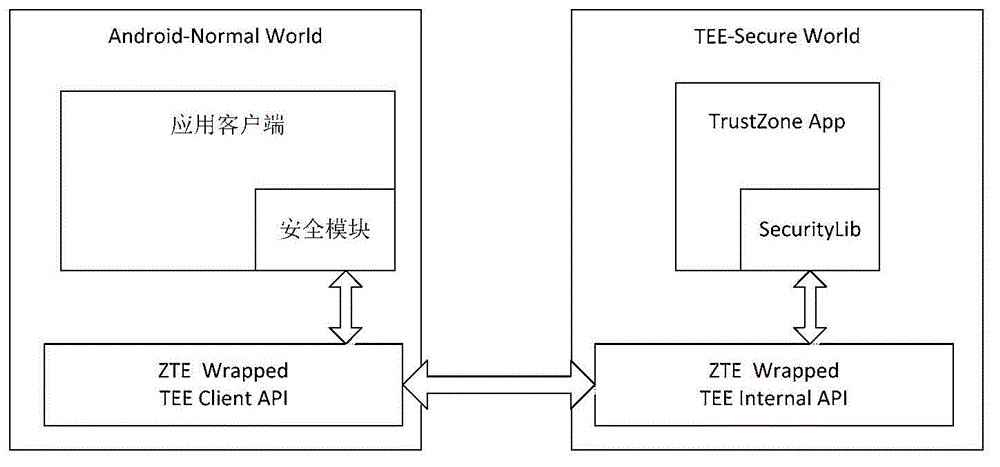
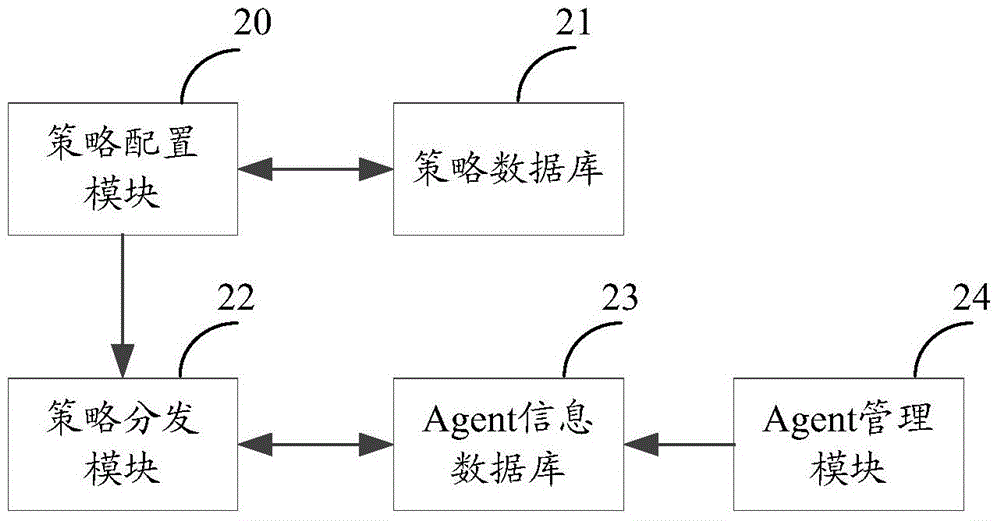
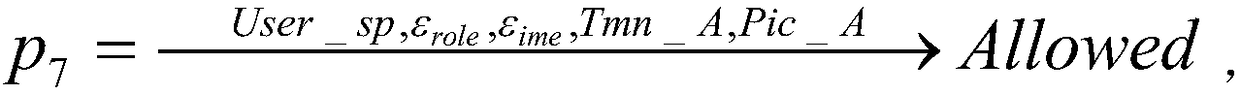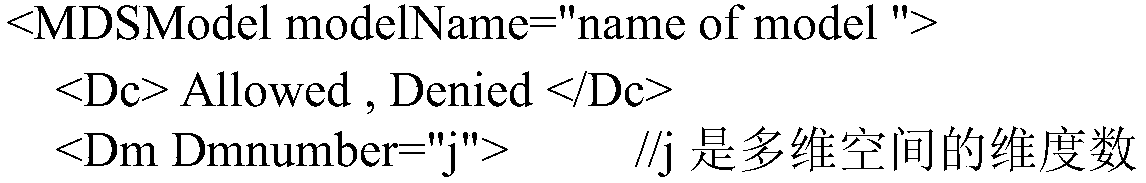Patents
Literature
68results about How to "Flexible Access Control" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Multistage authority management method for cloud storage enciphered data sharing
ActiveCN103107992AReduce complexityEasy to implementTransmissionAttribute-based encryptionCiphertext
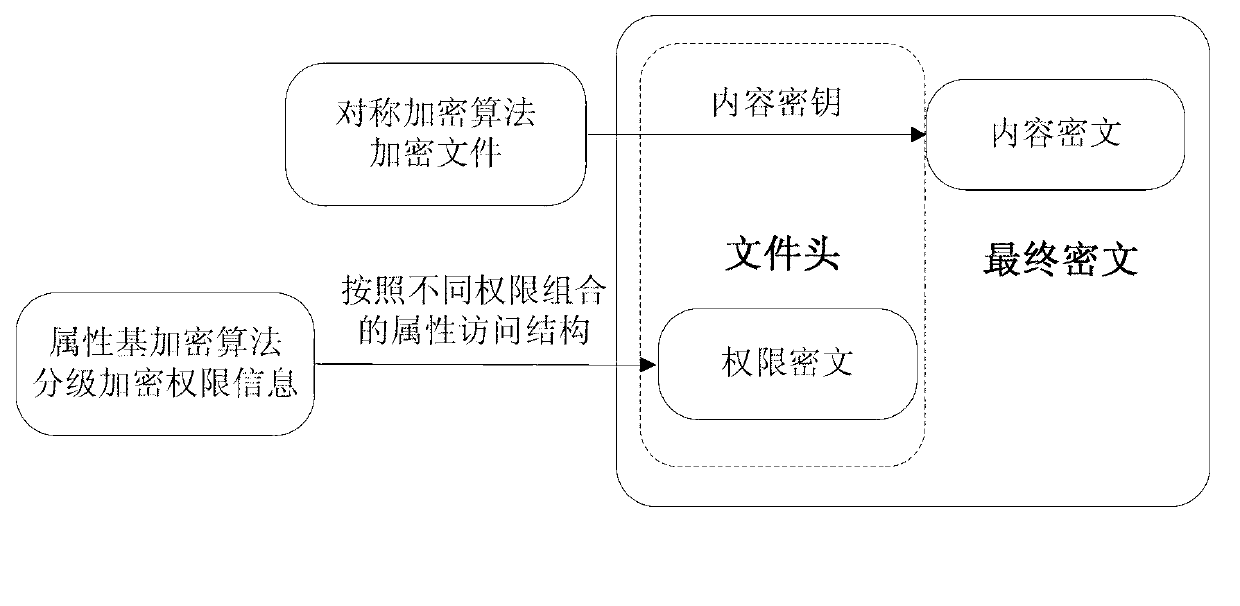
The invention relates to a multistage authority management method for cloud storage enciphered data sharing. The methods such as attribute based encryption, access control and authority management are used for providing a reliable method for access and multistage authority management of a shared cipher text in the cloud storage environment. Through mixing encrypt system, the multistage authority management method for cloud storage enciphered data sharing comprises steps: firstly applying a symmetric encryption algorithm to encrypt data, and generating a content cipher text; then adopting the attribute based encryption to encrypt according to different authority information, and generating an authority cipher text; adopting the attribute based encryption scheme to encrypt a symmetric key and the authority cipher text, regarding the symmetric key and the authority cipher text as a file header of the content cipher text, and generating a final cipher text. The multistage authority management method for cloud storage enciphered data sharing has the advantages of being convenient to achieve, strong in user information protectiveness, fine in authority control grit and the like. Under the premise that a server is not credible, the flexible and extensible authority management to the shared enciphered data is supported, the privacy and the security of the user data and authority information are effectively ensured, and the multistage authority management method for cloud storage enciphered data sharing has good practical value and wide application prospect in the cloud storage field.
Owner:HANGZHOU YUANTIAO TECH CO LTD
Scalable method for access control
InactiveUS20080012685A1Efficiently utilizedFlexible access controlElectric signal transmission systemsMultiple keys/algorithms usageMedia access controlAuthorization
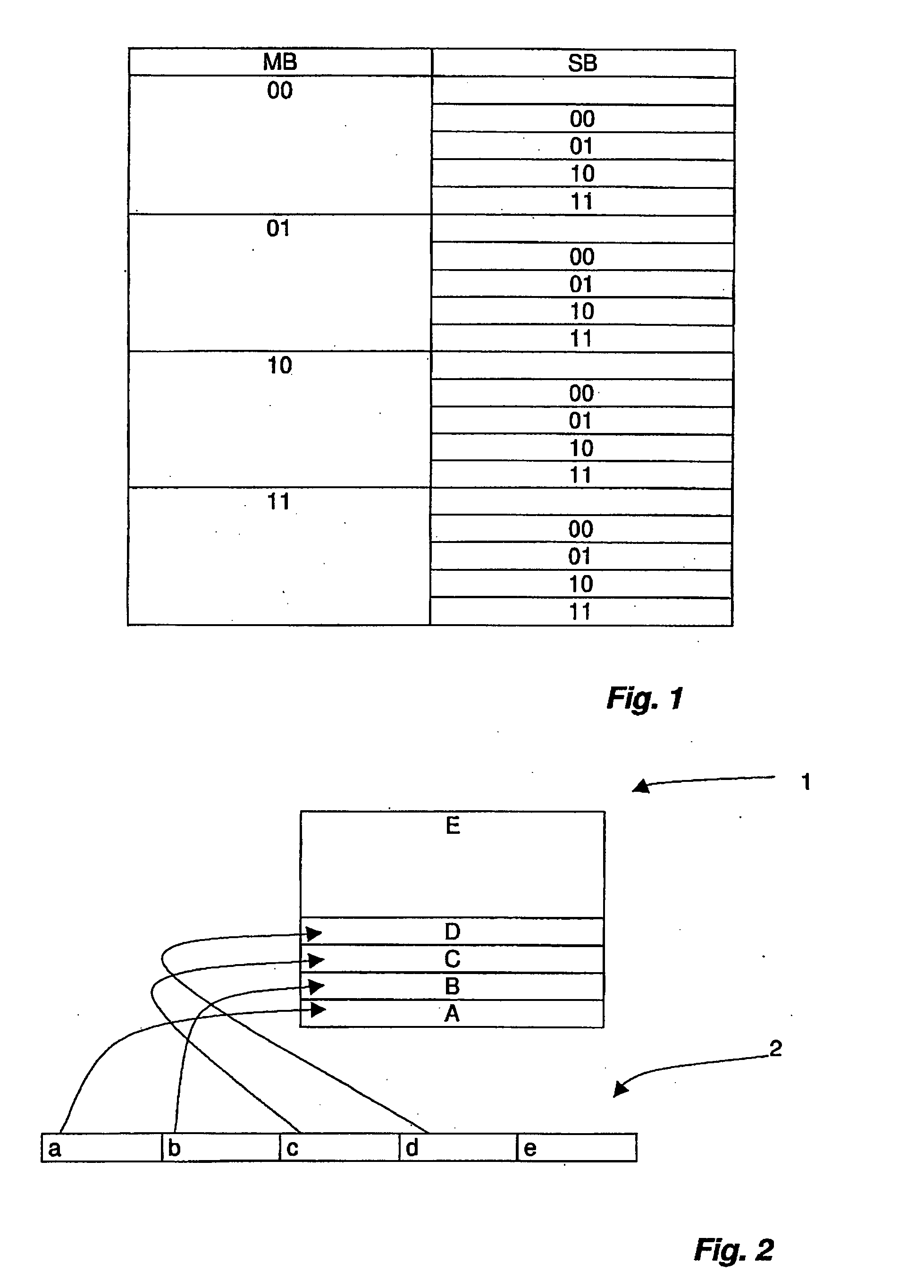
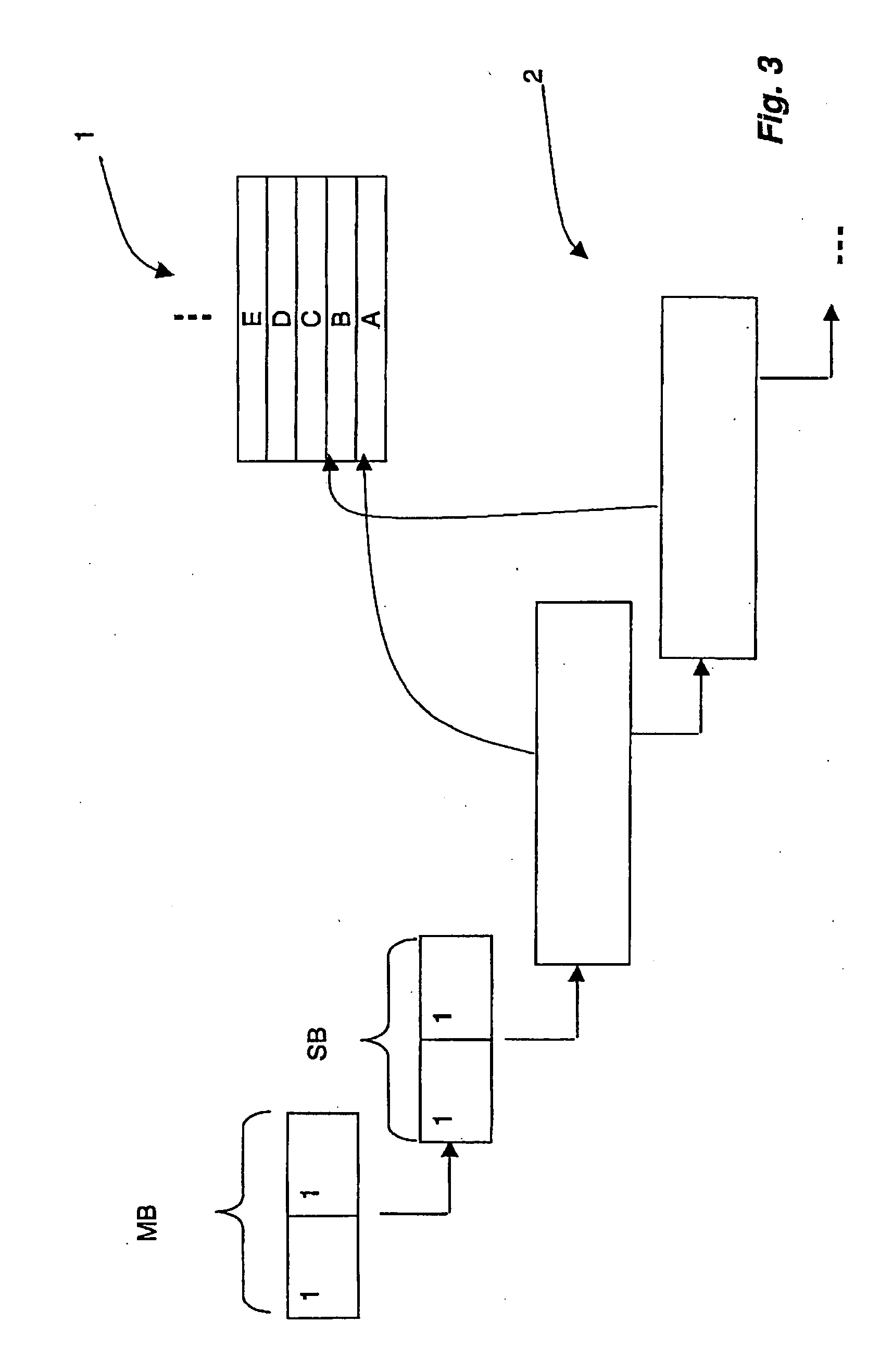
A method for specifying access authorization to at least one memory area of a transponder is provided, in which the memory area is assigned access control information, whereby the access control information comprises at least one configurable master access control information, and write access to the memory area is released at least by a first configuration of the master access control information and write access to the memory area is blocked by a second configuration of the master access control information, whereby in the method the access control information is stored further in the transponder, the access control information is assigned at least one first settable sub-access control information, and the information is scaled by the assignment of the first sub-access control information to the master access control information, so that access authorization specified by the configuration of the master access control information is adapted to at least one additional requirement. The invention relates further to scalable transponders and an RFID system comprising a scalable transponder.
