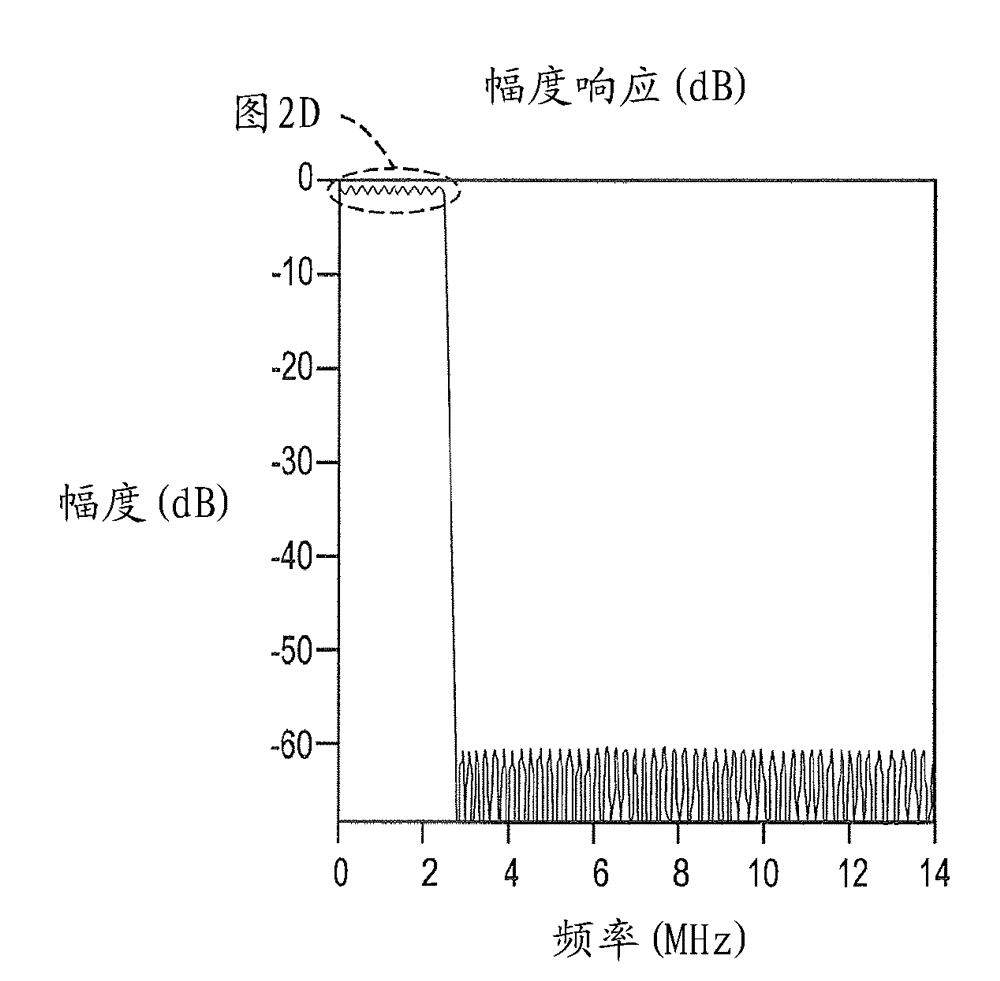
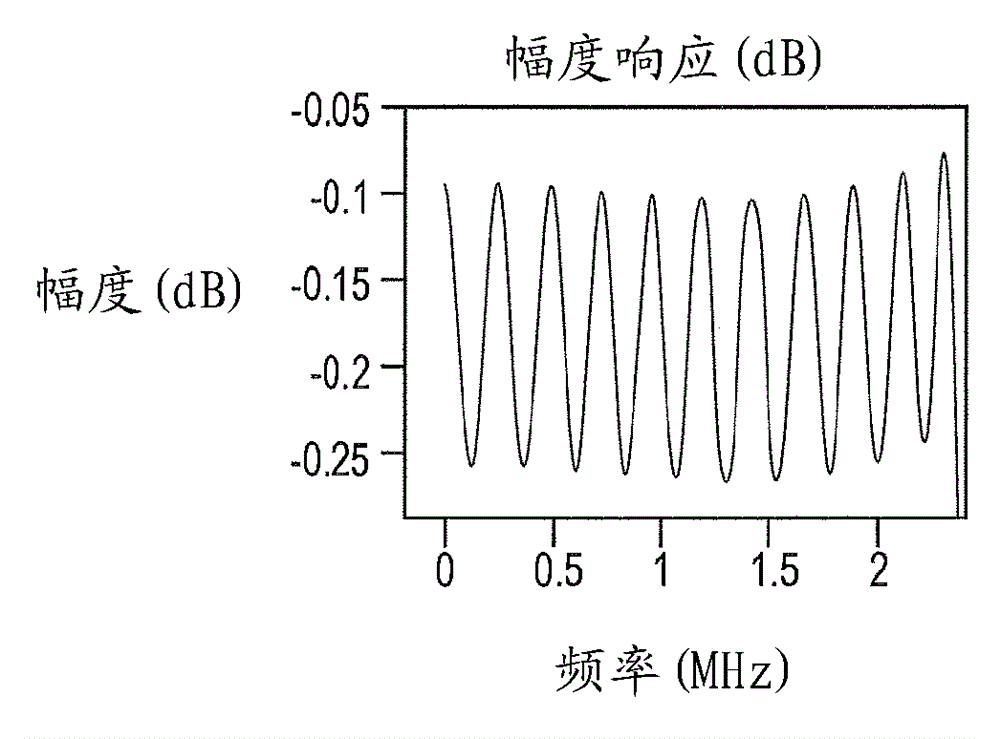
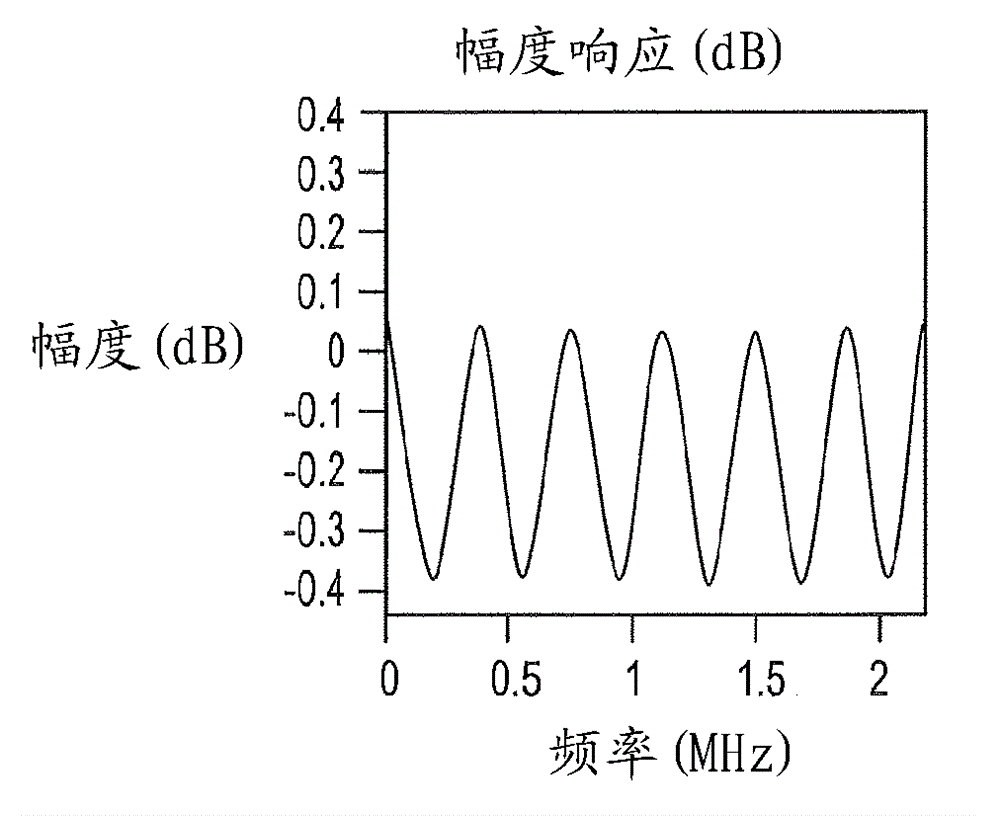
Patents
Literature
39results about How to "Support diversity" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
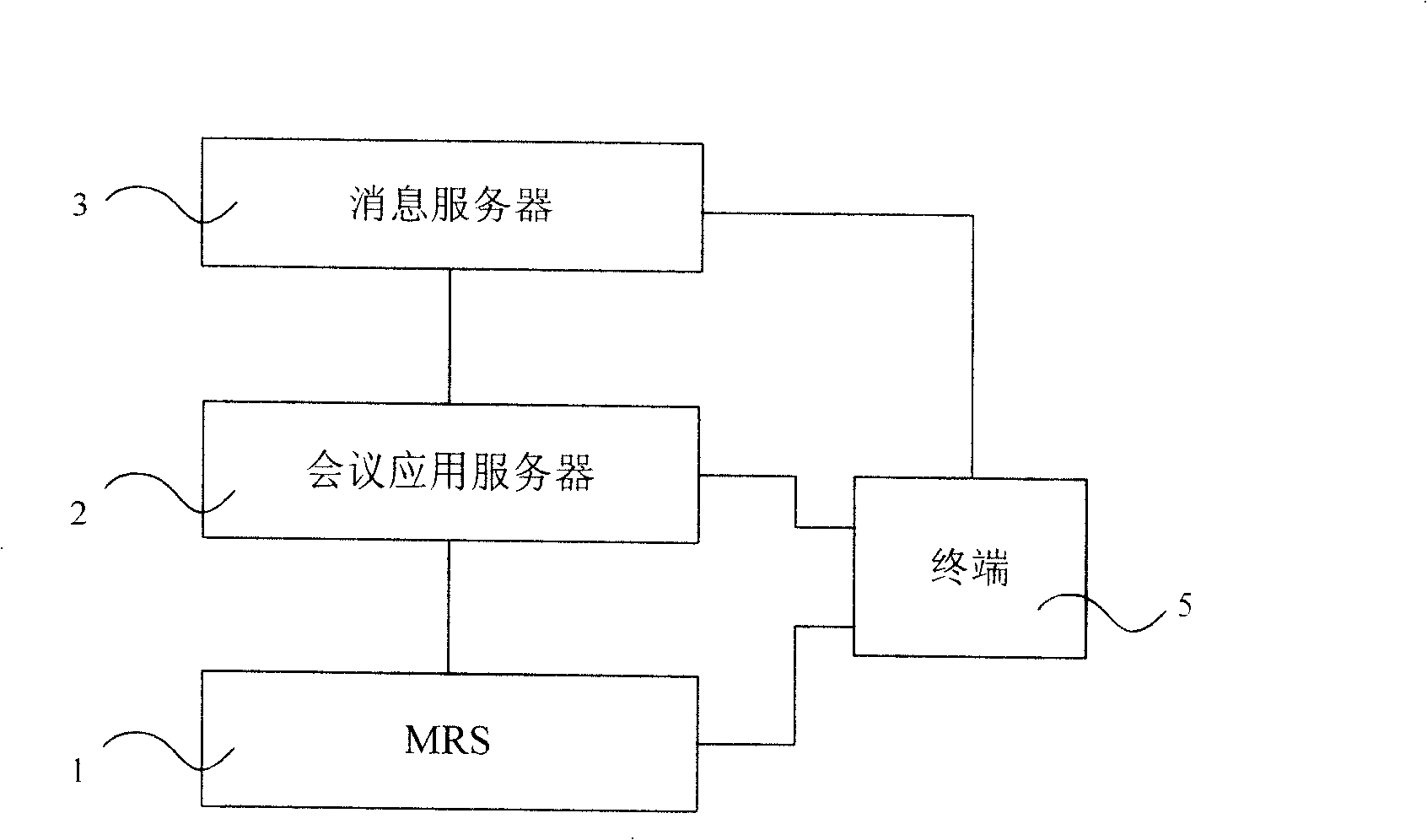
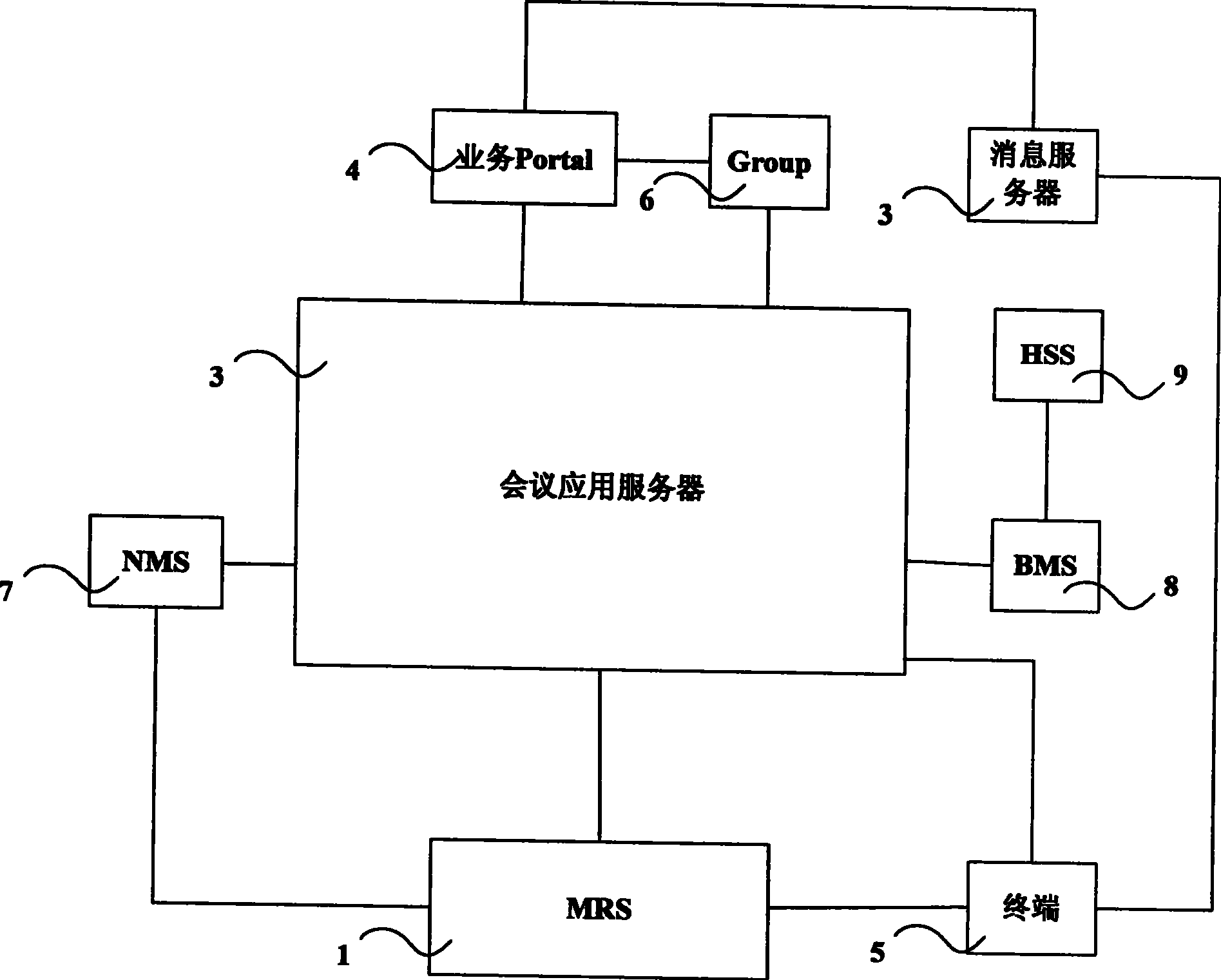
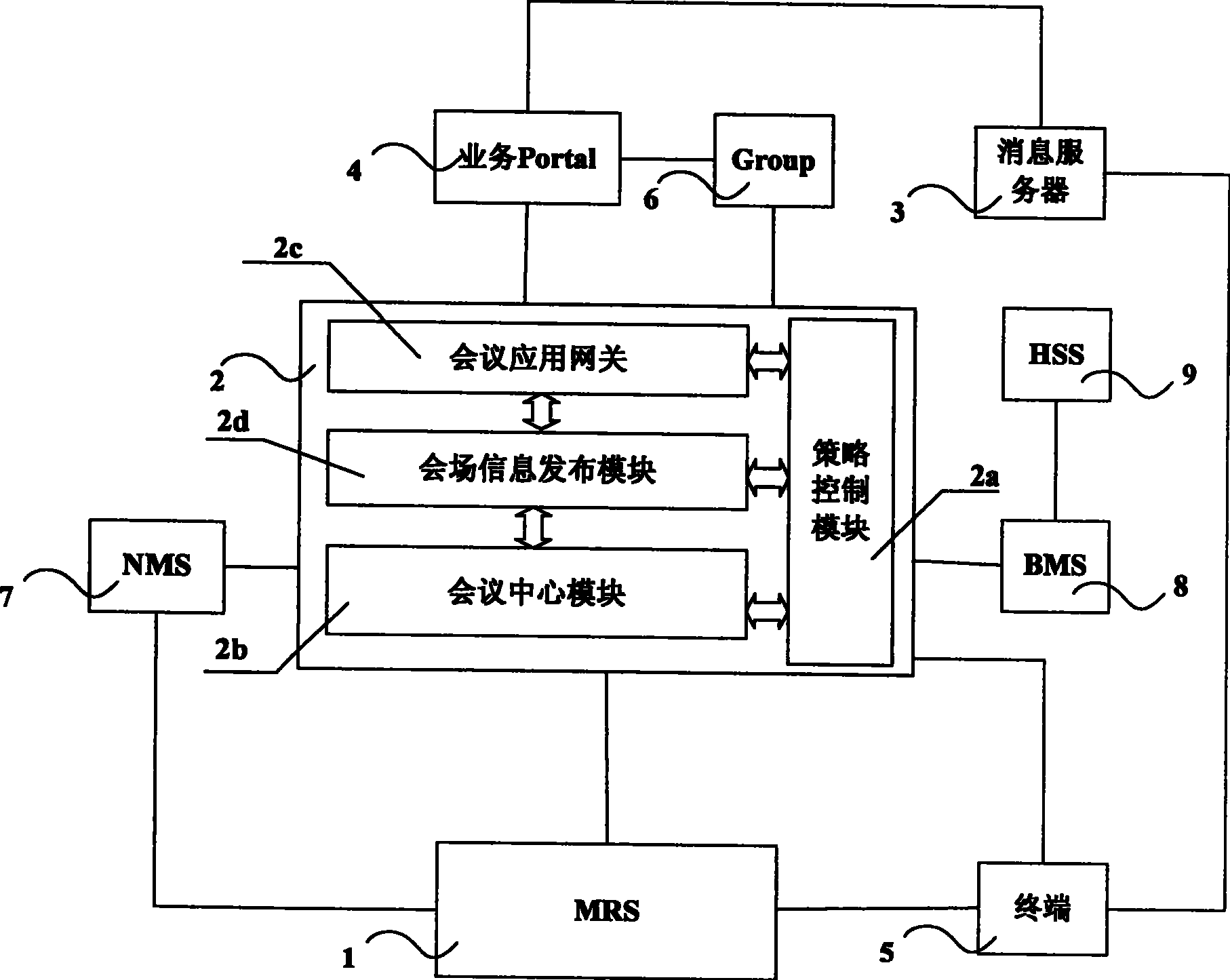
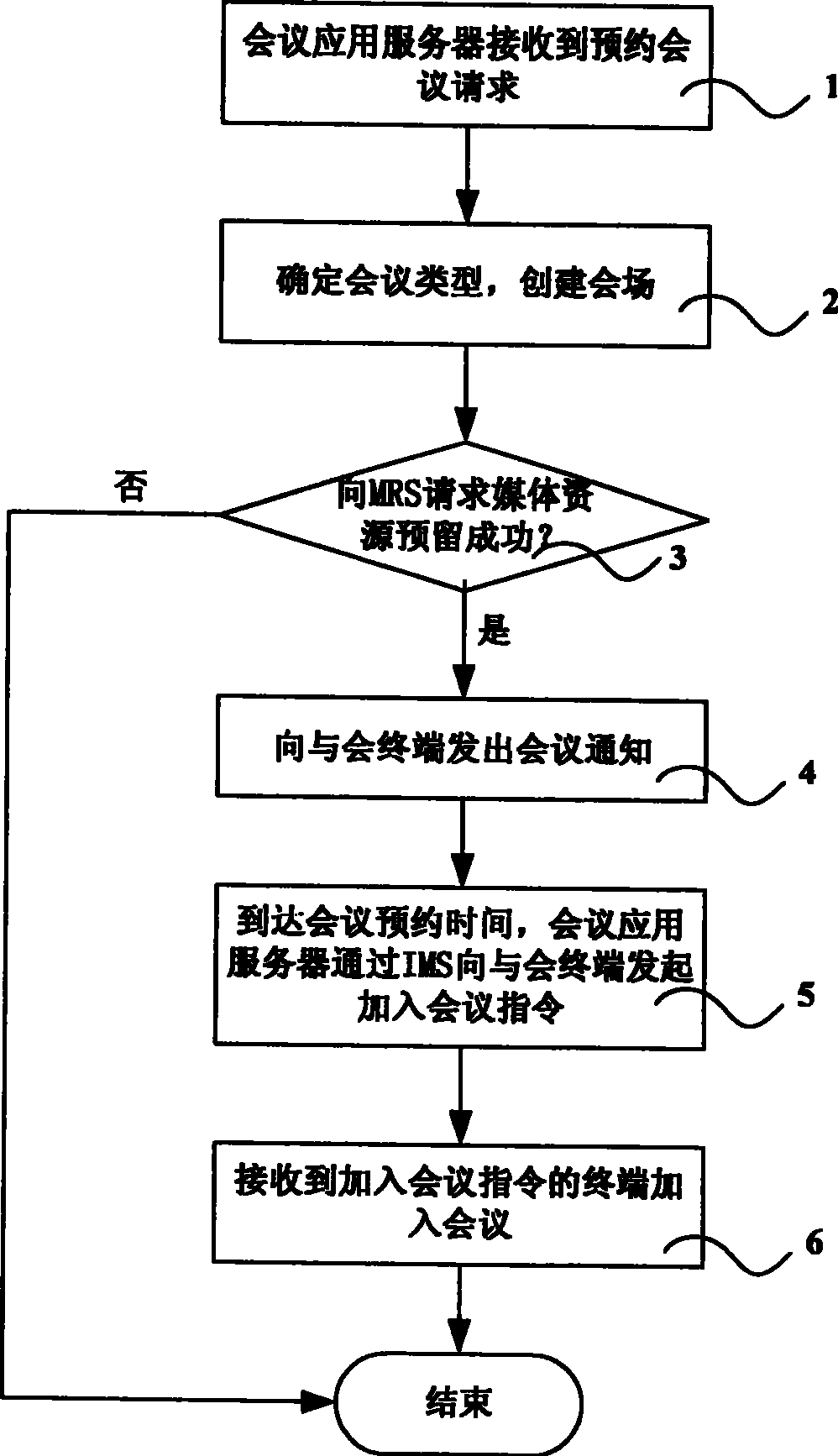
System and method for supporting multimedia conference booking
ActiveCN101257395ASupport diversityOvercoming the defect of single access formSpecial service provision for substationSpecial service for subscribersAppointment timeApplication server
The invention discloses a system supporting the multimedia conferencing reservation, comprising: a media resource server, a conference application server. Also disclosed is a method for supporting the multimedia conferencing reservation, comprising: conference application server receiving the conferencing reservation request; conference application server building up meeting plate and requesting to reserving corresponding media resource to the media resource server; transmitting notification to the participating terminal of resource is successfully reserved; arriving at the conferencing reservation time, the conference application server transmitting order for participating into the conference to the conference terminal via IMS; the terminal received the order participating into the conference. The method supports the diversification of participating into conference; realizes that the conference server builds up the multimedia conference actively at the predetermined time and avoids the time waste and bad feeling when the conference inviter invites and builds up the conference bridge one by one.
Owner:CHINA MOBILE COMM GRP CO LTD
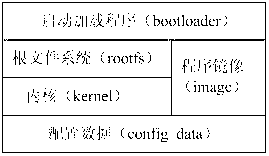
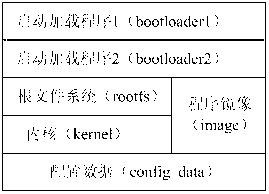
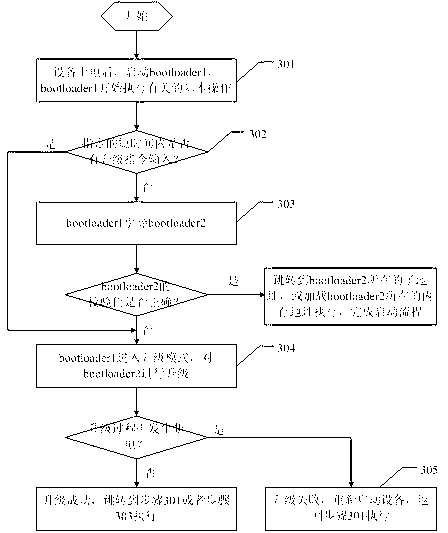
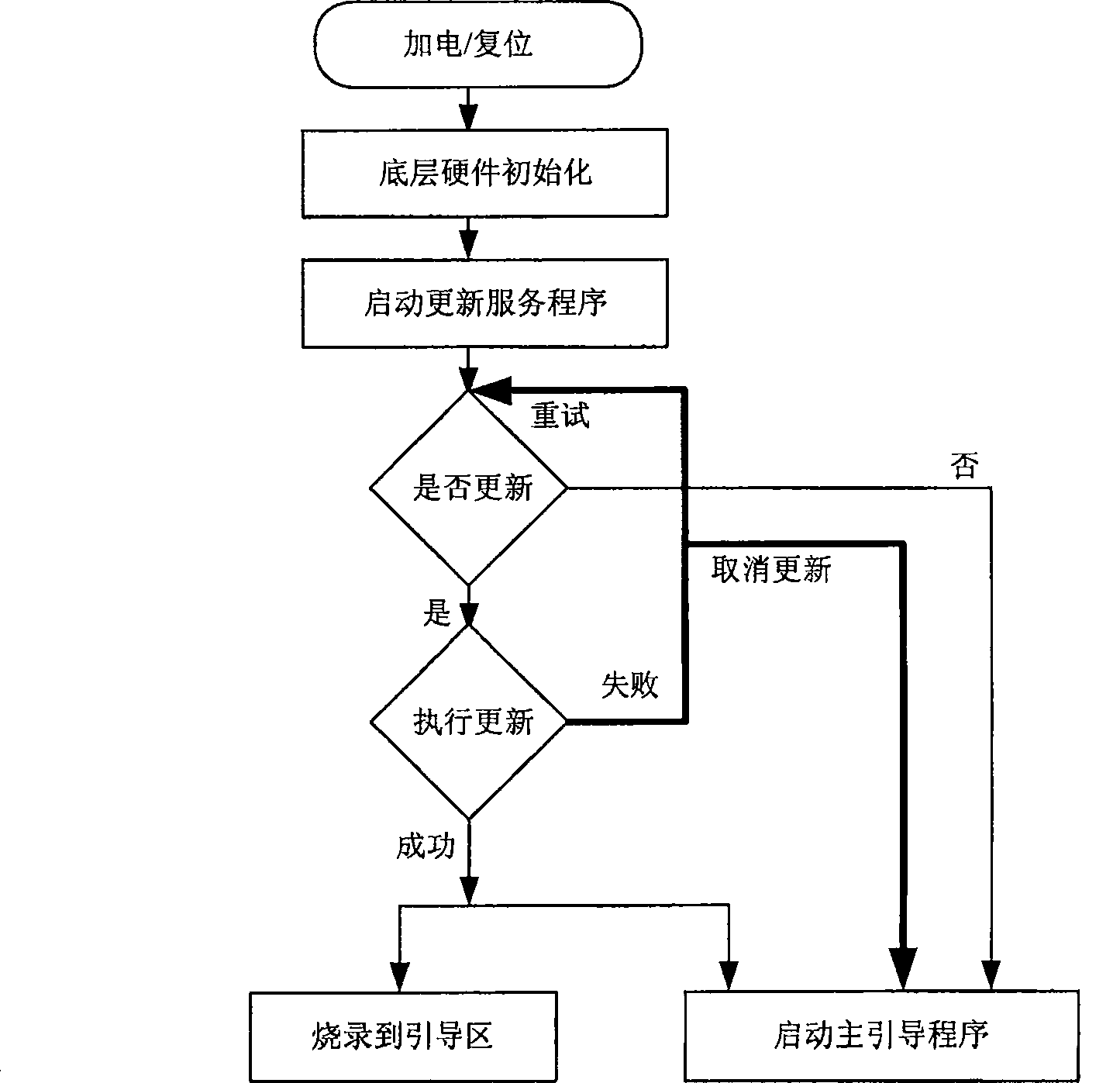
Multistage boot load method of embedded equipment
ActiveCN102902556ASupport diversitySo as not to damageProgram loading/initiatingEmbedded systemStorage area
The invention provides a multistage boot load method of embedded equipment. Flash of the embedded equipment is sequentially divided into a boot loader 2 partition, an image partition and a data configuration partition. The multistage boot load method comprises the following steps of: adding a boot loader 1 partition in a storage area, wherein the boot loader 1 partition has the functions of upgrading, guiding and configuring the boot loader 2; after the equipment is electrified, starting the boot loader 1 firstly; checking whether a command for upgrading / configuring the boot loader 2 is input or not within an appointed time in a circulating way; if the command is not input, guiding the boot loader 2 to start by the boot loader 1, and finishing a start flow; and if the command is input, upgrading / configuring the boot loader 2 by the boot loader 1, and skipping to the boot loader 2 after the upgrading / configuring to execute equipment reboot or directly reboot the equipment. According to the multistage boot load method provided by the embodiment of the invention, the diversity of an image and the boot loader are supported, and the safety requirements during the embedded upgrading are also satisfied.
