Decentralized multi-digital signature/electronic signature method
A digital signature and decentralization technology, applied in the field of network security, can solve problems such as malicious tampering, and achieve high security, data privacy protection, and convenient development process
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
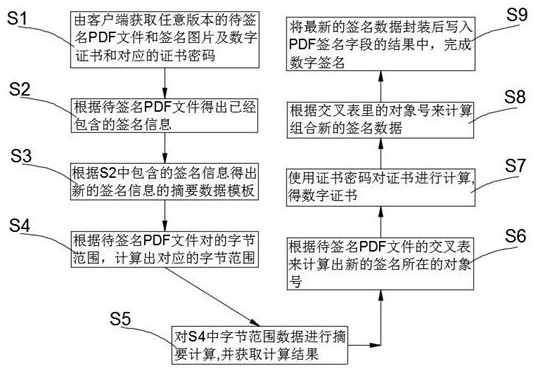
[0032] This embodiment discloses as figure 1 A decentralized multi-digital signature / electronic signature method shown includes the following steps:
[0033] S1 The client obtains any version of the PDF file to be signed, the signature image, the digital certificate and the corresponding certificate password;
[0034] S2 obtains the included signature information according to the PDF file to be signed;
[0035] S3 derives the summary data template of the new signature information according to the signature information contained in S2;
[0036] S4 calculates the corresponding byte range according to the byte range of the PDF file to be signed;
[0037] S5 performs digest calculation on the byte range data in S4, and obtains the calculation result;
[0038] S6 calculates the object number where the new signature is located according to the crosstab of the PDF file to be signed;
[0039] S7 uses the certificate password to calculate the certificate and obtain the digital cert...
Embodiment 2
[0049] This embodiment discloses an RSA algorithm, and its digital signature technology is actually realized through a Hash function. If the file changes, the value of the digital signature will also change accordingly. Different files will get different digital signatures. One of the simplest Hash functions is to add up the binary codes of the files and take the last few bits. The Hash function is public to both parties sending the data.
[0050] The implementation of RSA algorithm includes: key generation, encryption algorithm and decryption algorithm. The security of the RSA system mainly depends on the difficulty of decomposing large prime numbers. In order to ensure the security of the RSA system, each parameter must be carefully selected. The selection of p and q must be a prime number, and the two numbers must be sufficient, because n=pq, making n-factorization computationally infeasible. Therefore, when implementing the RSA algorithm in a computer, it is necessary ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com