Owner:ATMEL CORP
Control method for accessing computer system and I/0 ports
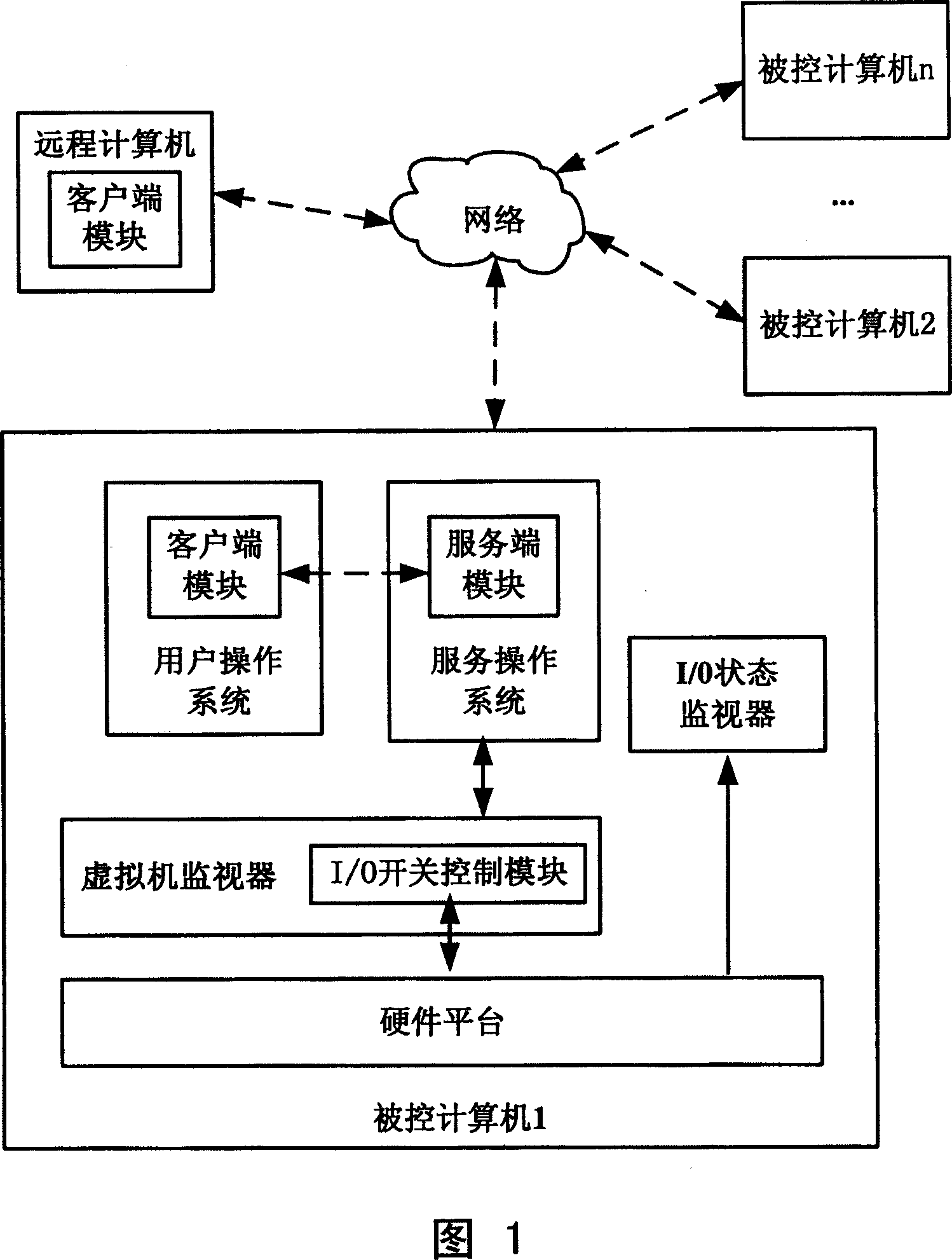
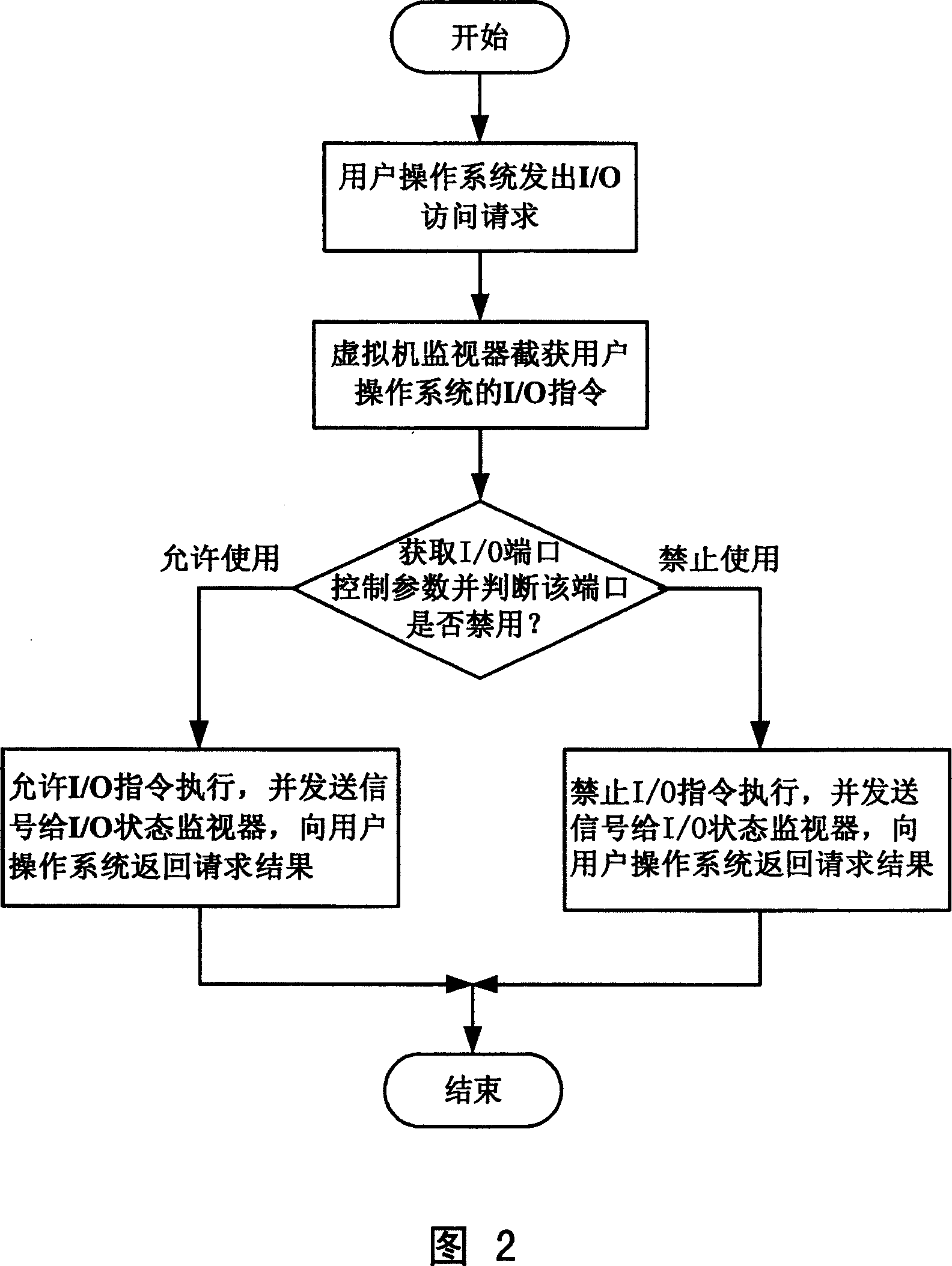
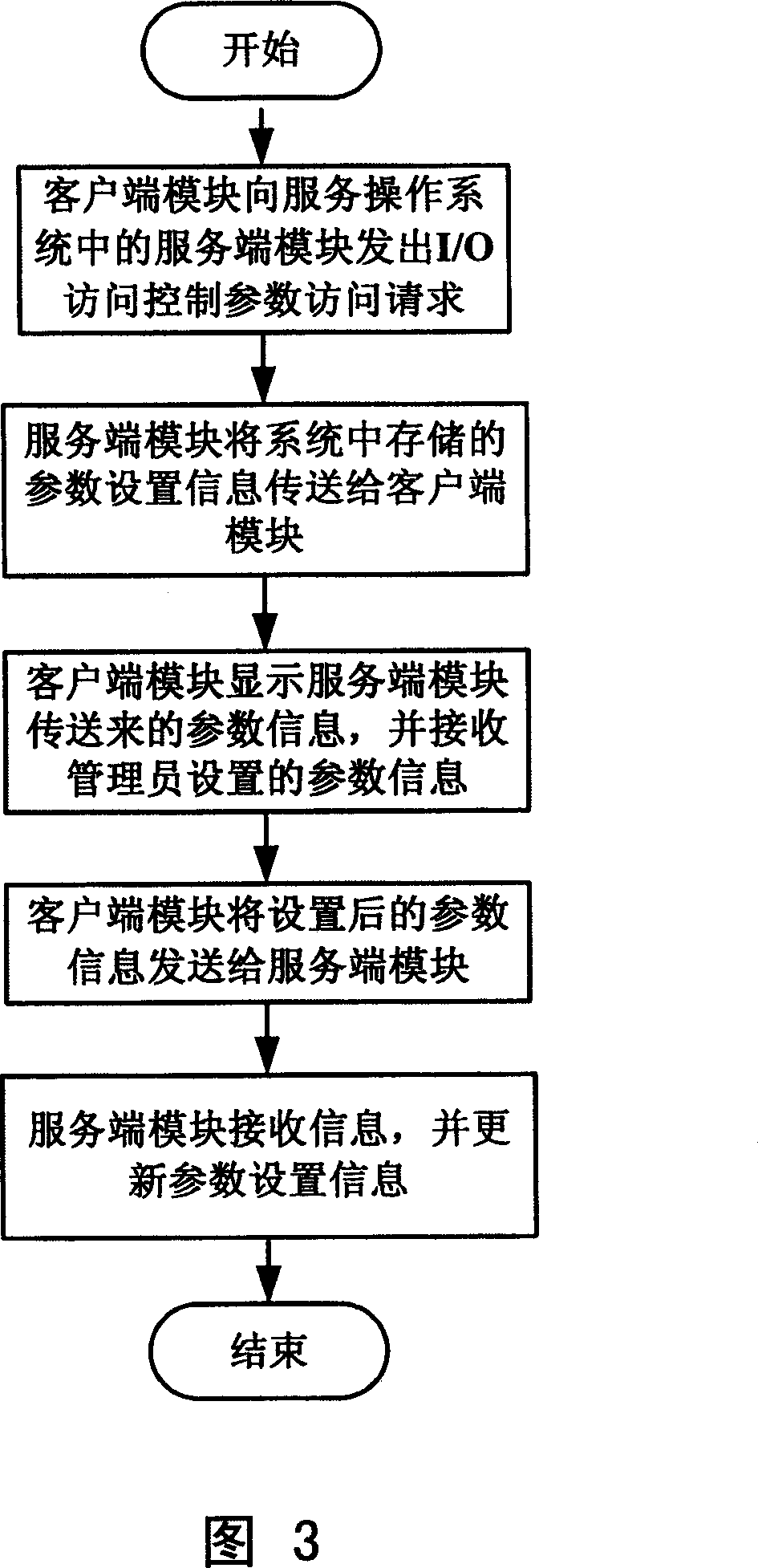
ActiveCN101004767AFlexible Access ControlRemove access control features yourselfHardware monitoringInternal/peripheral component protectionExecution controlControl parameters
A computer system enabling to control access of its I / O port comprises user operation unit with client end module for carrying out interaction with service end module and for receiving inputted I / O port access control parameters, service operation unit with service end module for carrying out interaction with client end module and for executing said control parameters, virtualizer monitor with I / O switch control module for deciding whether I / O command from user operation unit is to be executed or not according to said control parameters and I / O state monitor for displaying state of I / O port.
Owner:LENOVO (BEIJING) CO LTD
Method and device for controlling permission
InactiveCN102339367ASimple access controlFlexible Access ControlDigital data authenticationFull PermissionOperating system
Owner:ZTE CORP
Method for implementing distributed security policy, client terminal and communication system thereof
ActiveCN101431516AReduce the burden onImplement distributed processingNetwork connectionsCommunications systemClient-side
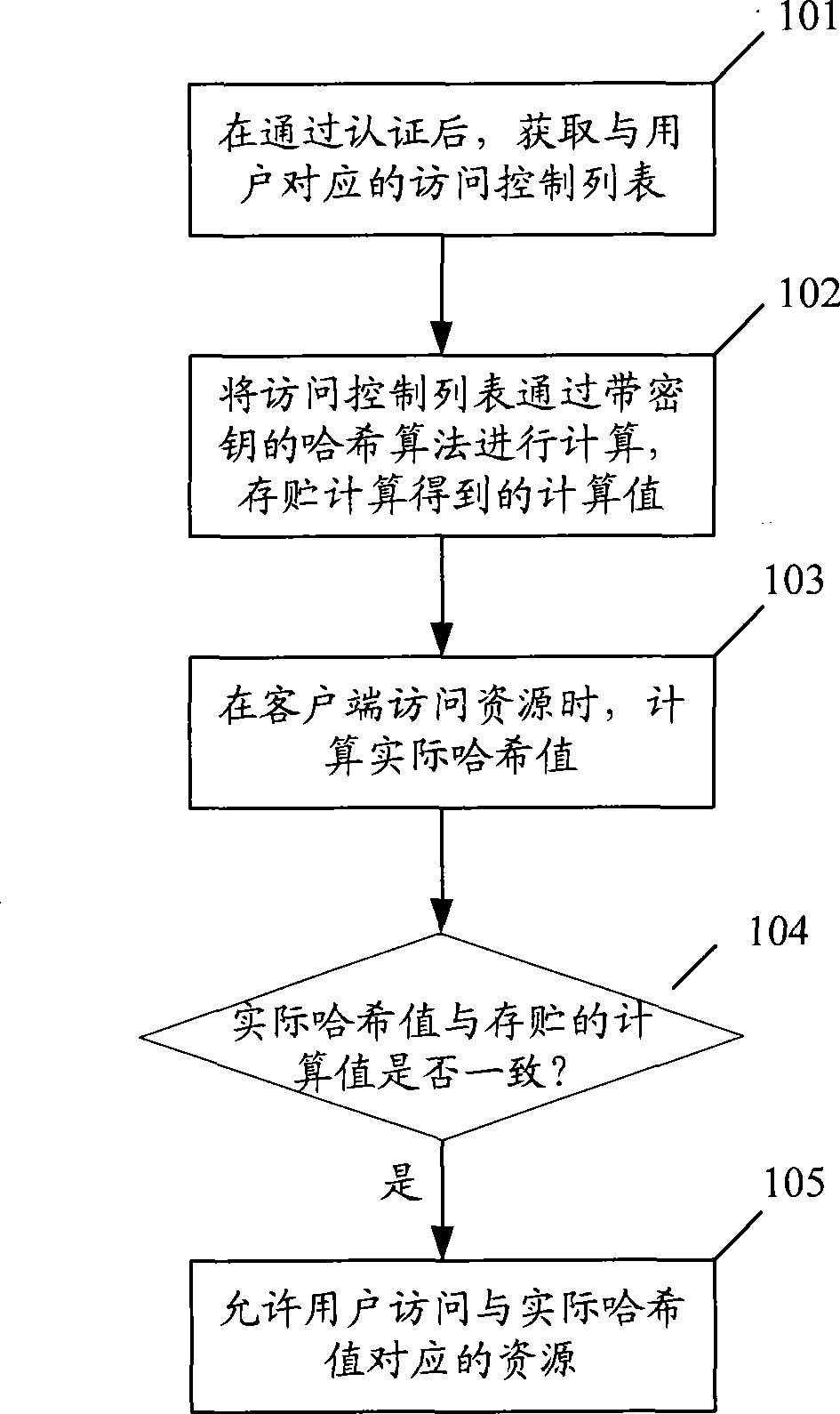
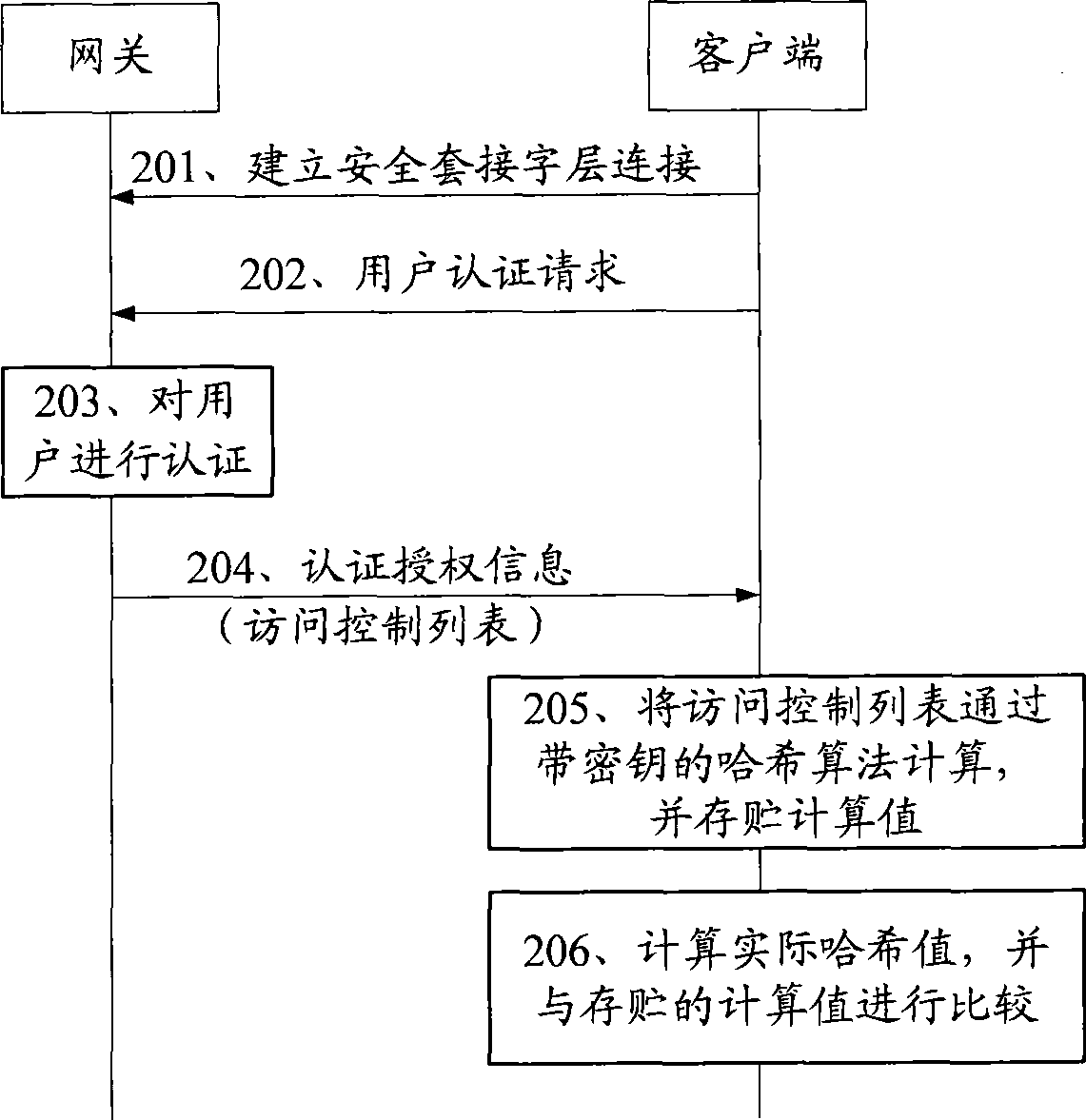
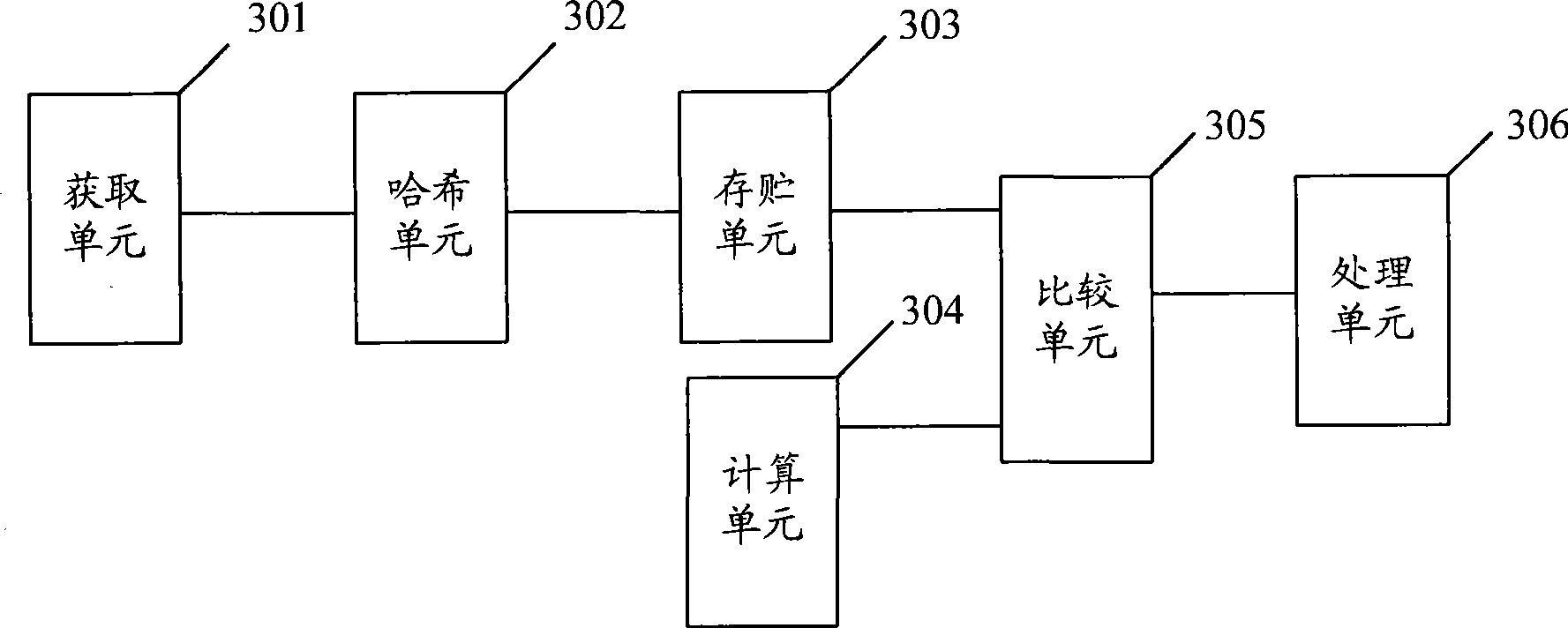
The embodiment of the invention discloses a distributed type safe strategy implementing method, client and communication system. The method comprises: acquiring access control list corresponding to user after authentication; calculating access control list by hash algorithm possessing key, storing the calculated value; calculating actual hash value when client accesses to resource; comparing actual hash value and stored calculated value; when actual hash value is identical with stored calculated value, allowing user access to resource corresponding to actual hash value. The invention implements distributive type processing for access control, relieves load of gateway, enciphers the access control list, thereby guaranteeing safety of access control and agility.
Owner:CHENGDU HUAWEI TECH
Nand Flash memory array based storage control apparatus
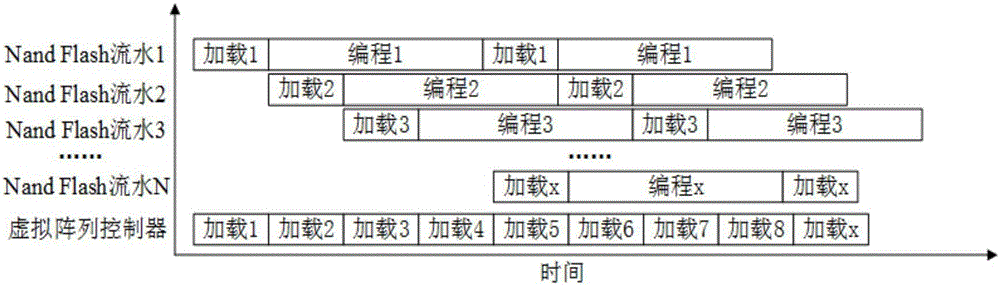
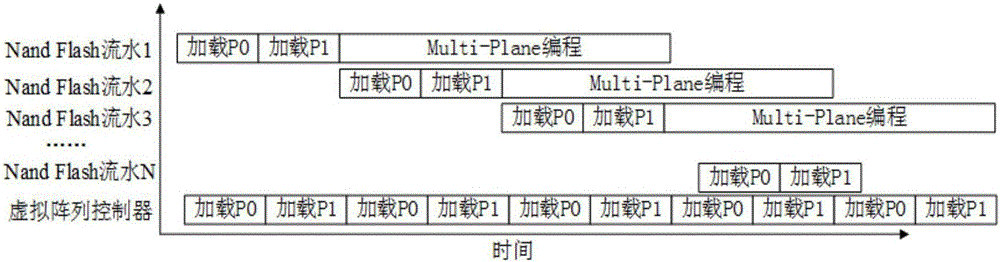
ActiveCN105931670AFlexible Access ControlSolve operational problemsRead-only memoriesRegister allocationData stream
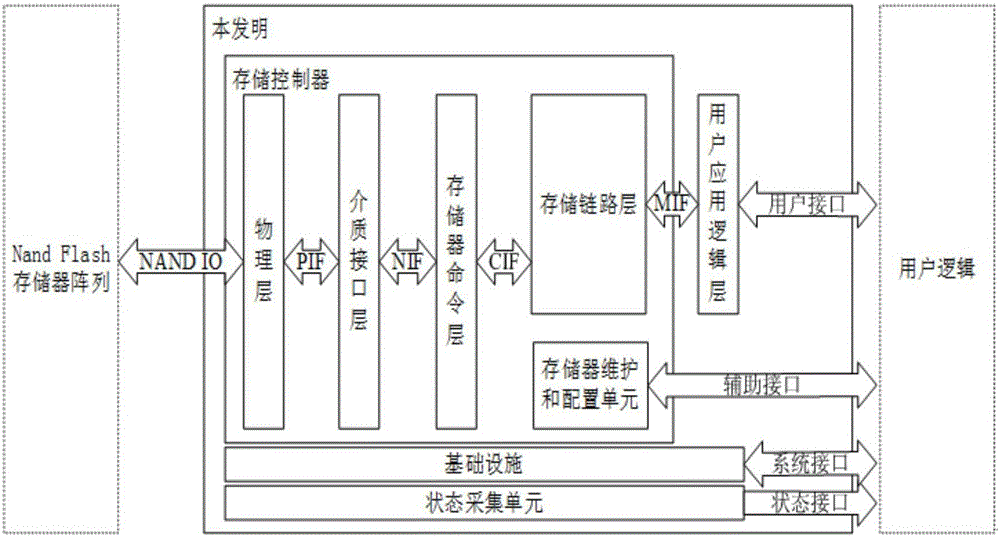