Owner:SHENZHEN GONGJIN ELECTRONICS CO LTD
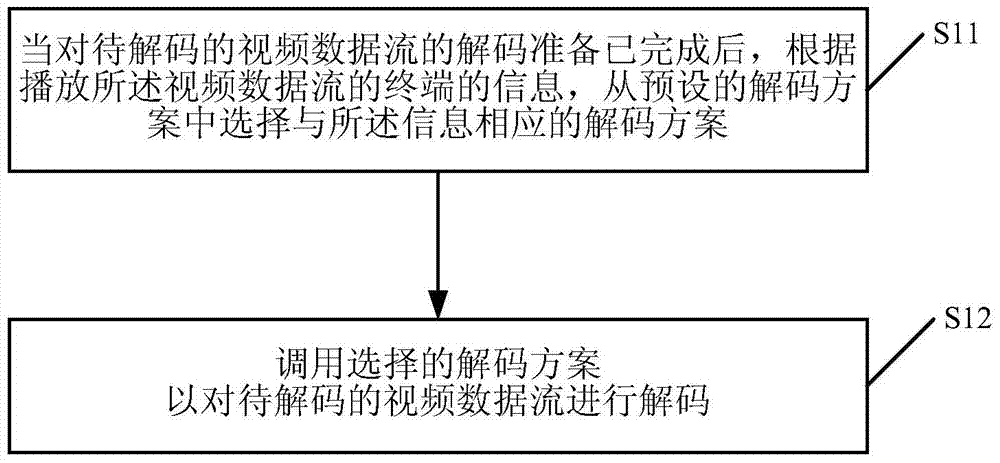
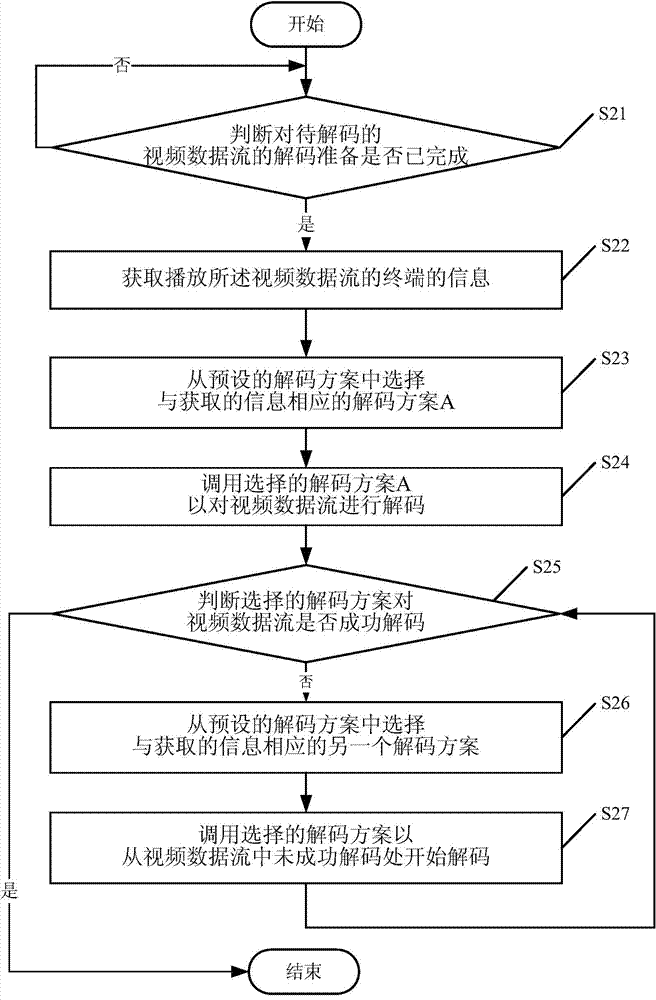
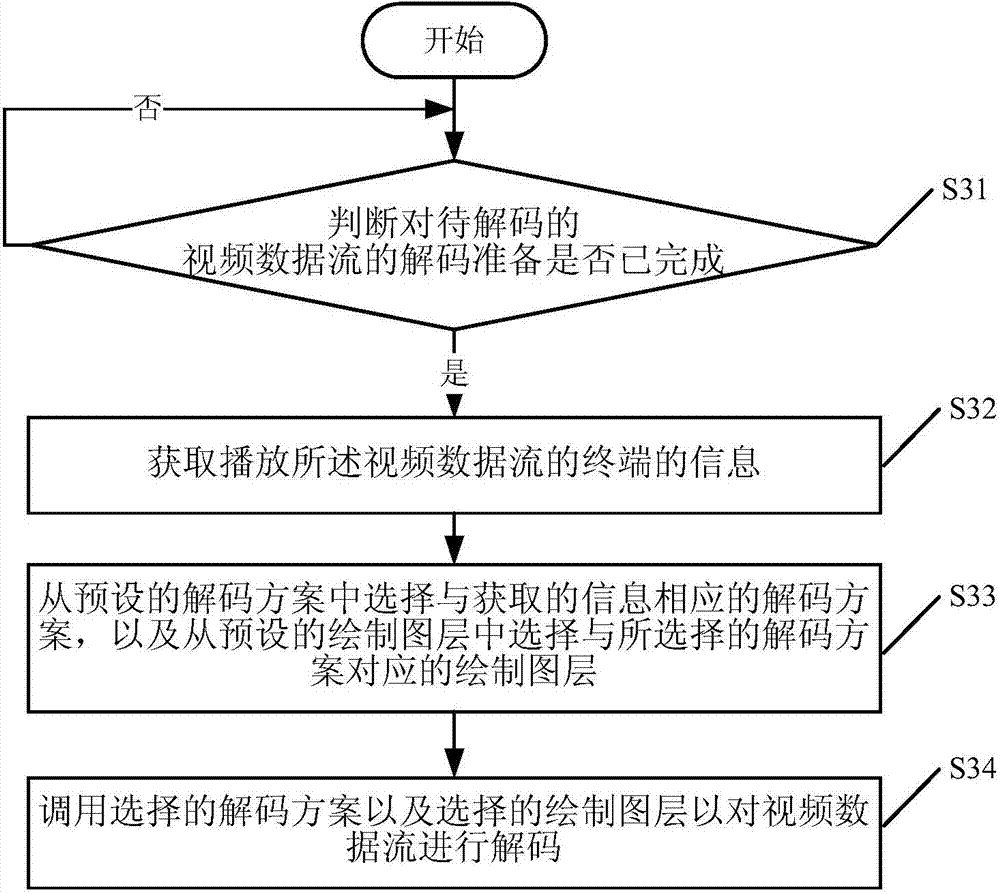
Method, device and player for decoding video
ActiveCN104780378AImprove user experienceRealize dynamic switchingDigital video signal modificationSelective content distributionData streamComputer engineering
The invention discloses a method, device and player for decoding video. The method comprises the following steps: after preparing the decoding of data streams of the video to be decoded, according to the information of a terminal playing the data streams of the video, selecting a decoding scheme corresponding to the information from a preset decoding scheme; transferring the selected decoding scheme to decode the data streams of the video to be decoded. Through the adoption of the method disclosed by the invention, different decoding schemes can be encapsulated in the player, and the structures of different decoding types can be taken account of; when the decoding scheme needs to be replaced, buffer again and decoding preparation are not needed, and the decoding schemes can be directly switched, so that the dynamic switching is realized, users hardly sense the dynamic switching, and the use experience of the user is improved.
Owner:TENCENT TECH (BEIJING) CO LTD
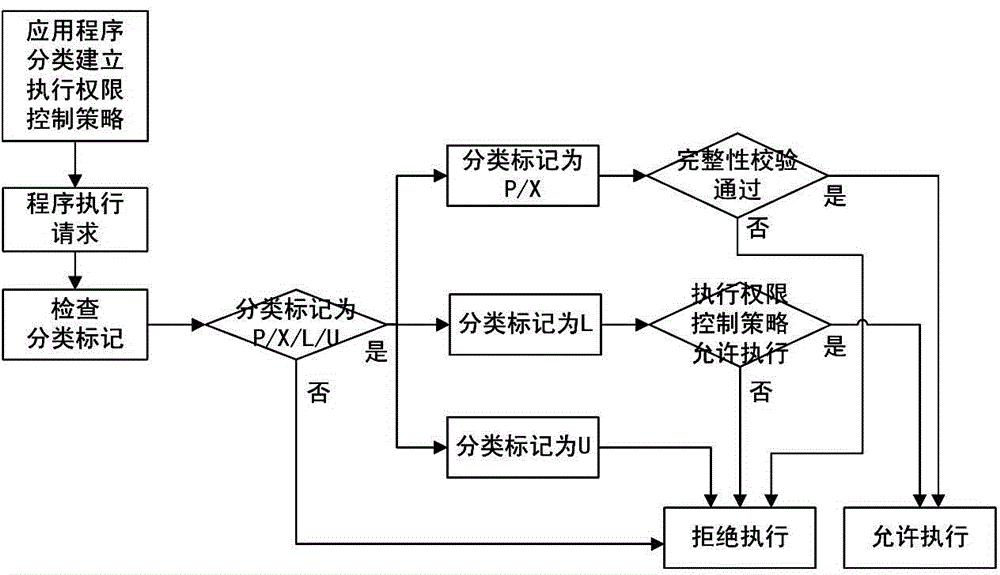
Application program executing permission control method used for operating system
InactiveCN104462950AStrong preventive abilityAchieve stabilityComputer security arrangementsTamper resistanceOperational system
The the invention discloses an application program executing permission control method used for an operating system. The method includes the following steps: classifying application programs in the operating system; establishing an executing permission control strategy of the application programs; when the application programs execute requests, checking classifying marks of the application programs, verifying completeness of the application programs if the classifying marks allow all users to execute or are protected and are tampering-proof, executing if verification passes, and refusing to execute if verification fails; if the classifying marks allow or refuse part of users to execute, inquiring the executing permission control strategy on the basis of inherent information of the application programs, executing if the executing permission control strategy returned by inquiring allows the application programs to be executed, and refusing to execute if not; if the classifying marks are empty or refuse all users to execute, refusing toe execute the application programs. The application program executing permission control method has the advantages of high malicious software preventing capability, safety, reliability, high stability, high universality and high expandability.
Owner:NAT UNIV OF DEFENSE TECH
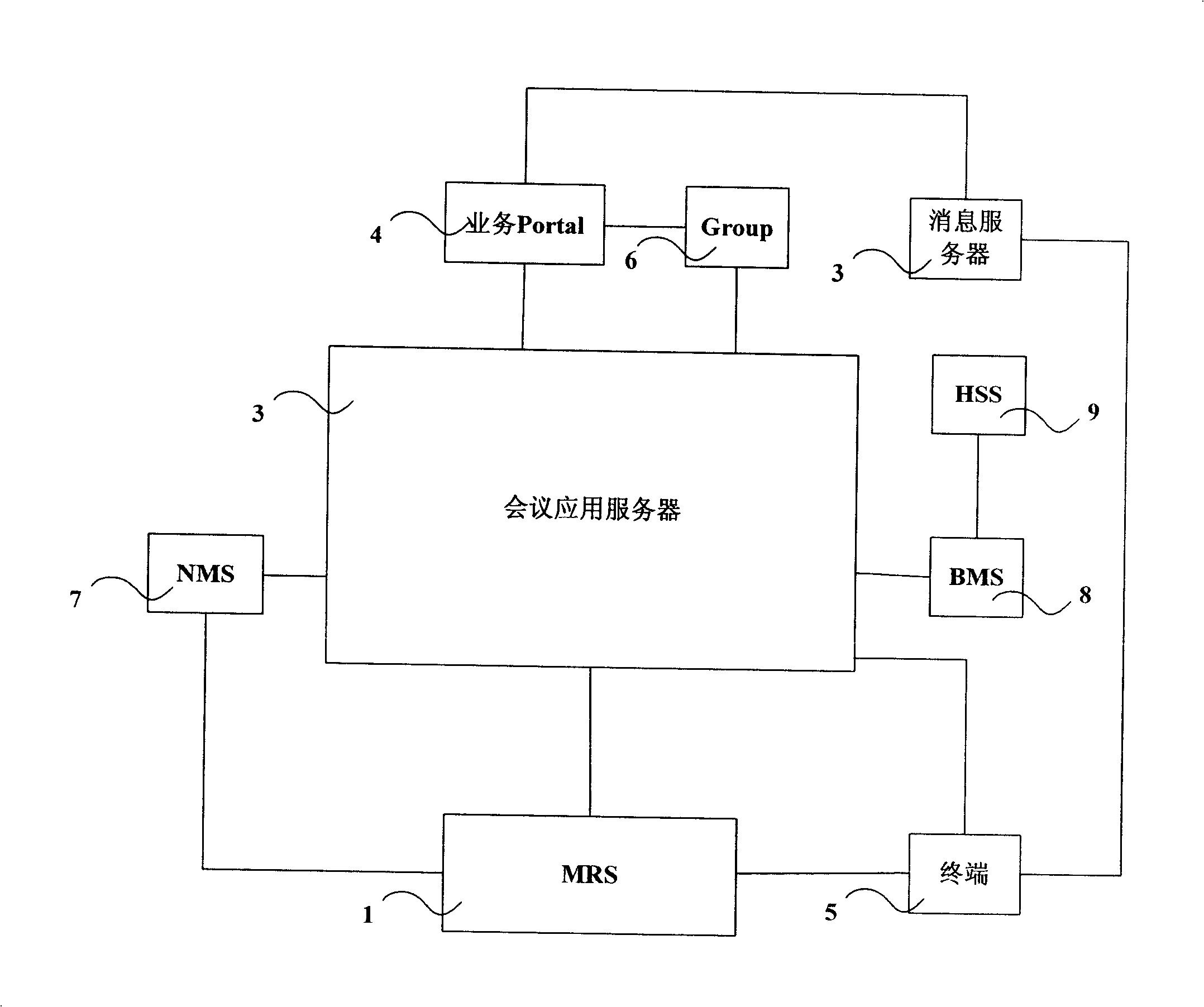
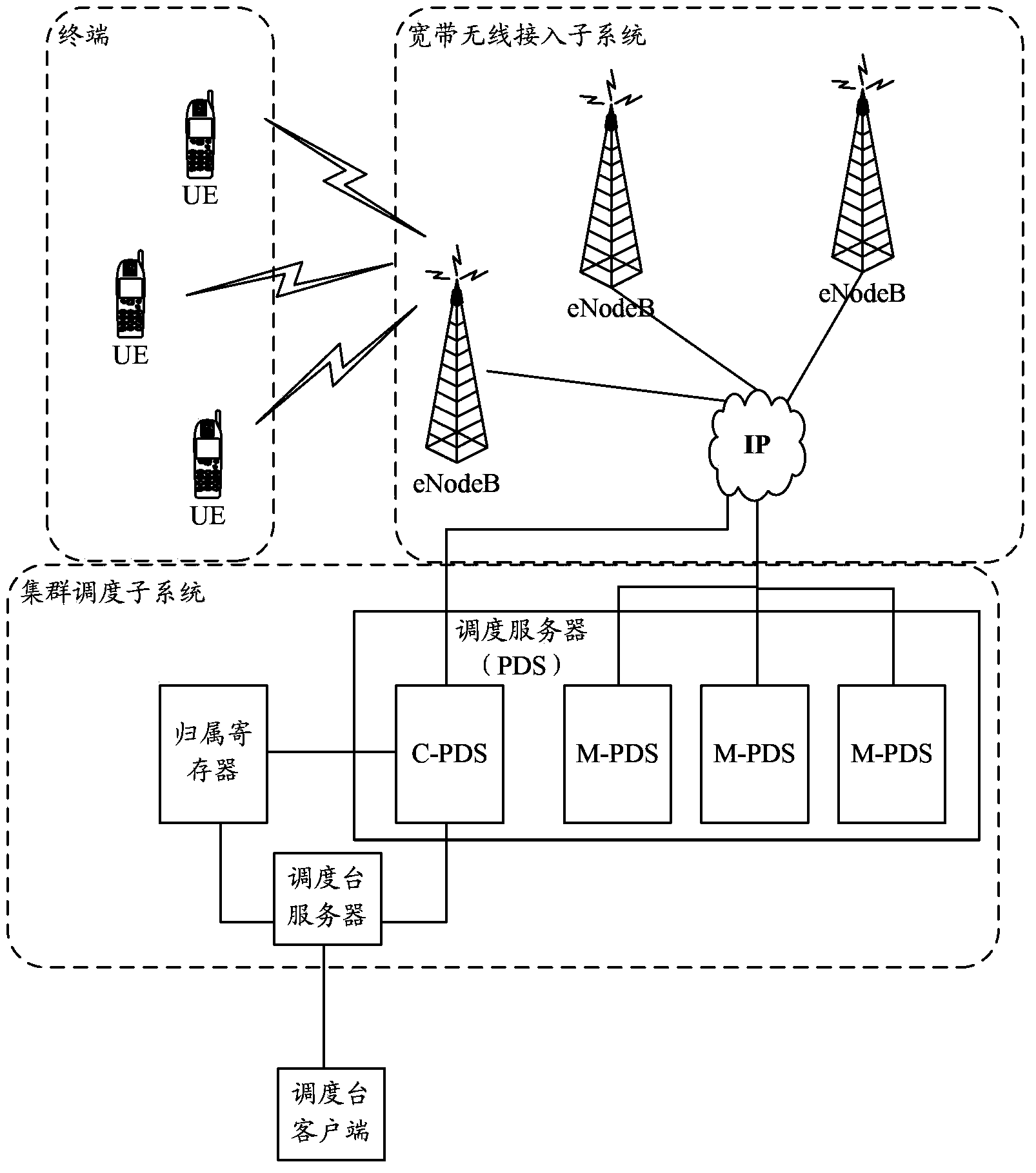
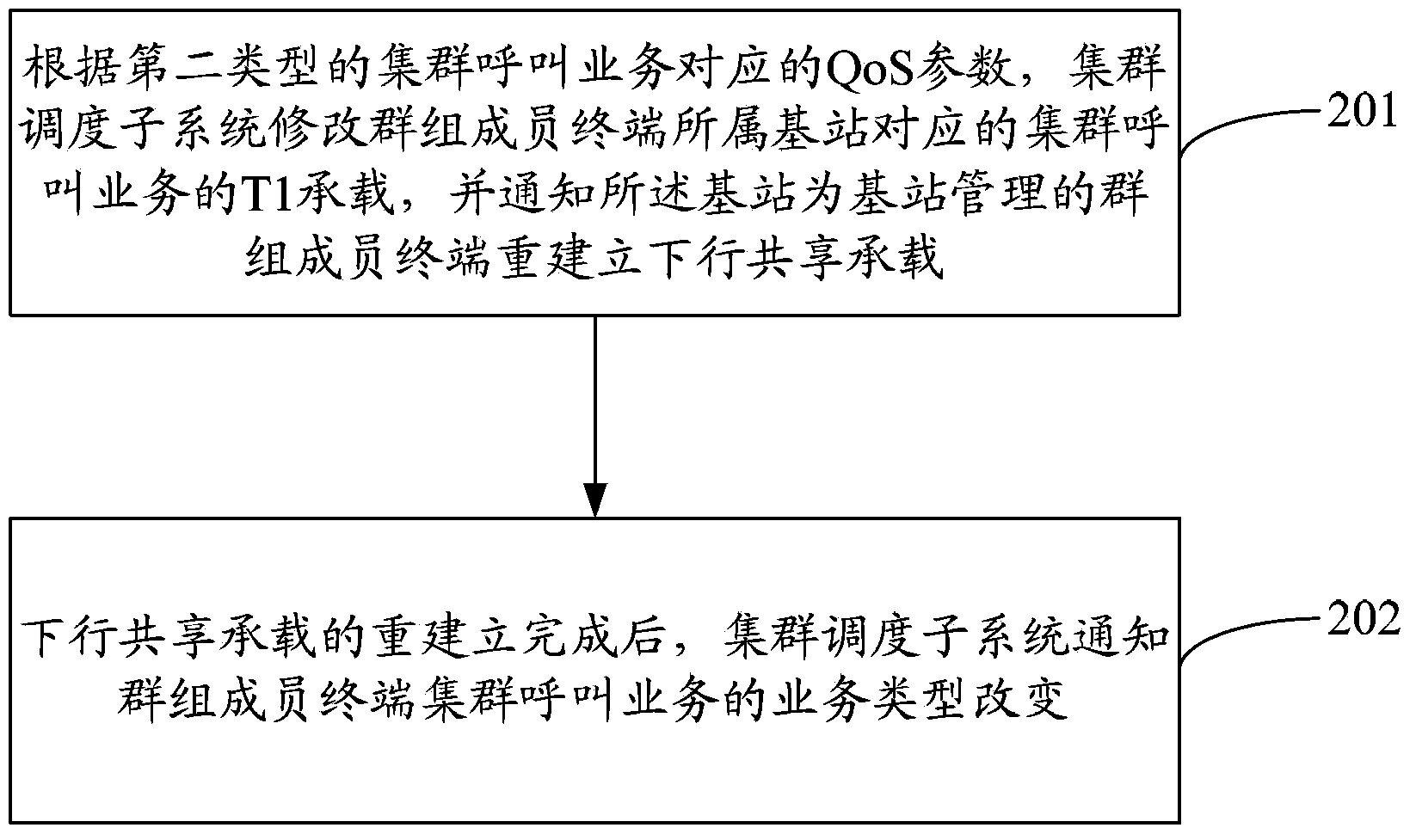
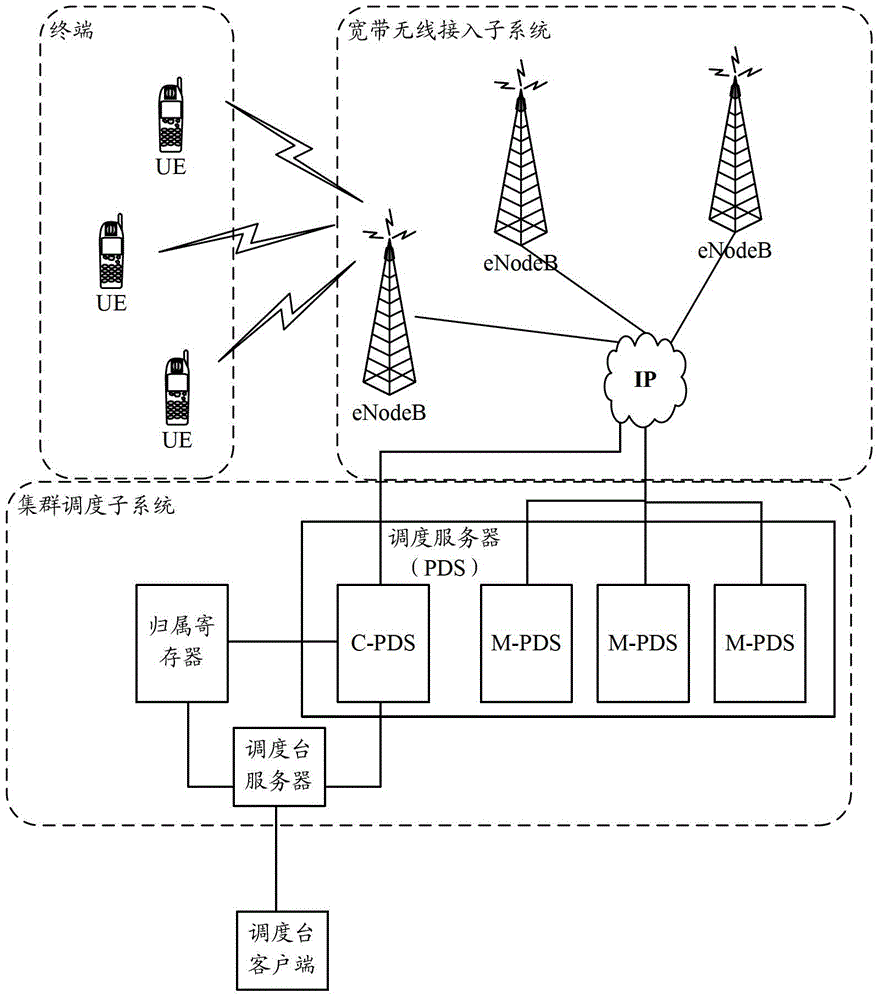
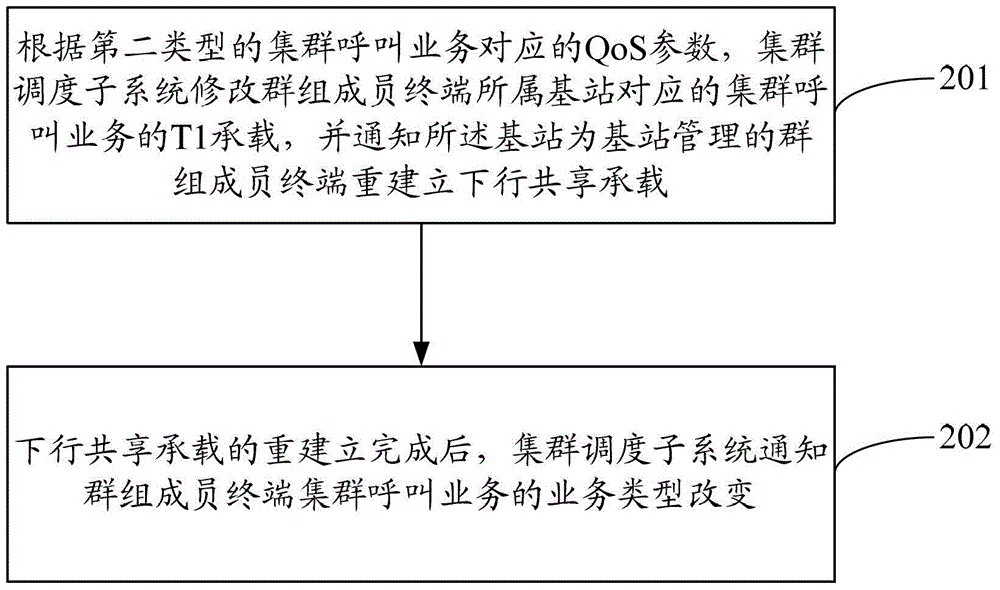
