Method and system for detecting web page vulnerabilities
A vulnerability detection and webpage technology, which is applied in the field of network security, can solve the problems of high false negative rate, high maintenance cost, and excessive occupancy, and achieve the effects of low false positive rate, low maintenance cost, and strong preventiveness
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
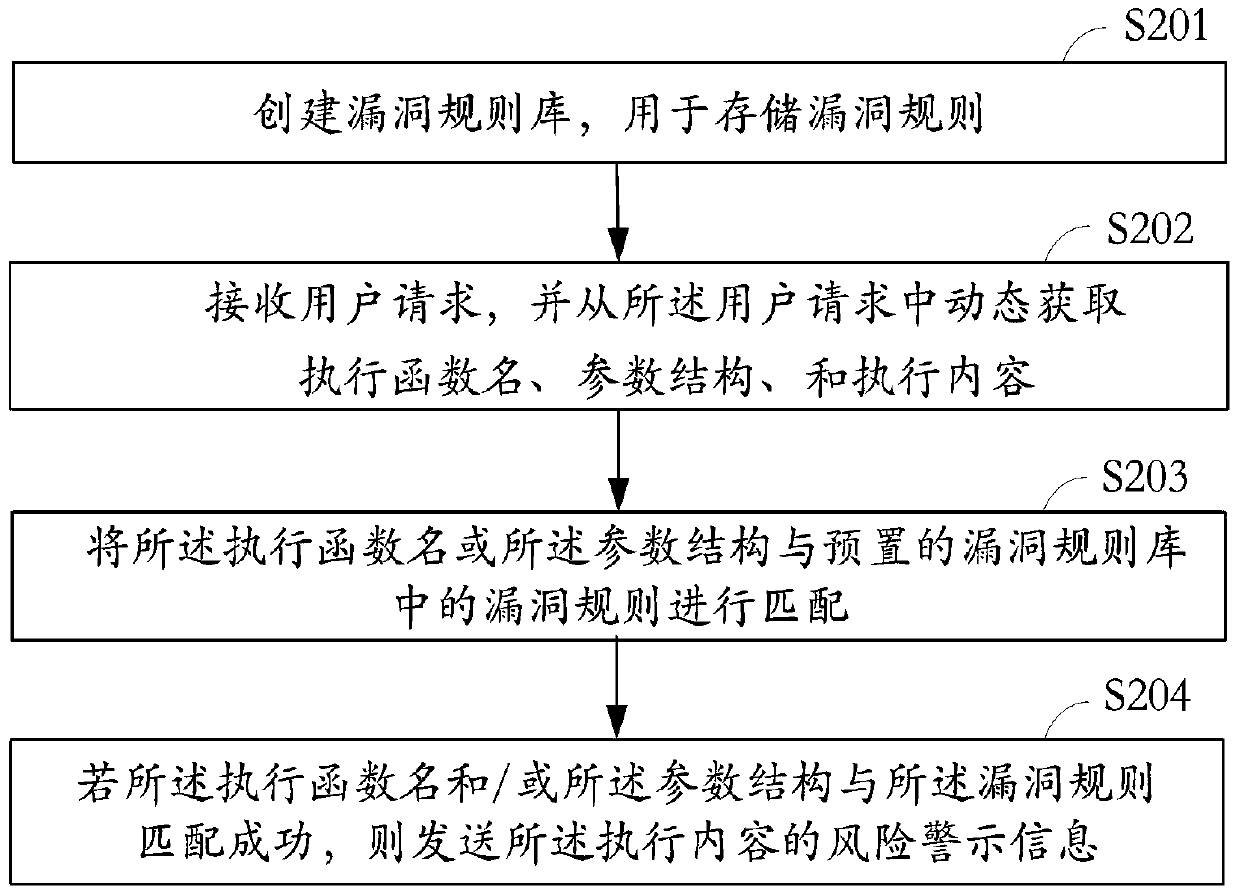
[0046] see figure 2 , which is a schematic flow chart of the method for detecting webpage vulnerabilities in the present invention. The method for detecting webpage vulnerabilities includes:
[0047] In step S201, a vulnerability rule library is created for storing vulnerability rules, wherein the vulnerability rules include vulnerability function names, execution function names and one or more corresponding vulnerability parameter structures.
[0048] Vulnerabilities in the vulnerability rules include, according to common types: structured query language (SQL) injection vulnerabilities, auto-completion vulnerabilities, directory traversal vulnerabilities, hidden field manipulation vulnerabilities, buffer overflow vulnerabilities, cross-site scripting vulnerabilities, and denial of One or more combinations of service attack vulnerabilities.
[0049] The creation method of the vulnerability rule base specifically includes: (1) analyzing the above-mentioned known vulnerabilit...