The present invention discloses a Nand Flash memory array based storage control apparatus. The Nand Flash memory array based storage control apparatus comprises: a Nand Flash memory array, a storage controller, a user application logic layer, user logic, an infrastructure, and a state acquisition unit. The Nand Flash memory array obtains an operation instruction; a physical layer obtains an operation time sequence; a media interface layer obtains a parsed reconstruction data stream; a memory command layer obtains a decomposed Nand Flash operation data stream and a command interface time sequence; a storage link layer obtains data fames in accordance with the command interface time sequence and a decoded command interface time sequence; the user layer obtains a register configuration command, clock and reset signals, a work state, the operation instruction data stream; a memory maintenance and configuration unit obtains parsed register configuration command; the infrastructure obtains the clock and reset signals; the state acquisition unit obtains the work state; the user application logic layer obtains a data format and an operation format required by a memory control interface; and the state acquisition unit obtains a user logic operation command.
Owner:XIDIAN UNIV
High security removable storage device
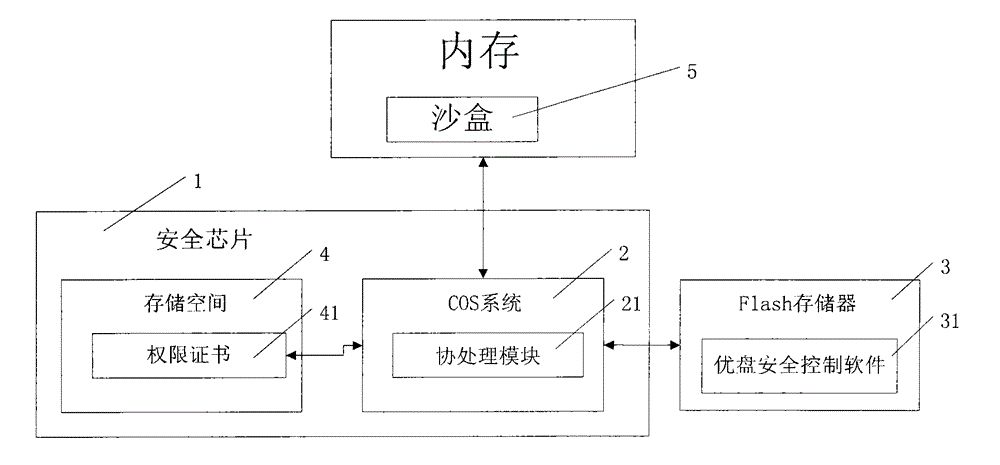
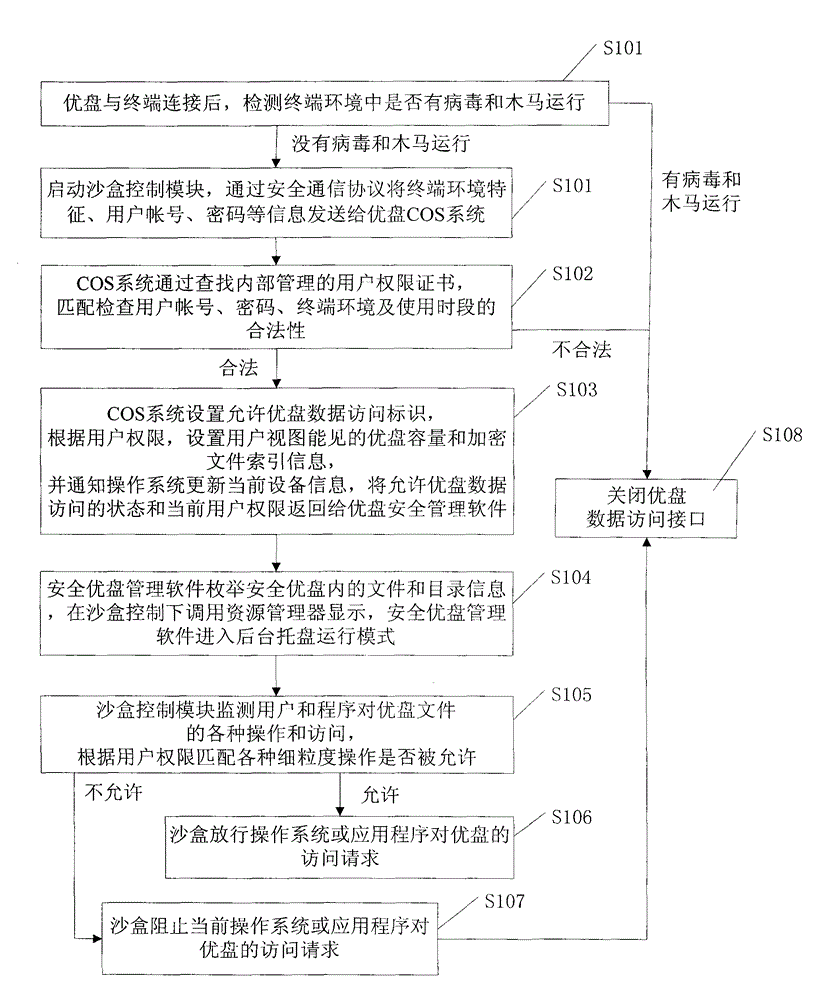
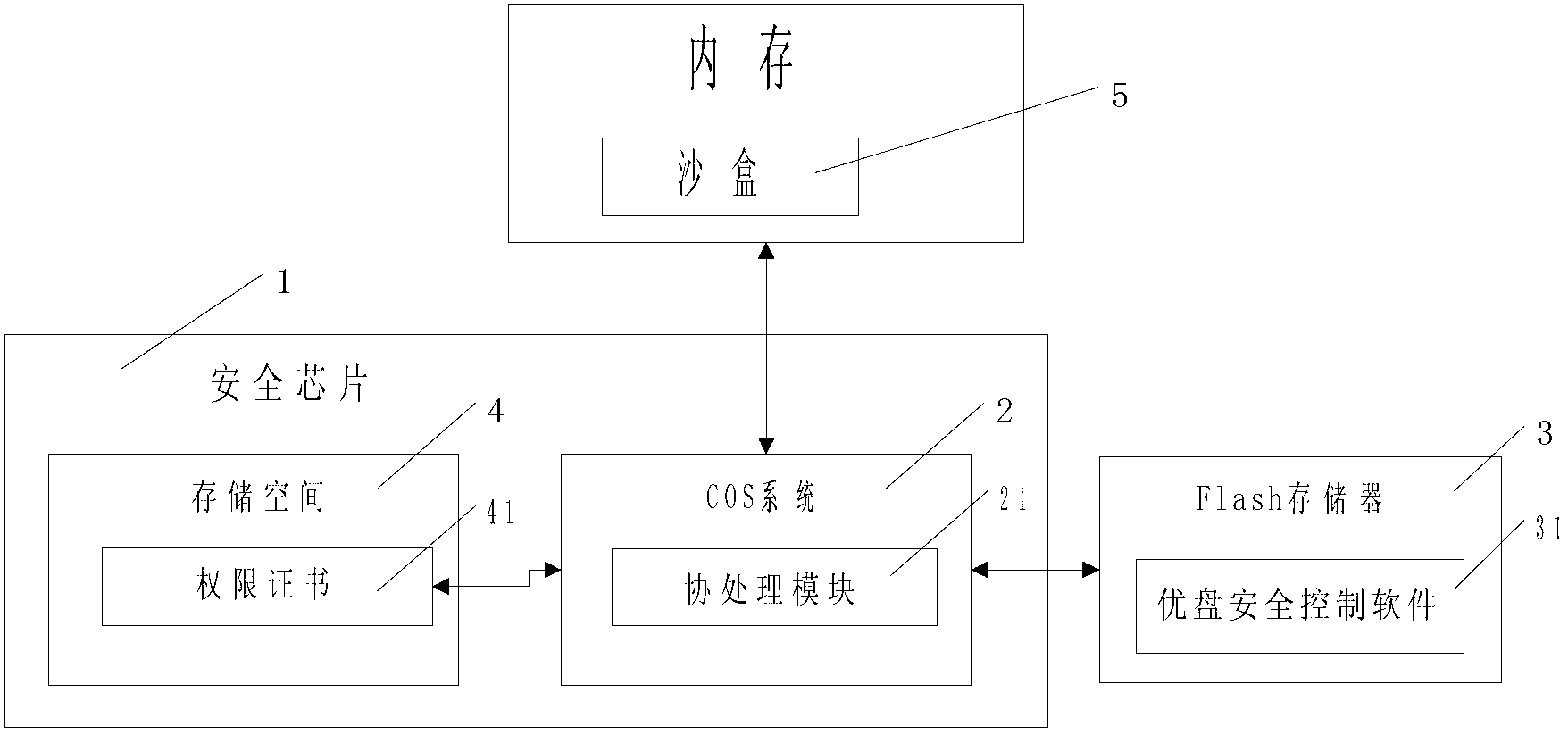
InactiveCN104102595AReduce the risk of useProtect Physical SecurityUnauthorized memory use protectionInternal/peripheral component protectionChip operating systemData view
The invention provides a high security removable storage device which comprises a safe main control chip, a chip operating system (COS) arranged in the chip, a flash memory and removable storage device safety management software arranged in the flash memory, wherein the COS system is stored in the safe chip and is used for managing the authority certificates corresponding to users; the removable storage device safety management software adopts a memory sandbox technology, and is used for monitoring and filtering various operations which are carried out on a removable storage device by the users and programs, checking the device service environment and the access authority of the removable storage device by being matched with the COS system, controlling the unauthorized use behaviors of data files of the removable storage device decoded to the memory, and recording various key sensitive operations. The high security removable storage device adopts an integral protection technology combining software and hardware, so that the security access control of the removable storage device can be realized, and the users having different authorities have different data views and fine grit operation authorities for the removable storage device; therefore, the users are prevented from privately copying the files and the content in the removable storage device, and the data of the removable storage device is prevented from being broken and stolen by viruses and Trojan horses.