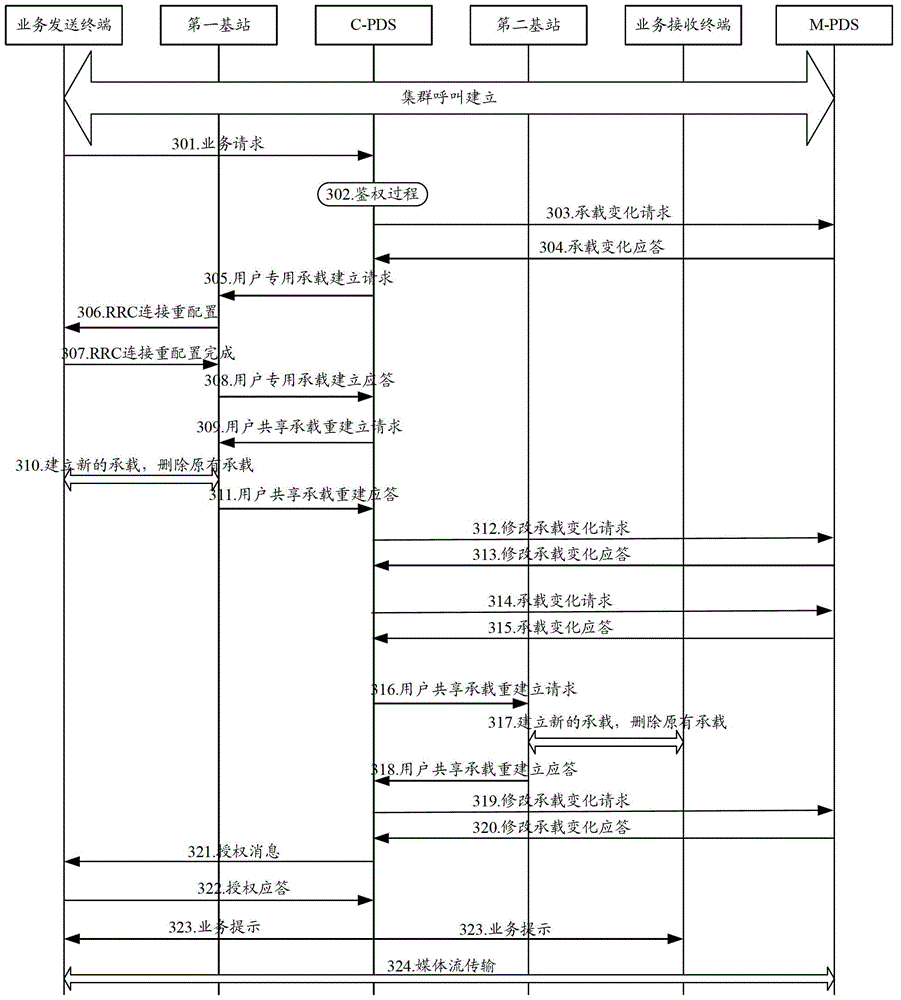
Broadband trunking service realizing method and broadband trunking service realizing system
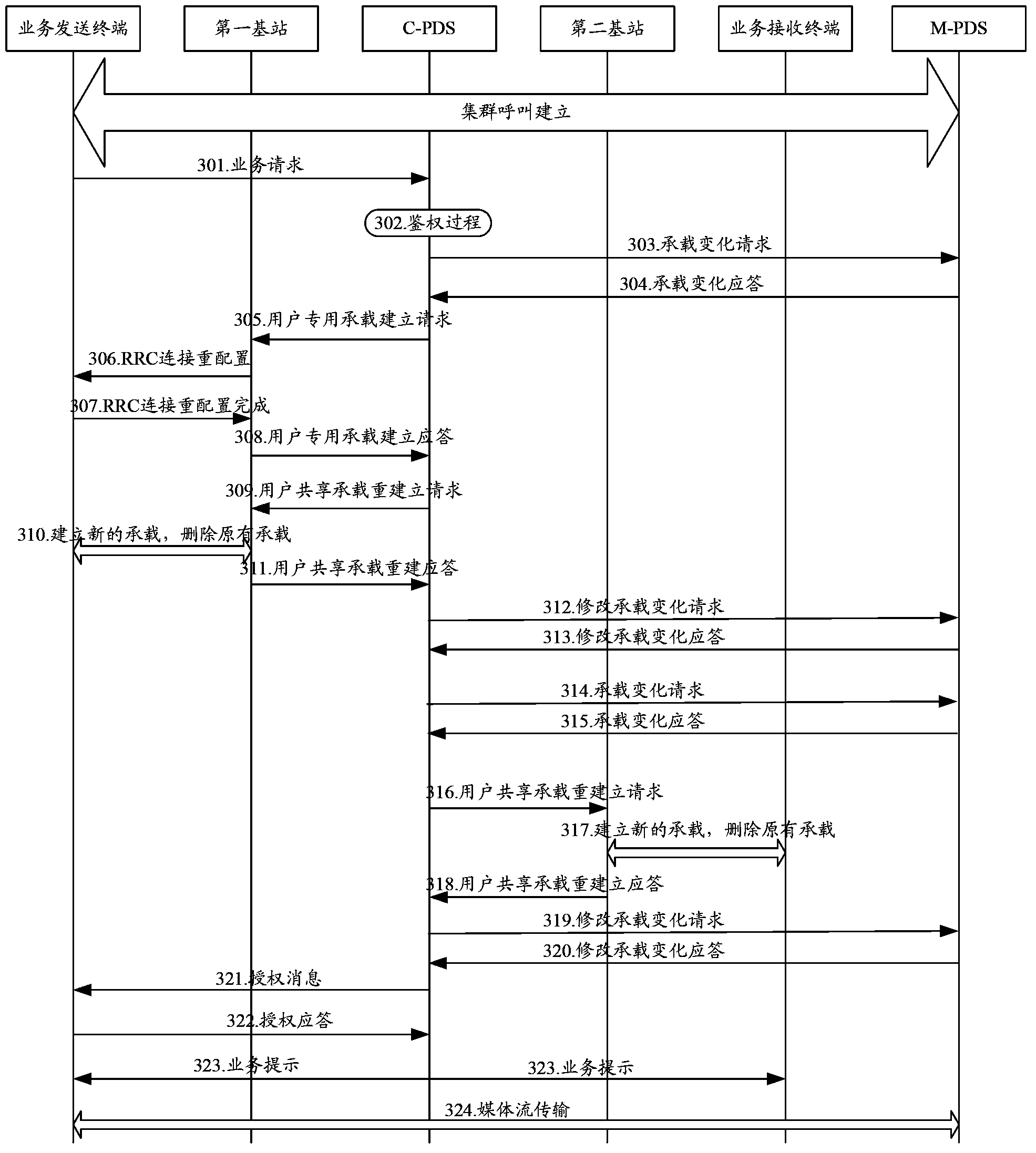
ActiveCN103581839ASupport diversityReduce loadNetwork traffic/resource managementBroadcast service distributionTrunkingBroadband
The invention discloses a broadband trunking service realizing method and a broadband trunking service realizing system. The method comprises the following steps: when the service type of an established trunked call service is transformed from a first type to a second type, a trunked scheduling subsystem modifies a T1 bearer of a trunked call service corresponding to a base station to which group member terminals belongs according to QoS parameters corresponding to the trunked call service of the second type, and notifies the base station to reestablish a downlink shared bearer for the group member terminals managed by the base station; and the trunked scheduling subsystem notifies the group member terminals that the service type of the trunked call service is changed after reestablishment of the downlink shared bearer is finished. With the broadband trunking service realizing method and the broadband trunking service realizing system, diversification and real-time transmission of broadband services can be realized.
Owner:SHENZHEN ZTE TRUNKING TECH CORP
Loose coupling role authorized-type implementation access control method and system thereof
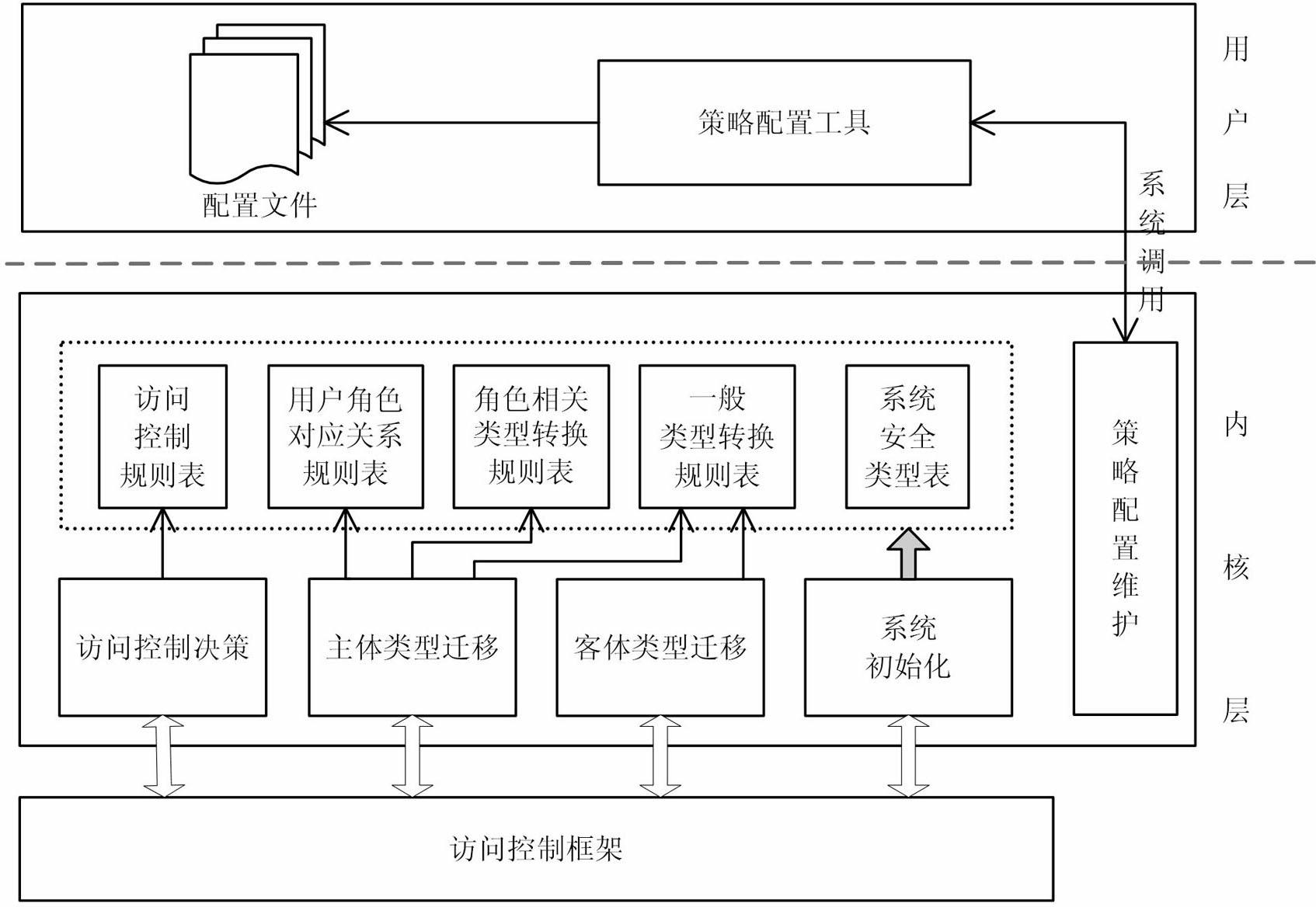
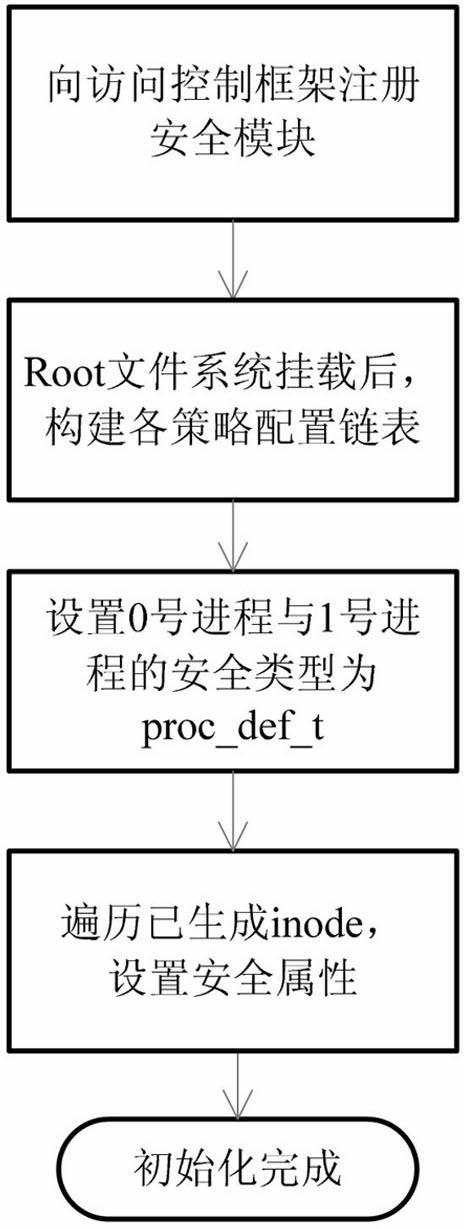
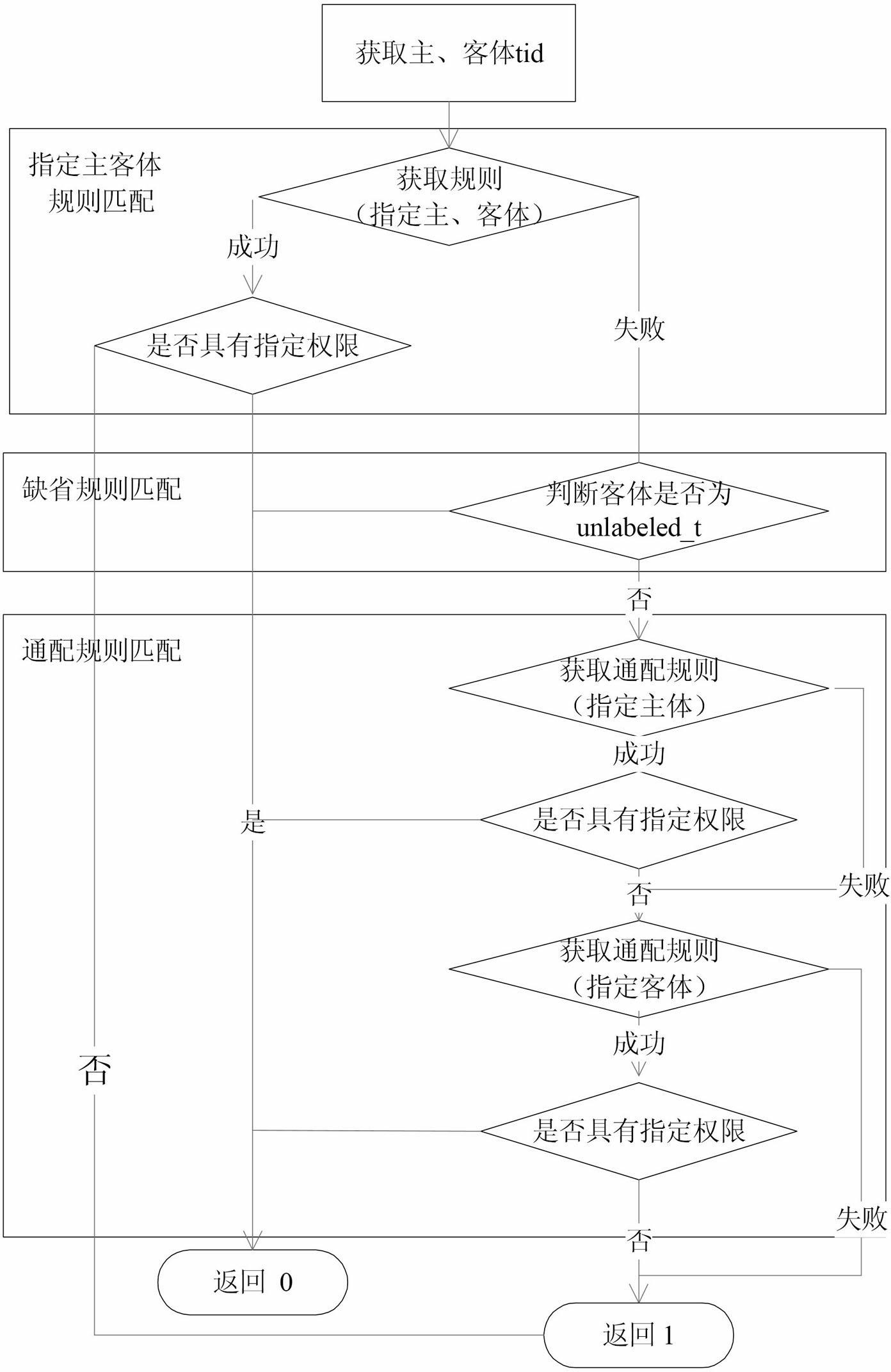
InactiveCN102222191AChange execution flowImplement featuresUnauthorized memory use protectionDigital data protectionOperational systemSecurity domain
The invention discloses a loose coupling role authorized-type implementation access control method and a system thereof. The method comprises the following steps of: adding a user role incidence relation based on a type implementation access control method; adding a related process type transformation rule definition relating to a user role and a corresponding type transformation decision mechanism; when a system process type is transformed, according to the process type transformation rule, judging whether to perform role related type transformation according to a current role of the user to change a user process execution flow; and entering a specific security domain of the user role. The system comprises a type implementation access control policy module, a policy security configuration module and a policy rule configuration module, wherein the type implementation access control policy module is operated in the kernel of an operating system; the policy security configuration module is operated on the user layer of the operating system; and the policy rule configuration module is positioned in a file system. The method and the system have the advantages of reducing the influence of user role configuration change on a type implementation rule system, reducing the security configuration difficulties, facilitating flexible configuration according to actual service conditions.
