Identity authentication method and system based on telecommunication smart card
An identity authentication and smart card technology, applied in the field of communications, can solve the problems of multiple entry of reserved information and additional carrying, and achieve the effect of improving security and realizing storage.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0032] For the sake of understanding, the related terms involved in this application will be explained first.
[0033] 1. Smart card
[0034] Smart card Generic term for plastic cards with embedded microchips. Some smart cards contain a microelectronic chip, and the smart card needs to exchange data through a reader. The integrated circuit in the smart card includes a central processing unit (CPU), random access memory (RAM) and an in-card operating system solidified in the read-only memory. The data in the card is divided into external reading and internal processing parts. , which can handle a large amount of data by itself. At present, smart cards are mainly divided into two categories, one is operator smart cards, and the other is financial smart cards.
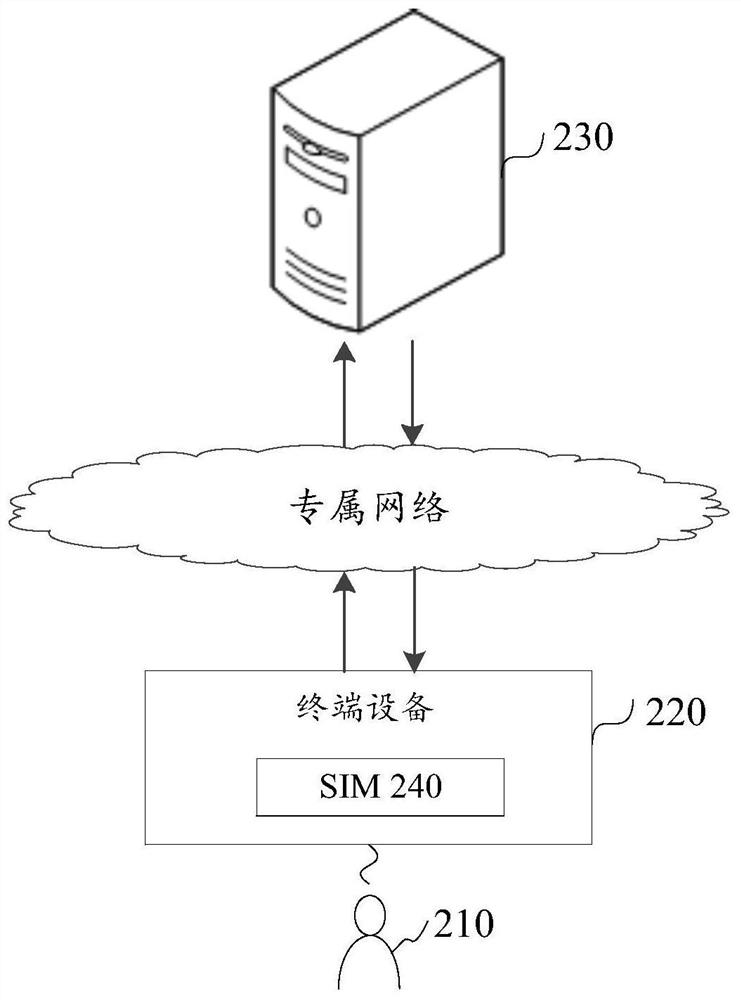
[0035] For the operator's smart card, for example, the subscriber identity module (SIM card for short) is the identity authentication card held by the mobile users of the global system for mobile communications (GSM), ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com