Owner:张永昌
Safe USB flash disk and data active protection method thereof
ActiveCN102799539AImprove securityReduce the risk of useUnauthorized memory use protectionMedia access control'Active' protection
The invention provides a safe USB flash disk and a data active protection method thereof. The safe USB flash disk comprises a safe main control chip, a chip operating system (COS) in a chip, a Flash memory and USB flash disk safe management software built in the Flash memory, wherein the COS system is used for storing and managing an authority certificate corresponding to a user; and the USB flash disk safe management software is used for monitoring and filtering various operations carried out on the USB flash disk by the user and a program, checking use environment and access authority of the USB flash disk equipment in cooperation with the COS system, controlling a unauthorized use behaviour of a USB flash disk data document which is deciphered to the memory and recording various key sensitive operations by adopting a memory sandbox technology. Since the USB flash disk adopts a hardware-software integrated protection technology, the safe access control of the USB flash disk is realized and users having different authorities have different USB flash disk data views and fine-grit operation authorities so that users can be prevented from privately copying documents and contents in the USB flash disk and the USB flash disk data is prevented from be destroyed and stole due to viruses and Trojans.
Owner:CHANGSHA WENDUN INFORMATION TECH
Method and a system for controlling user data reading and writing security rights based on roles and resources
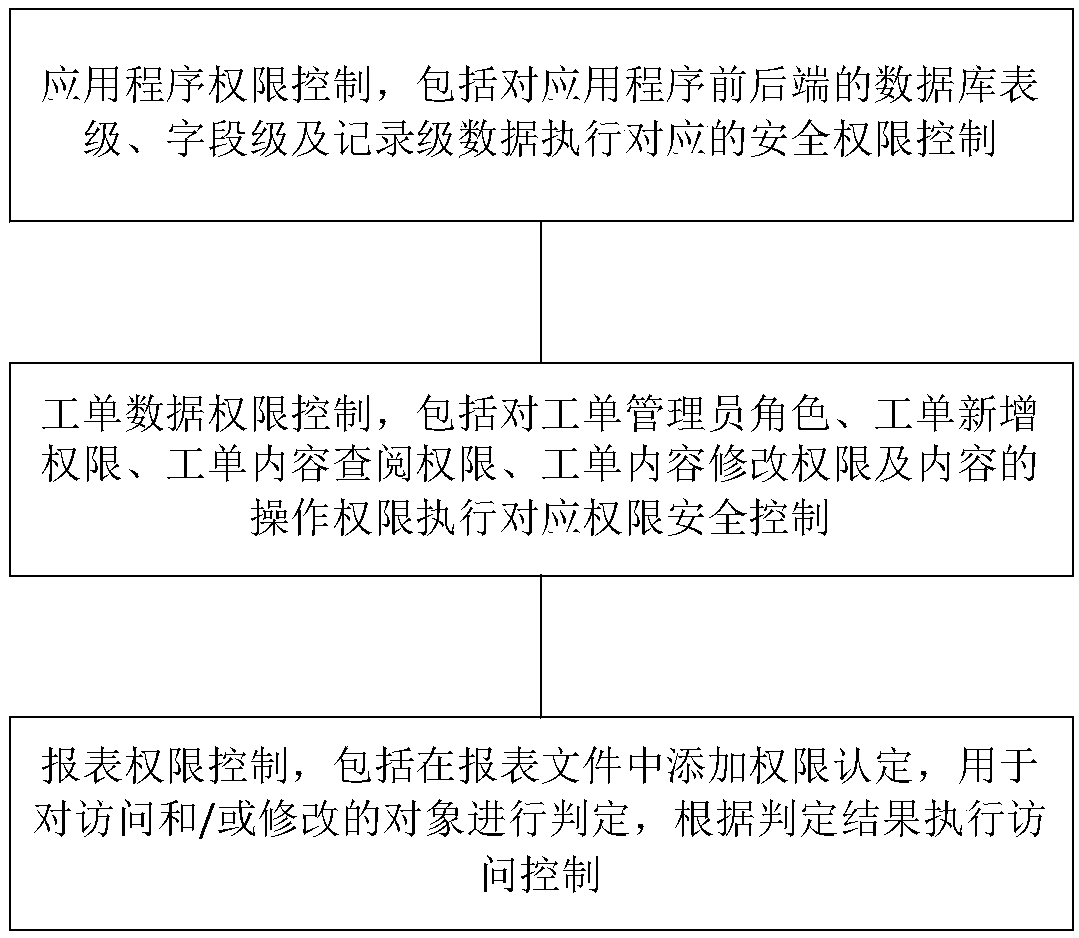
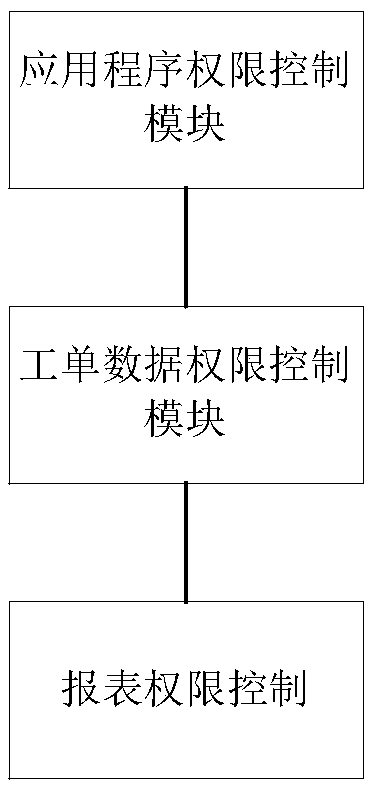
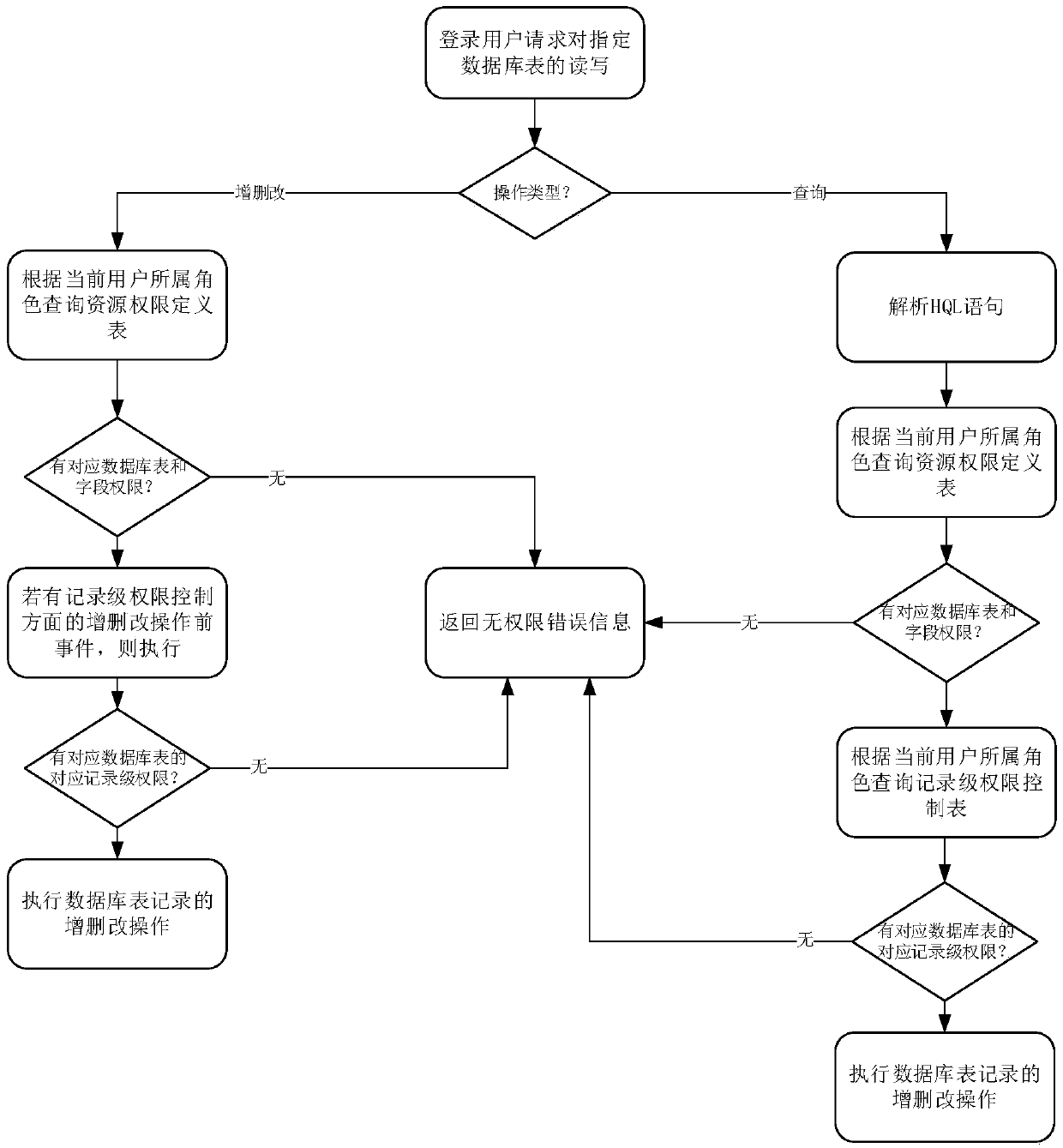
ActiveCN109522707AFlexible Access ControlFlexible Assist ControlDigital data authenticationApplication softwareLevel data
The technical proposal of the invention comprises a method and a system for controlling user data reading and writing security rights based on roles and resources, which are used for realizing the following functions: controlling application program rights, including executing corresponding security rights control on database table level, field level and record level data at the front and back ends of the application program; controlling user data reading and writing security rights based on roles and resources. Work order data permission control, including work order administrator role, workorder adding permission, work order content viewing permission, work order content modifying permission and content operation permission to implement corresponding permission security control; Reporting permission control, including the addition of permission assertions to the report file, is used to determine access and / or modified objects, and to perform access control based on the determinationresults. The invention has the advantages that the user-defined matching can flexibly define various complicated fields or report screening conditions; Flexible and changeable table level, field level and record level omni-directional matrix permission control can be realized.
Owner:珠海伟诚科技股份有限公司
Method, device and equipment for credibly executing environmental safety authentication
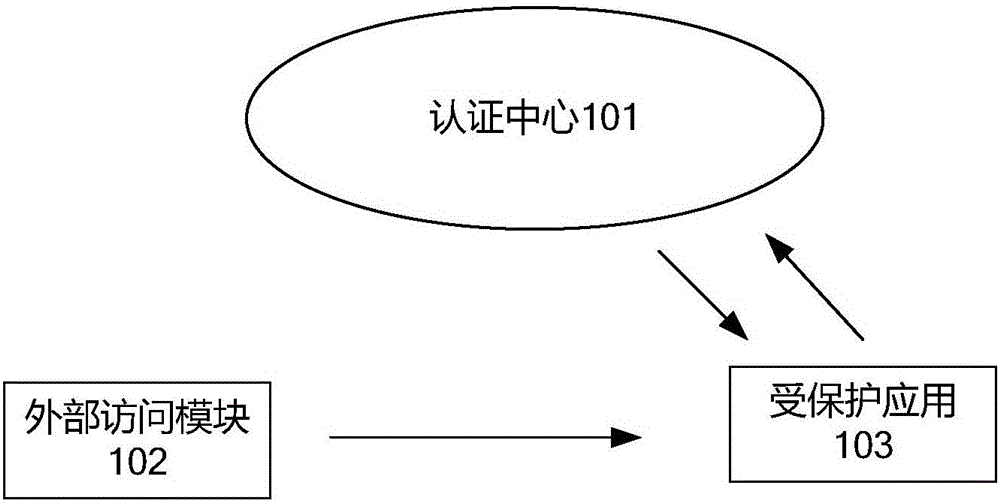
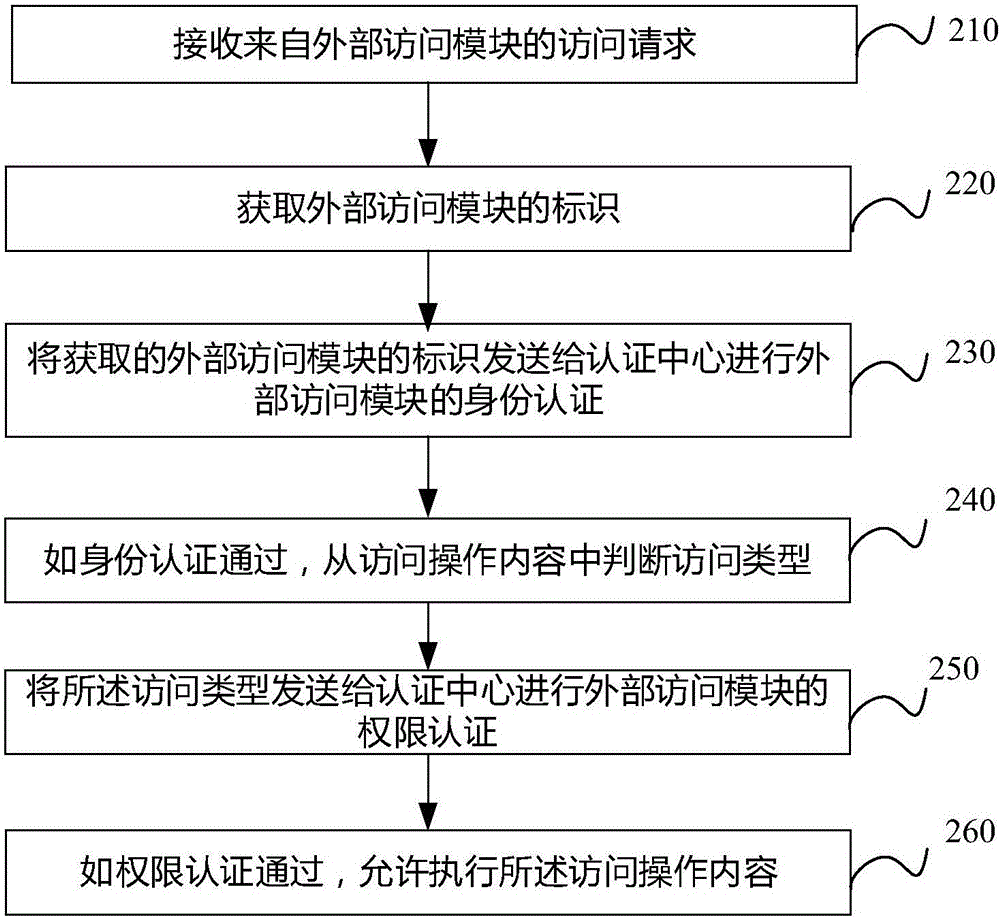
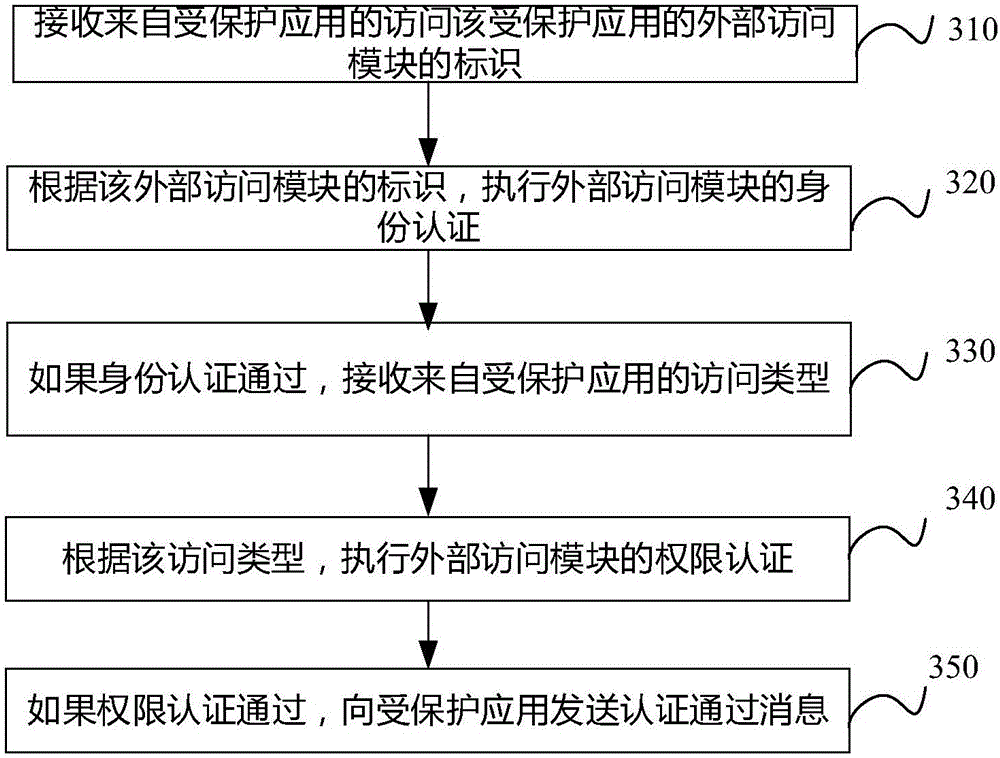
ActiveCN106778342AFlexible Access ControlMeet information authentication requirementsDigital data protectionAuthenticationEnvironmental safety
The invention discloses a method, a device and equipment for credibly executing environmental safety authentication. The method comprises the following steps: receiving an access request from an external access module, wherein access operation content is contained in the access request; acquiring an identity of the external access module; sending the acquired identity of the external access module to an authentication center and authenticating the identity of the external access module; if passing the identity authentication, judging the access type from the access operation content; sending the access type to the authentication center and authenticating the authority of the external access module; and if passing the authority authentication, allowing to execute the access operation content. The invention provides a more flexible TEE safety authentication method which can meet various information authentication requirements of the computer development at present.
