Payment authentication method and payment authentication system
A technology for payment authentication and authentication equipment, which is applied in payment systems, payment architectures, instruments, etc., and can solve problems such as user loss, easy leakage of credentials, and outstanding security issues in the field of mobile payment.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
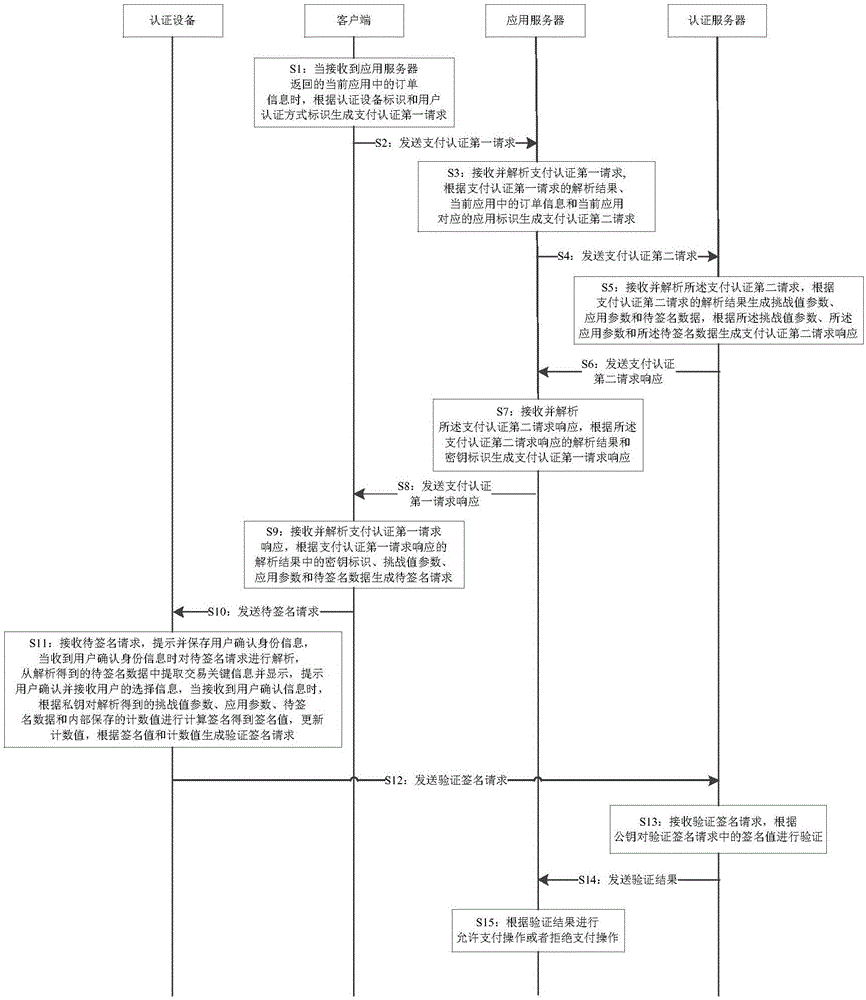
[0143] Such as figure 1 As shown, the first embodiment provides a payment authentication method, including the following steps:
[0144] Step S1: When the client receives the order information in the current application returned by the application server, the client generates a first request for payment authentication according to the authentication device ID and the user authentication mode ID;
[0145] In step S1 of this embodiment, before the client generates the first payment authentication request according to the authentication device ID and the user authentication mode ID, any one of steps B, R, and T is included,
[0146] Step B: the client sends a request to obtain the device ID and the user authentication mode ID to the authentication device, and the authentication device sends the authentication device ID and the user authentication mode ID to the client;
[0147] Step R: the client sends a request to obtain the authentication device identifier to the authenticatio...