Owner:NAT UNIV OF DEFENSE TECH
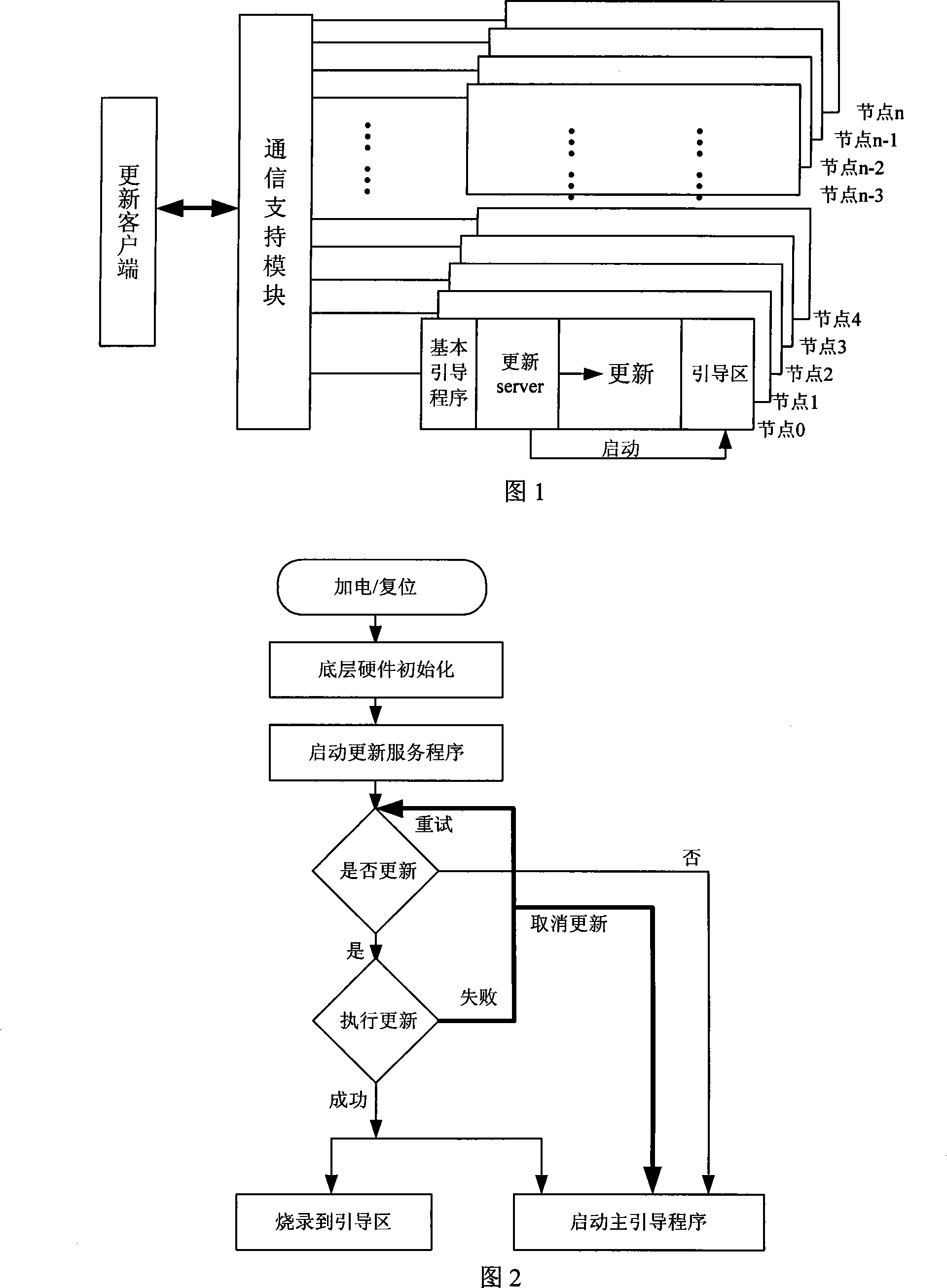
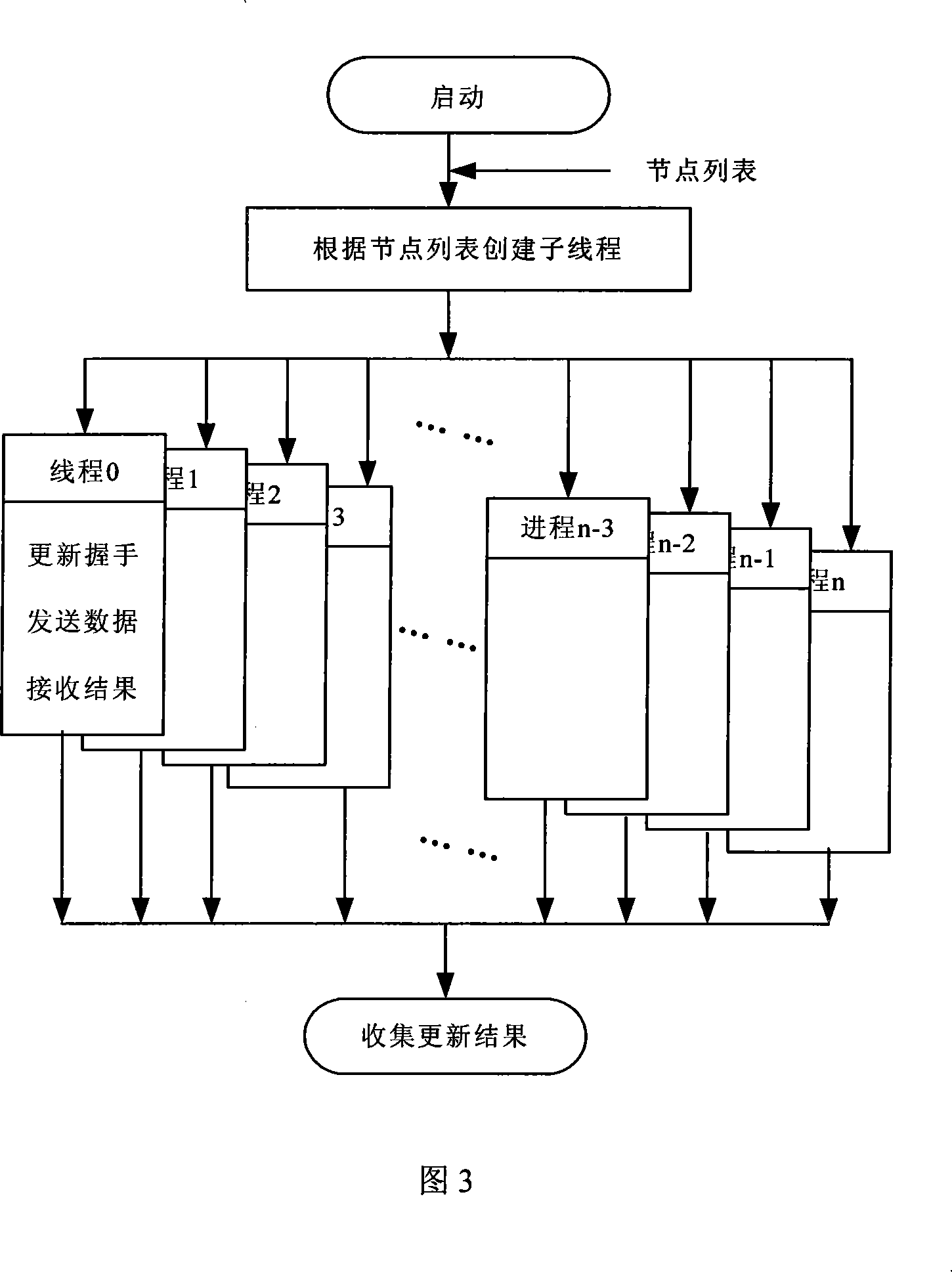
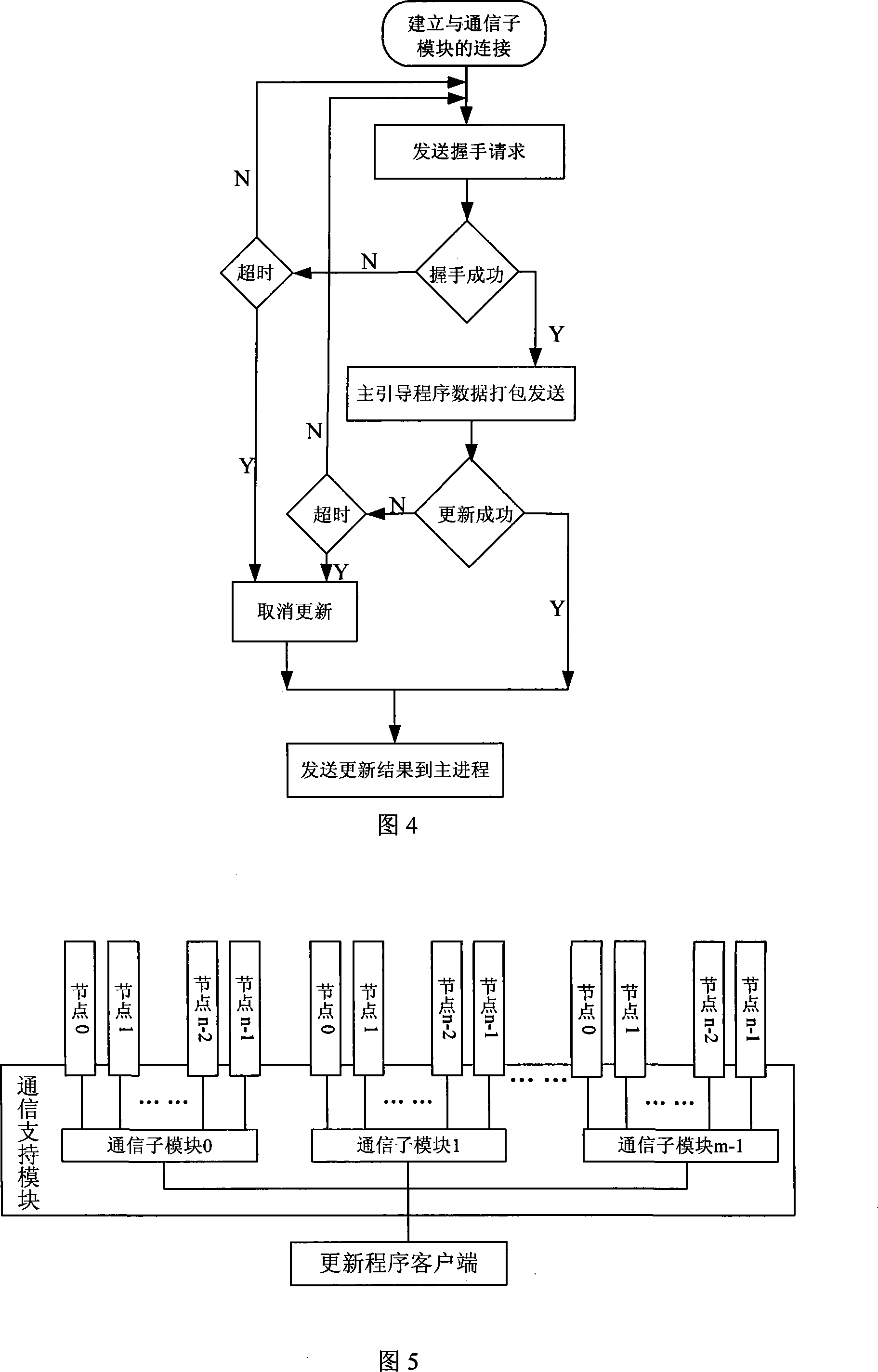
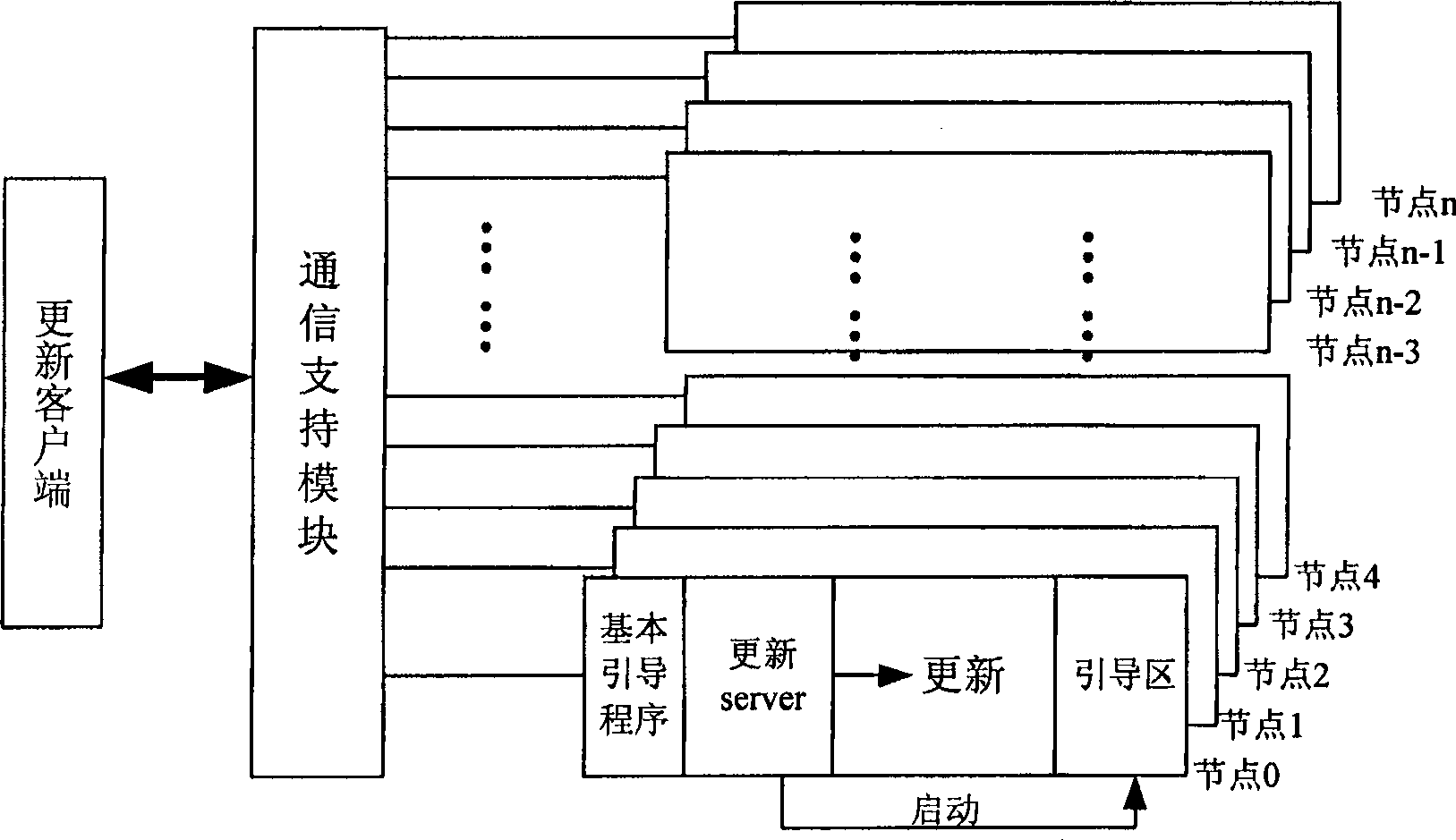
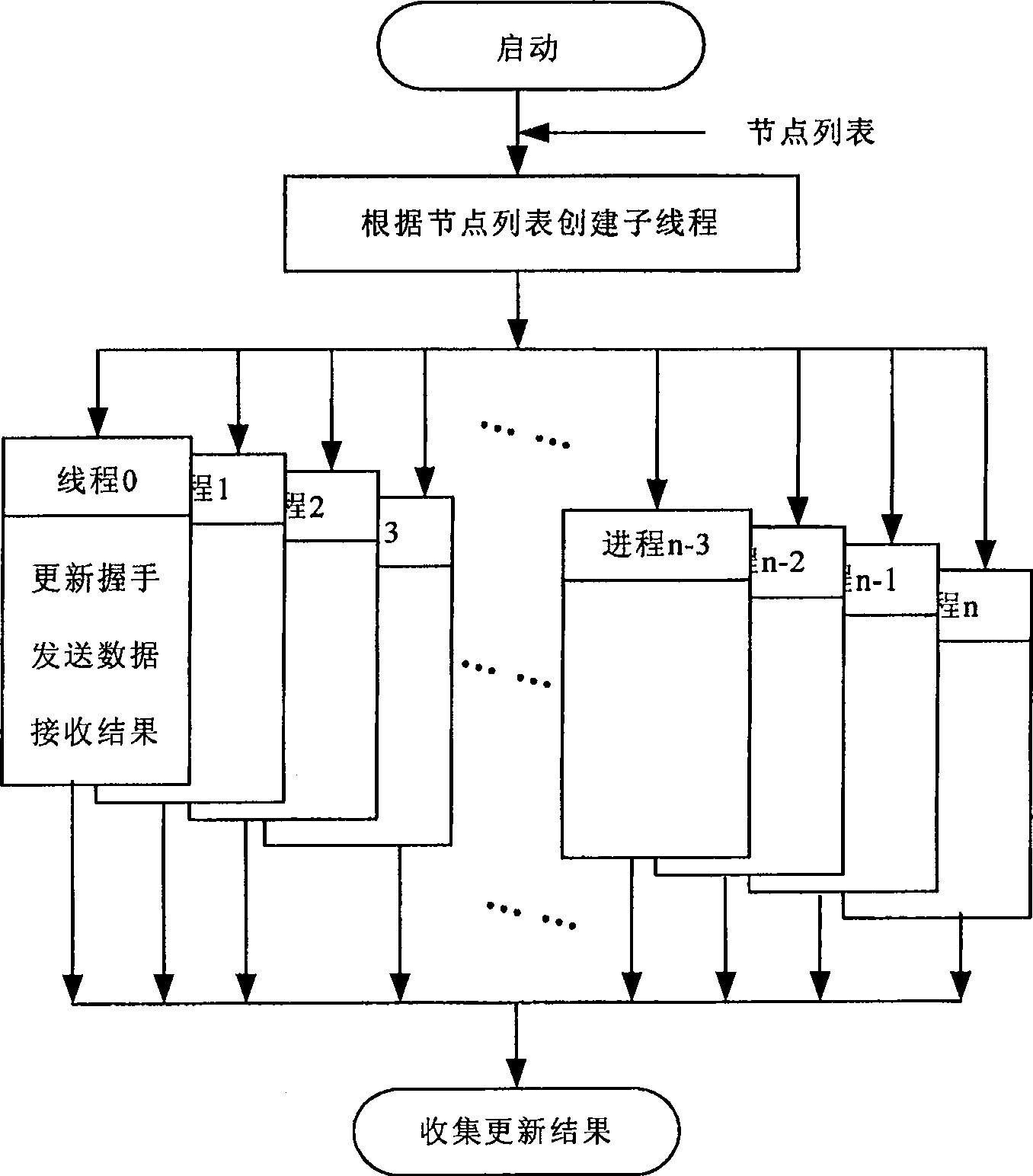
Large scale computer node bootstrap paralleling update method and system
InactiveCN101178659AShorten update timeImprove update efficiencyMultiprogramming arrangementsData switching by path configurationProblem of timeComputer module
The invention discloses a parallel update method and a system for large-scale computer node guiding procedure. The update customer terminal transmits update order and data to every node of the large-scale computer in parallel by a communication support module. The node update service module at every node receives the update order and data of the update customer terminal to update the guiding procedure of every node. The update system comprises a communication support module, an update customer terminal running at the ordinary micro-computer and a node guiding procedure update module arranged at every node of the large-scale computer. All the node update service modules are connected with the update customer terminal by the communication support module to answer for the update order of the customer terminal and finally realize the parallel update of every node guiding procedure. The invention adopts the parallel mode and has the advantages of simple structure, convenient operation and capability of resolving the problem of time and energy consuming of the guiding procedure in the large-scale system.
Owner:NAT UNIV OF DEFENSE TECH
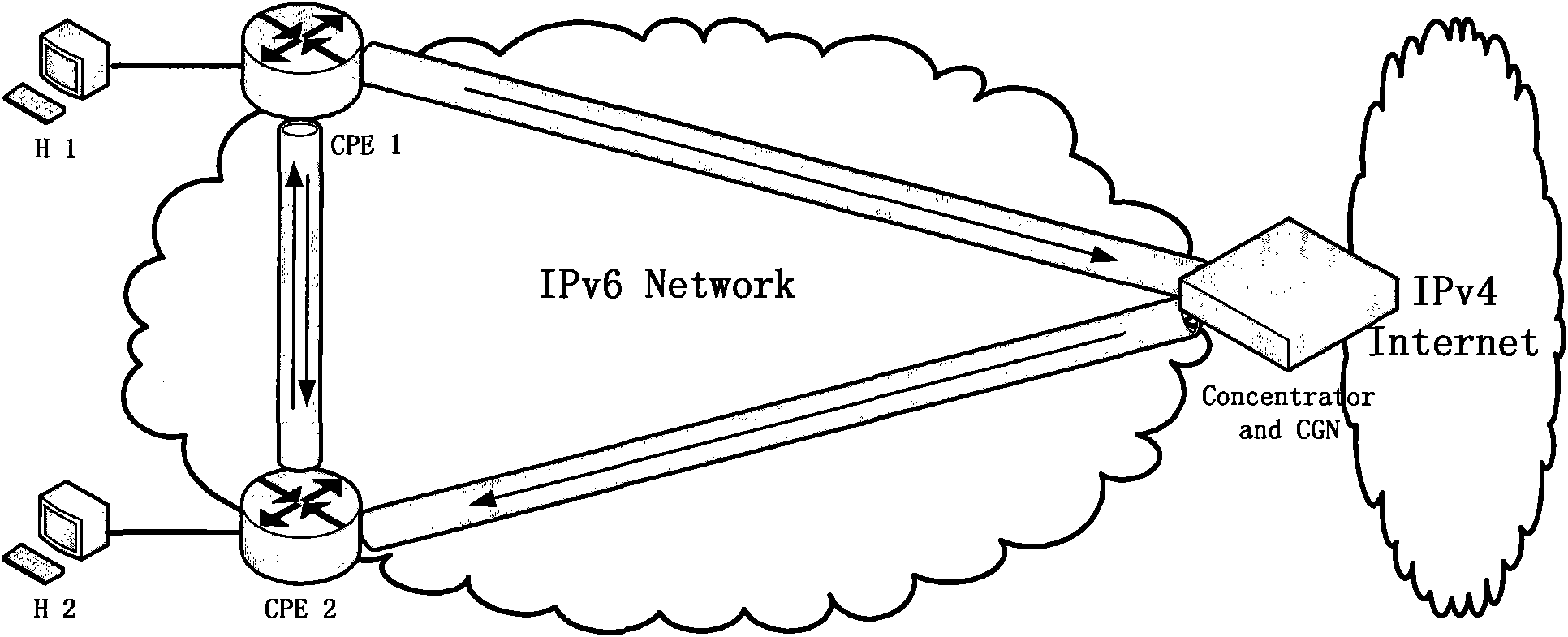
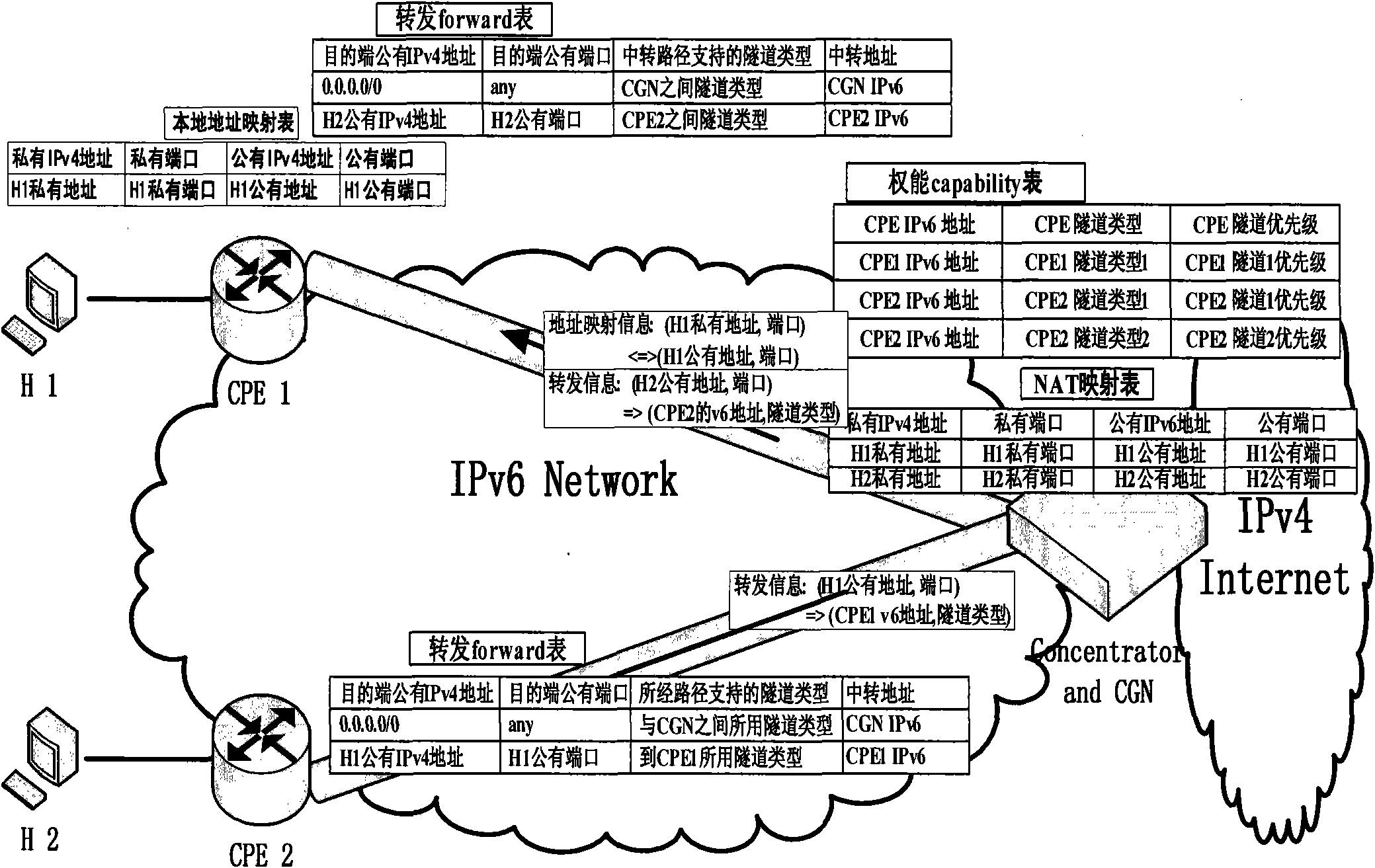
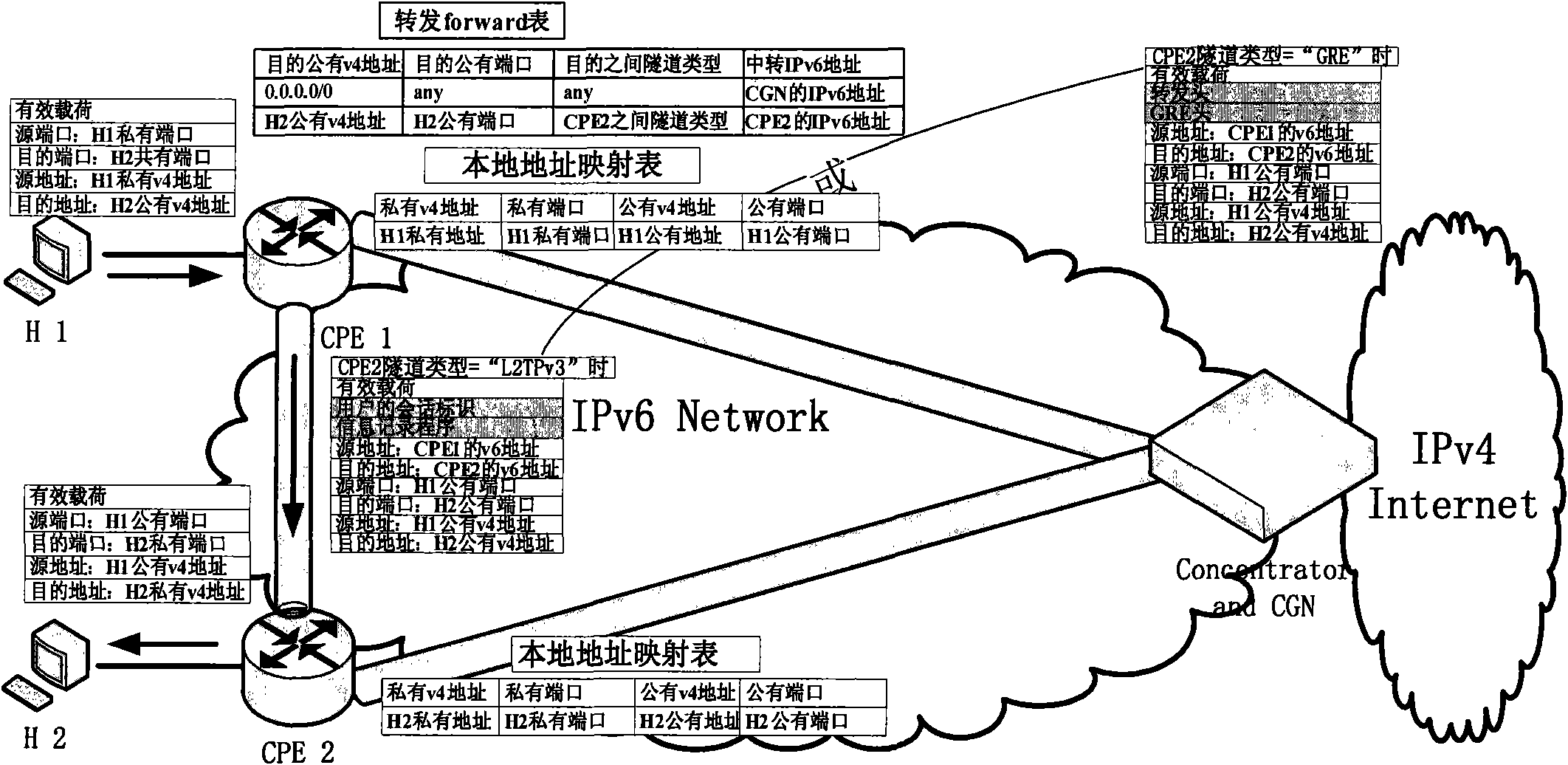
Tunnel selection method in optimization of visit between hosts under edge network double stack access
ActiveCN101977250ASupport diversityData switching by path configurationData transmissionNetwork address
The invention discloses a tunnel selection method in the optimization of visit between hosts under edge network double stack access, belonging to the field of the Internet technology. The tunnel selection method is characterized in that a tunnel selection mechanism is added to a consultation mechanism between client access equipment CPE and a network address decoder CGN, which is introduced underedge network double stack access; under the condition that all the CPEs support the tunnel mechanism in 2-3 and the CGN feeds back CGN tunnel information to each CPE according to the IPv6 address of each CPE, tunnel types supported by the CPEs and the priority grade thereof, the CGN is used for maintaining the tunnel types and other information under the edge network double stack access, and after being confirmed by the CGN, and tunnels used in the tunnel consultation mechanism are sent to the CPE used as source terminals. By the invention, the problem how to select a more proper tunnel type to carry out tunnel transmission when various tunnel mechanisms coexist can be solved, thereby better supporting the diversity of network application.
Owner:TSINGHUA UNIV
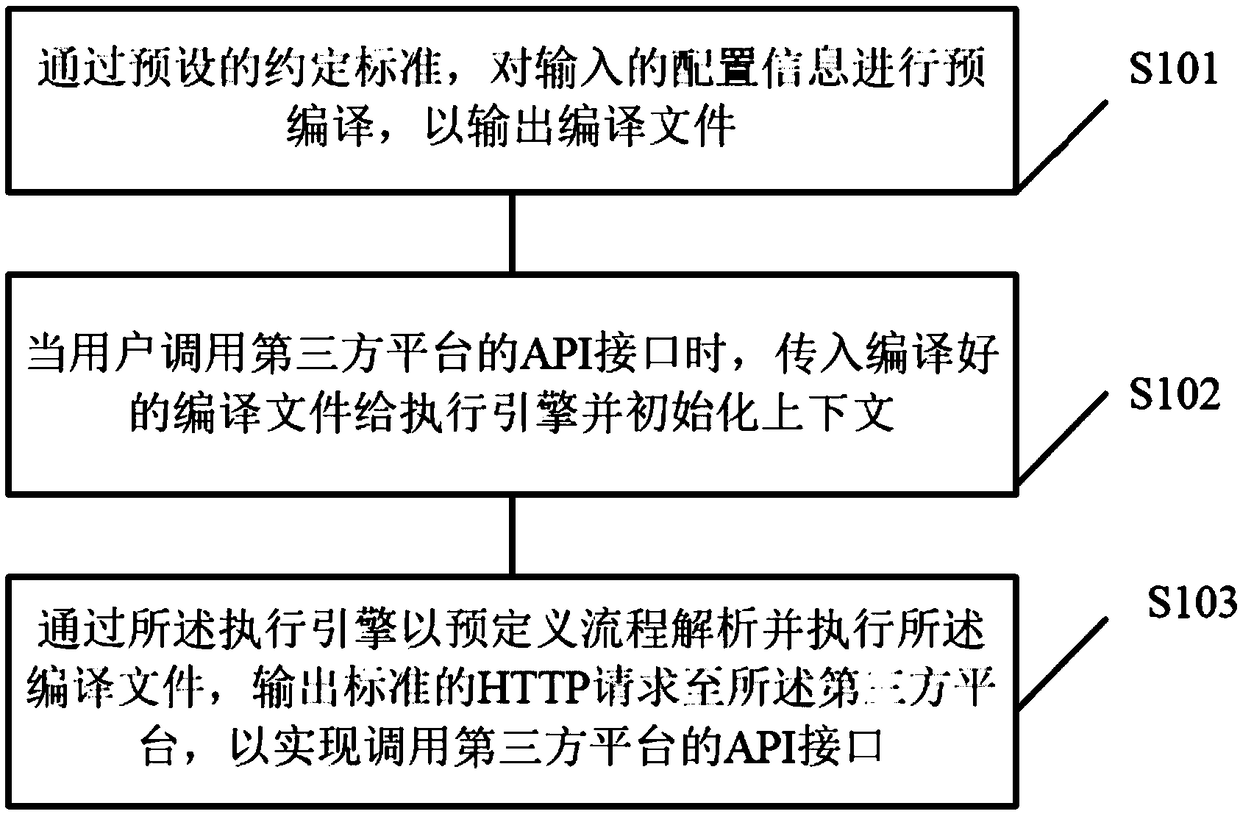
Third-party platform docking implementation method, device, equipment and storage medium
ActiveCN108829467AImplement the callQuick dockingExecution paradigmsCode compilationThird partySoftware engineering
The invention discloses a third-party platform docking implementation method, a device thereof, equipment and a storage medium. The method comprises: pre-compiling input configuration information by using a preset agreement standard to output a compiled file, wherein the configuration information includes predefined tags and content corresponding to each tag, and the tags are used to distinguish corresponding request headers, URL parameters, request bodies, and variables when calling an API interface of a third-party platform; when the user calls the API interface of the third-party platform,introducing the compiled file to the execution engine and initializing the context; parsing and executing the compiled file by the execution engine in a predefined process, outputting a standard HTTPrequest to the third-party platform, so as to implement the calling of the API interface of the third party platform. The invention may realize the docking to the API interface of the third-party platform, which is simple, low in error rate, high in expansion and low in maintenance cost.