Owner:BEIJING BANGCLE TECH CO LTD
Implementation method of communication middleware by adopting HTTP proxy database protocol
ActiveCN111818166AStrong penetrating powerEasy to develop and testDigital data information retrievalEncryption apparatus with shift registers/memoriesConnection poolEngineering
The invention discloses an implementation method of communication middleware by adopting an HTTP proxy database protocol. Database protocols realized by different manufacturers themselves are adoptedin the database middleware to connect different databases, different manufacturers need to add different JDBC drive packages in advance, and the JDBC drive packages are packaged into HTTP protocols for proxy communication. The HTTP protocol can penetrate through the gateway layer more easily, the influence of the network layer is reduced, and development testing and formal deployment are facilitated. The Client only needs one access address, so that multiple types of databases can be conveniently accessed and managed at the same time. The number of connection pools of the database layer can beobviously reduced after service growth. Rich sql execution conditions and runtime monitoring information can be increased. The flexible database access control, such as access permission and requestfrequency, can be self-defined.
Owner:杭州隐捷适生物科技有限公司
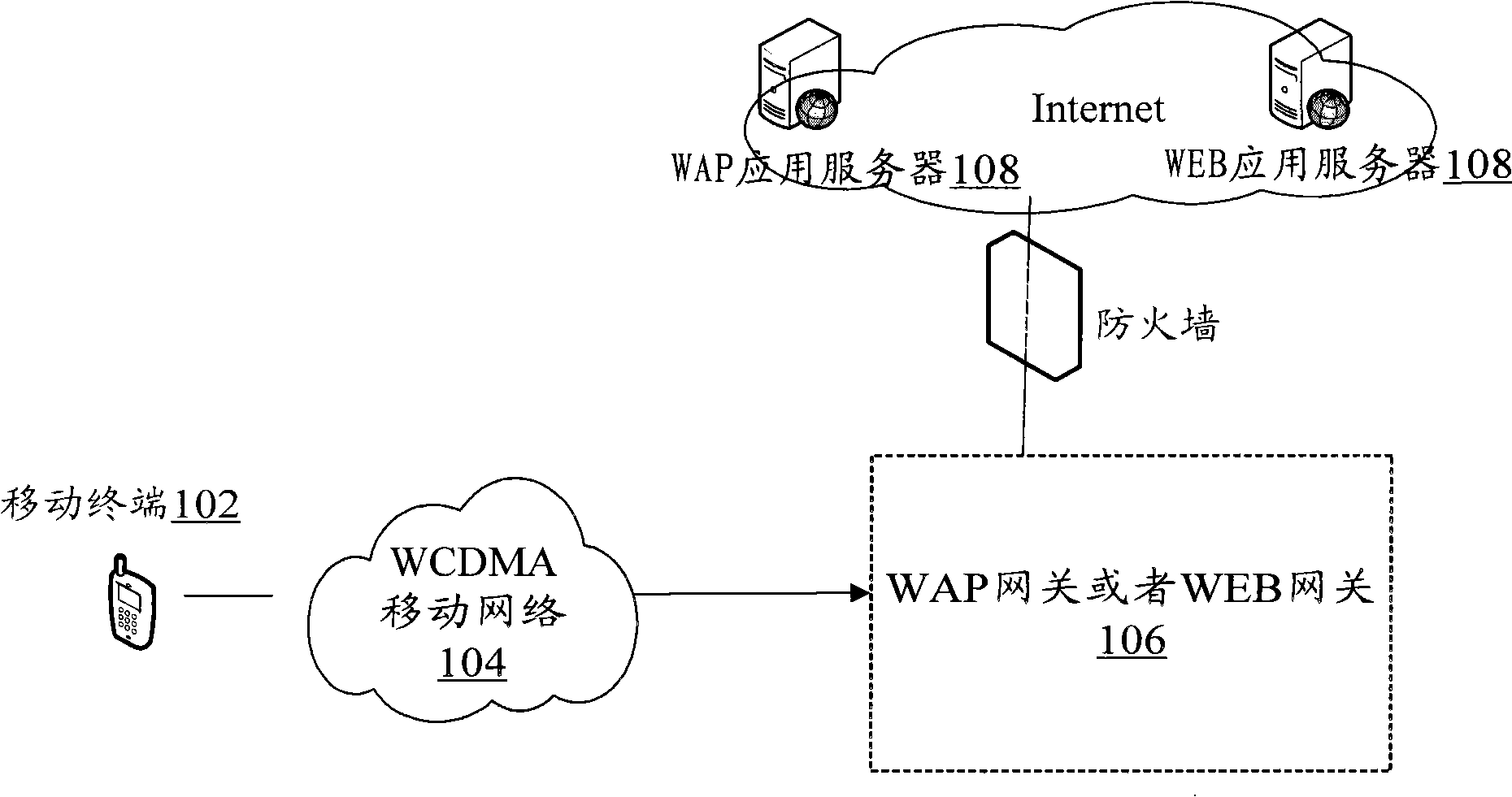
Access-controlling method, repeater, and server
InactiveUS20050226256A1Flexible Access ControlMaintain unityMultiple digital computer combinationsRadio/inductive link selection arrangementsRelevant informationComputer terminal
Access from a terminal of an outside network to a server of an inside network is put under control. A repeater and the server permit a packet transmission from the terminal to the server under limited conditions. When the server acknowledges connection for the permitted packet, the transmission conditions for packets to be sent to the server are loosened. After then, packet transmission between the terminal and the server is controlled under the loosened transmission conditions. As for encrypted packets, the server decodes the encrypted packets and notifies the relevant information to the repeater.
Owner:SOVEREIGN PEAK VENTURES LLC
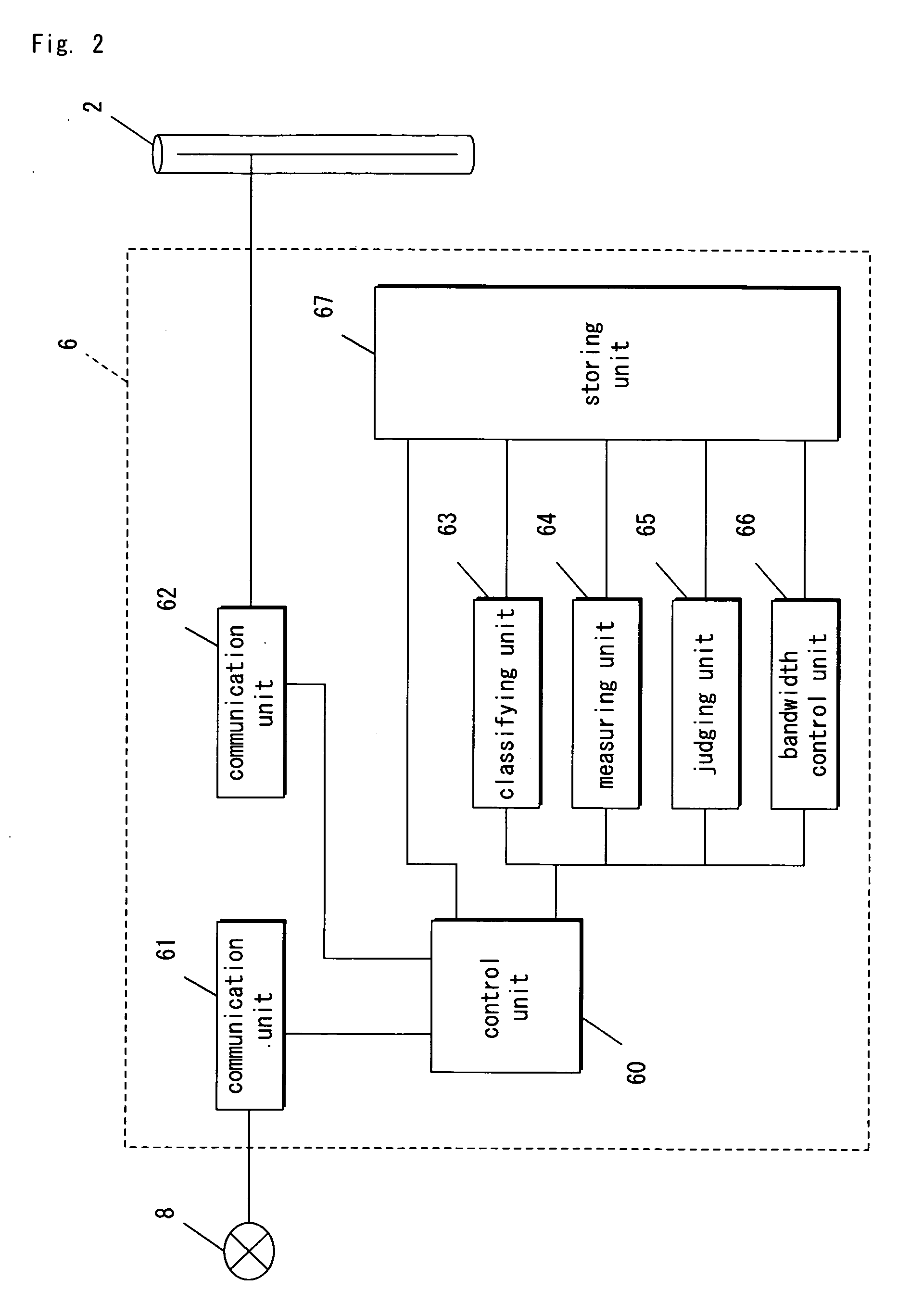
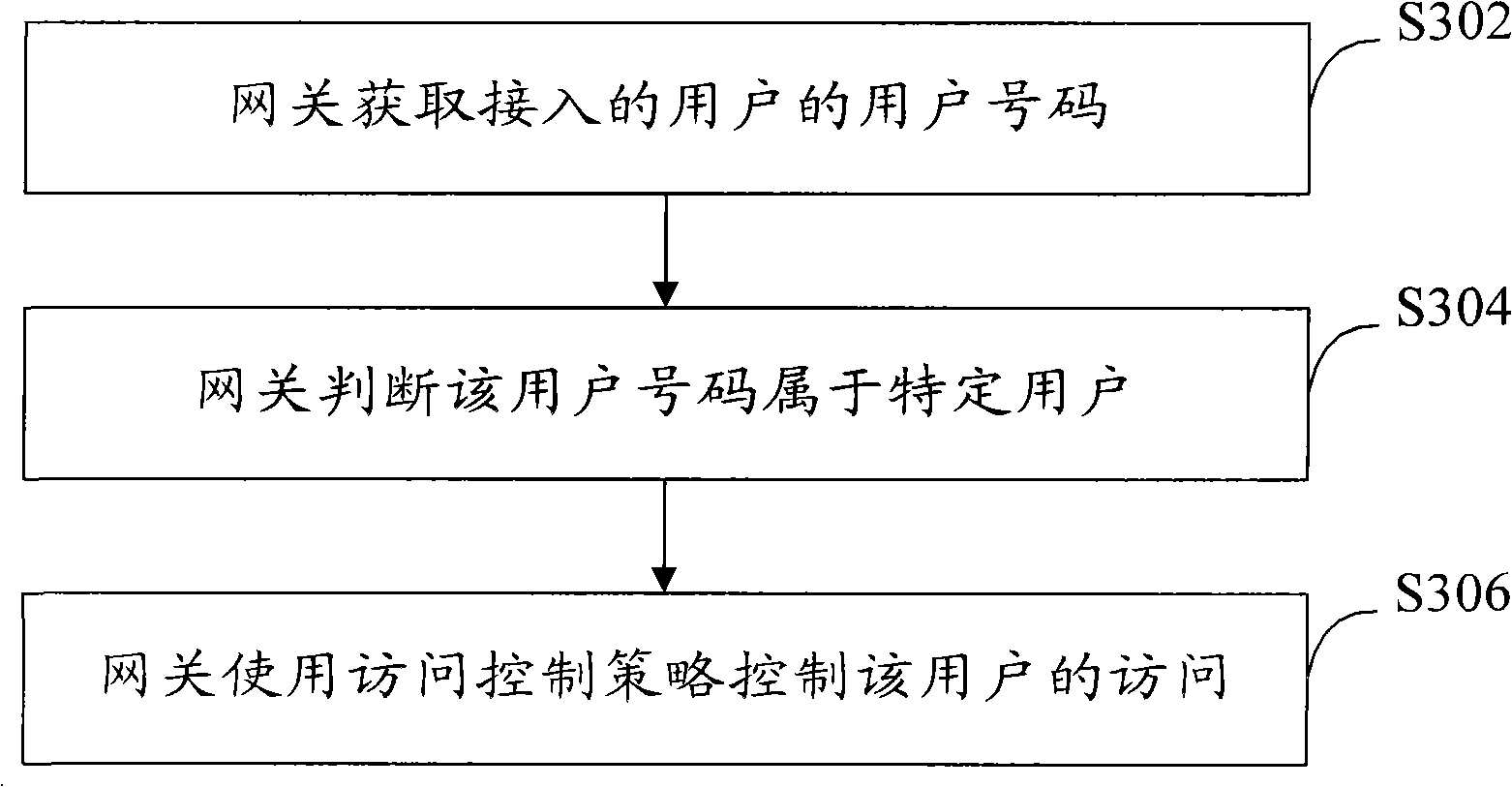
Access control method and gateway
InactiveCN102340493AImplement access controlIncrease flexibilityWireless network protocolsTransmissionService controlAccess time
The invention discloses an access control method and a gateway. The access control method comprises: a gateway uses access control strategies to carry out access control on a specific user, wherein the access control strategies includes at least one among the following strategies: an access address control strategy, an access time control strategy and an access service control strategy; besides, the access address control strategy is used for controlling an accessed unified resource localization URL address; the access time control strategy is used for controlling access time; and the access service control strategy is used for controlling services provided by an accessed service provider. According to the invention, flexibility and convenience of access control on a specific user are realized.