Embodiment 2
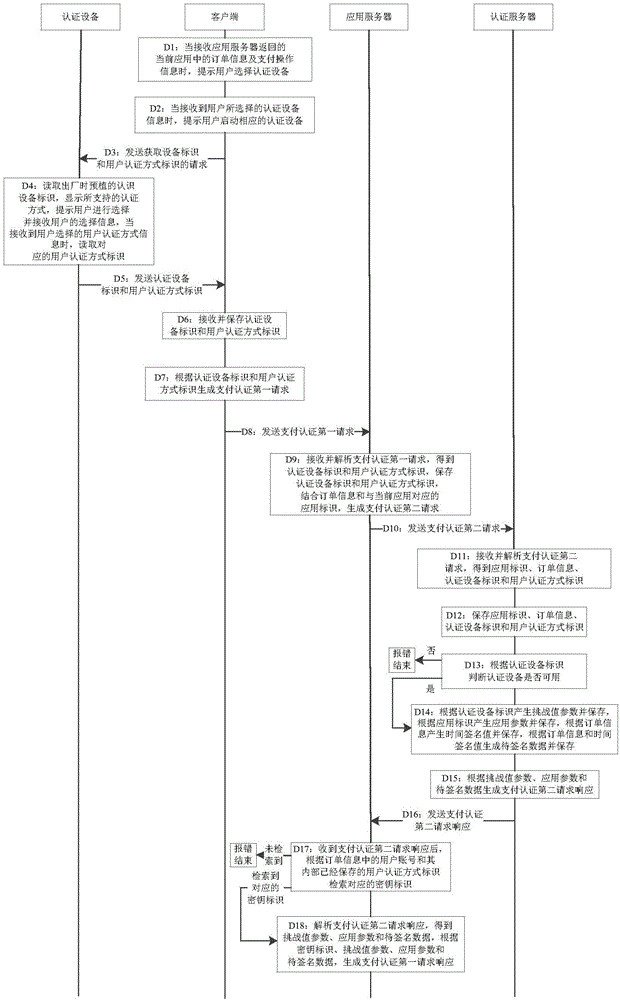
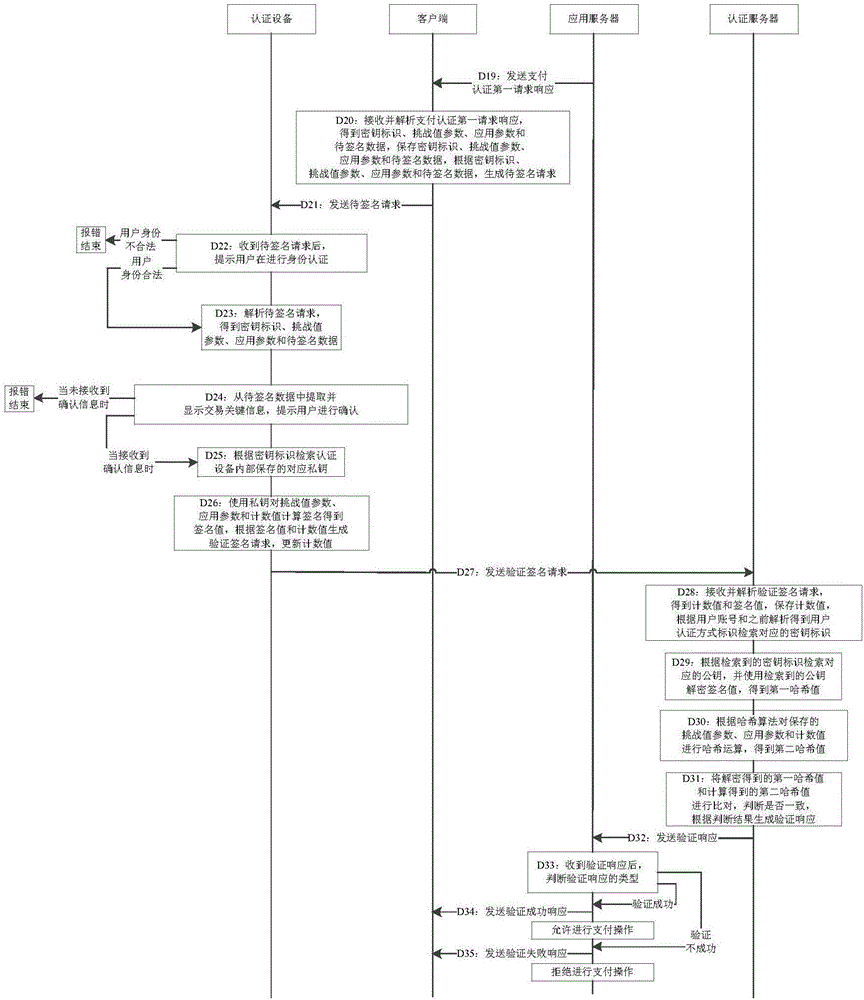
[0191] Such as figure 2 and 3 As shown, the second embodiment provides a payment authentication method, including the following steps:
[0192] Step D1: When the client receives the order information and payment operation information in the current application returned by the application server, prompt the user to select an authentication device;
[0193] Step D2: When the client receives the authentication device information selected by the user, it prompts the user to activate the corresponding authentication device;
[0194] Step D3: The client sends a request to obtain the device ID and the user authentication mode ID to the authentication device;
[0195] For example, the request to obtain the device ID and user authentication mode ID is: 0x00c7000009;
[0196] Step D4: The authentication device reads the authentication device logo pre-planted at the factory, displays the supported user authentication methods, prompts the user to make a choice and receives the user's ...
Embodiment 3
[0333] Such as image 3 and 4 As shown, the third embodiment provides a payment authentication method, including the following steps:
[0334] Step M1: When the client receives the order information and payment operation information in the current application returned by the application server, the user is prompted to select an authentication device;
[0335] Step M2: When the client receives the authentication device information selected by the user, the client prompts the user to activate the corresponding authentication device;
[0336] Step M3: The client judges whether the corresponding authentication device ID has been saved internally. If the client has saved the authentication device ID, execute step M12. If the client does not save the authentication device ID, execute step M4;
[0337] Specifically, step M3 includes: the client judges according to the user account number in the order information whether the corresponding authentication device identifier has been st...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com