Owner:GUANGZHOU FENGZHUSHOU NETWORK TECHNOLOGY CO LTD
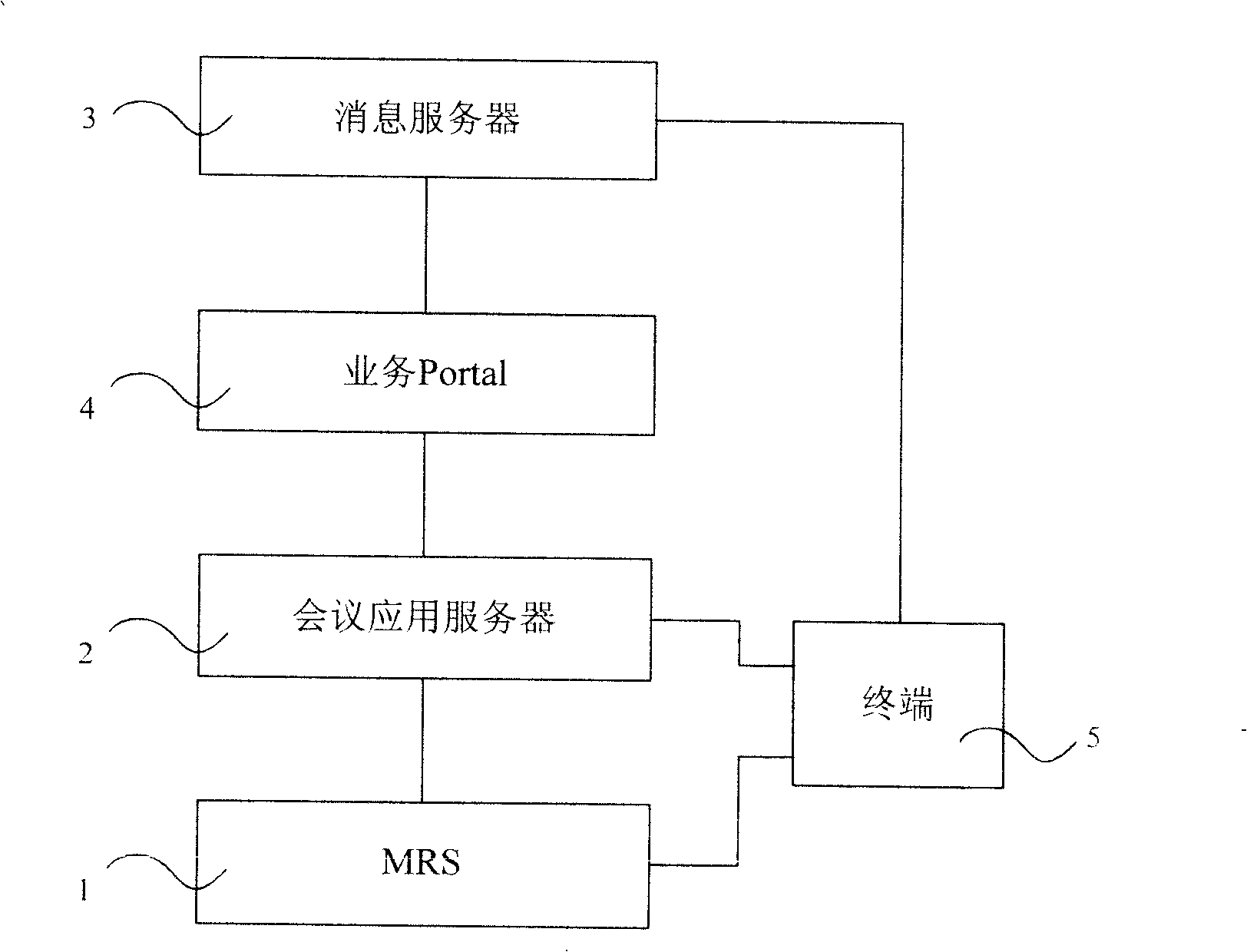
System and method for supporting multimedia conference booking
ActiveCN101257395BSupport diversityOvercoming the defect of single access formSpecial service provision for substationSpecial service for subscribersApplication serverMediaFLO
The invention discloses a system supporting the multimedia conferencing reservation, comprising: a media resource server, a conference application server. Also disclosed is a method for supporting the multimedia conferencing reservation, comprising: conference application server receiving the conferencing reservation request; conference application server building up meeting plate and requesting to reserving corresponding media resource to the media resource server; transmitting notification to the participating terminal of resource is successfully reserved; arriving at the conferencing reservation time, the conference application server transmitting order for participating into the conference to the conference terminal via IMS; the terminal received the order participating into the conference. The method supports the diversification of participating into conference; realizes that the conference server builds up the multimedia conference actively at the predetermined time and avoids the time waste and bad feeling when the conference inviter invites and builds up the conference bridge one by one.
Owner:CHINA MOBILE COMM GRP CO LTD
Reconfigurable variable length FIR filters for optimizing performance of digital repeater
InactiveCN104584002AAvoid permanent disadvantageSupport diversityDigital technique networkComplex mathematical operationsFiberProgrammable circuits
The invention addresses the problem of parameter optimization for best filter performance and, in particular, the influence from the requirements on radio or fiber to radio repeaters utilizing those filters, that often proves to be conflicting for an FIR filter. The FIR filters are implemented in a programmable circuit and are not thereby restricted for use in communication repeaters although this particular usage may put the most serious restrictions on the filter performance. Within the imposed constraints, this disclosure illustrates a method to strike a middle ground while minimizing the trade-offs. The advantage of the concept presented allows the choice of a suitable filter pertaining to a particular traffic configuration, meaning a particular choice of individually filtered frequency bands set at different gain and intended to support a diversity of traffic formats. The disclosed approach banks on the reconfigurable variable length FIR filter architectures. Implementation architecture and results in brief are also presented.
Owner:INTEL CORP
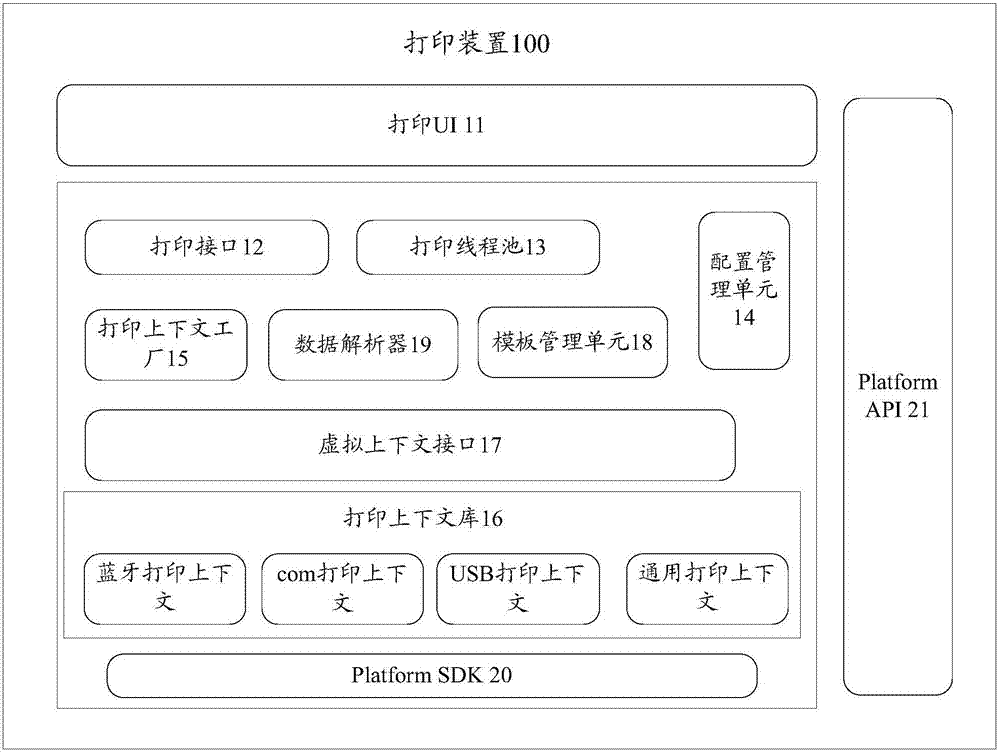
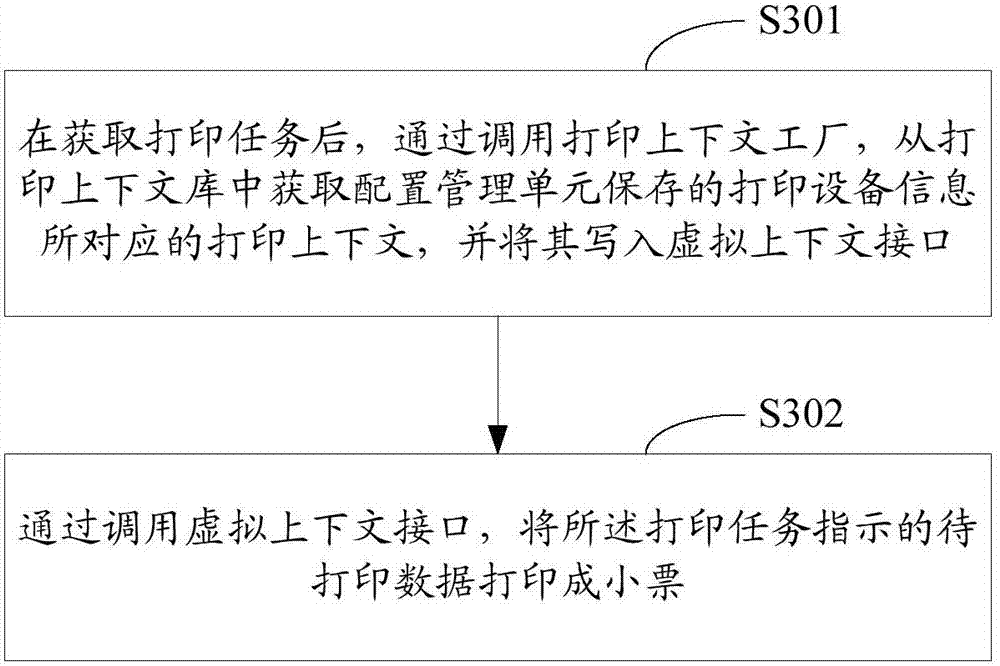
Printing apparatus and printing method
InactiveCN106933518AStrong scalabilityImprove scalabilityDigital output to print unitsConfiguration managementComputer engineering
The invention relates to the technical field of the internet, in particular to a printing apparatus and a printing method. The printing apparatus comprises a configuration management unit, a printing context plant, a printing context library and a virtual context interface, wherein the configuration management unit is used for providing a printing device configuration interface for a user to configure printing device information needed to be used, and storing the printing device information; the printing context plant is used for obtaining a printing context corresponding to the printing device information stored by the configuration management unit from the printing context library and writing the printing context in the virtual context interface; the printing context library is used for storing printing contexts corresponding to different printing devices; and the virtual context interface is used for storing the printing contexts written by the printing context plant and providing a printing call interface.
Owner:KOUBEI HLDG
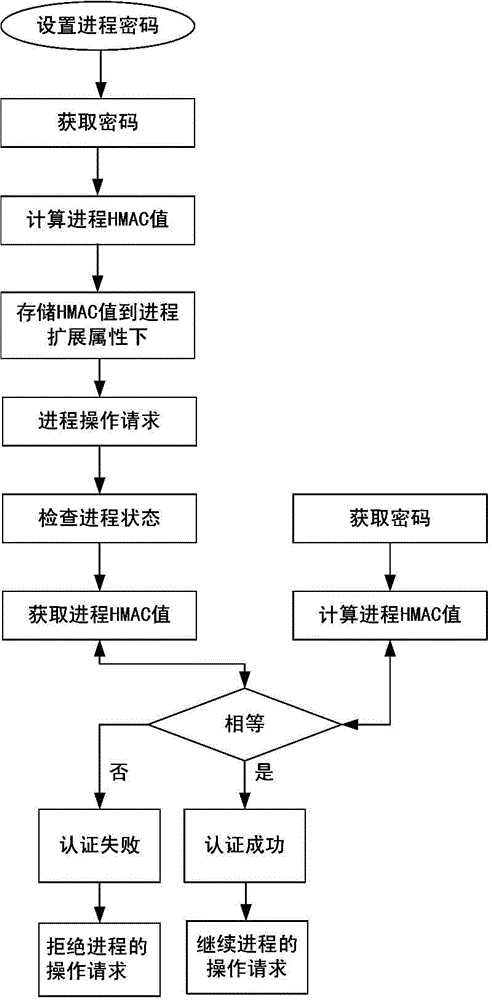
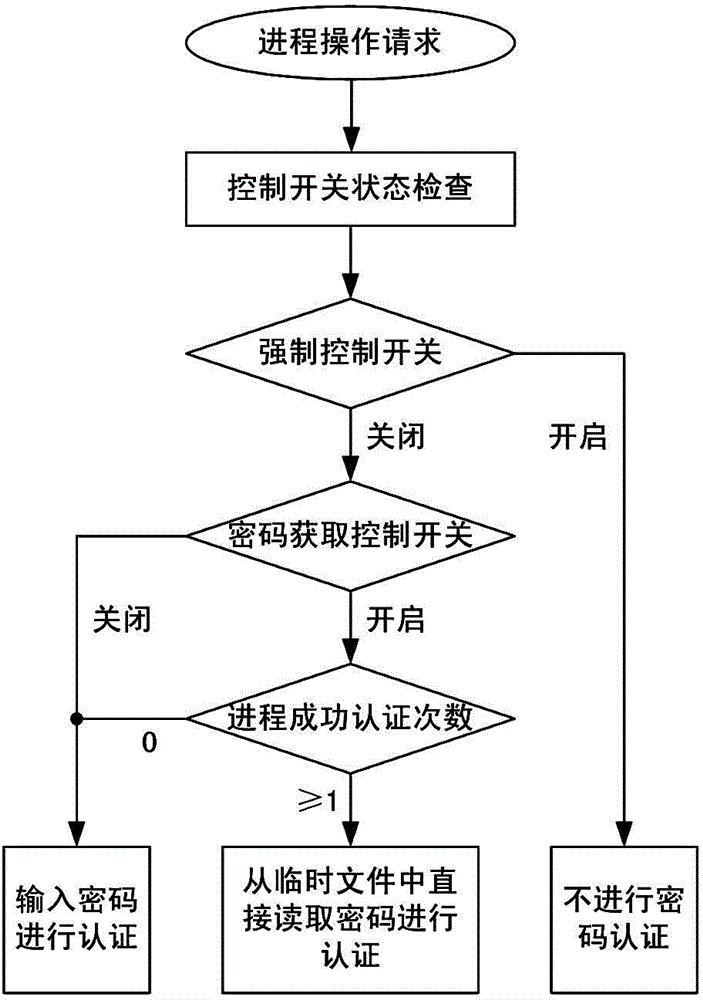
Progress authentication method based on password
ActiveCN104408365AReduce risks such as process execution and tamperingImprove securityDigital data authenticationControl switchExtensibility
The invention discloses a progress authentication method based on a password. The method comprises the following steps: setting an authentication password for a progress, calculating the HMAC value of the progress according to the authentication password and storing the HMAC value in extended attributes; presetting a password acquisition control switch in an operating system and configuring password acquisition control switch states; after receiving an operation request of the progress, judging whether to check the password according to the password acquisition control switch, acquiring the authentication password if needing to check the password; calculating the HMAC value of the progress based on the authentication password, comparing the HMAC value obtained by calculation with the HMAC value in the extended attributes of the progress, judging that the password authentication of the progress is successful and continuing the operation request of the progress if the HMAC values are the same, otherwise rejecting the operation request of the progress. The method disclosed by the invention has the advantages of reducing the risk of falsification of the system progress and being high in safety, good in universality and high in extensibility.
Owner:NAT UNIV OF DEFENSE TECH
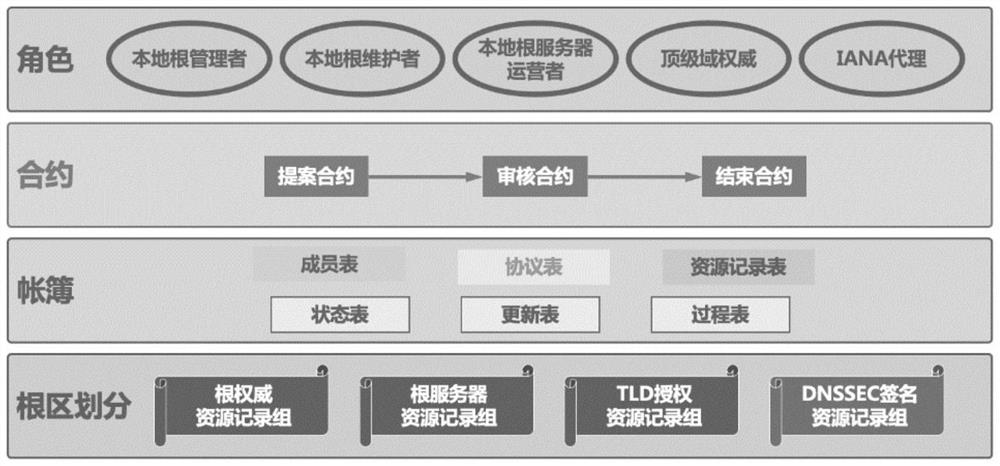
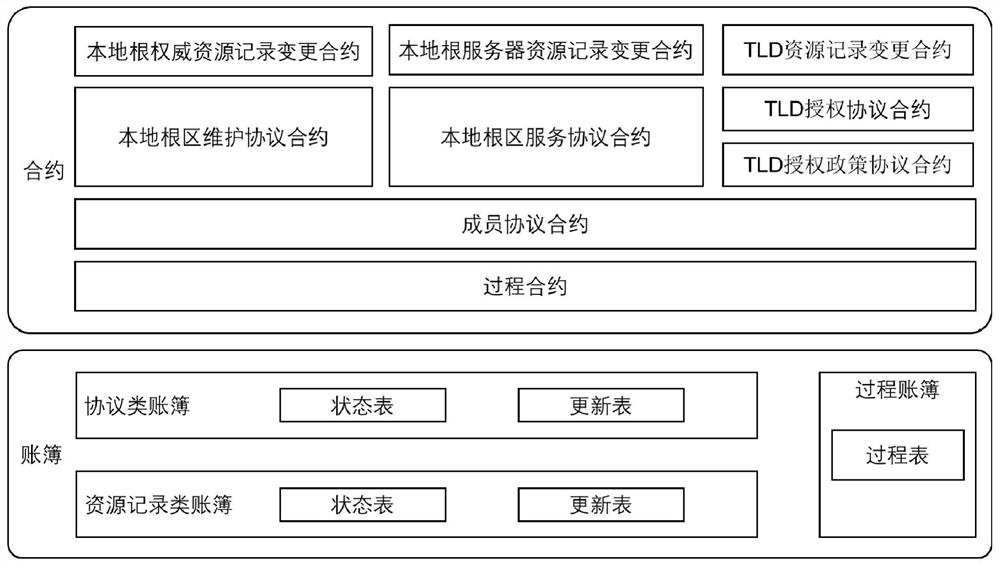
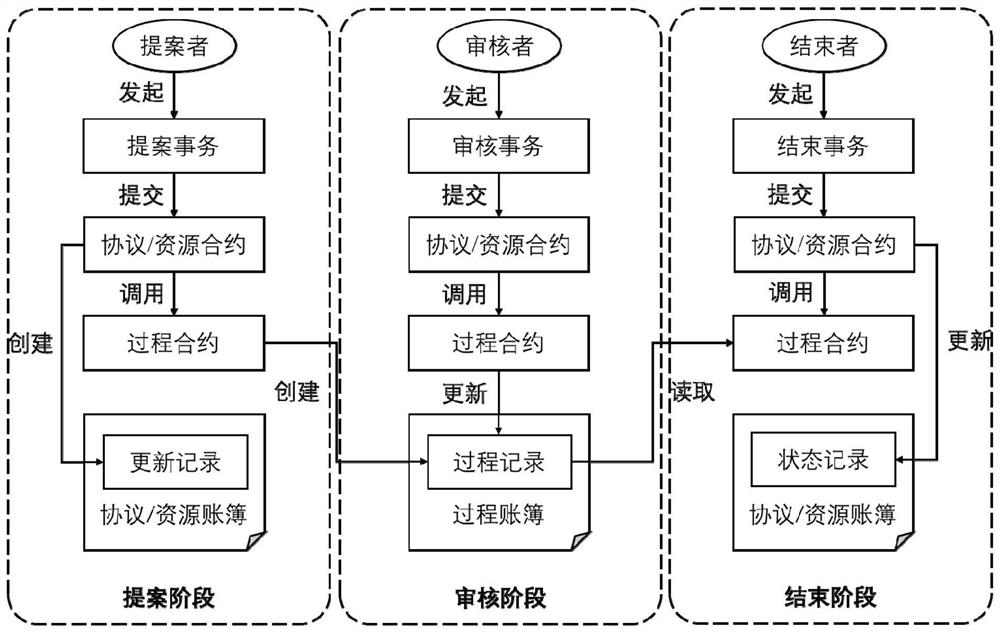
Intelligent contract system based on decentralized DNS root zone management
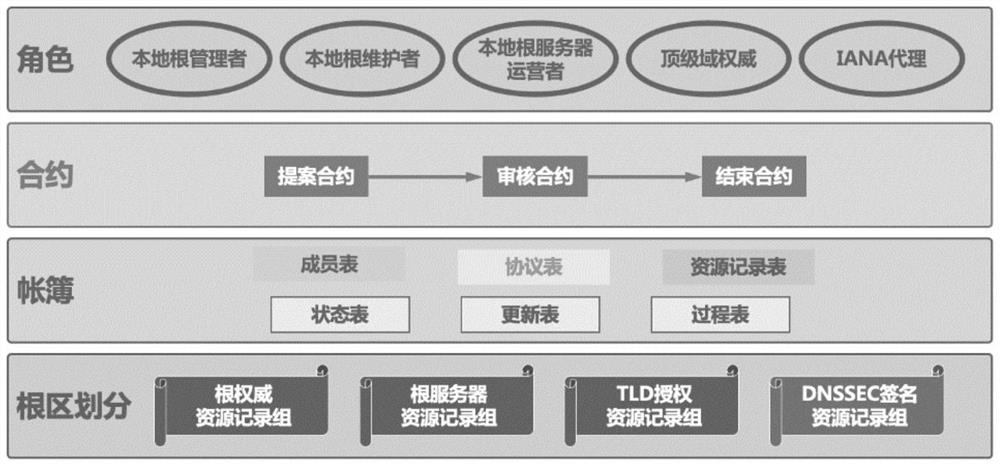
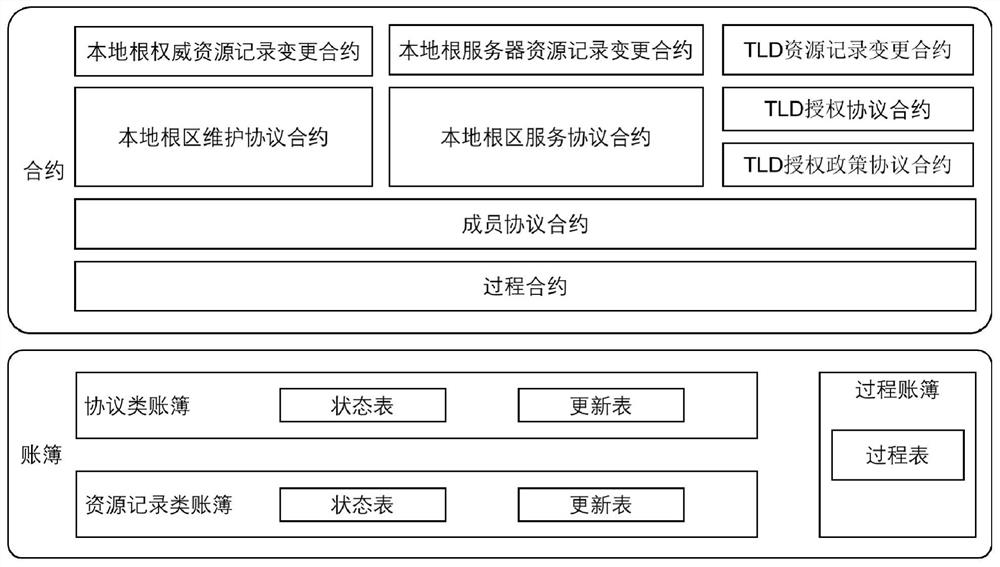
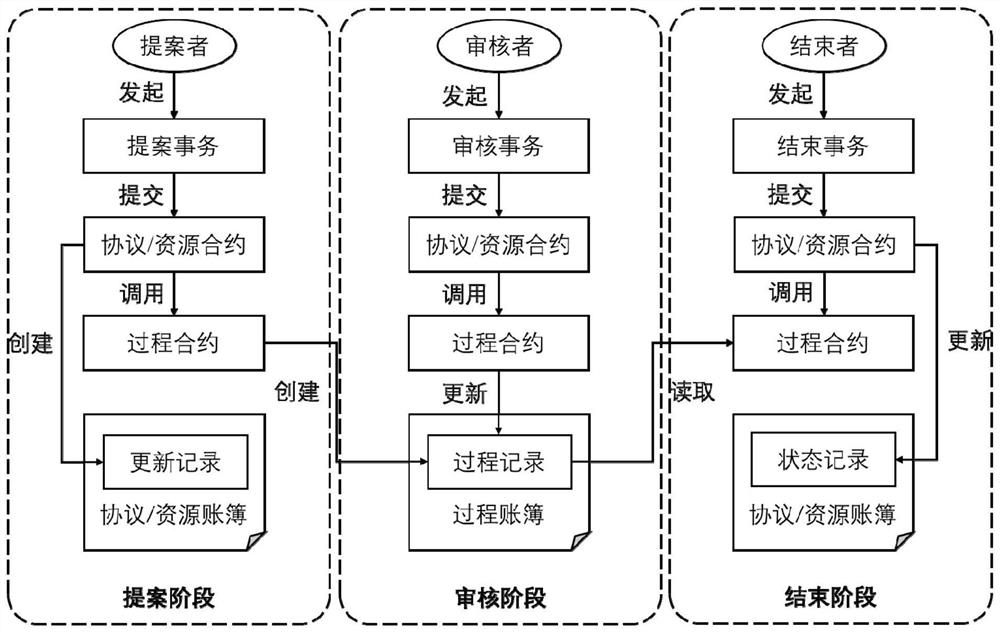
The invention discloses an intelligent contract system based on decentralized DNS root zone management, relates to the technical field of Internet, and is used for solving the problems of ambiguity of governance subjects, name space splitting and malicious rush injection caused by the existing root zone management decentralized technology. The technical key points of the invention are as follows: an account book module abstracts various data existing in root zone management into processes, protocols and resources; a contract module abstracts the updating of the protocol and resource data into a proposal-auditing-ending three-stage model, and uses a flexible auditing strategy, thereby supporting the diversity of root zone management. According to the root zone management system, the problems of centralization, low transparency, low automation degree and the like of traditional root zone management are solved, and the system can enable a plurality of participants of root zone management to access all root zone management data and participate in multi-party management of the root zone in a highly automatic mode. The method can be applied to the management of the domain name system root zone data in the Internet.