Owner:ZTE CORP
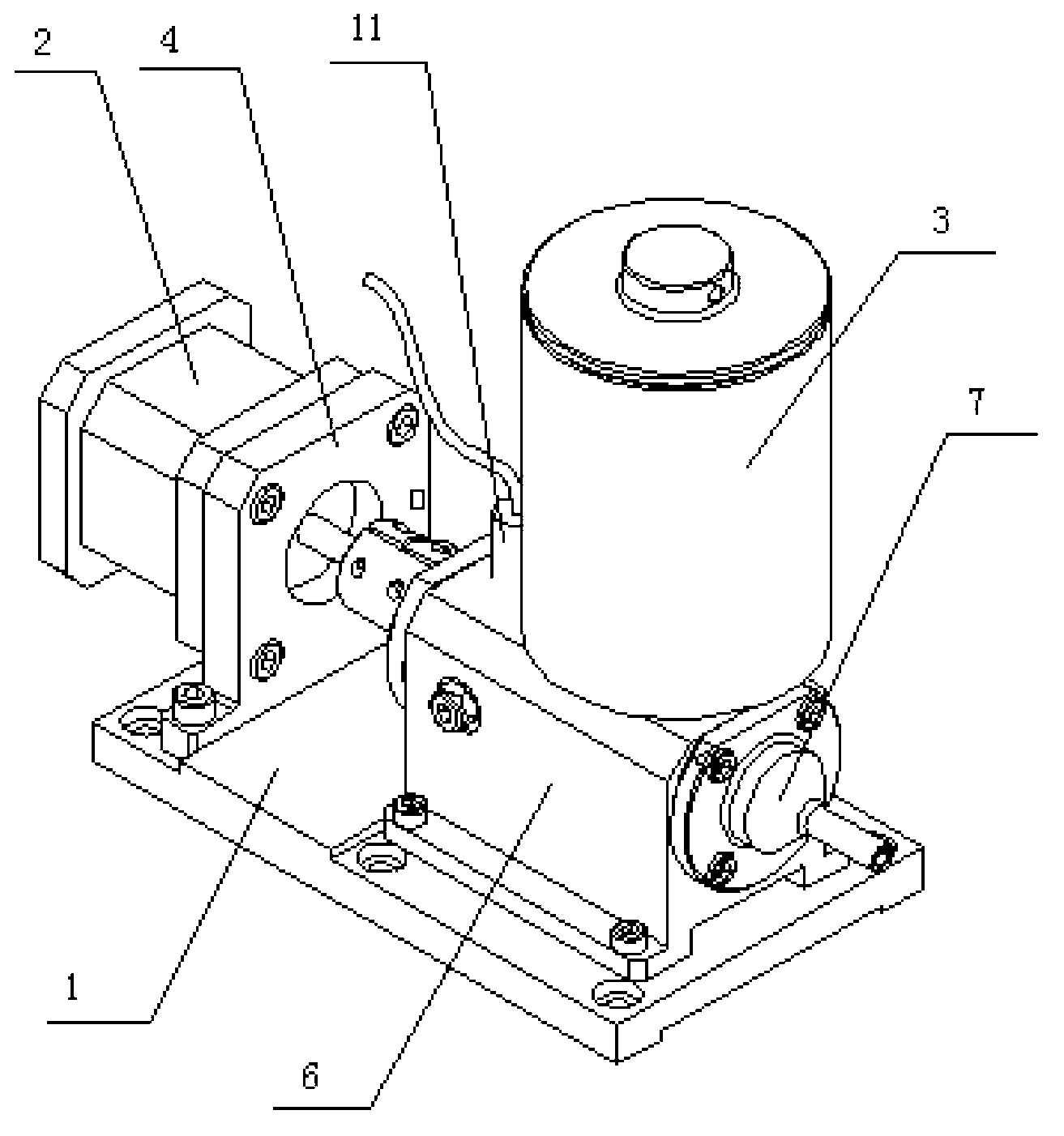
Dispenser
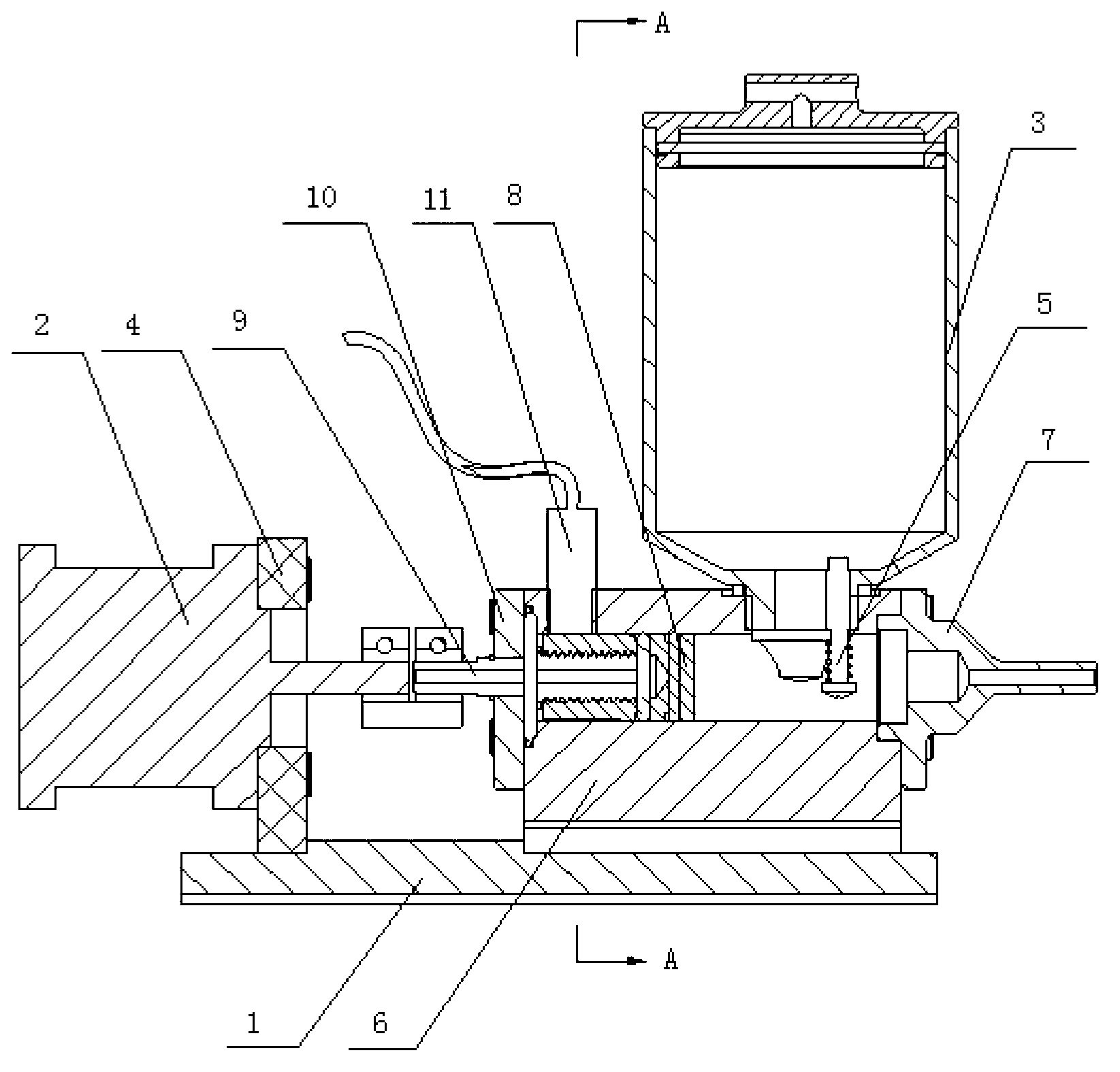
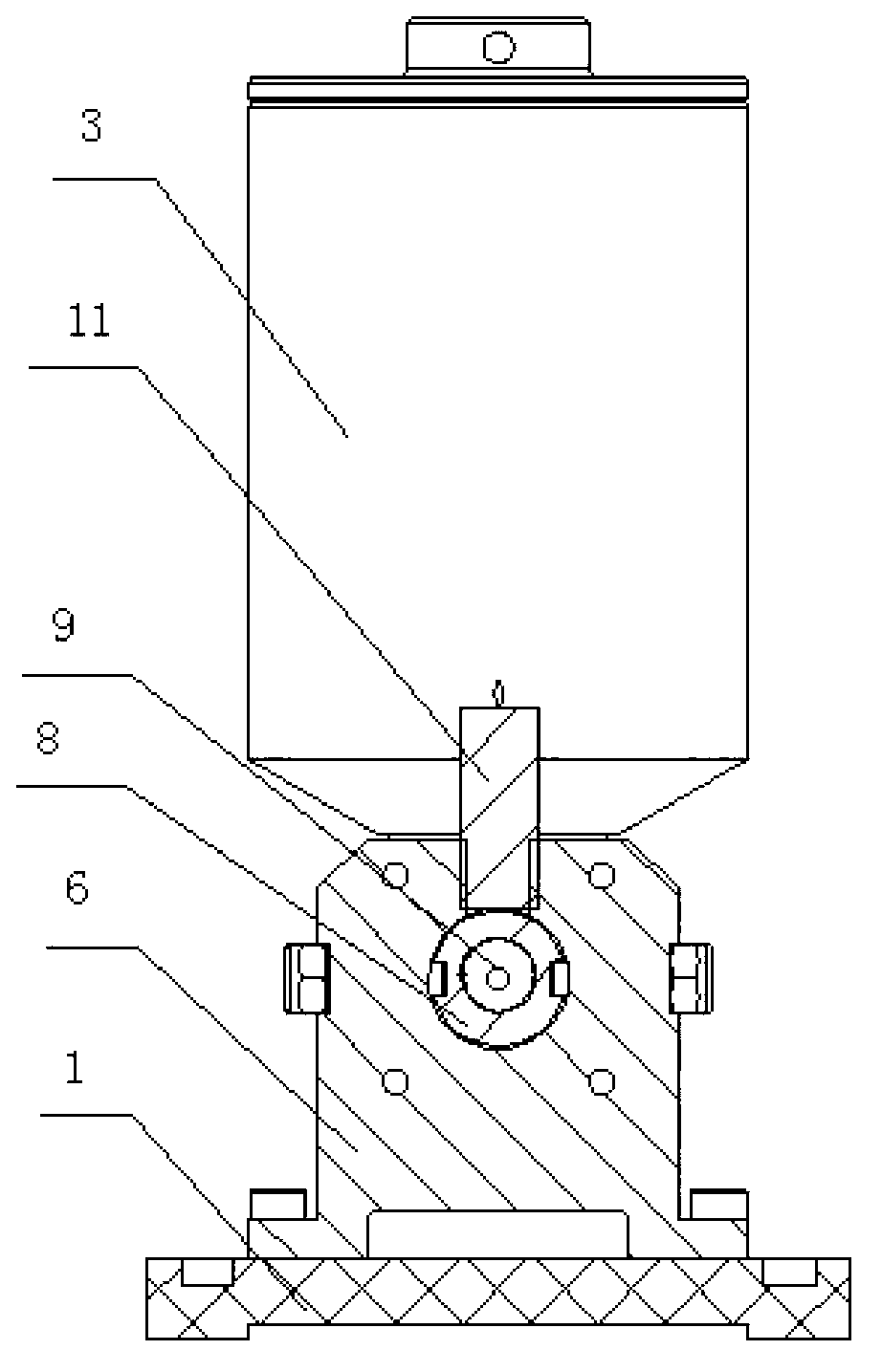
InactiveCN102836803AWith suction functionSimple structureLiquid surface applicatorsCoatingsCouplingEngineering
The invention discloses a dispenser, relating to a gluing device. The dispenser comprises a pedestal, a motor, a glue tank and a dispensing device, wherein the motor is fixedly arranged at one end of the pedestal through a mounting plate; the dispensing device is fixedly arranged at the other end of the pedestal; the glue tank is fixedly arranged above the dispensing device; a one-way valve is arranged at an opening of the glue tank; the dispensing device comprises a cavity; the front end of the cavity is fixed with a glue discharge nozzle; a piston is arranged in the cavity; symmetric grooves are arranged on two sides of the piston; the piston is fixedly arranged on a screw; the screw is fixedly arranged at the tail end of the cavity through an end cover; the tail end of the screw is connected with a motor output shaft through a coupling; and a heating film is also wound outside the cavity. The dispenser has the advantages of simple structure, small size, convenience in control and capabilities of realizing flexible control to finish quantitative feed and discharge functions of glue.
Owner:SHANDONG ATAW IND ROBOT TECH
Access control method and device
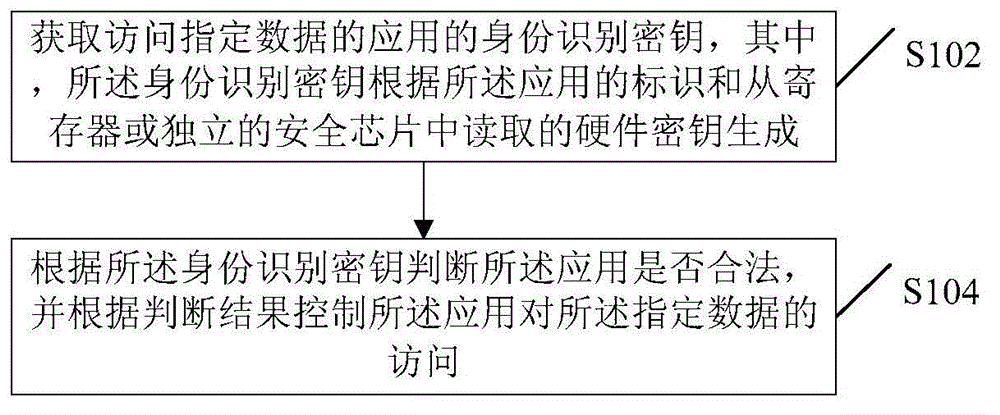
InactiveCN105282117ASolve the problem of limited access control methodsFlexible Access ControlTransmissionIdentification keyProcessor register
The present invention discloses an access control method and device. The access control method comprises: obtaining an identification key of an application for assign data access, the identification key being generated by reading a hardware key from a dwell vessel or an independent security chip according to the identification of the application; determining whether the application is legal or not according to the identification key; and controlling the application for the assign data access according to the determination result. Through adoption of the access control method and device, the problem that right control modes of data access in correlation techniques having limitations is solved, the right control of data access may be more flexible, and the safety is much higher.
Owner:ZTE CORP
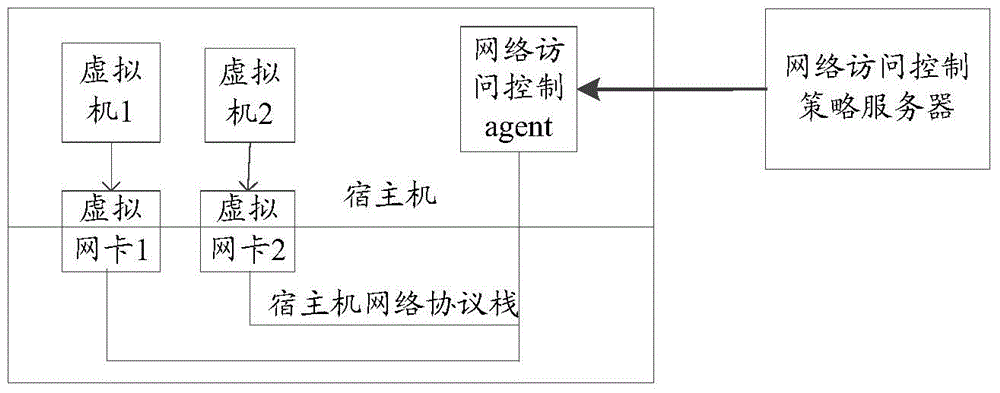
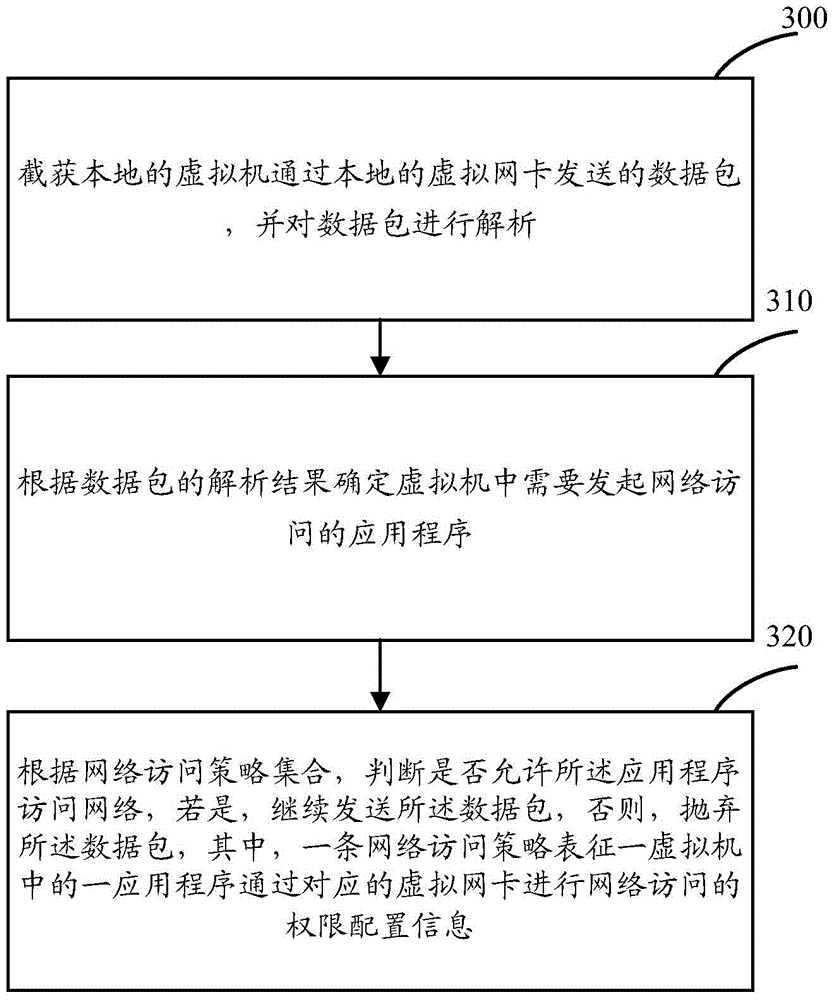
A method and apparatus realizing virtual machine network access control
ActiveCN106161396AFlexible network access controlFlexible Access ControlData switching networksNetwork packetNetwork Access Control
The application relates to the field of computers, and especially relates to a method and apparatus realizing virtual machine network access control in order to realize network access control of any application in a virtual machine. The method comprises the steps of intercepting data packets sent by a local virtual machine through a local virtual Ethernet adapter and analyzing the data packets; determining an application program, which needs to initiate network access, of the virtual machine according to the analysis result of the data packets; according to a network access strategy collection, determining whether to allow the application program to access the network; if the application program is allowed to access the network, continuing to send data packets; otherwise, discarding the data packets. As a result, the method and apparatus have characteristics of fine grains and bypassing preventing, thereby enabling the network access control of the virtual machine to be more flexible and more reliable.
