Identity authentication method for security information interaction
A security information and identity authentication technology, applied in user identity/authority verification, electrical components, transmission systems, etc., can solve problems such as poor convenience and versatility, malicious theft, and low security, and achieve a high degree of ease of use, The effect of avoiding leakage and high security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
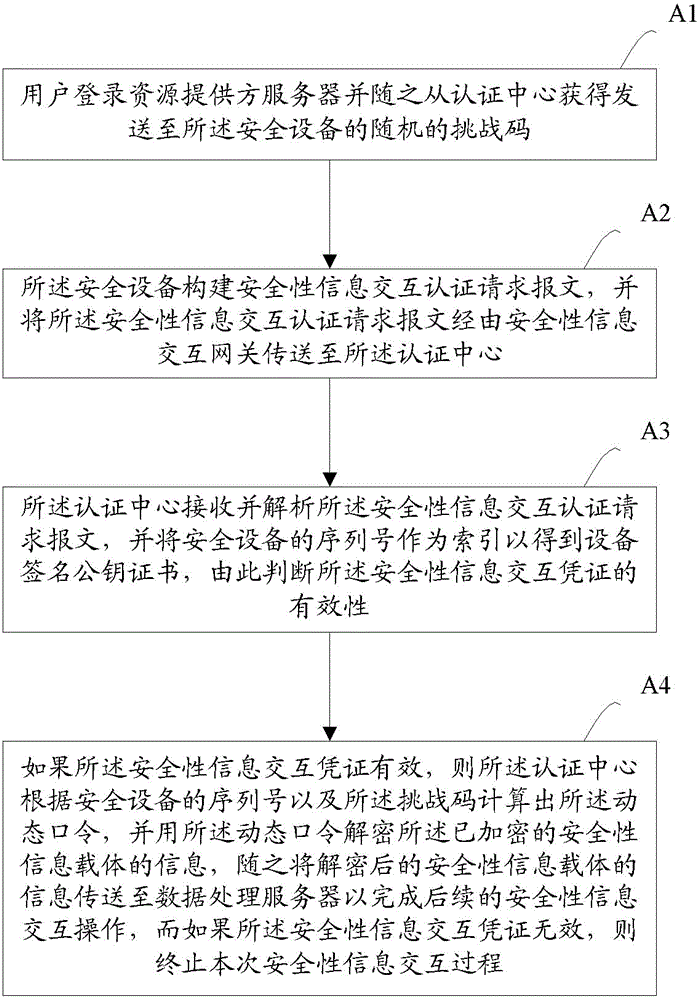
[0034] figure 1 It is a flow chart of the key process of the identity authentication method for security information interaction according to the embodiment of the present invention. like figure 1 As shown, the identity authentication method for security information interaction disclosed in the present invention includes the following steps: (A1) The user obtains a security device containing a security chip from a service provider and performs an initialization operation to activate the security device; ( A2) The user initiates and completes the security information interaction process by means of the activated security device.
[0035]Preferably, in the identity authentication method for security information interaction disclosed in the present invention, the initialization operation includes combining information (such as card number) of at least one security information carrier (such as a bank card) of the user with the security The device is bound, and the binding relati...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com