Owner:HARBIN INST OF TECH
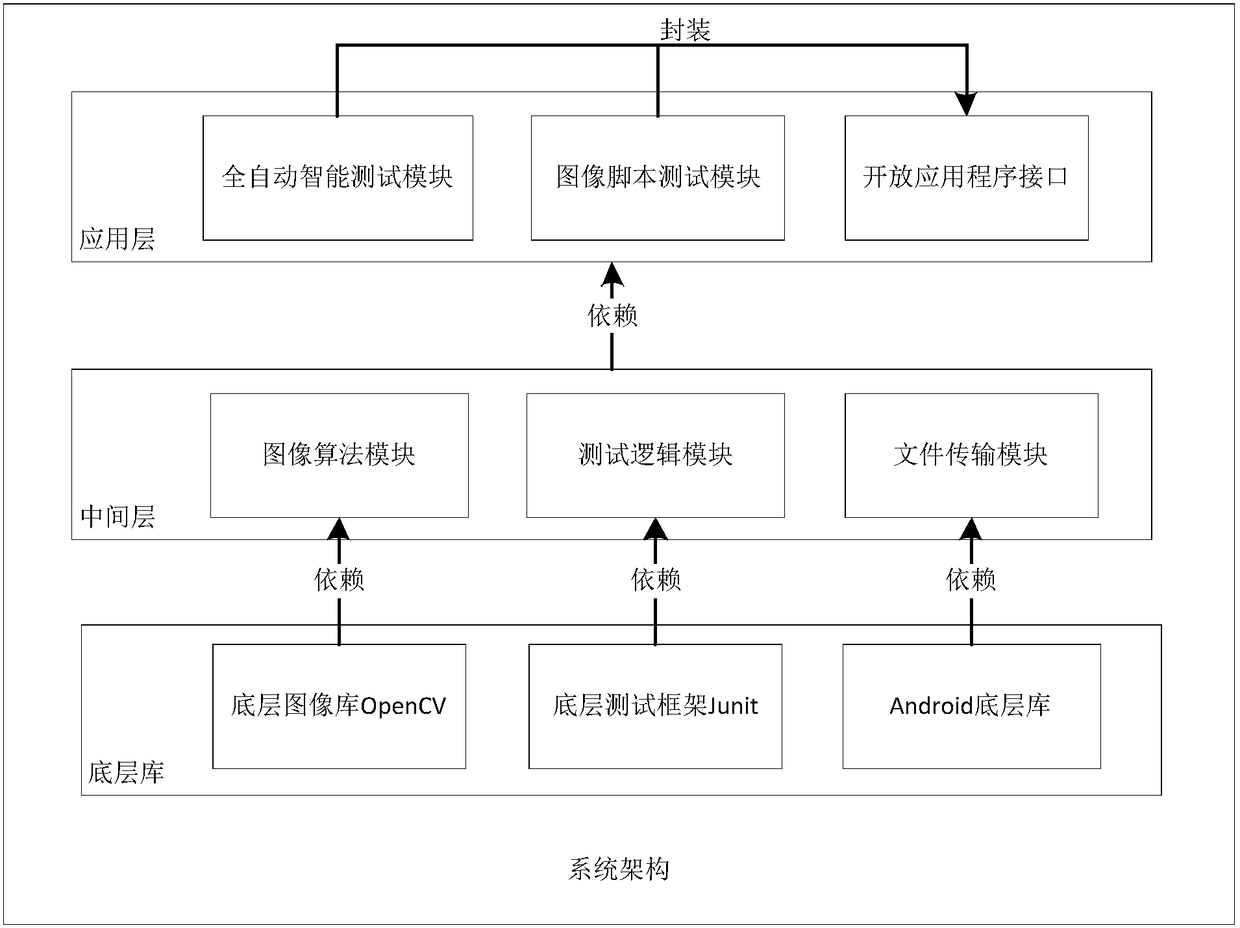
A computer vision-based mobile application testing system and method
ActiveCN105868102BImprove adaptabilityMeet operational needsSoftware testing/debuggingVision basedPoint match
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
Heart monitoring equipment and heart monitoring method
InactiveCN110327037AImprove accuracySupport diversityRespiratory organ evaluationSensorsEcg signalHeart monitoring
The invention provides heart monitoring equipment and a heart monitoring method. The heart monitoring device comprises an elastic chest band, an electrocardiosignal acquisition unit, an oxygen saturation acquisition unit, a respiratory motion acquisition unit and a processor; one end of the elastic chest band is connected to the respiratory motion acquisition unit, and the other end is connected to the processor so as to form a closed ring together; the electrocardiosignal acquisition unit, the oxygen saturation acquisition unit and the respiratory motion acquisition unit are all connected tothe processor so as to gather data acquired by the electrocardiosignal acquisition unit and the oxygen saturation acquisition unit to the processor; and the processor carries out mutual correction analysis on the data acquired by the three acquisition units and takes the correction analysis result as monitoring data. The result of mutual correction analysis based on the data acquired by the threeacquisition units is used as monitoring data, so that the diversity of the performance of the heart monitoring equipment is supported, the accuracy of the monitoring data is improved, and the requirements of current medical practice are met.
Owner:ZHONGSHAN HOSPITAL FUDAN UNIV
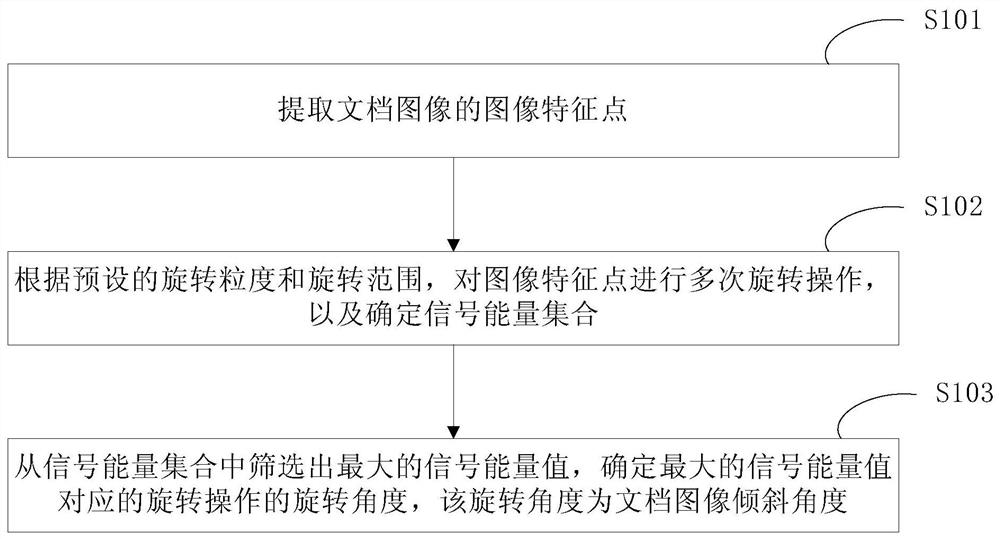
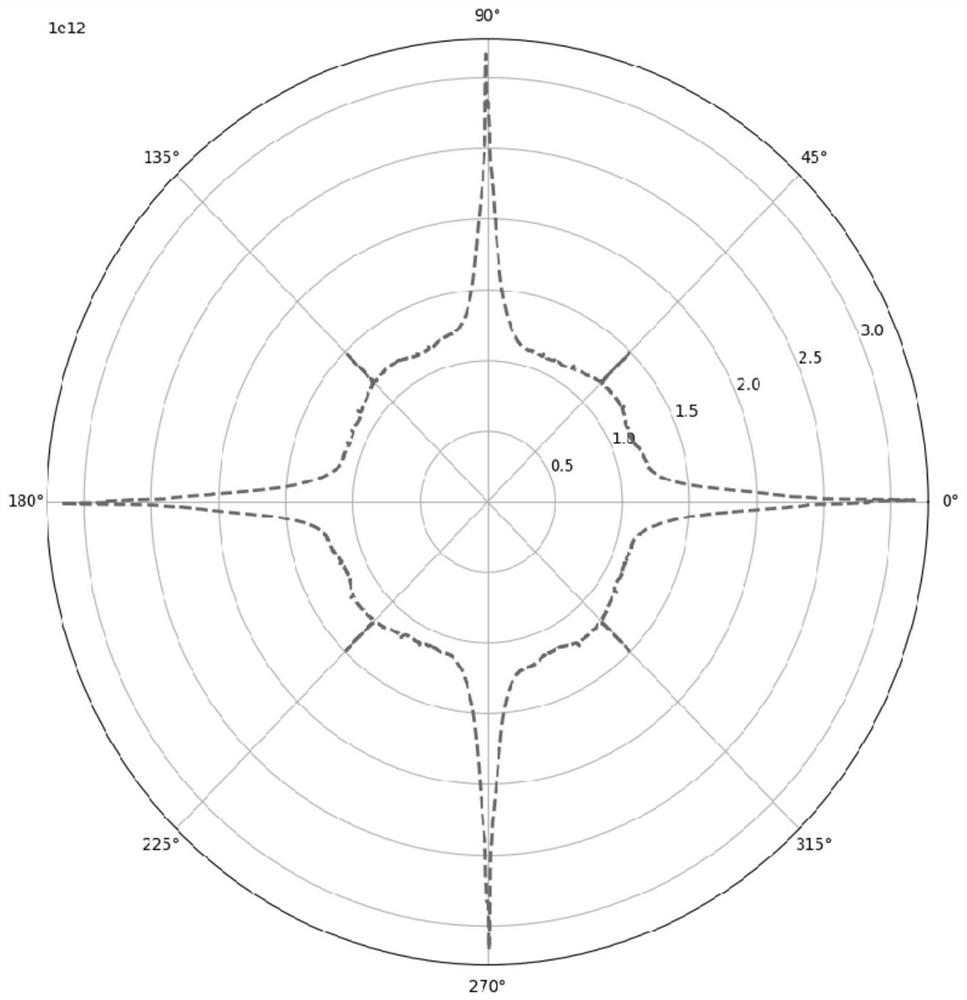
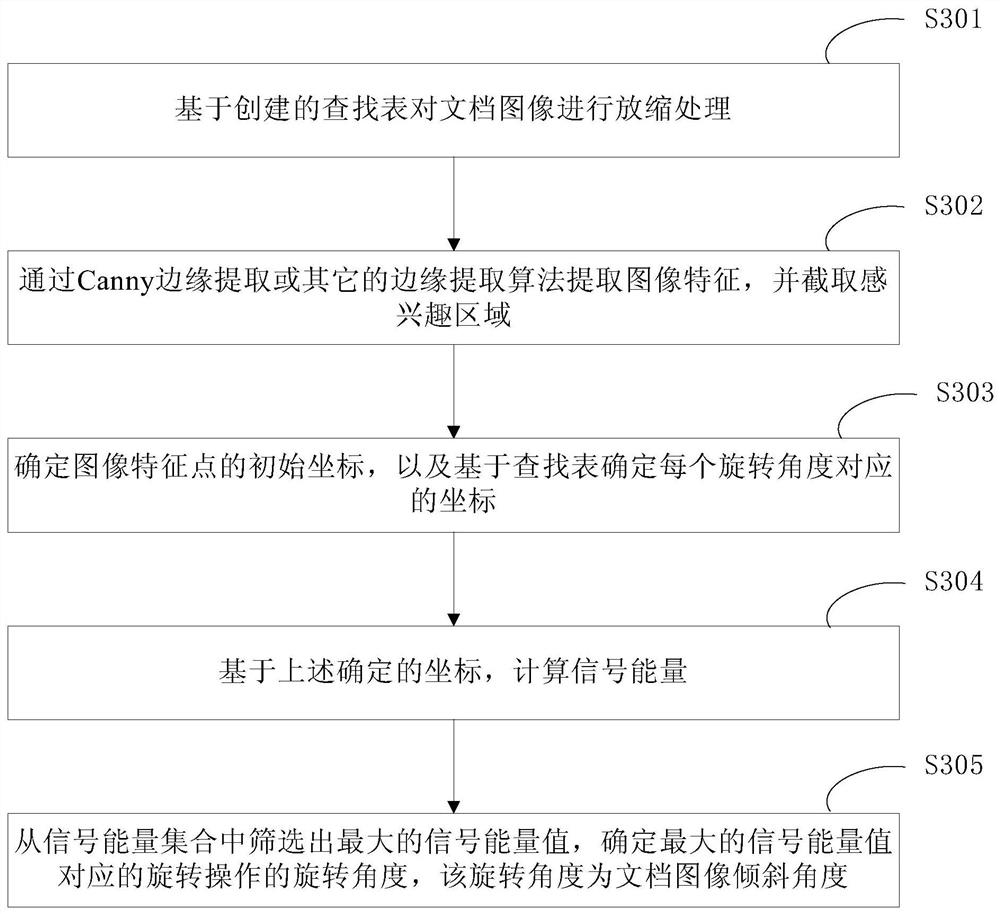
Method and device for document image tilt detection
ActiveCN109784332BSupport diversitySpeed up the detection progressCharacter and pattern recognitionComputer graphics (images)Engineering
The invention discloses a document image inclination detection method and device, and relates to the technical field of computers. A specific embodiment of the method comprises the steps of extractingimage feature points of a document image; Performing multiple rotation operations on the image feature points according to preset rotation granularity and rotation range, and determining a signal energy set; wherein the signal energy set comprises a signal energy value of each rotation operation; and screening out a maximum signal energy value from the signal energy set, and determining a rotation angle of a rotation operation corresponding to the maximum signal energy value, the rotation angle being a document image inclination angle. According to the method, the inclination angle is detected based on signal energy of image features, multiple document layouts are supported, the documents are not limited to be horizontal, vertical or mixed layouts, multiple image features are supported, the detection precision is high, and the calculation speed is increased.
Owner:JINGDONG TECH HLDG CO LTD
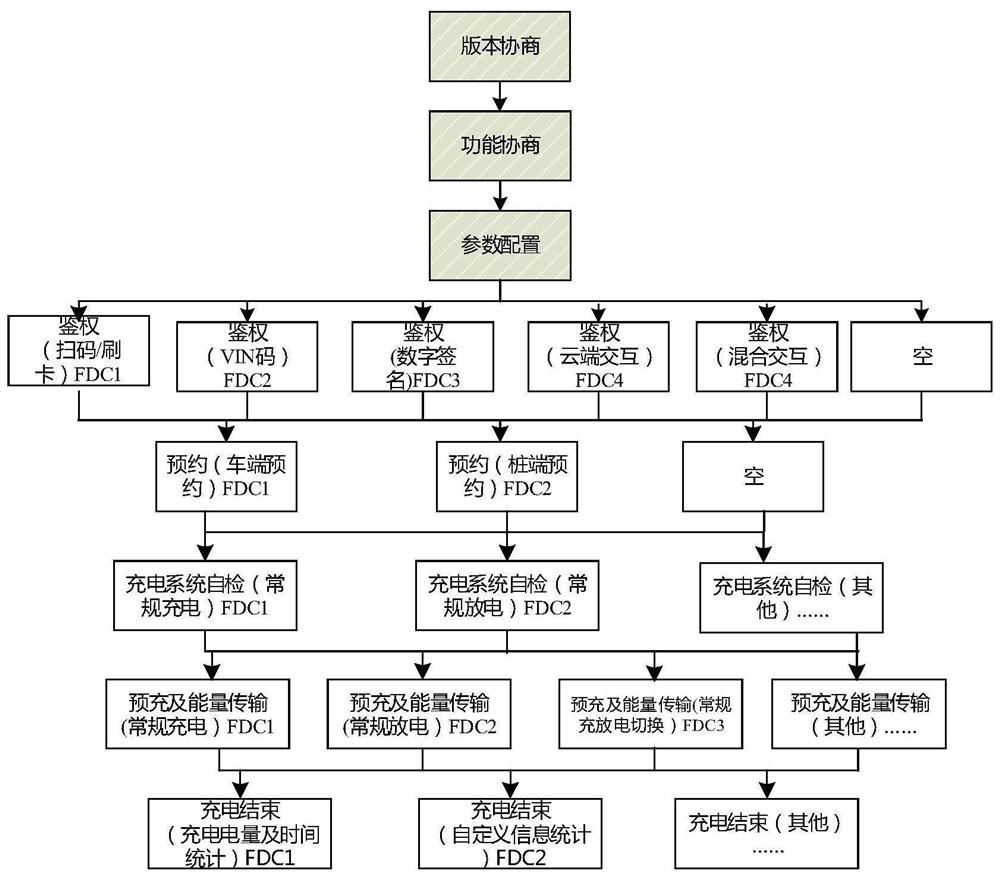
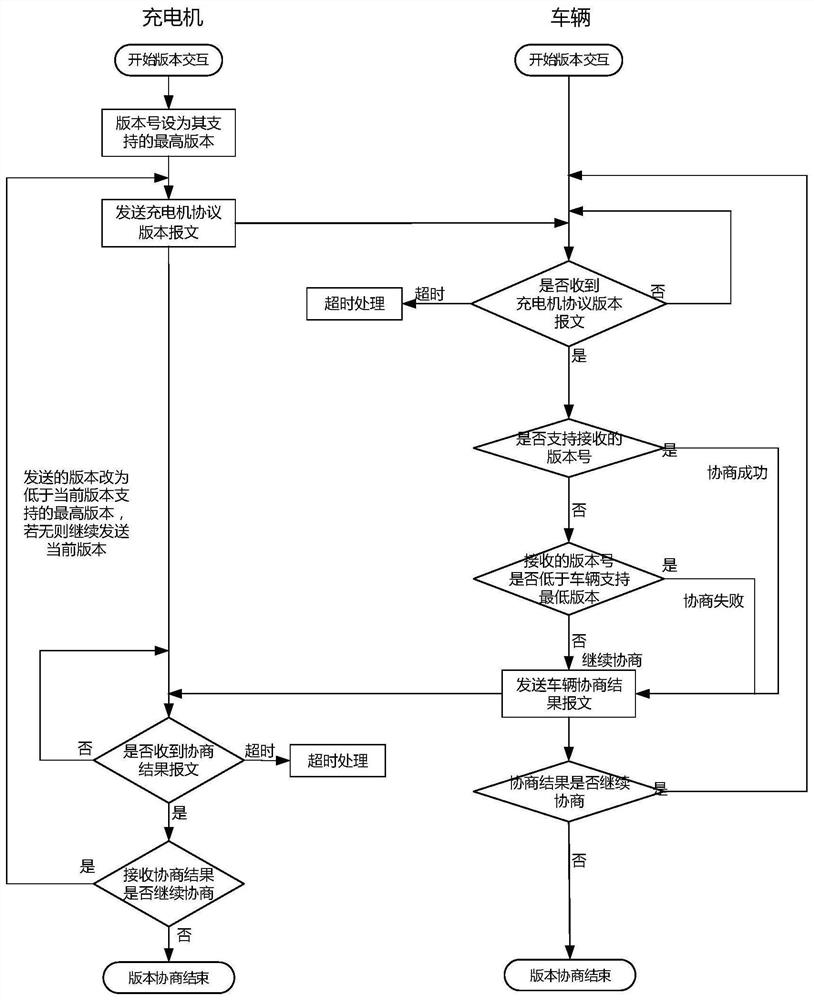
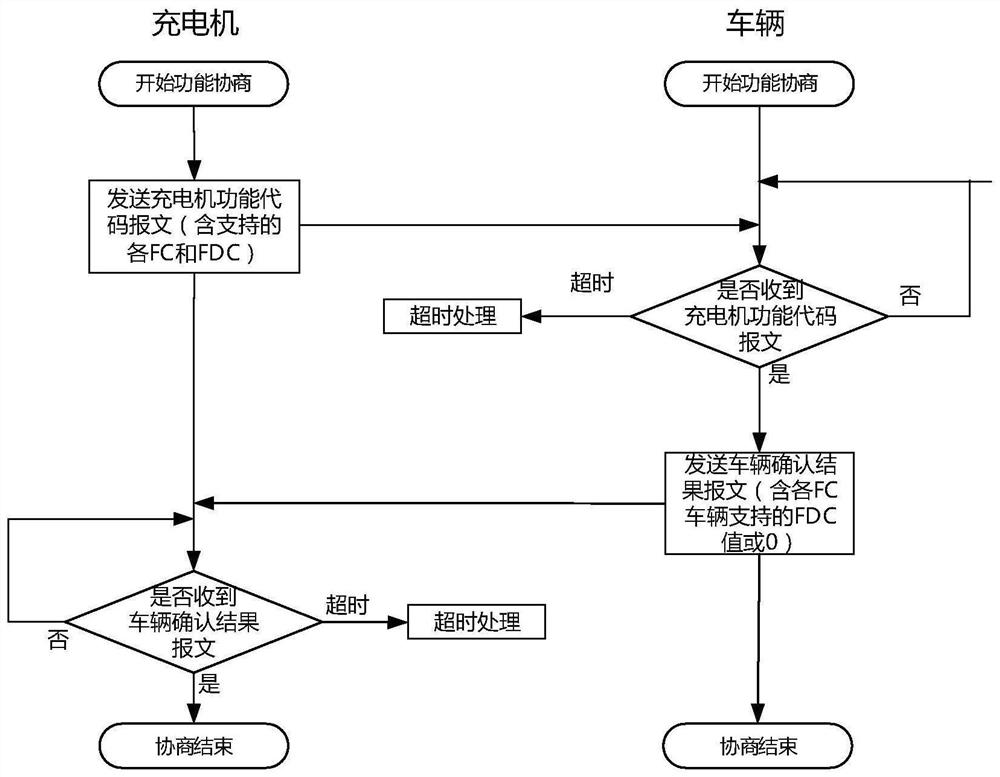
Charging communication protocol framework for electric vehicle and off-board charger and implementation method thereof
ActiveCN113689626ASupport for reloadable featuresSupport diversityCharging stationsElectric vehicle charging technologyIn vehicleElectric vehicle
The invention discloses a charging communication protocol framework for an electric vehicle and an off-board charger and an implementation method thereof. The charging communication protocol framework comprises a plurality of ordered function modules: version negotiation, function negotiation, parameter configuration, authentication, reservation, charging system self-inspection, pre-charging and energy transmission, and charging ending; the charging communication protocol is composed of all necessary function modules and zero or more optional function modules in the framework, and supports one or more application examples of the function modules capable of being reloaded at the same time; different versions of communication protocols can support different option function modules and different application examples of reloading function modules; the vehicle / charger following a certain specific version of communication protocol can realize all / part of functions supported by the version of communication protocol according to own realization conditions and requirements; through version negotiation, function negotiation and flexible configuration of the selectable function module and the reloaded function module, the requirements of the charging communication protocol for compatibility, expansibility and flexibility are met.