Owner:ALIBABA GRP HLDG LTD
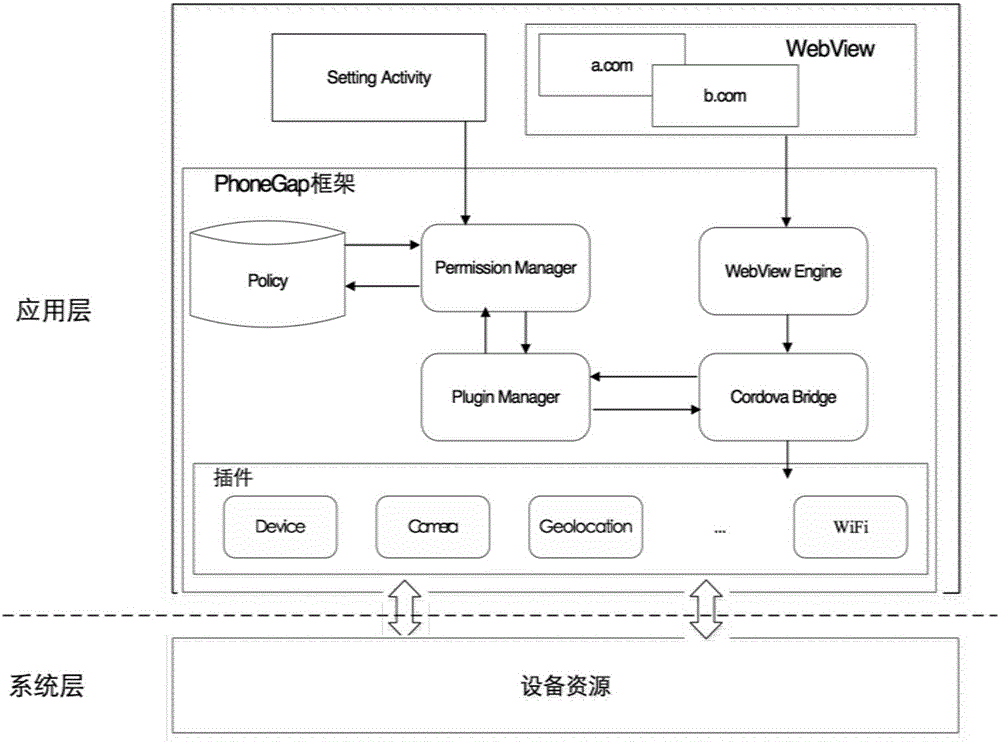
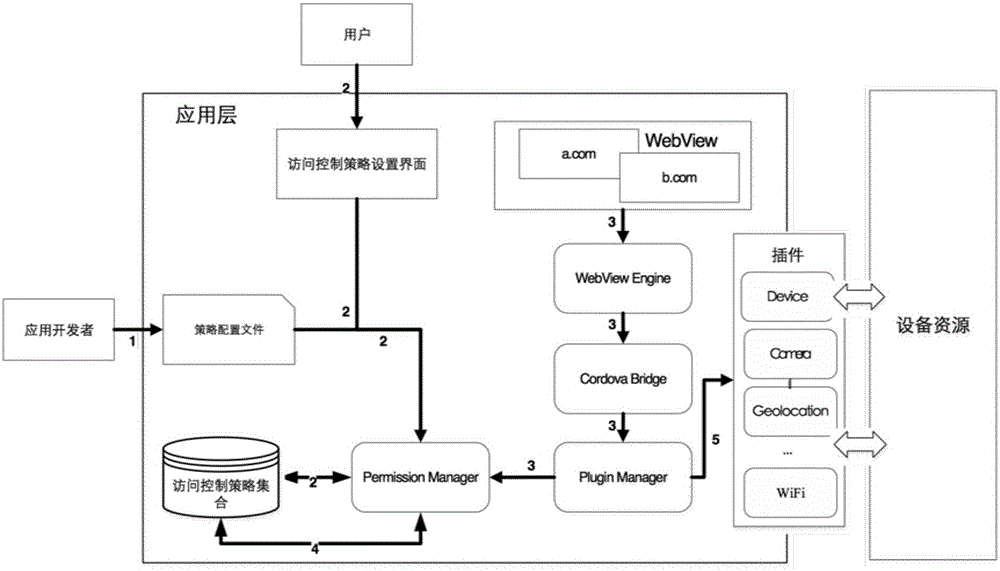
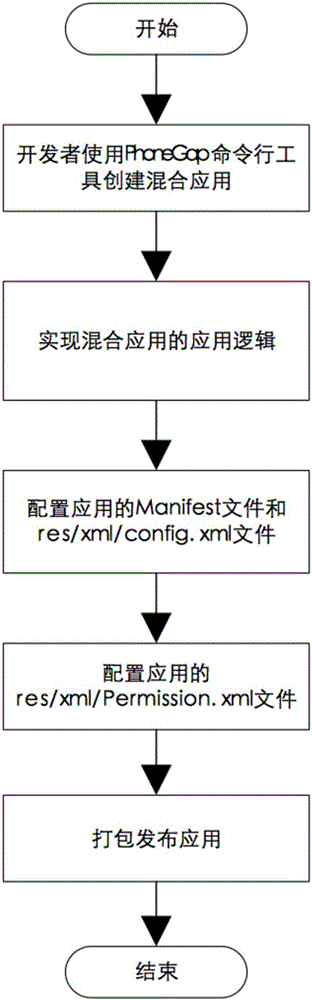
Fine-grained access control method for hybrid Android applications
ActiveCN106850545AFlexible Access ControlAvoid management methodsDigital data authenticationTransmissionNetwork codeMedia access control
The invention discloses a fine-grained access control method for hybrid Android applications. The method comprises: an accessing operation to system resources of an Android device is encapsulated in the form of plug-in objects; different plug-in access permission is granted to network content loaded from different sources in a hybrid application by configuring an access control policy; and when a system resource access operation is triggered by the hybrid application, whether a current request has access permission to the requested resources is judged by an access control framework according to the access control policy so as to control accessing operations on the system resources by different network codes loaded in the hybrid application. Compared with a permission-based native access control mechanism on an Android platform, the method has finer-grained access control and grants different system resource access permission to different network codes in the hybrid applications, so that the use is flexible, no modification is required in Android system and Web pages and the usability is good.
Owner:HUAZHONG UNIV OF SCI & TECH
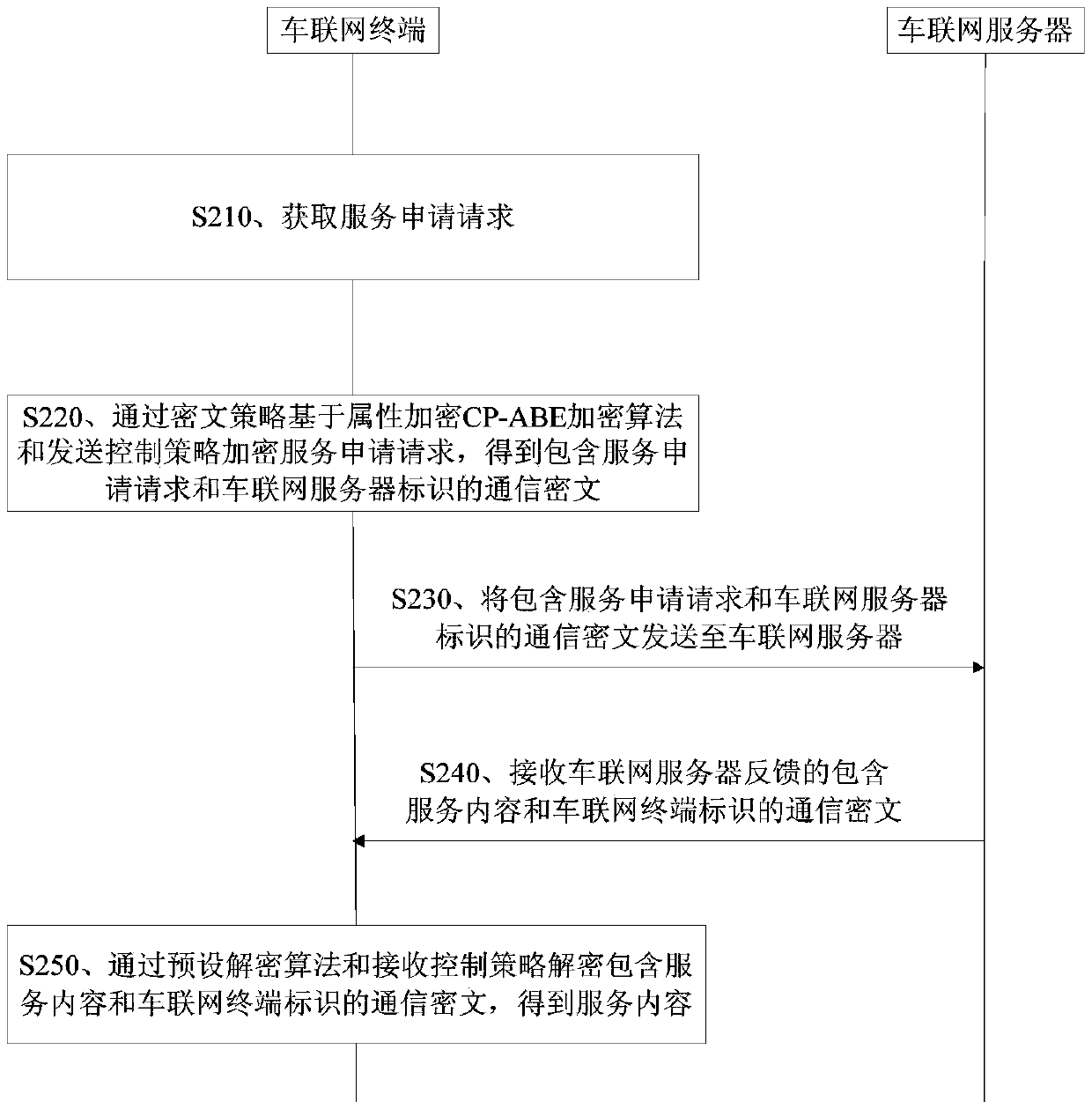
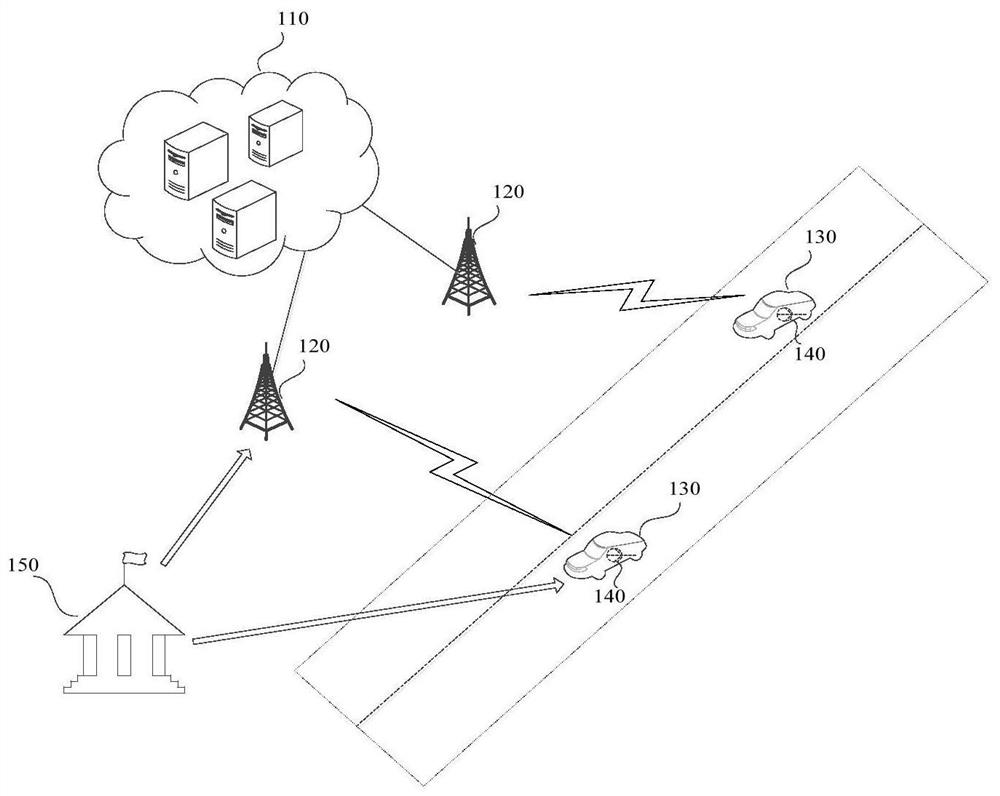
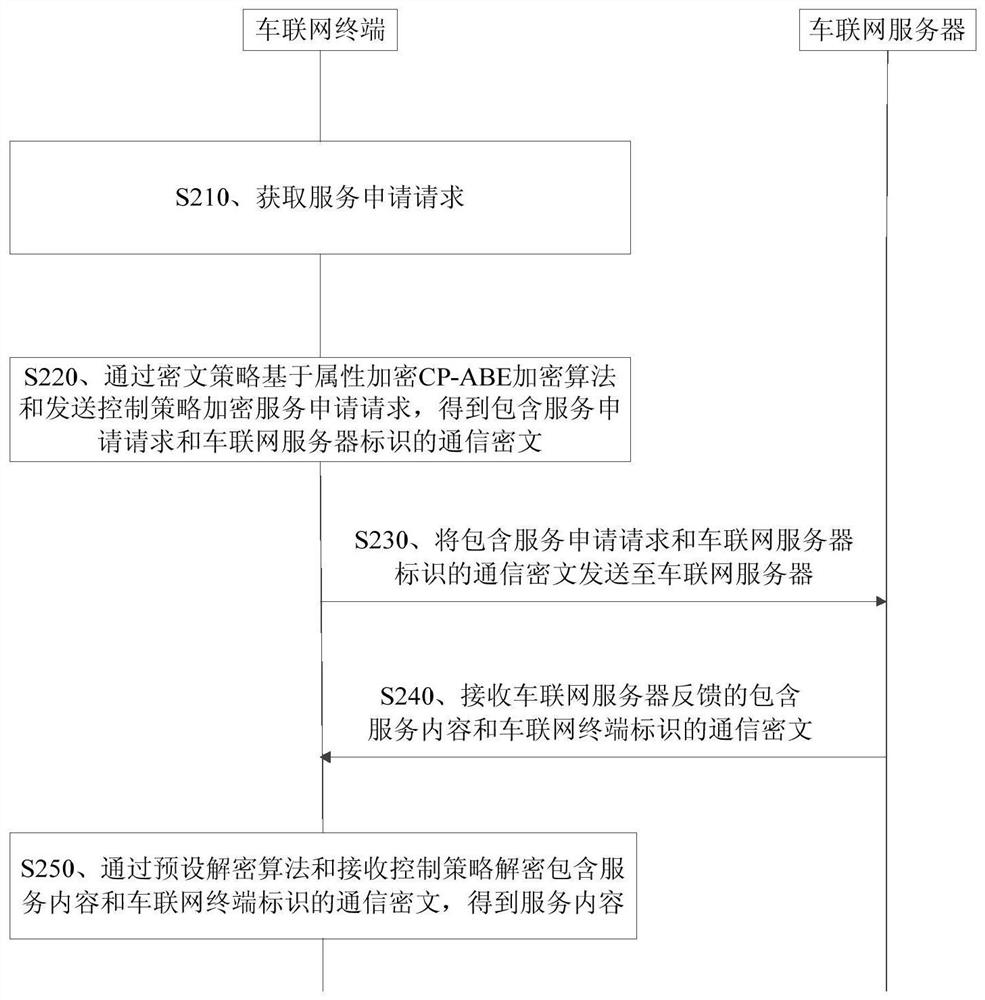
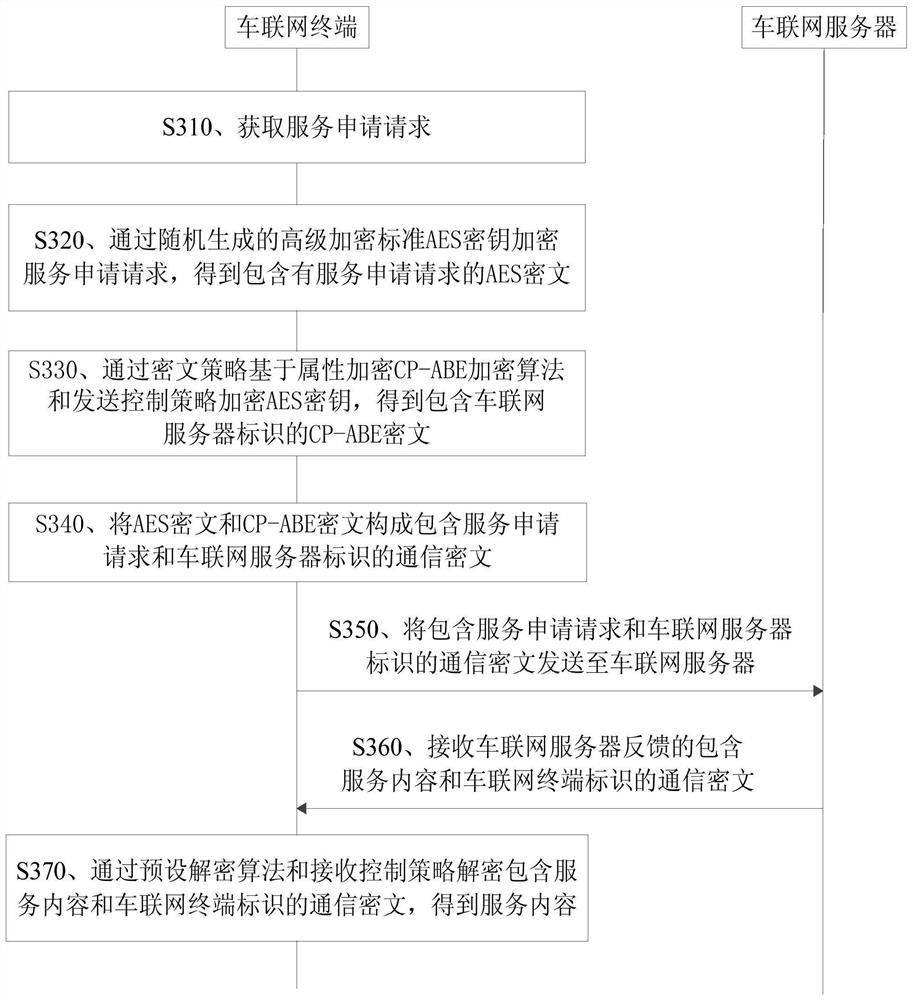
A vehicle networking service request method and apparatus
ActiveCN109543439AFlexible Access ControlGuaranteed confidentialityDigital data protectionAttribute-based encryptionConfidentiality
The invention discloses a vehicle networking service request method and device. The method comprises the following steps of: obtaining a service application request, wherein the service application request comprises vehicle information and a service type; performing Attribute-based encryption via ciphertext policy CP-ABE encryption algorithm and transmitting a control strategy encryption service application request to obtain a communication ciphertext including a service application request and an identification of a vehicle networking server; Sending a communication ciphertext including a service application request and a vehicle networking server identification to the vehicle networking server; Receiving a communication cipher text fed back by a vehicle networking server including a service content and a vehicle networking terminal identification; obtaining The service content by decrypting the communication ciphertext containing the service content and the vehicle networking terminal identifier by a preset decryption algorithm and a reception control strategy. The method realizes the access control of the vehicle networking terminal and the vehicle networking server flexibly while ensuring the data confidentiality.
