Progress authentication method based on password
A technology of password authentication and authentication method, which is applied in digital data authentication, instruments, electrical digital data processing, etc., and can solve the problem of high risk of system process execution and tampering, system process is easy to be controlled and tampered by viruses/trojan horses, etc., and system security Low performance and other issues, to reduce the risk of process execution and tampering, good versatility, and strong scalability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
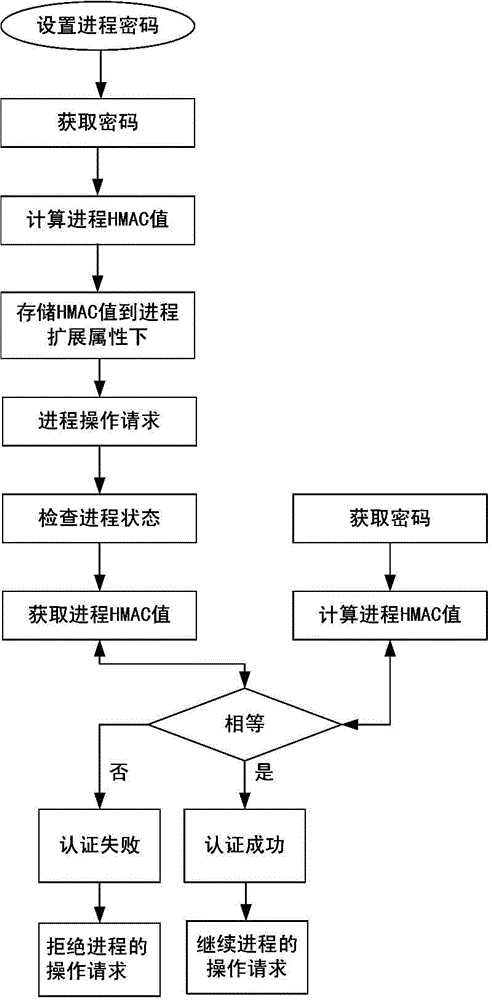
[0028] Such as figure 1 As shown, the implementation steps of the password-based process authentication method in this embodiment are as follows:
[0029] 1) Set the authentication password for the process, calculate the HMAC value of the process according to the authentication password and store it in the extended attribute of the process; set the password acquisition control switch in the operating system in advance, and configure it according to the startup parameters of the operating system or the settings of privileged users The password obtains the status of the control switch; after receiving the operation request of the process, jump to the next step;
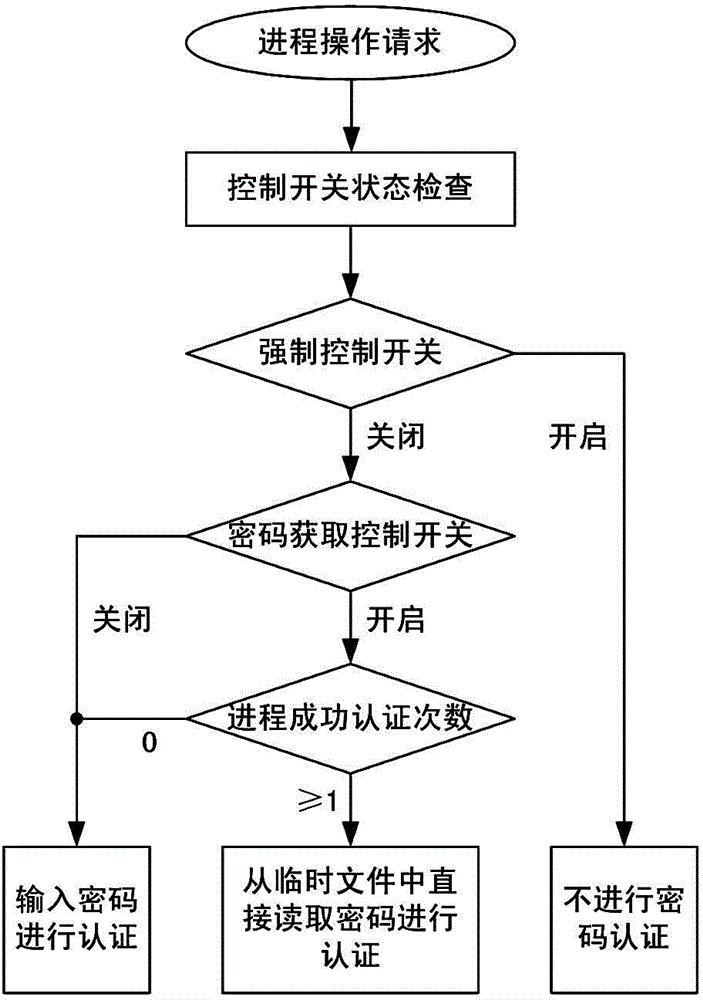
[0030] 2) Determine whether password verification is required according to the password acquisition control switch. When password verification is required, the authentication password is obtained, and the HMAC value of the process is calculated based on the authentication password. The calculated HMAC value and the HMAC...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com