Embodiment 2
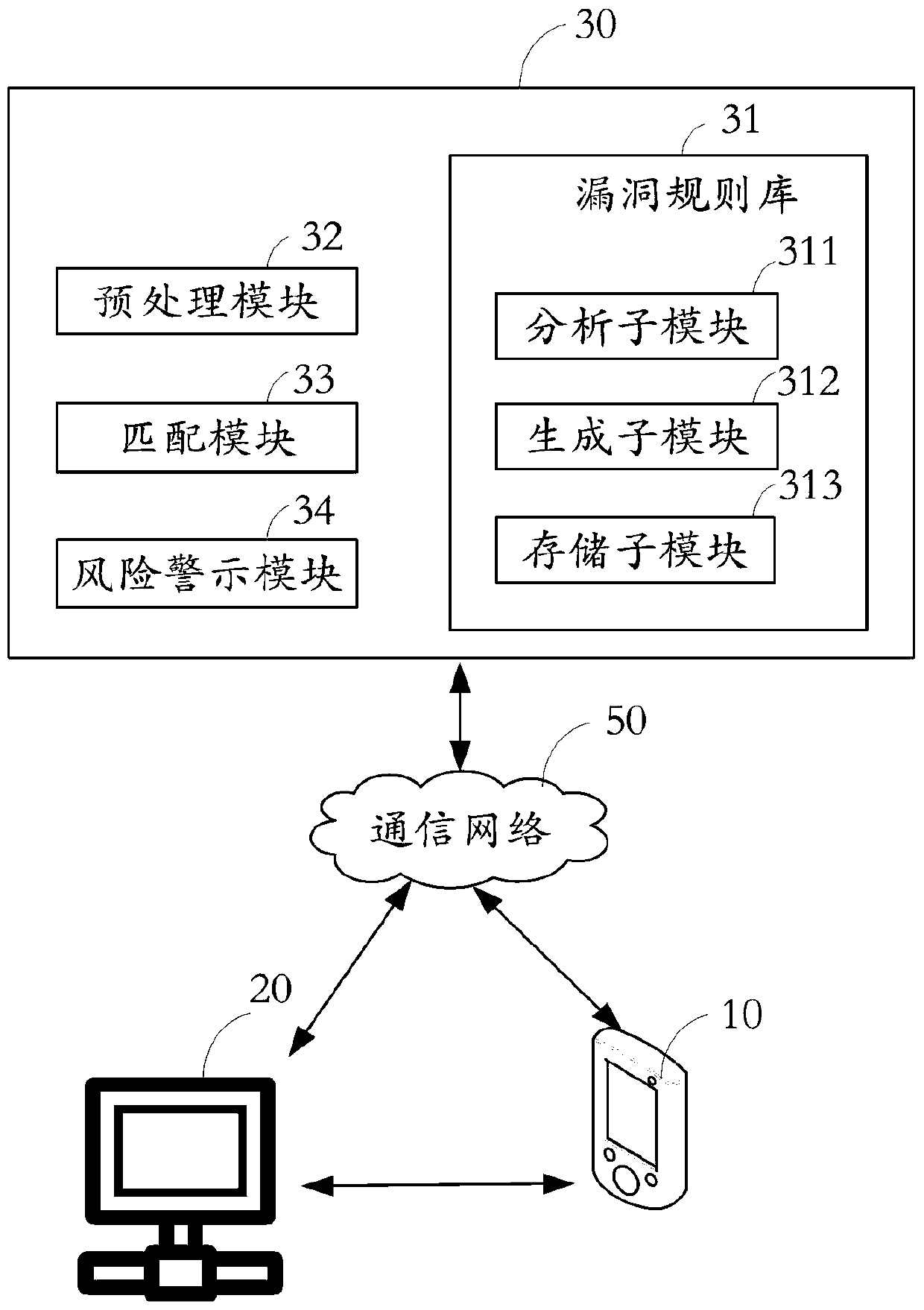
[0067] see image 3 , which is a block diagram of the system for detecting web page loopholes of the present invention.
