A Method of User Authorization on Demand Supporting Least Privilege
A user and privileged technology, applied in the direction of instruments, digital data authentication, electronic digital data processing, etc., can solve problems such as incompletion, security risks, and non-compliance with the principle of least privilege, and achieve the effect of minimizing authority
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
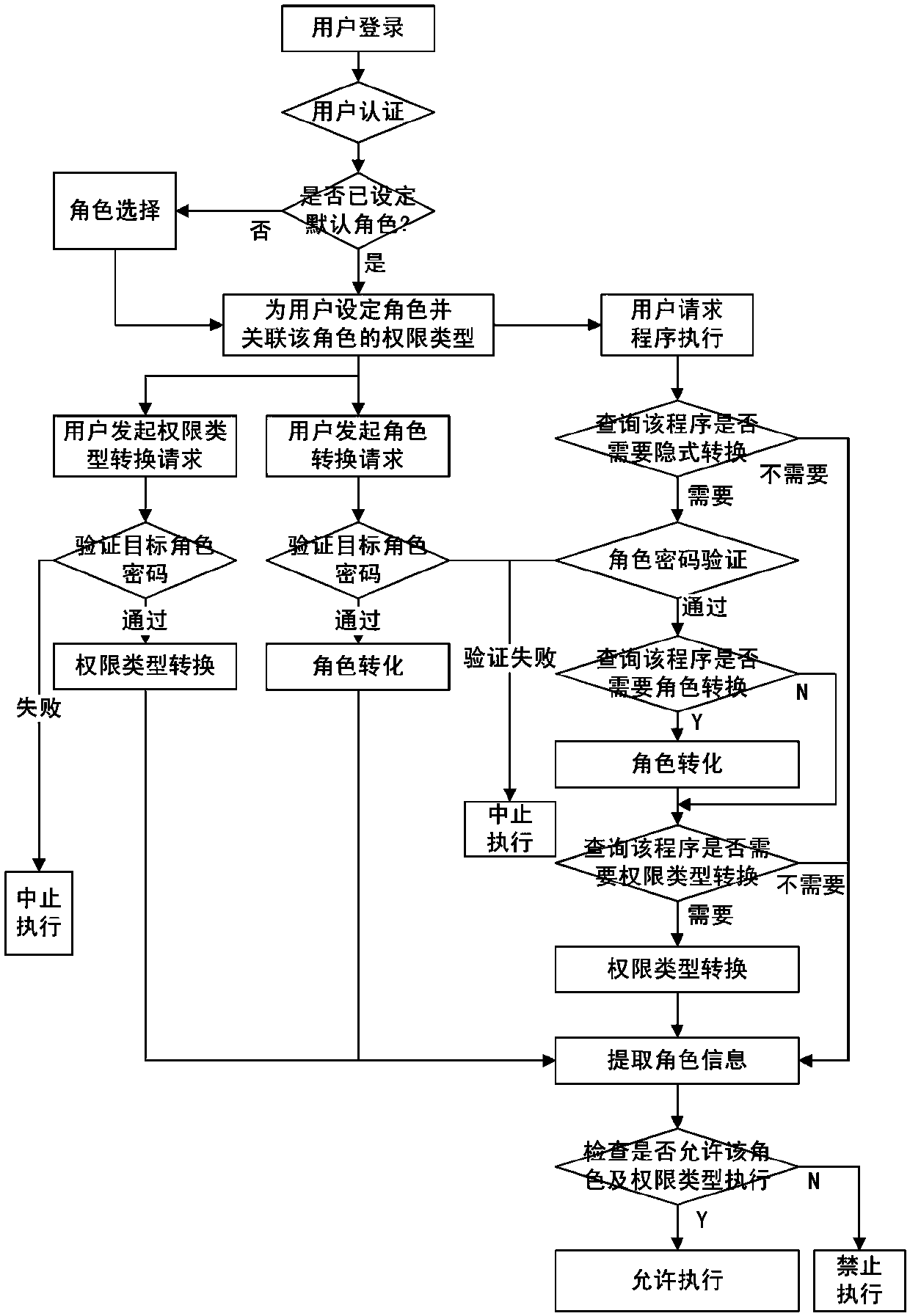
[0045] Such as figure 1 As shown, the implementation steps of the method for supporting the least privileged user on-demand authorization in this embodiment are as follows:
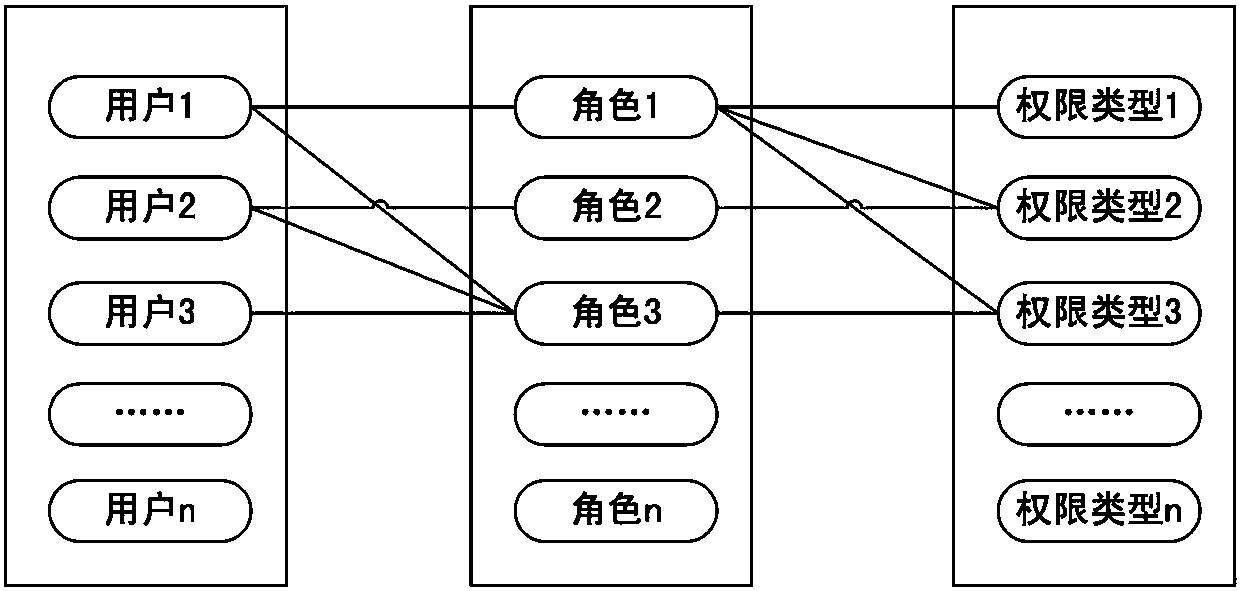
