Application program executing permission control method used for operating system
An application program and permission control technology, applied in the fields of instruments, electrical digital data processing, computer security devices, etc., can solve problems such as hidden dangers, system performance impact, and inability to effectively protect system security, and achieve comprehensive control and prevention capabilities. Strong, prevent the effect of illegal program running
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
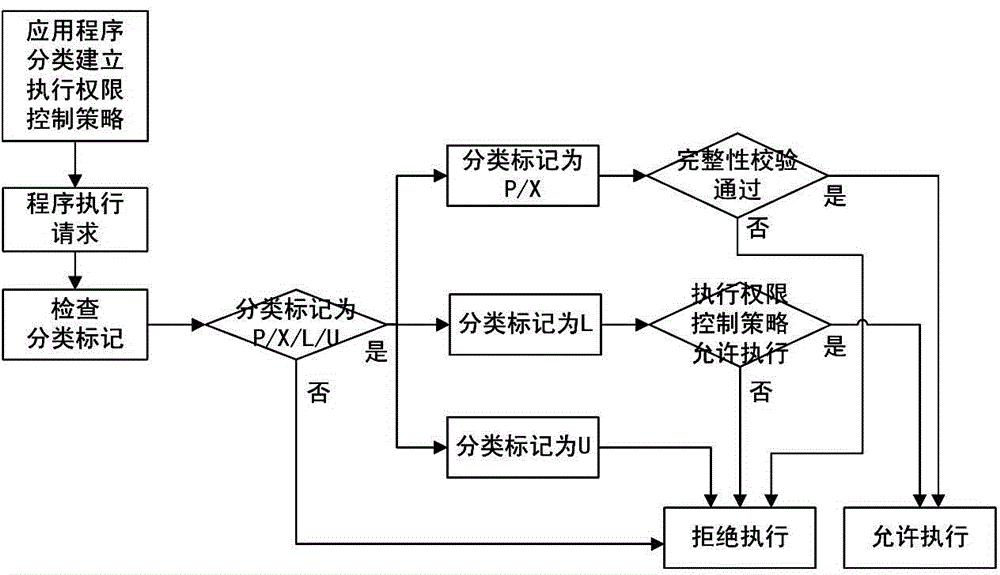
[0035] Such as figure 1 As shown, the implementation steps of the application execution authority control method for the operating system in this embodiment are as follows:
[0036]1) Classify the application programs in the operating system into four categories: allowing all users to execute P, protected and tamper-proof X, allowing or denying some users to execute L, and denying all users to execute U, and store them as classification marks of application programs; at the same time, For the applications in the operating system, the execution authority control policy of the application is established according to the inherent information of the application. The execution authority control policy is configured to require administrator authority to operate when adding and modifying. A record includes the inherent information for the specified and the information that the specified user allows or prohibits the execution of the application;
[0037] 2) Intercept the application ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com