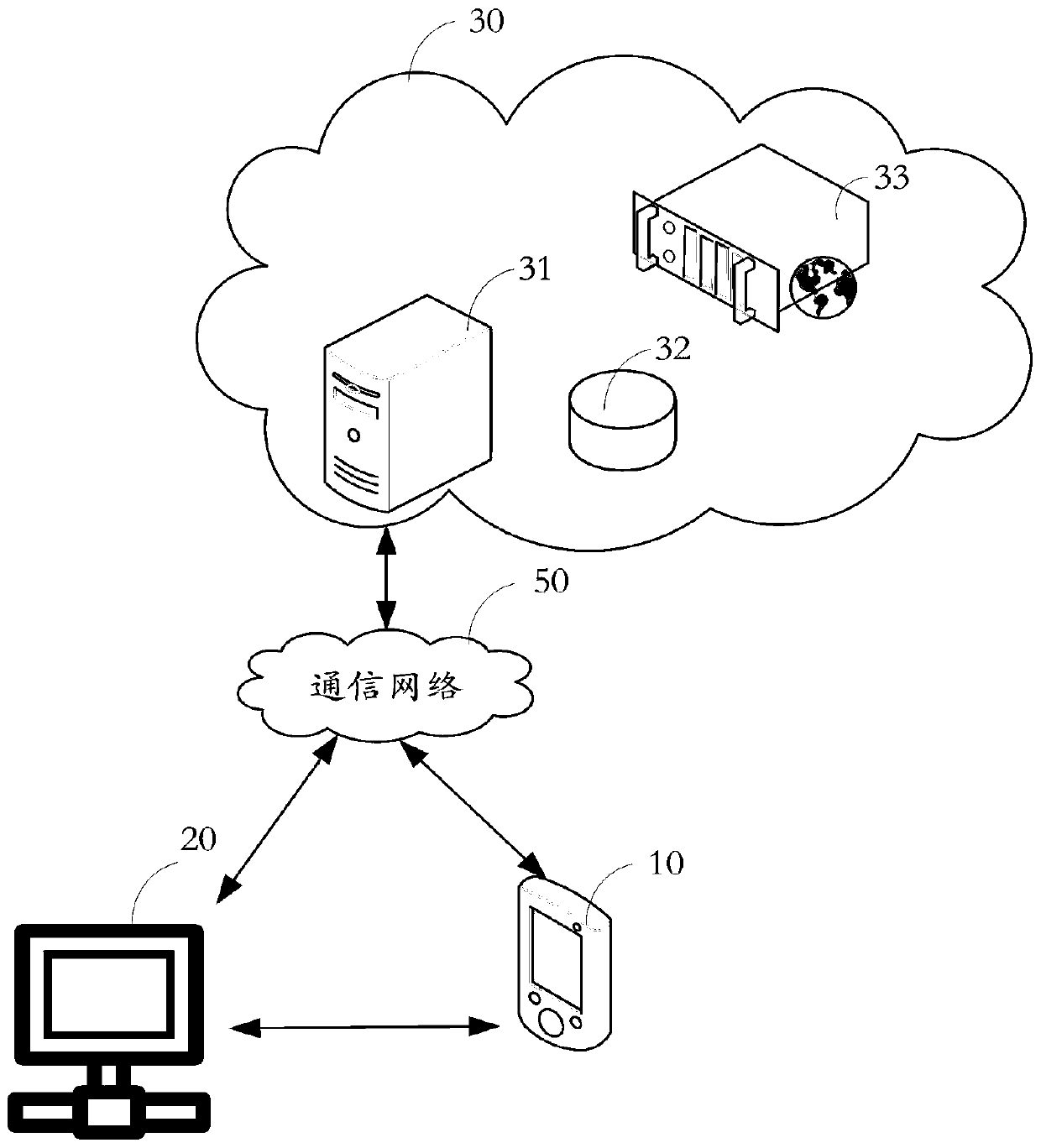
[0068] A webpage vulnerability detection system is applied to a server 30. It can be understood that: the server 30 may be a server host, or a cloud server platform.
[0069] The webpage loophole detection system is used to receive user requests, analyze whether there are webpage loopholes, and send risk warning information accordingly. The web page vulnerability detection system at least includes: a vulnerability rule base 31 , a preprocessing module 32 , a matching module 33 , and a risk warning module 34 .
[0070] Vulnerability rule library 31 is used to store the vulnerability rules, wherein the vulnerability rules include the name of the vulnerability function, the name of each execution function and one or more corresponding vulnerability parameter structures.
[0071] Vulnerabilities in the vulnerability rules include, according to common types: ...
Embodiment 3
[0092] see Figure 4 , which is a schematic diagram of the defense framework of the webpage vulnerability detection system of the present invention. From the perspective of defense architecture, the webpage vulnerability detection system is explained.
[0093] A webpage vulnerability detection system includes a vulnerability analysis part 41 and a data support part 42.
[0094] It can be understood that: the vulnerability analysis part 41 is generally located at figure 1 on the analysis server 31, and the vulnerability rule generation part can be located on the analysis server 31, also can be located at figure 1 The data is supported on the server 33.
[0095] The vulnerability analysis part 41 is used to receive user requests, analyze whether there are webpage vulnerabilities, and send risk warning information accordingly. Specifically, the vulnerability analysis part includes: a preprocessing module 411 , a matching module 412 , a risk warning module 413 , and a preset v...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com