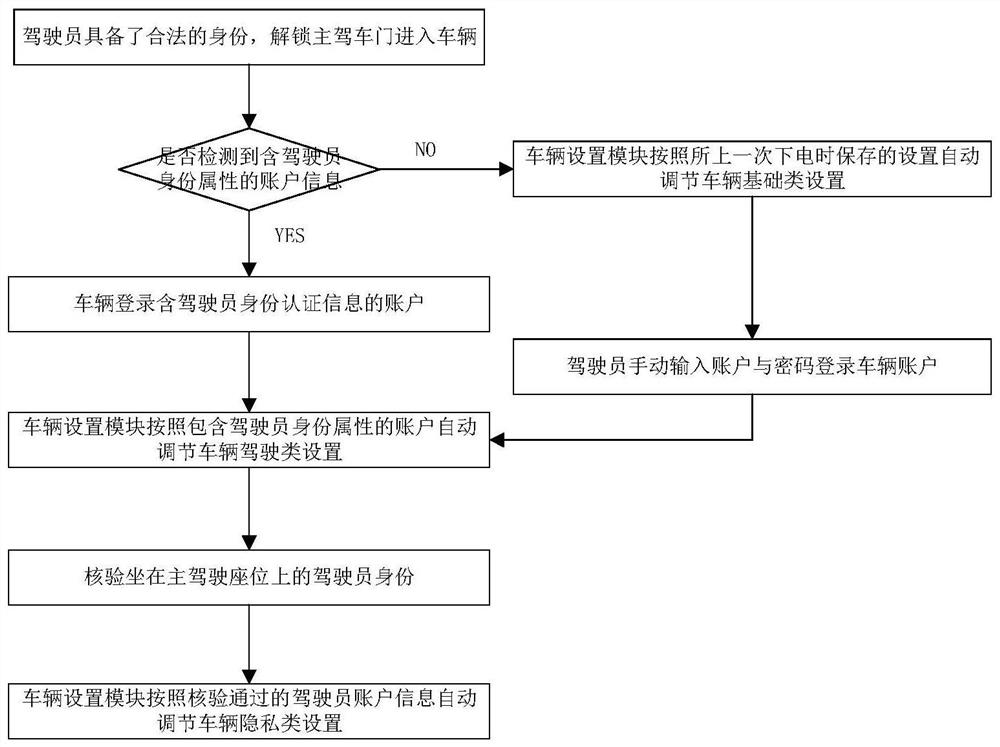
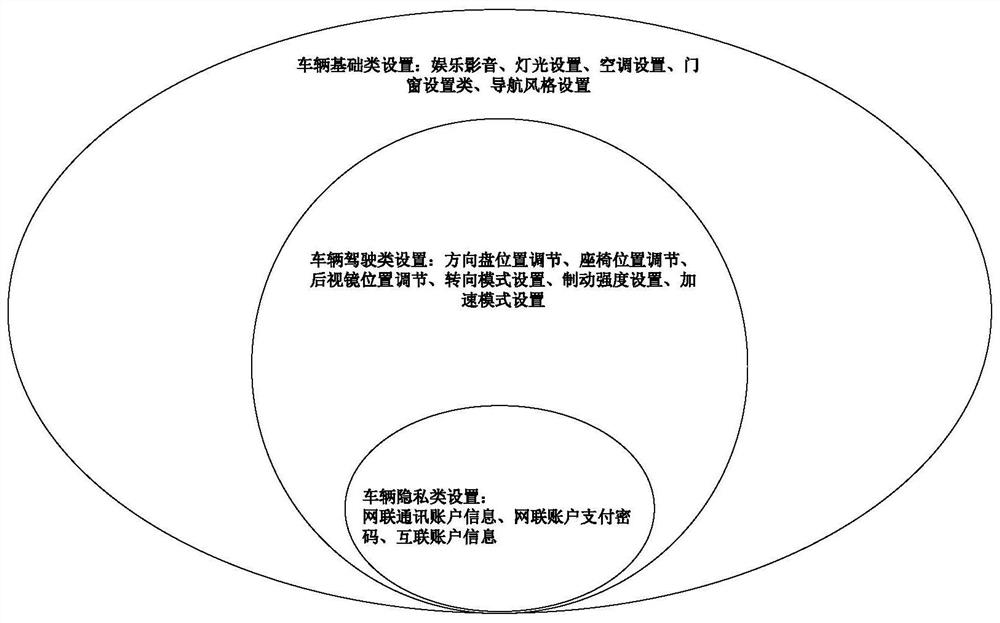
ActiveCN114422550AGuaranteed privacyMeet different needsDigital data authenticationIndividual entry/exit registersPersonalizationDriver/operator
The invention provides a whole vehicle setting personalized association method, which comprises the following steps that: a vehicle setting module executes vehicle door unlocking and whole vehicle power-on after collecting a vehicle door unlocking request; after the whole vehicle is powered on, the vehicle setting module judges whether a pre-associated vehicle cloud account exists or not based on the vehicle door unlocking request; if the pre-associated vehicle cloud account exists, the vehicle setting module automatically logs in the pre-associated vehicle cloud account; after the vehicle cloud account is automatically logged in, the vehicle setting module adjusts the associated vehicle basic class setting according to the vehicle basic class setting information recorded in the vehicle cloud account; and after the driver enters the vehicle, the vehicle setting module adjusts preset vehicle basic type setting, vehicle driving type setting and / or vehicle privacy type setting based on the type to which the vehicle door unlocking request belongs.
Owner:深蓝汽车科技有限公司
Security Information Interaction Method Based on Customizable Browser
ActiveCN104348807BAvoid the risk of being leakedImprove securityData switching networksInternet privacyService provision
The invention brings forward a security information interaction method based on a customizable browser. The method comprises the steps that a user logs in a service provider server via an internet terminal and applies for a customized browser which is related to one or multiple security carriers possessed by the user; the customized browser is generated by the service provider server based on the application of the user; the user downloads the customized browser and installs the customized browser in a trusted processor; and the user performs the related security information interaction process via the customized browser installed in the trusted processor. The security information interaction method based on the customizable browser has enhanced security and is convenient to use.
Owner:CHINA UNIONPAY
Identity authentication method for security information exchange
ActiveCN104980276BAvoid the risk of being leakedImprove securityUser identity/authority verificationService provisionSecurity information
The present invention proposes an identity authentication method for security information interaction, which includes the following steps: the user acquires a security device containing a security chip from a service provider and performs an initialization operation to activate the security device; the user uses the security chip to activate the security device; The activated security device initiates and completes the security information exchange process. The identity authentication method for security information interaction disclosed by the invention has high security and is convenient to use.
Owner:CHINA UNIONPAY
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com