Tunnel selection method in optimization of visit between hosts under edge network double stack access
An edge network, host technology, applied in the Internet field
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
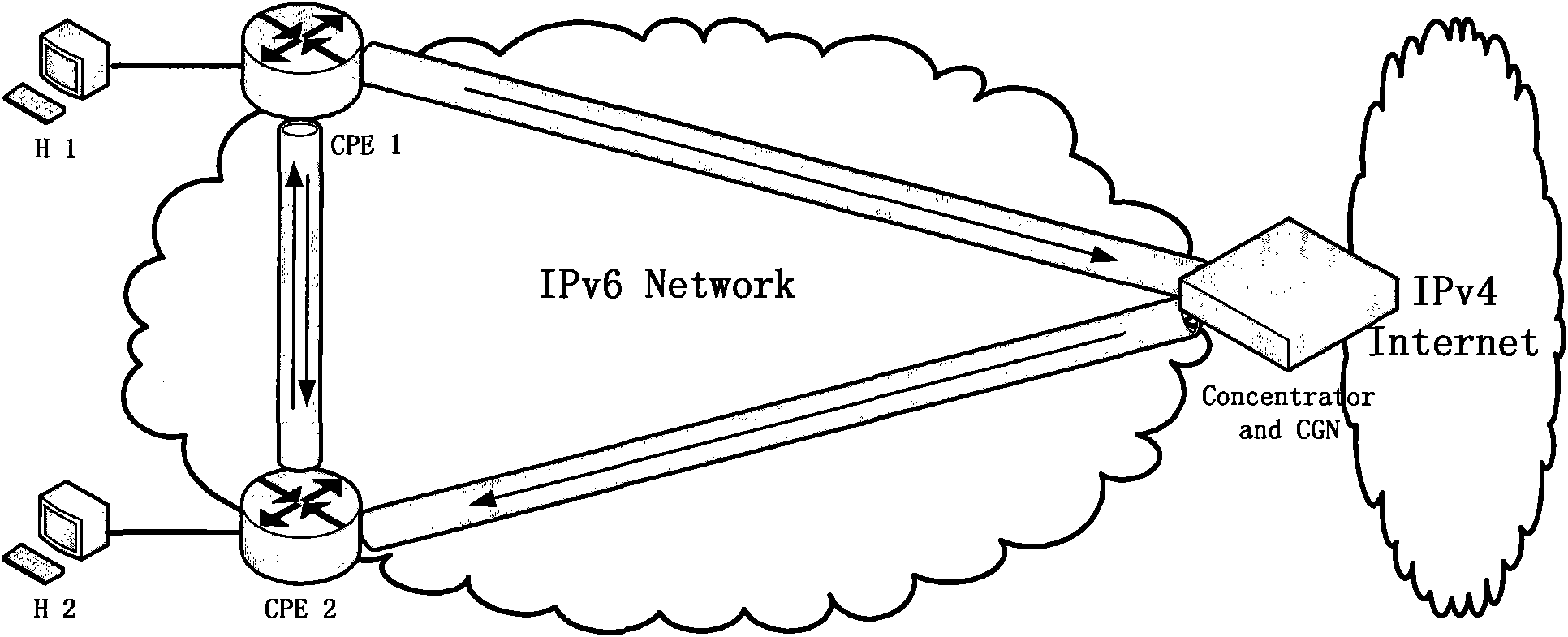
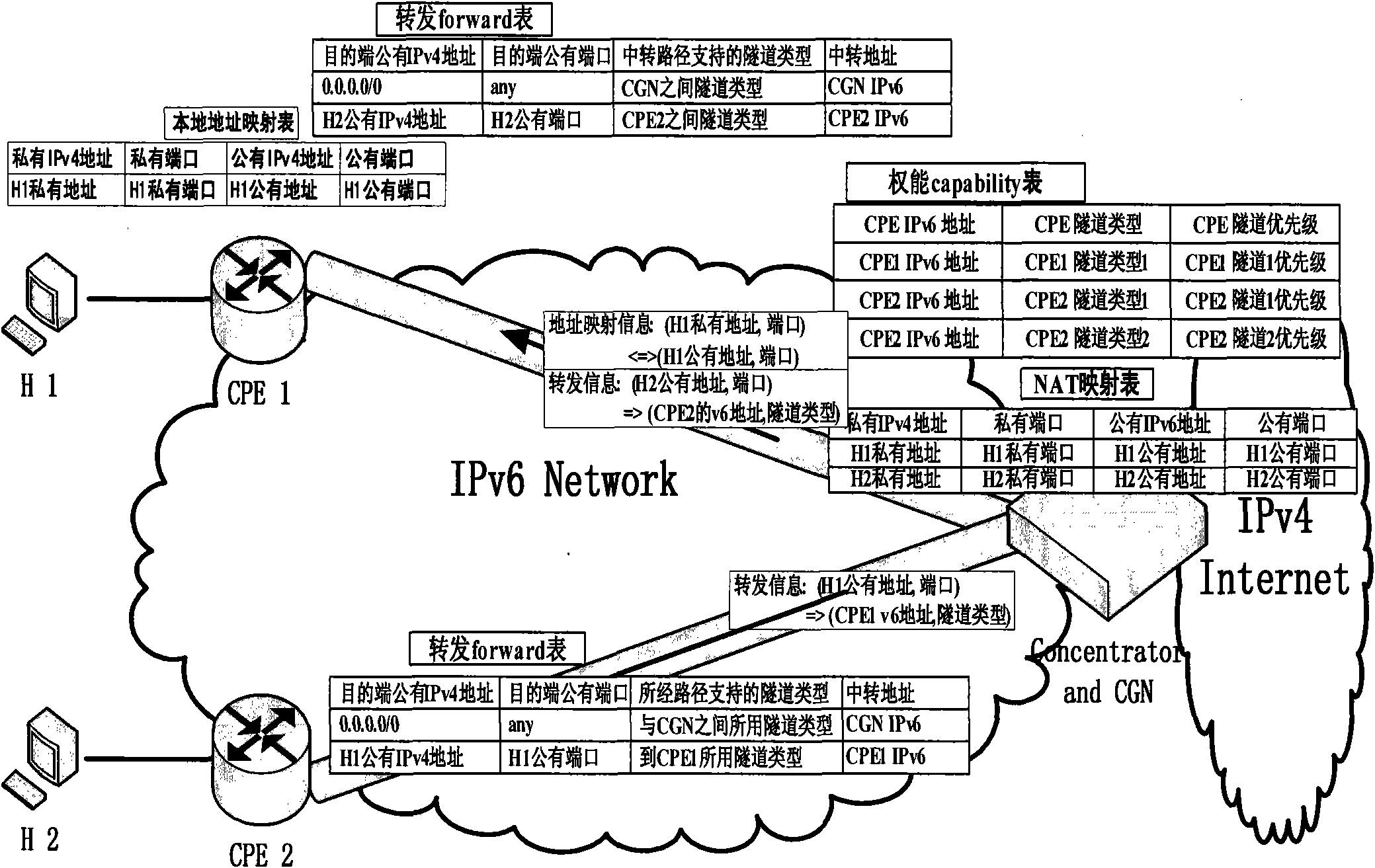
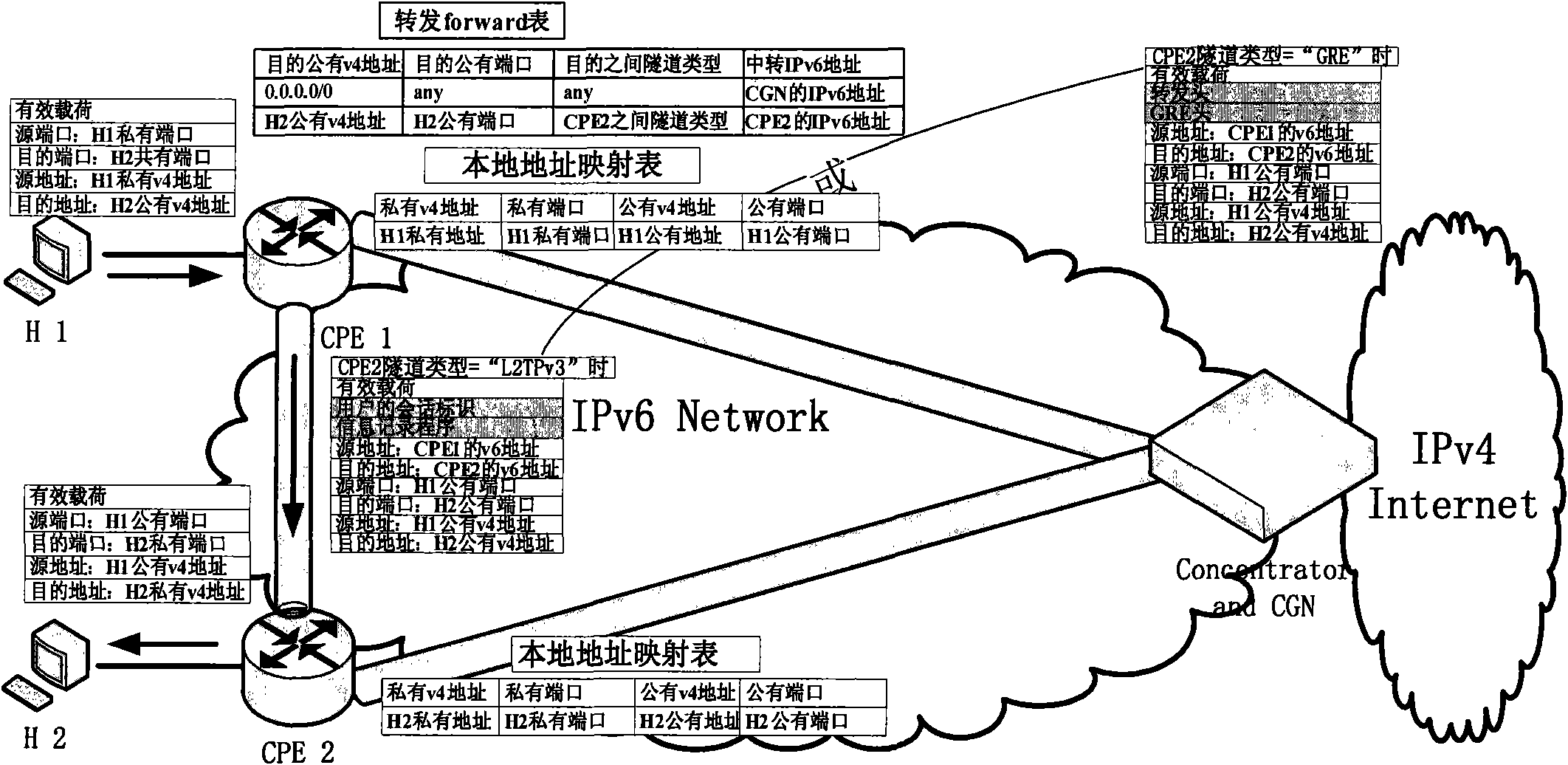
[0027] The CPE registers with the CGN, and the CGN obtains the tunnel information between CPE1 and CPE2, generates a capability table, and at the same time replies forward information to CPE1 to update the forward table; replies address allocation information to CPE to update the local address mapping table, such as Figure 5 . When the host H1 with the private IPv4 address of 192.168.1.2 sends data to the host H2 with the public IPv4 address of 166.111.8.56 (the address is allocated by DHCPv6 corresponding to the CGN), the data packet is encapsulated with destination and source address information and sent For CPE1 (IPv6 address: 1:0:0:0:0:0:0:1). CPE1 looks up the forward table (the non-shaded part, the shaded part is the information updated after the next step), encapsulates the data packet according to the forwarded forward table, and encapsulates the source and destination IPv6 addresses (CPE1 and CGN addresses) and ports, Then encapsulate the GRE header and send it to C...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com