[0046] 1) Establish multiple roles in the operating system, and set authentication passwords for each role; define the different permissions required by different applications in the operating system to run as different permission types, and control that one user can associate multiple roles and Each user can only be associated with one role at the same time, a role can be associated with multiple permission types, and each role can only be associated with one permission type at the same time;
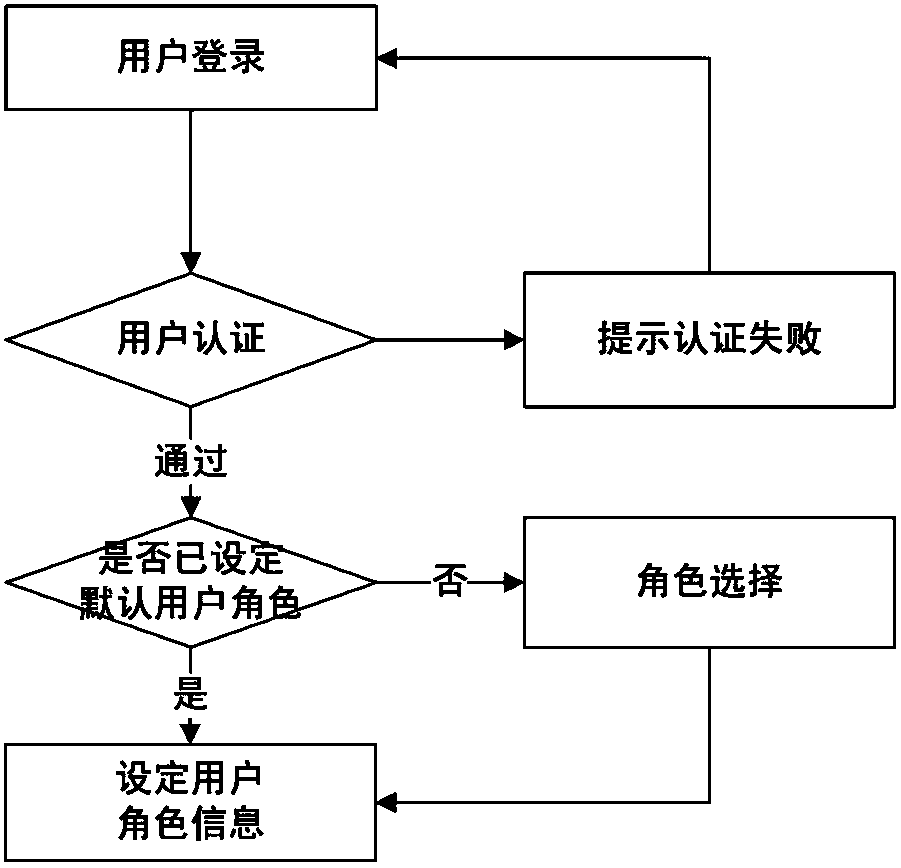
[0047] 2) When a user logs in to the operating system, set a role for the user and associate the permission type of the role, and provide the user with an explicit conversion function that specifies the required role and permission type conversion during the operation of the operating system. When the user initiates a c...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com