Owner:STATE GRID ELECTRIC POWER RES INST +1
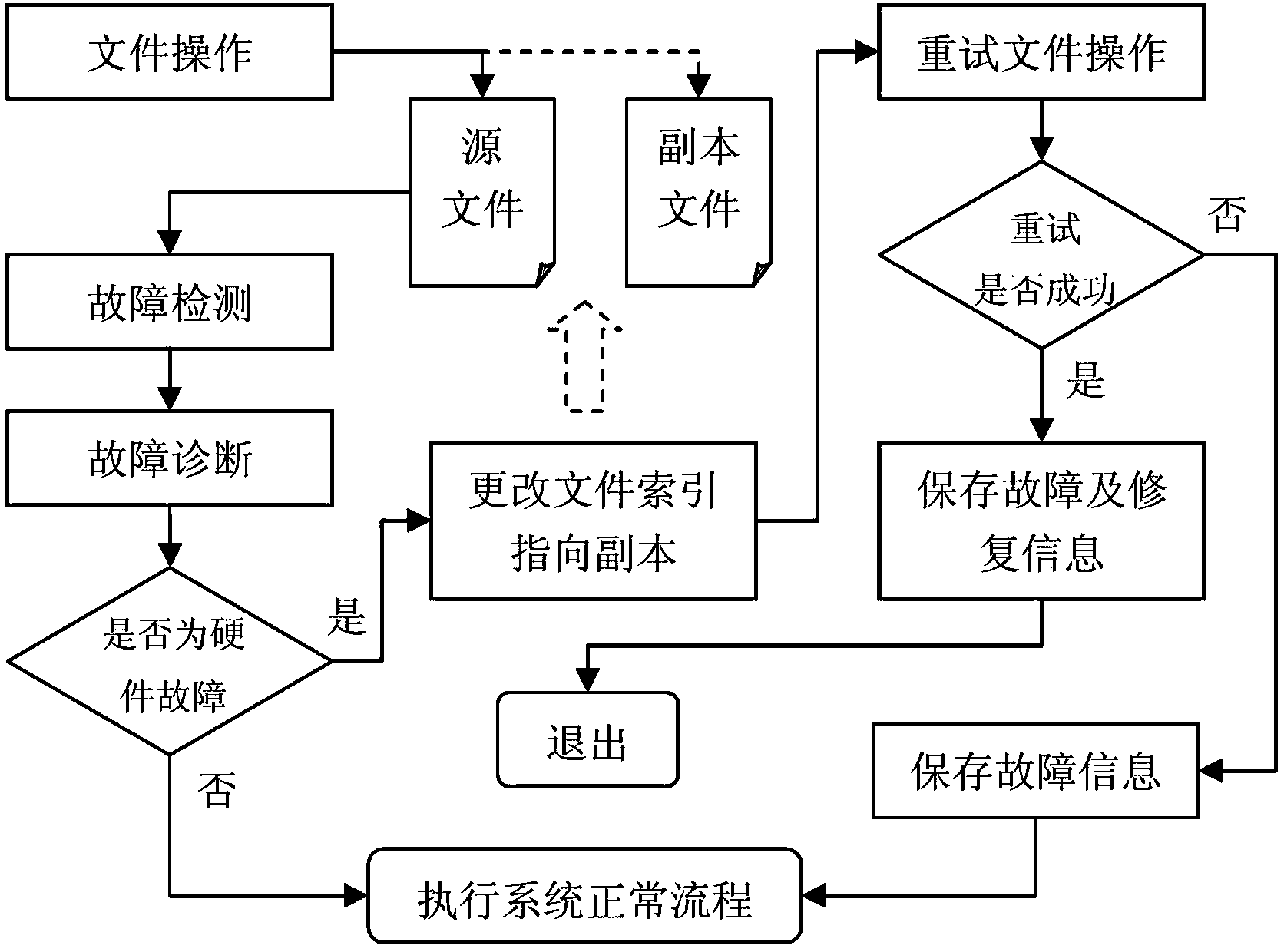
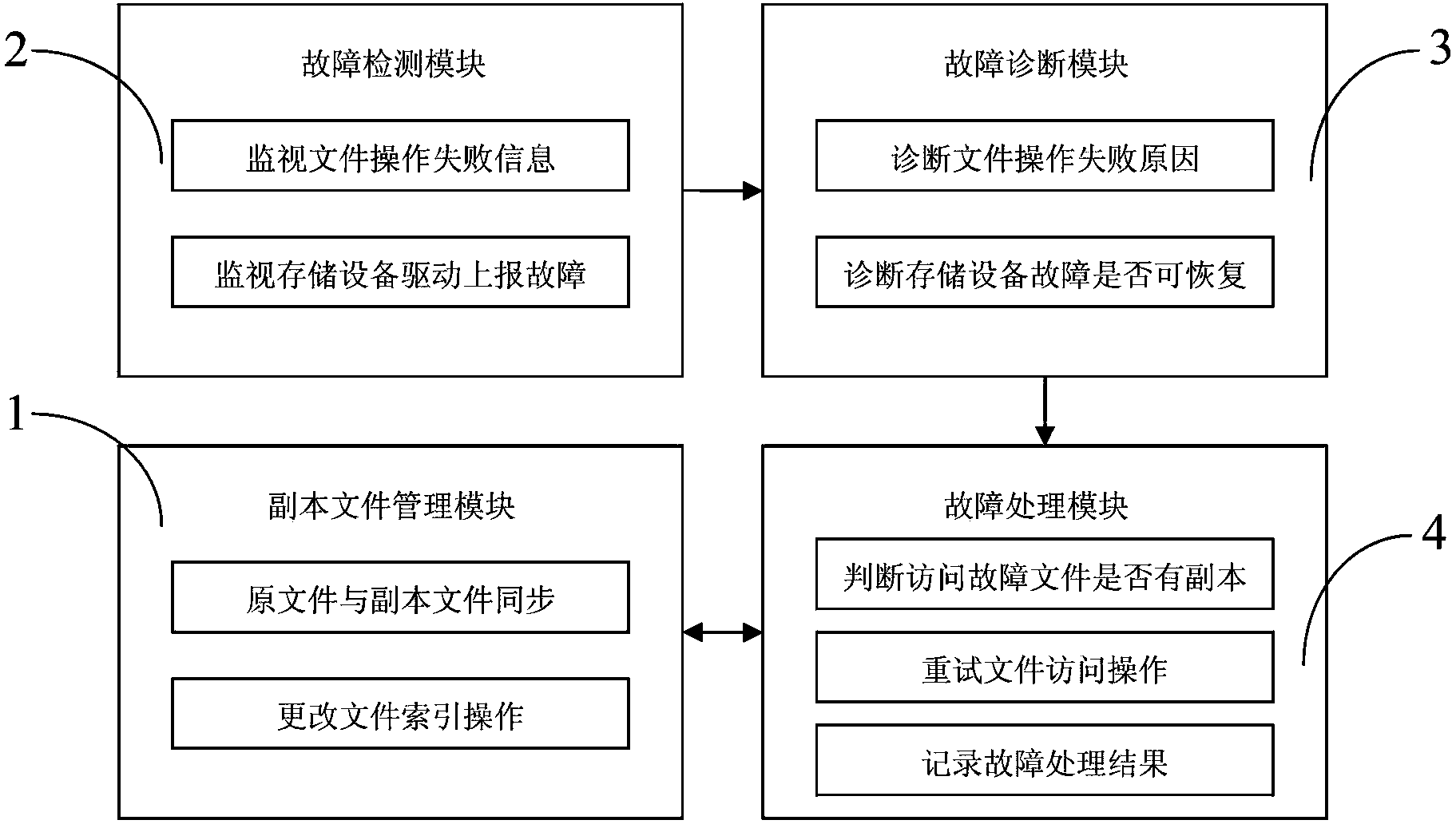
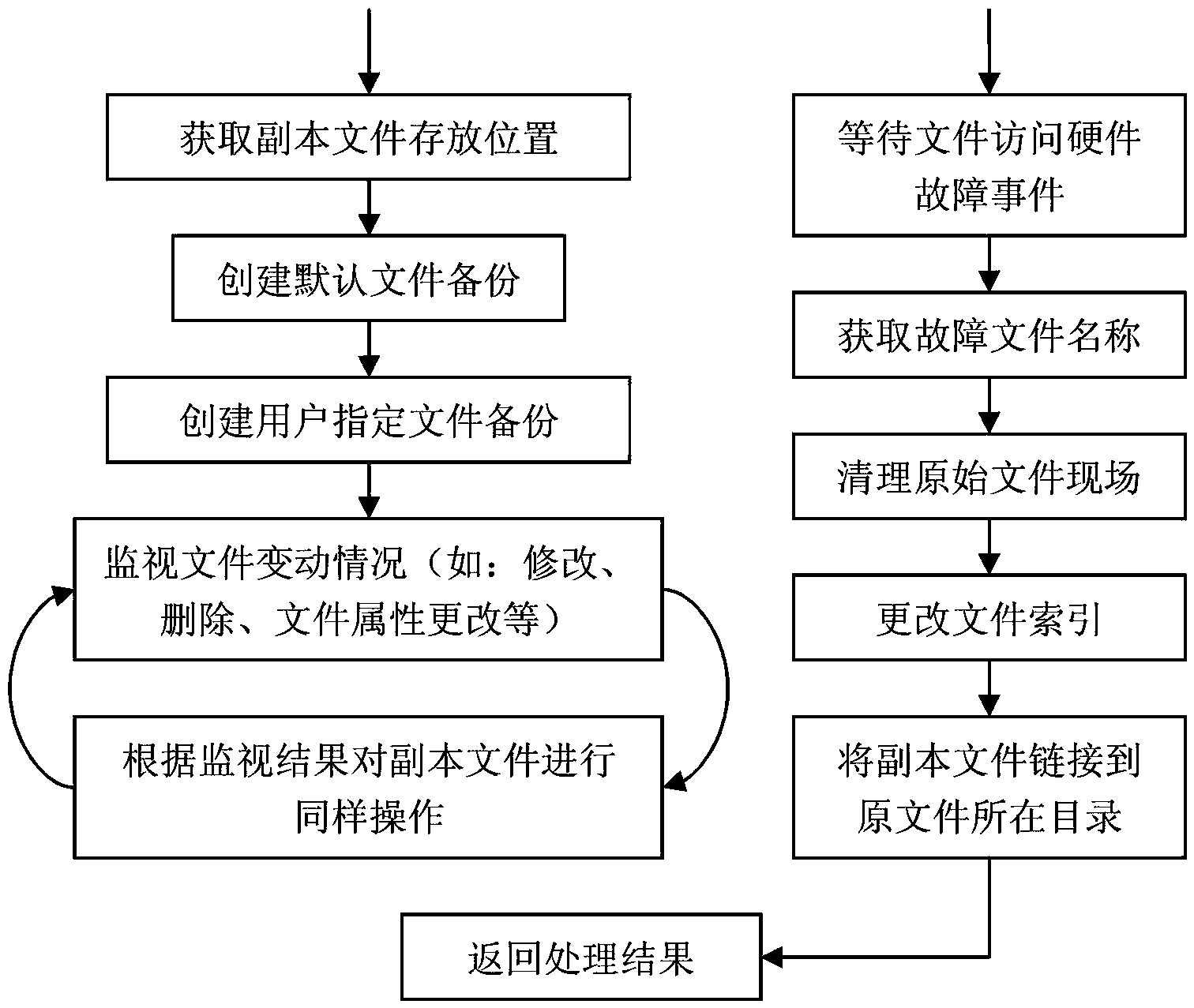
Hardware fault-oriented method and device for correcting faults in key files of system
InactiveCN102880522BAvoid inaccessibilityAvoid failureFault responseSpecial data processing applicationsFault toleranceOperational system
The invention discloses a hardware fault-oriented method and a hardware fault-oriented device for correcting faults in key files of a system. The method comprises the following steps: (1), establishing a backup file table which contains information of the key files of the system, establishing a copy file for each target file of the backup file table and maintaining synchronization of the copy files and the target files; (2), detecting file operation fault of an operating system in real time and diagnosing the reason of the fault, when the file confronting the operation fault is the target file corresponding to the backup file table and the fault is caused by hardware fault of a storage system, carrying out next step; and (3), replacing the file encountering the operation fault with the corresponding copy file and trying to operate the file again. The device comprises a copy file managing module, a fault detecting module, a fault diagnosing module and a fault processing module. According to the method and the device, the problem of system down or service crash caused by file access failure can be prevented; and the method and the device have the advantages of good fault tolerance characteristic, high robustness, real-time fault recovery, transparency to user, strong expandability and good commonality.
Owner:NAT UNIV OF DEFENSE TECH +1
Dynamic form implementation method and device, electronic equipment and storage medium
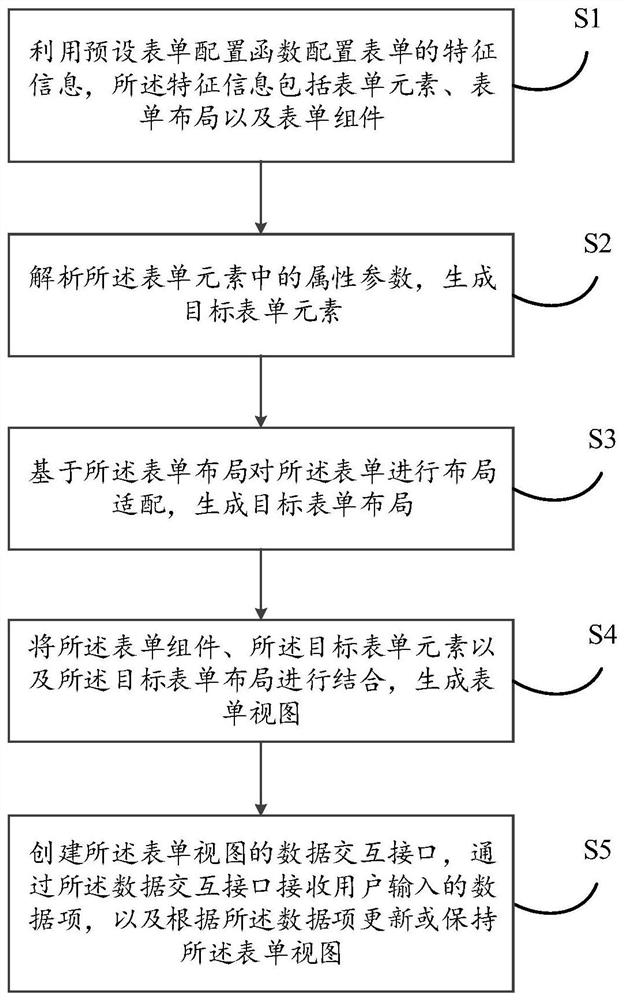
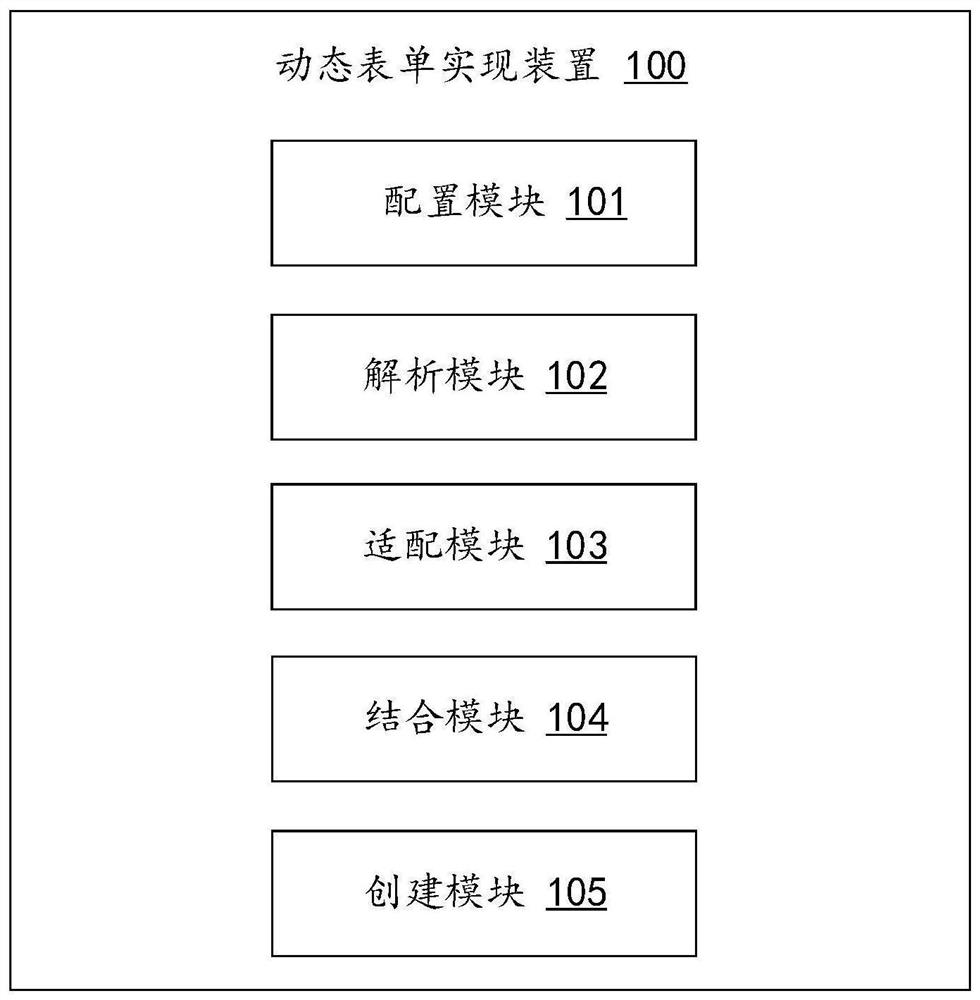
PendingCN111638876ASupport diversityEasy maintenanceVisual/graphical programmingCode compilationMaintainabilityUser input
The invention relates to the technical field of software development, and discloses a dynamic form implementation method, which comprises the steps of configuring feature information of a form by utilizing a preset form configuration function, the feature information comprising a form element, a form layout and a form component; analyzing attribute parameters in the form elements to generate target form elements; performing layout adaptation on the form based on the form layout to generate a target form layout; combining the form component, the target form element and the target form layout togenerate a form view; and creating a data interaction interface of the form view, receiving a data item input by a user through the data interaction interface, and updating or maintaining the form view according to the data item. The invention also relates to a blockchain technology, and the form view is stored in the blockchain. According to the invention, the maintainability and expansibility of the dynamic form can be improved, and the self-adaptive layout of the dynamic form is supported.
Owner:ONE CONNECT SMART TECH CO LTD SHENZHEN
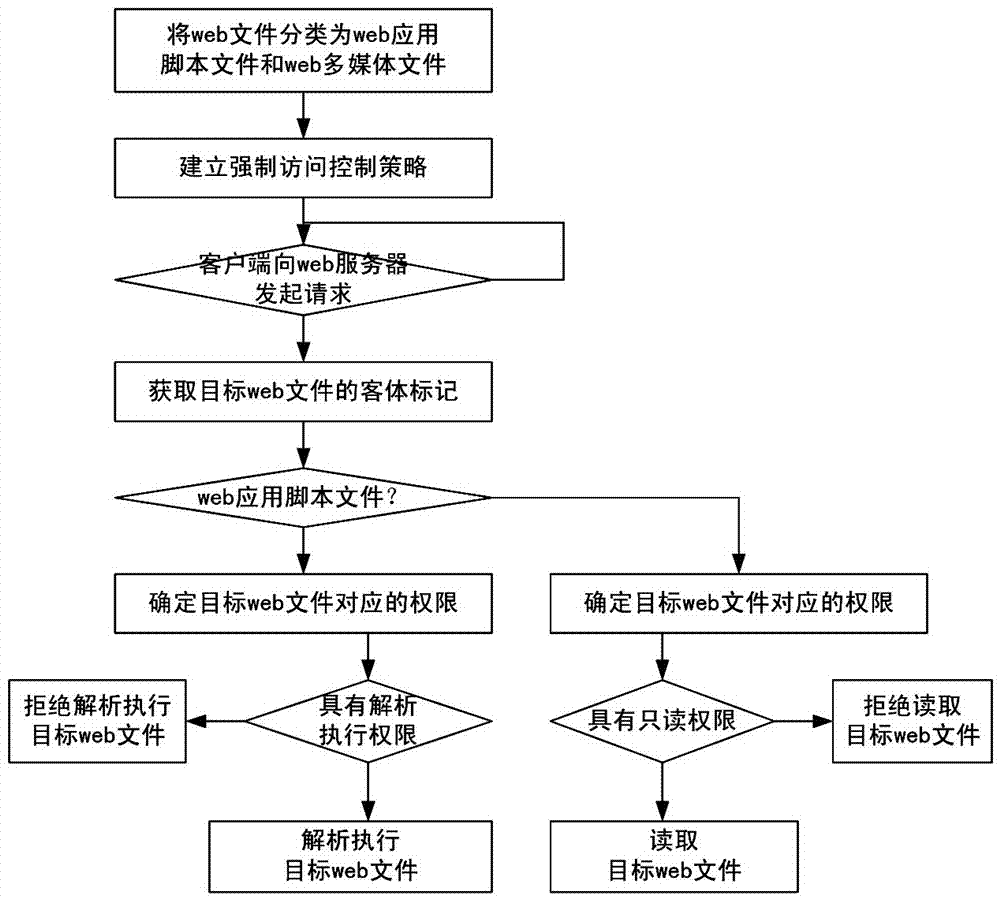
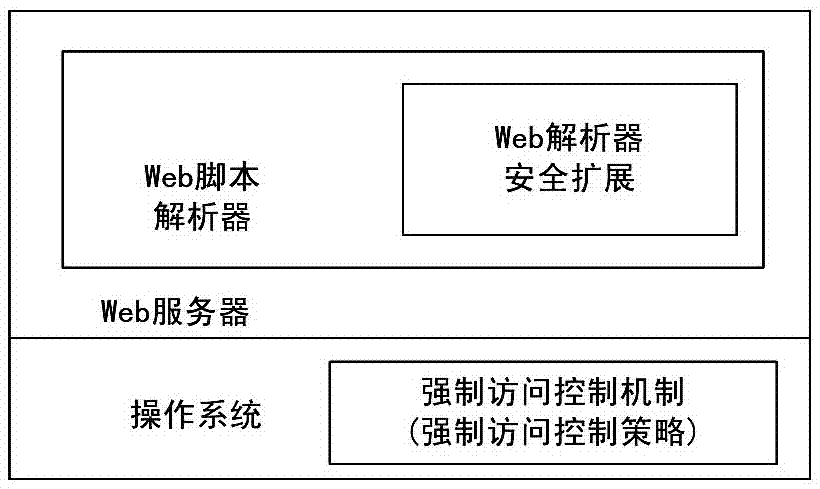
A webshell defense method based on mandatory access control mechanism
The invention discloses a webshell prevention method based on a mandatory access control mechanism. The webshell prevention method comprises the following implementation steps: classifying web files and establishing a mandatory access control policy based on classification; obtaining object tags of target web files requested by a client, inquiring the mandatory access control policy to determine limits of authority corresponding to the target web files if the object tags are web application script files and determining whether to analyze and implement the target web files or not according to inquiry results; inquiring the mandatory access control policy to determine limits of authority corresponding to the target web files if the object tags are web multi-media files and determining whether to read the target web files or not according to inquiry results. The webshell prevention method has the benefits that webshell uploaded by an intruder can be prohibited from being analyzed and implemented, so that the intruder is prevented from implementing further damage through the webshell; the webshell is complete in prevention and has high safety and reliability, low cost and good universality.
