Login authentication method and device
A technology for login authentication and login request, applied in the network field, it can solve problems such as interruption of business, and achieve the effect of avoiding leakage, expanding the scope of application, and having strong practicability.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0035] In order to make the purpose, technical solution and advantages of the present disclosure clearer, the implementation manners of the present disclosure will be further described in detail below in conjunction with the accompanying drawings.
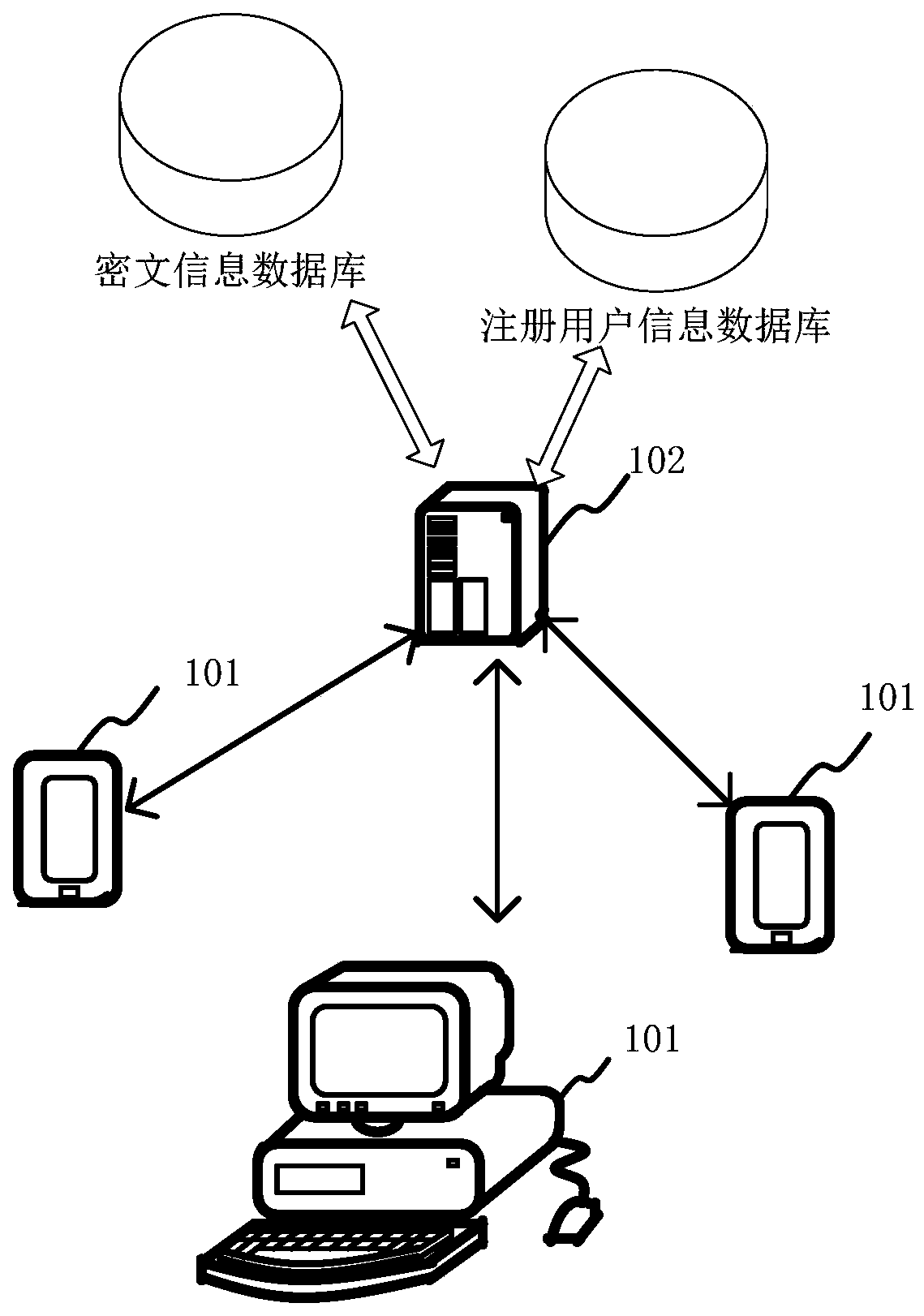
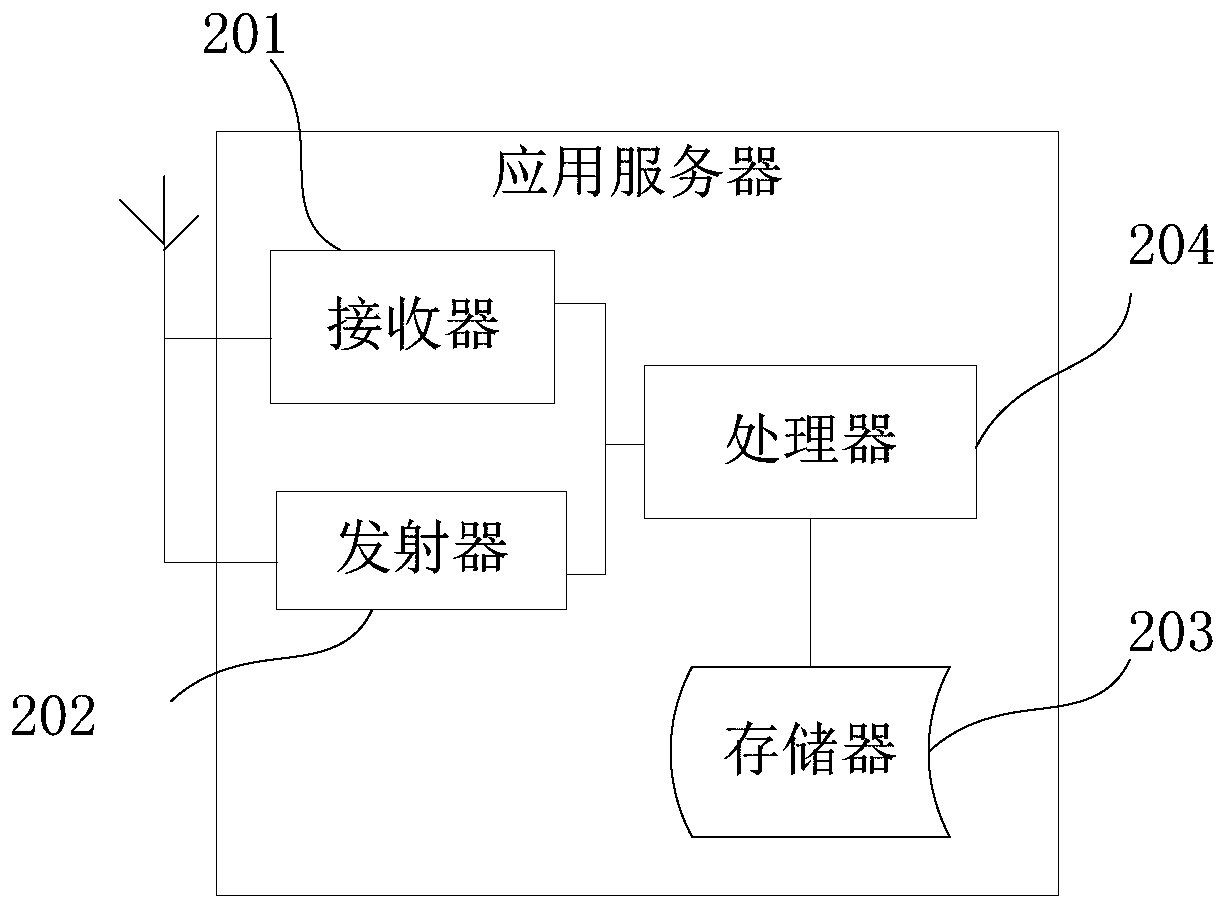
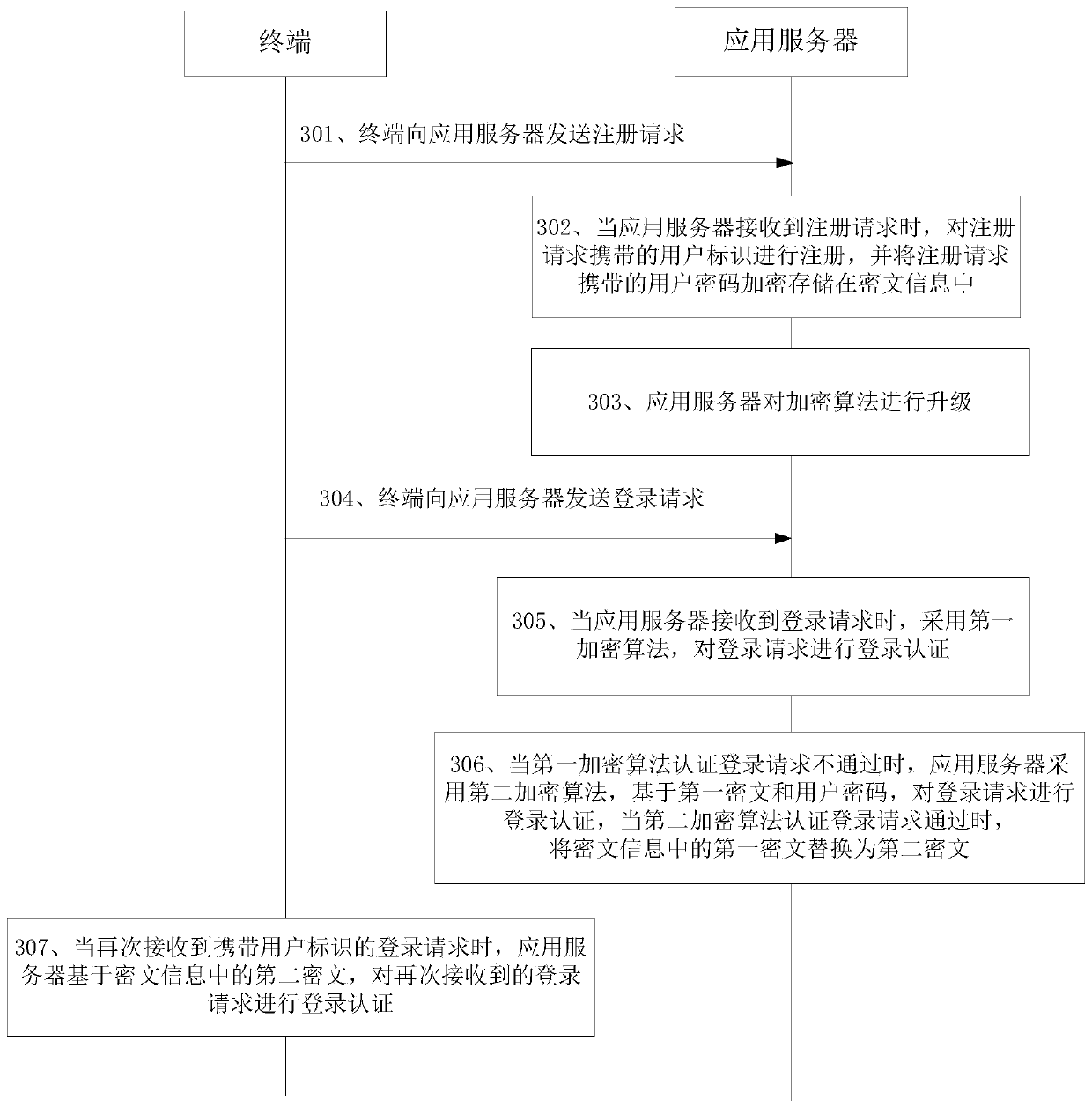
[0036] figure 1 is a schematic diagram of an implementation environment provided by an embodiment of the present disclosure, such as figure 1 As shown, the implementation environment includes multiple terminals 101 and application servers 102 . Each terminal 101 can be connected to the application server 102 through a wireless or wired network, and each terminal 101 can be a desktop computer, a notebook computer, a mobile phone, etc., and the application server 102 can be a server, or a server cluster composed of several servers , or a cloud computing service center. Optionally, the application server 102 may also have at least one type of database, such as a ciphertext information database, a registered user information database...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com