Owner:NAT UNIV OF DEFENSE TECH
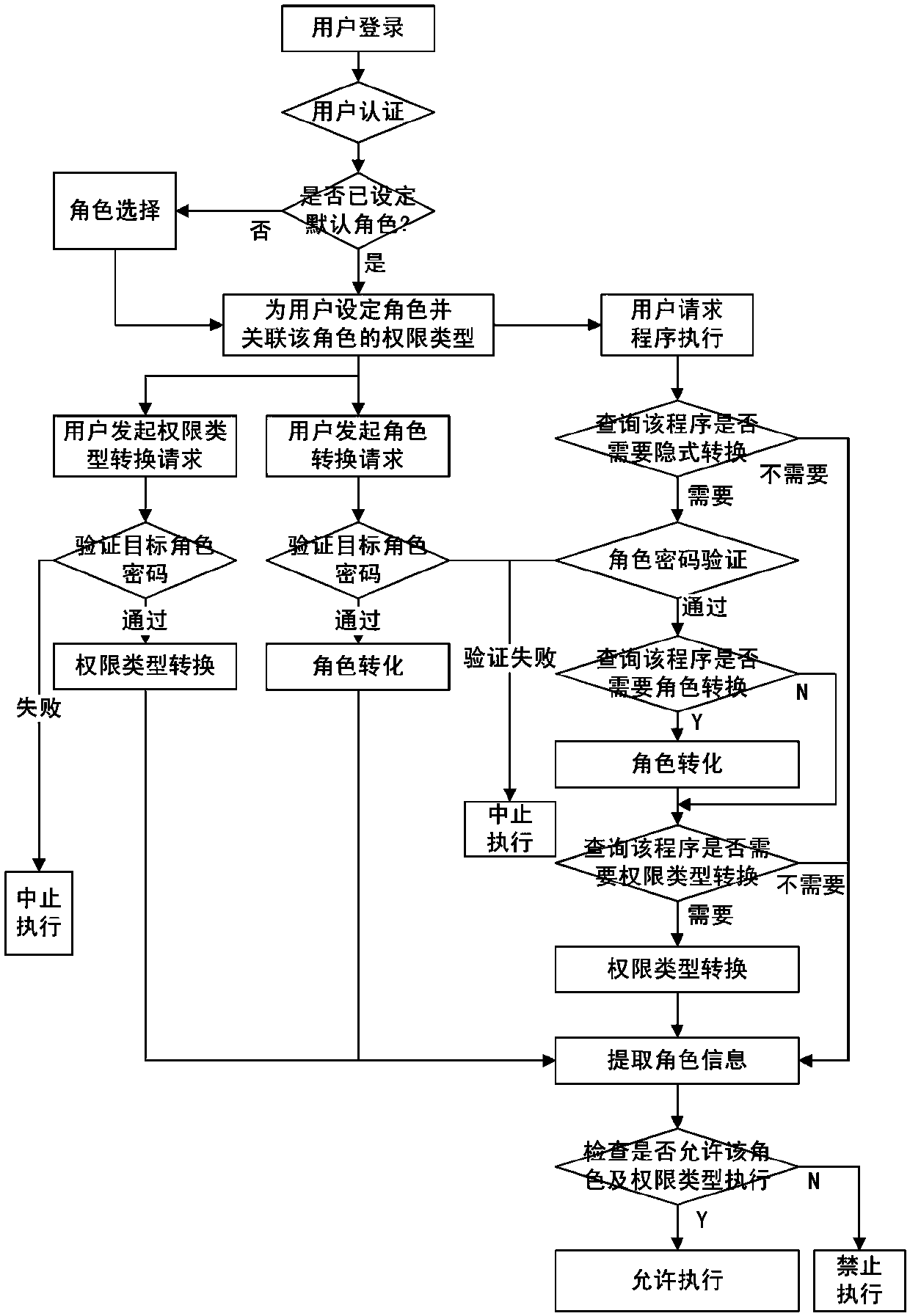
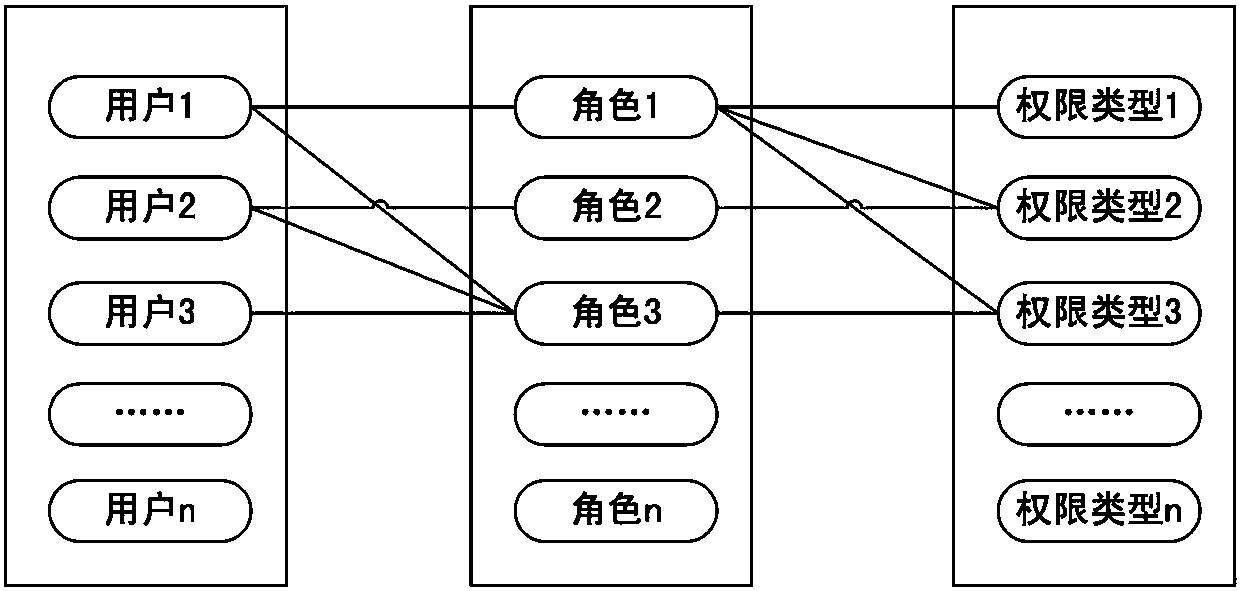
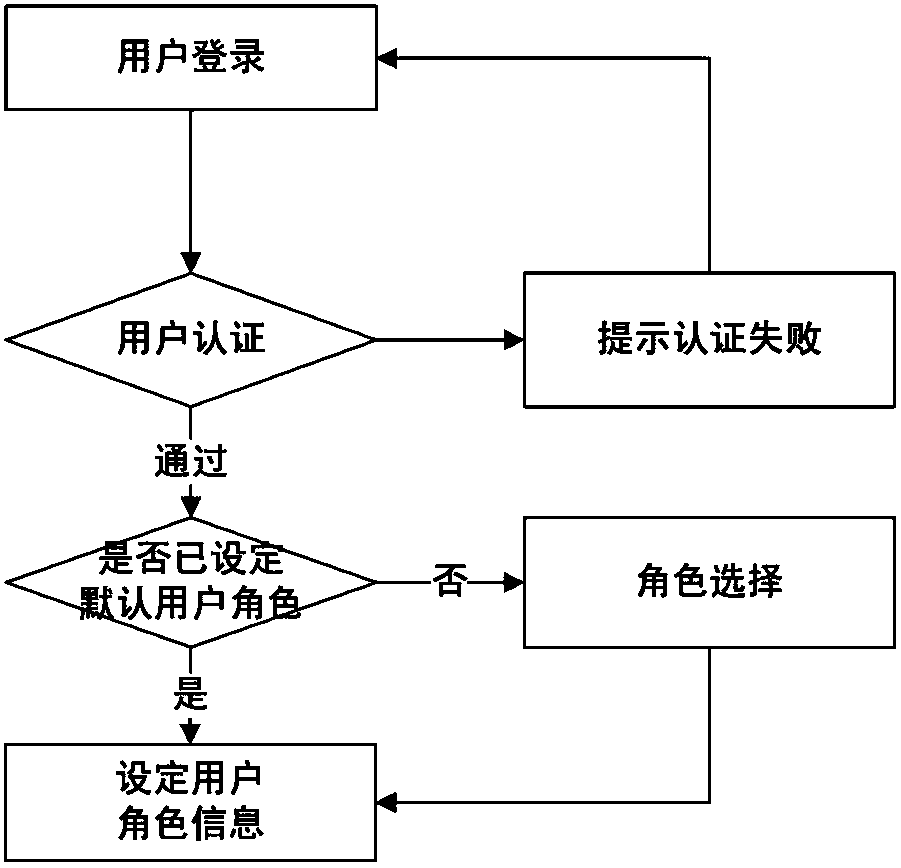
A Method of User Authorization on Demand Supporting Least Privilege
Owner:NAT UNIV OF DEFENSE TECH
Buried point-based data acquisition method and device, electronic equipment and storage medium
PendingCN112685259ASolve the problem of excessive resource consumptionSupport diversityHardware monitoringComputer hardwareControl set
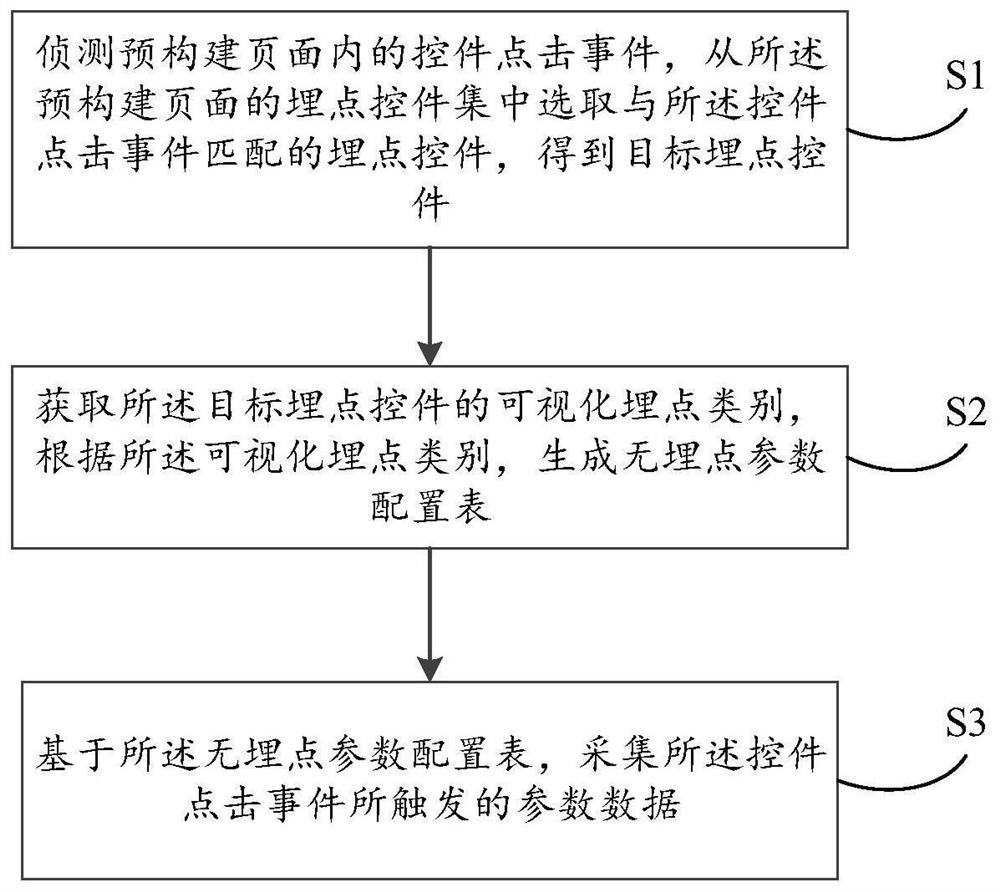
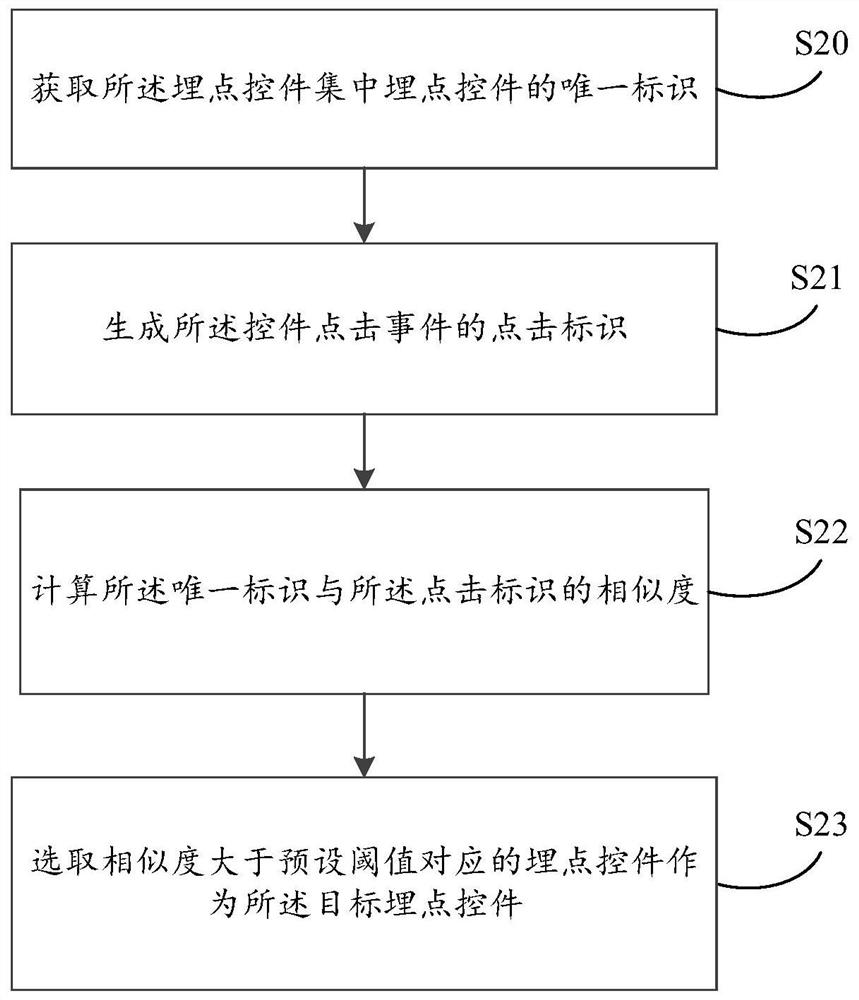
The invention relates to a big data technology, and discloses a buried point-based data acquisition method, which comprises the following steps of: detecting a control click event in a pre-constructed page, and selecting a buried point control matched with the control click event from a buried point control set of the pre-constructed page to obtain a target buried point control; obtaining a visual buried point category of the target buried point control, and generating a buried-point-free parameter configuration table according to the visual buried point category; and acquiring parameter data triggered by the control click event based on the buried-point-free parameter configuration table. The invention also relates to a blockchain technology. The target buried point control can be deployed in a blockchain node. According to the invention, type parameter configuration of data acquisition based on buried points can be realized, and flexibility of data acquisition based on buried points is supported.
Owner:PING AN SECURITIES CO LTD
Method for rapidly switching gigabit network cards in gigabit switching environment
ActiveCN102064964BImprove perceptionThe application process is convenient and agileData switching networksState variationNetwork link
The invention relates to a method for rapidly switching gigabit network cards in a gigabit switching environment. In the method, a timer used for polling a network card register is arranged in a gigabit network card equipment driver, detects a network link state change by polling contents of the network card register, and when a link state is changed from connection to breaking, sets a link statechange bit of a network card interruption register to trigger the interruption of the link state change in advance. The improved gigabit network card equipment driver in the method can detect a link breaking state only in less than 100 milliseconds. Therefore, the link breaking perceiving performance of the network card driver is greatly improved.
Owner:NAT UNIV OF DEFENSE TECH
Data management platform supporting high customization
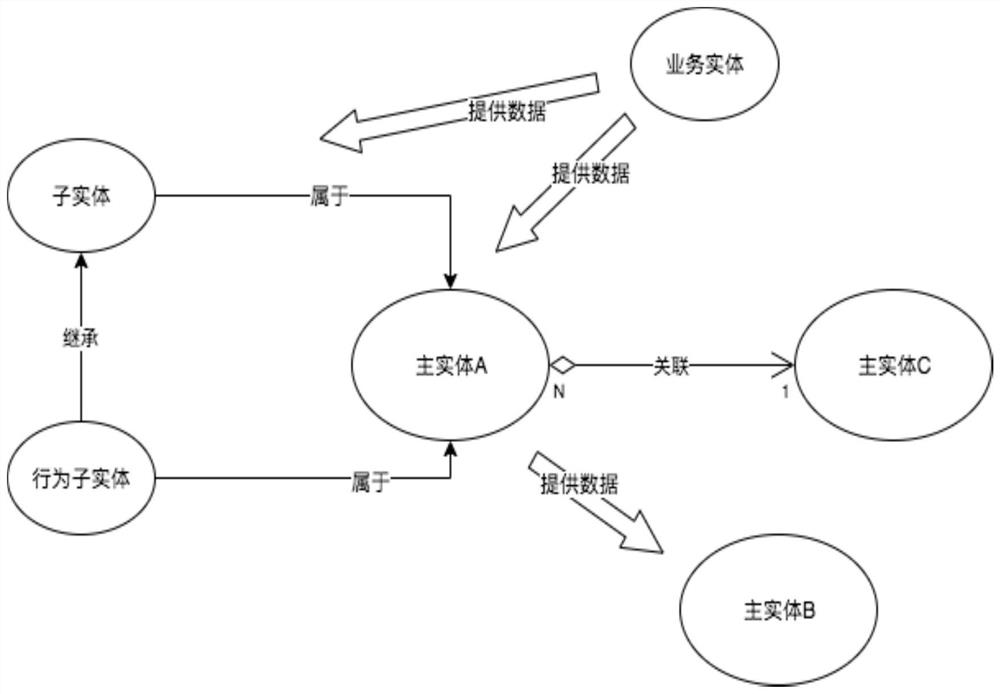
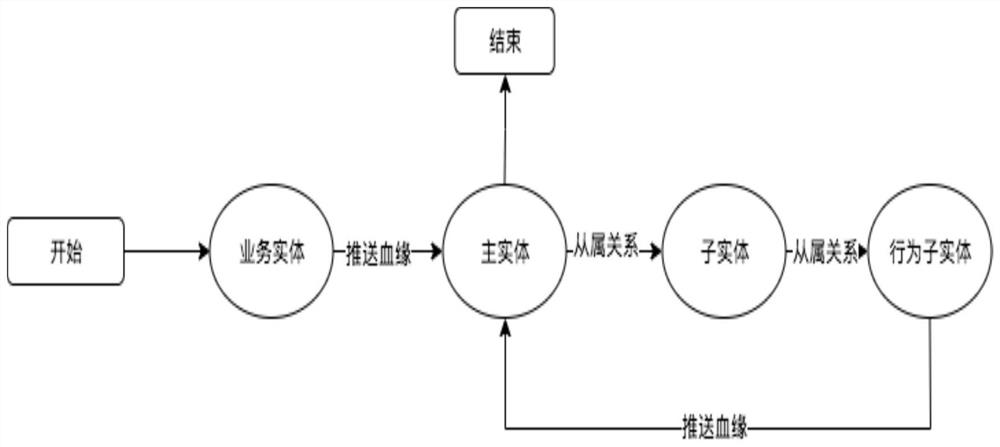
PendingCN112699107ASave moneyImprove data securityRelational databasesSpecial data processing applicationsData sourceEngineering
The invention relates to the technical field of customizing a plurality of main data management modules, data extraction and pushing, data conversion, data isolation and aggregation, data blood relationship and task scheduling, in particular to a data management platform supporting high customization, which comprises a main entity, a sub-entity, a behavior sub-entity and a service entity, wherein the main entity comprises a main entity A, a main entity B and a main entity C, the service entity provides data for the main entity A and the sub-entity respectively, an affiliated relationship is established between the main entity A and the sub-entity and between the main entity A and the behavior sub-entity respectively, and an associated relationship is established between the main entity A and the main entity C. According to the data management platform supporting high customization, through data isolated storage, the service requirements are met, the data security is improved, multiple modes of data source connection are expanded, and through data cleaning, the data quality is improved, so that the accuracy is improved, the enterprise expenditure is greatly saved, convenience and rapidness are achieved, and the human efficiency is improved.
Owner:北京优奥创思科技发展有限公司
Method and system for realizing broadband trunking service
ActiveCN103581839BSupport diversityReduce loadNetwork traffic/resource managementBroadcast service distributionService implementationTrunking
The invention discloses a broadband trunking service realizing method and a broadband trunking service realizing system. The method comprises the following steps: when the service type of an established trunked call service is transformed from a first type to a second type, a trunked scheduling subsystem modifies a T1 bearer of a trunked call service corresponding to a base station to which group member terminals belongs according to QoS parameters corresponding to the trunked call service of the second type, and notifies the base station to reestablish a downlink shared bearer for the group member terminals managed by the base station; and the trunked scheduling subsystem notifies the group member terminals that the service type of the trunked call service is changed after reestablishment of the downlink shared bearer is finished. With the broadband trunking service realizing method and the broadband trunking service realizing system, diversification and real-time transmission of broadband services can be realized.
Owner:SHENZHEN ZTE TRUNKING TECH CORP
A smart contract system based on decentralized dns root zone management
ActiveCN113067836BSupport diversityFlexible Audit PolicySecuring communicationCybersquattingDNS root zone
A smart contract system based on decentralized DNS root zone management, involving the field of Internet technology, to solve the problems of unclear governance subjects, name space splitting and malicious squatting brought about by the existing root zone management decentralization technology question. The technical points of the present invention include: the account book module abstracts all kinds of data existing in the root zone management into processes, agreements and resources; Flexible audit policies to support the diversity of root zone management. The present invention solves the problems of centralization, low transparency, and low degree of automation in traditional root zone management. The system can enable multiple participants in root zone management to access all root zone management data, and perform high-level automation in a highly automated manner. Participate in multi-party management of the root zone. The invention can be applied to the data management of the domain name system root zone in the Internet.
Owner:HARBIN INST OF TECH
Large scale computer node bootstrap paralleling update method and system
InactiveCN100524218CShorten update timeImprove update efficiencyMultiprogramming arrangementsData switching by path configurationComputer moduleClient-side
The invention discloses a large-scale computer node boot program parallel update method and system. The update client sends update commands and data in parallel to each node of the large-scale computer through a communication support module, and the node update service module on each node receives the update Update the bootloader of each node after the update command and data of the client. The update system includes a communication support module, an update client running on an ordinary microcomputer, and a node bootloader update module arranged on each node of a large-scale computer, and all node update service modules are connected to the update client through the communication support module, Respond to the update command of the client and finally realize the parallel update of the bootstrap of each node. The invention adopts a concurrent mode, has simple structure and convenient operation, and can effectively solve the problems of time-consuming and labor-intensive updating of boot programs in large-scale systems.
Owner:NAT UNIV OF DEFENSE TECH
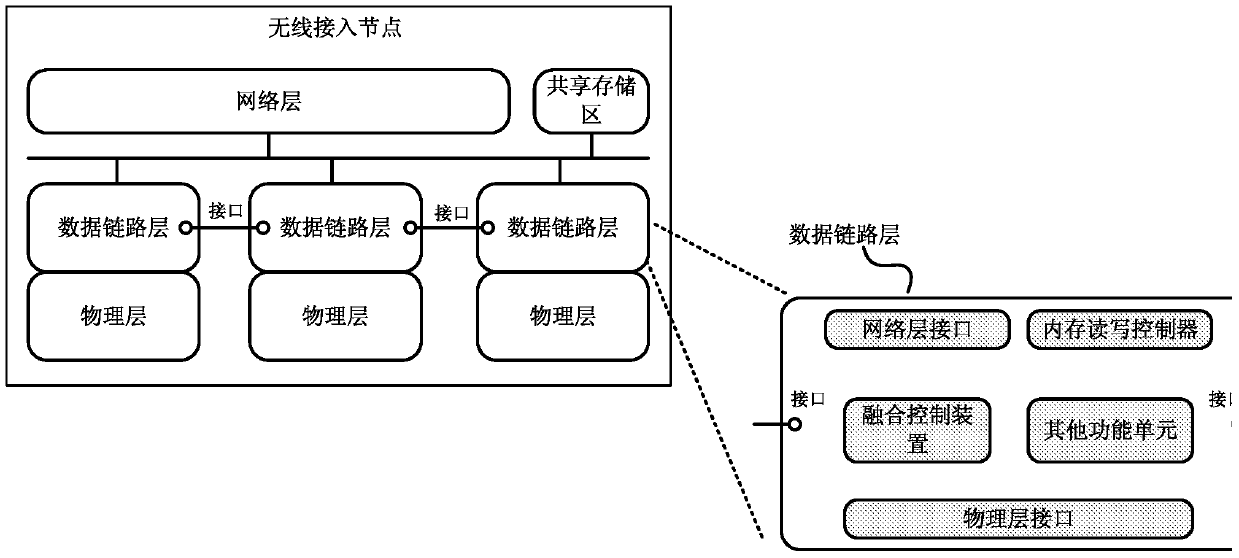
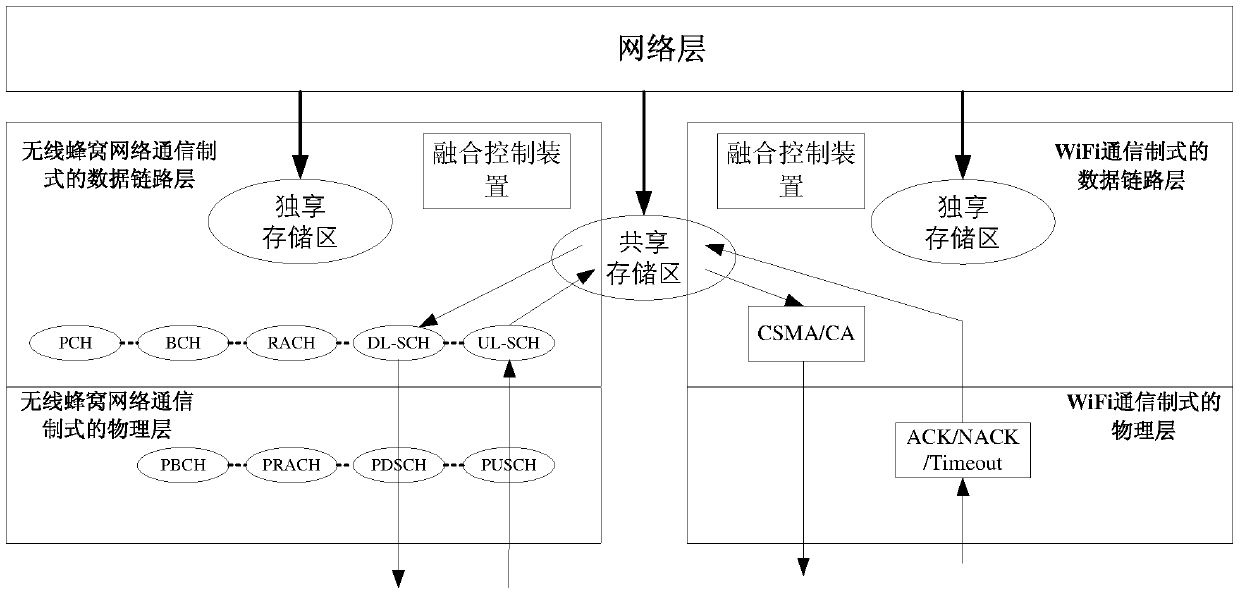
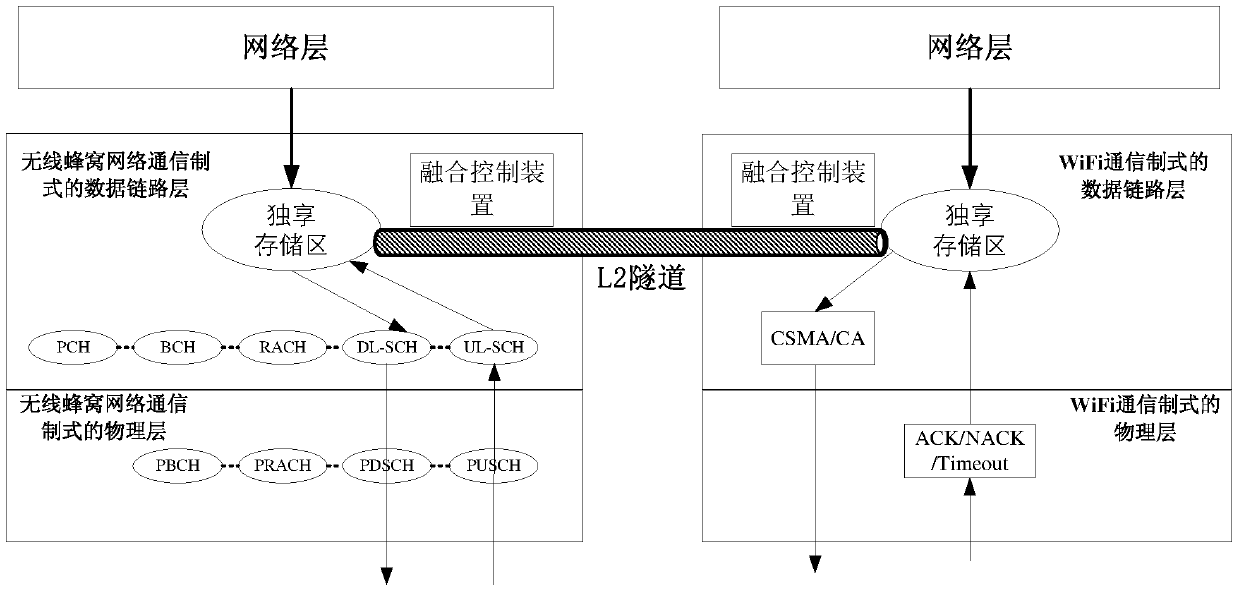
Network communication method and device
ActiveCN106576294BAvoid performance bottlenecksFast dynamic responseAssess restrictionNetwork topologiesService flowCommunications system
An embodiment of the present invention provides a network communication method, including: after receiving the indication message sent by the first fusion control device, the second fusion control device acquires a preset proportion of the service data that the first fusion control device needs to transmit business data; the second fusion control device performs parameter matching on the preset ratio of business data according to the system parameters of the current communication standard; the second fusion control device transmits the matched data through the corresponding data link layer The preset ratio of business data. The embodiment of the present invention also discloses a network communication device. By implementing the embodiment of the present invention, the temporary interruption of the service flow of the user terminal can be avoided, and the consistency of user experience can be ensured, so that the overall efficiency of the communication system is higher.
Owner:HUAWEI TECH CO LTD
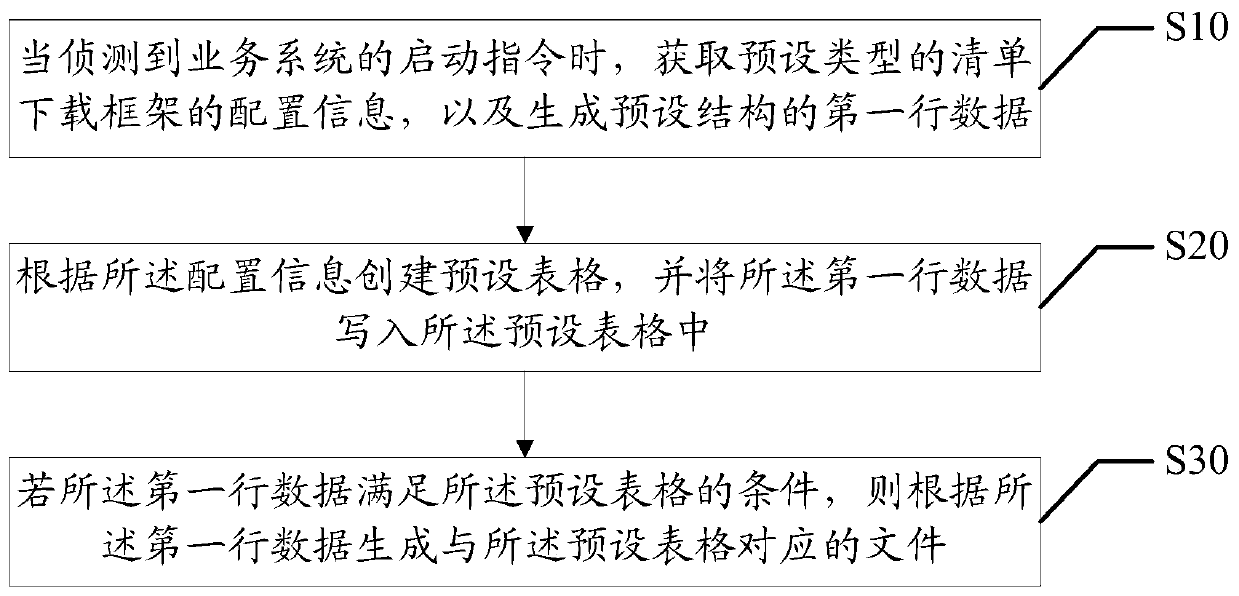
File generation method, device, and computer-readable storage medium
ActiveCN107688456BAchieve diversificationSupport diversitySoftware designSoftware engineeringDatabase
A method, device and equipment for generating a file and a computer readable storage medium, wherein the method comprises the steps of: when a starting instruction from a service system is detected, acquiring the configuration information for a list downloading frame of a predetermined type, and generating a first line of data having a predetermined structure (S10); creating a preset form according to the configuration information, and writing the first line of data into the preset form (S20); if the first line of data satisfies the criteria of the preset form, then a file corresponding to the preset form will be generated according to the first line of data (S30). The described method achieves the generation of corresponding files by means of the list downloading frame of a preset-type, wherein the files may support xls or xlsx formats, thus being able to support the diversification of generated files.
Owner:PING AN TECH (SHENZHEN) CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com