Owner:RUN TECH CO LTD BEIJING
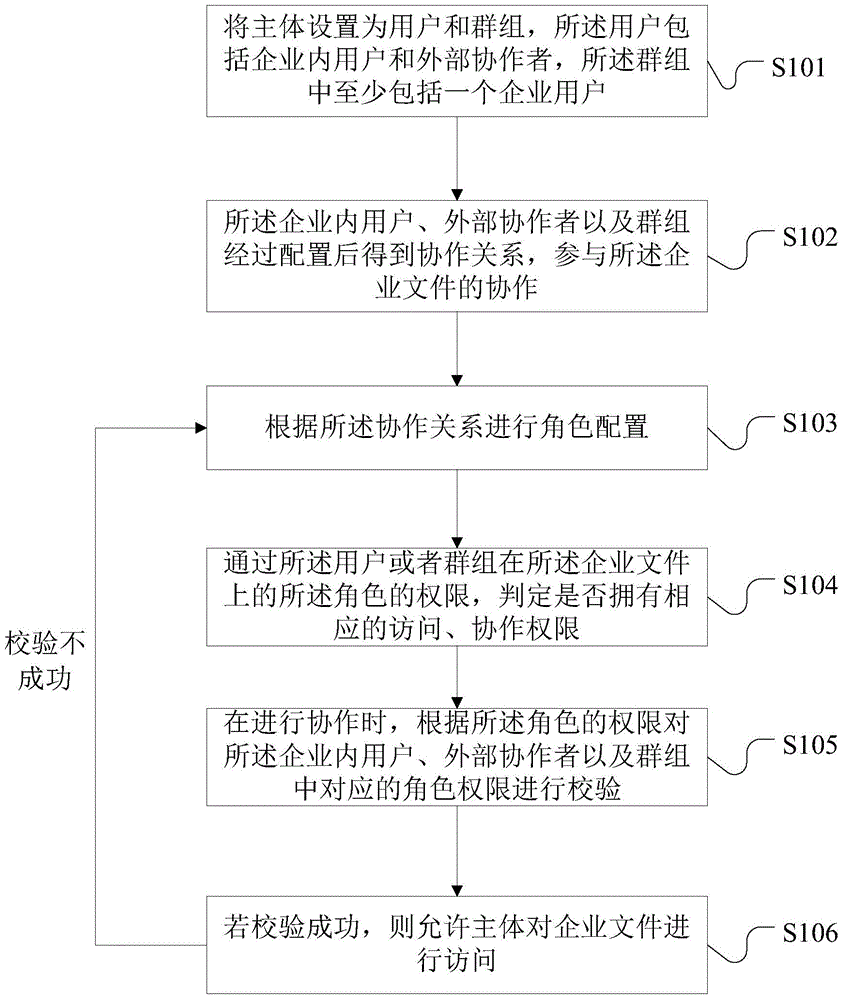
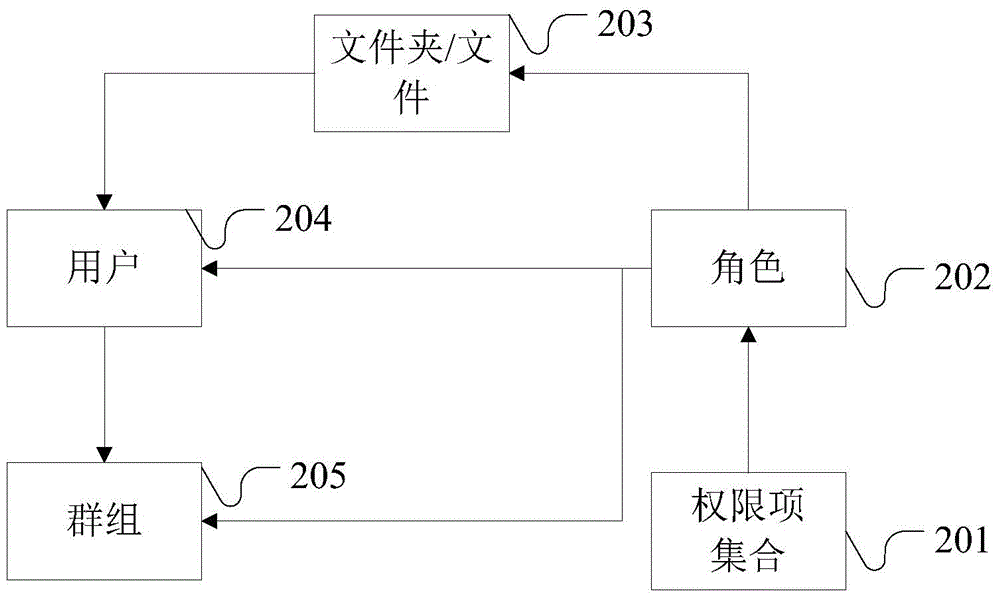
Enterprise file collaboration and access control method and system based on RABC
ActiveCN105760774ASimplify collaboration managementCollaborateDigital data protectionSpecial data processing applicationsComputer scienceWorld Wide Web
The invention provides an enterprise file collaboration and access control method and system based on RABC.Users in an enterprise, outside collaborators and groups are configured in an RABC model to obtain a collaborative relationship to participate in collaboration of enterprise files.Role authorities corresponding to the users in the enterprise, the outside collaborators and the groups are verified through the authorities of the roles, an original model is expanded, conceptions of the groups and the outside collaborators are introduced, and control management is more convenient and flexible.The roles can be separated from the users and the groups, the roles can be separated from the authorities, each user owns one role, and each role owns a corresponding authority set; the users can own different collaboration authorities for different files or folders by changing the roles, and the corresponding relationships between the roles and the authorities are automatically adjusted; access control of the users judges whether corresponding operating authority items are owned or not through the roles of the users on the files.The access control implementation difficulty is simplified, and front authority verification sets rear role authority verification.
Owner:杭州奇亿云计算有限公司
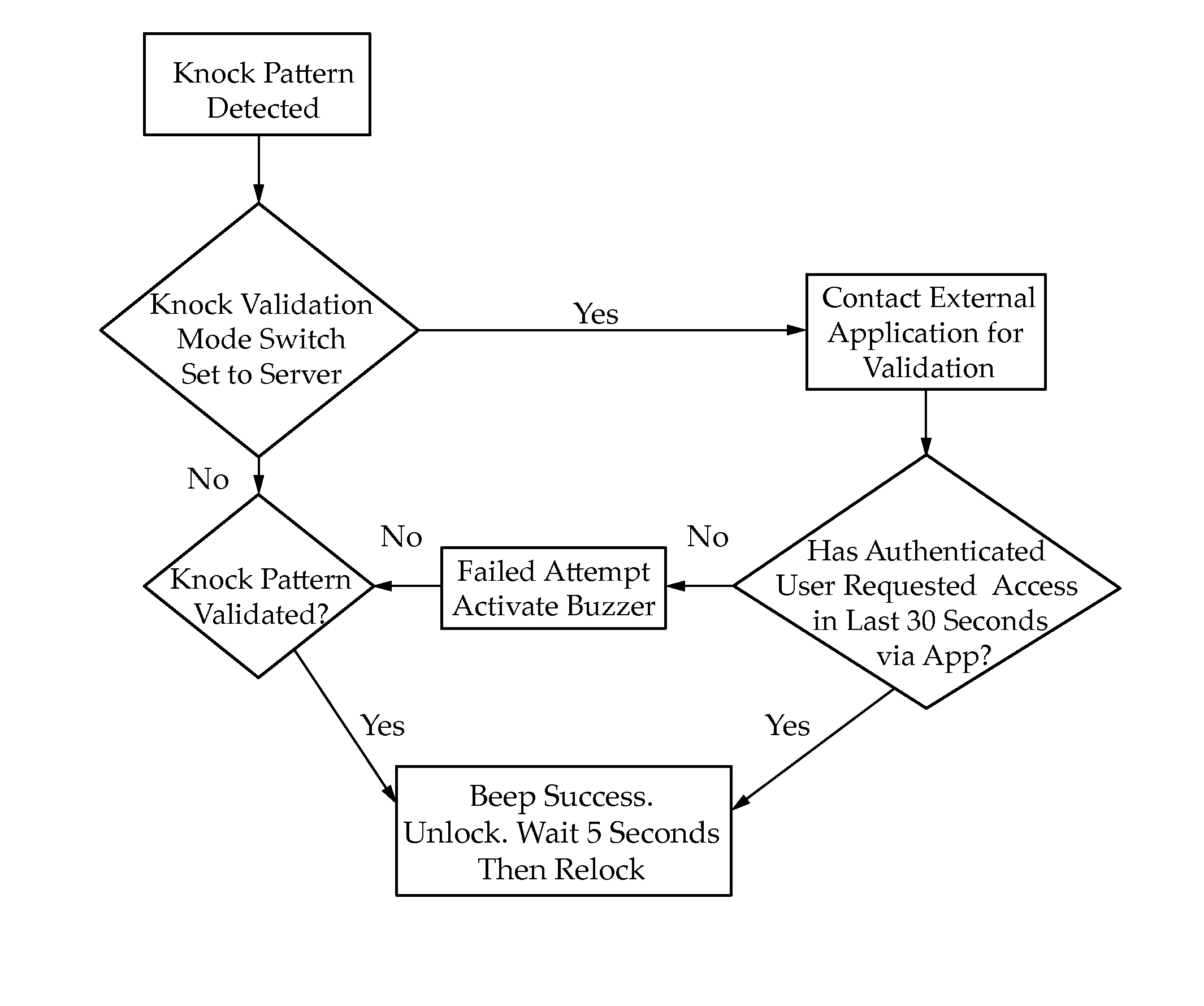
Remote Control Unlocking and Locking System
ActiveUS20150015362A1Shorten the timeFlexible Access ControlElectric signal transmission systemsMultiple keys/algorithms usageSystems designControl system
A portable, temporary removable system for locking and unlocking a door knob, door lever or locking deadbolt without the requirement of using keyed entry. Several manners of automated locking and unlocking are introduced and the instant system is designed for quick installation and removal. Once attached, the system may be remotely controlled from the outside of the door via a pattern of knocks, via electronic communications or a combination of a knock pattern and electronic communication.
Owner:MURPHY MATTHEW
Access control method, system and device and access behavior identification method, system and device and storage medium
ActiveCN111209574AReasonable access controlFlexible Access ControlDigital data protectionApplication procedureEngineering
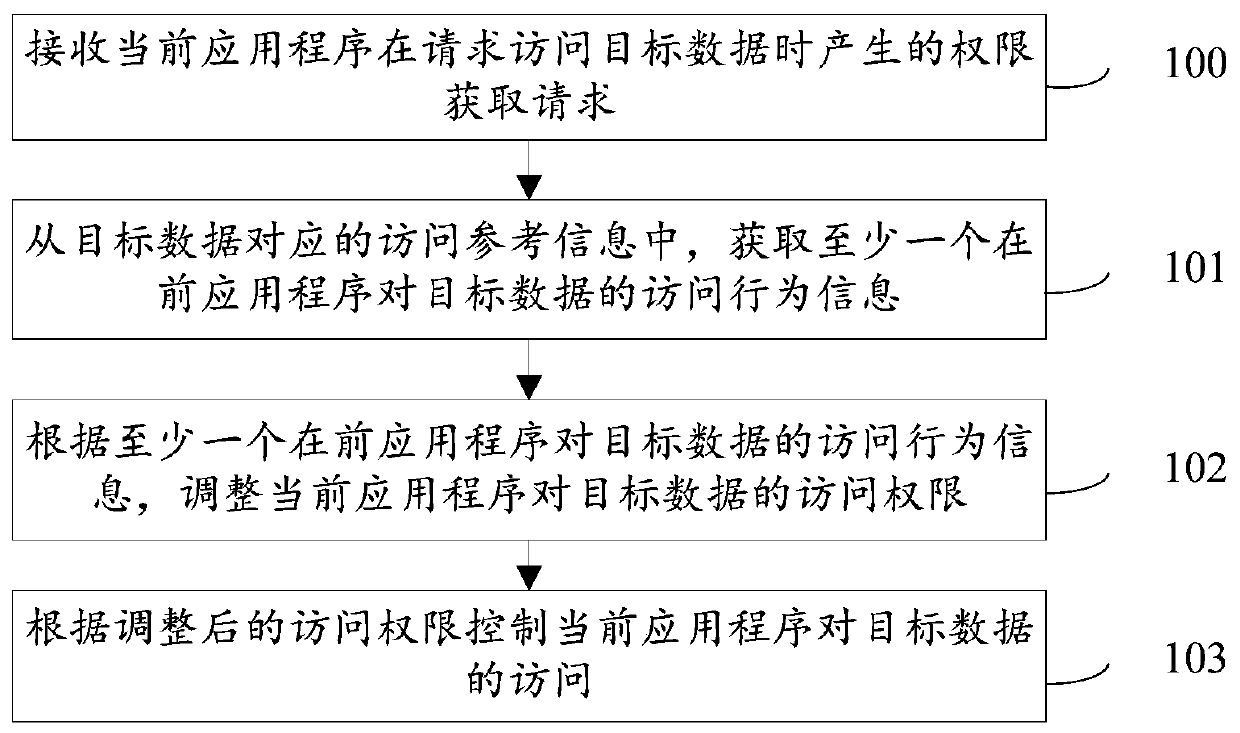
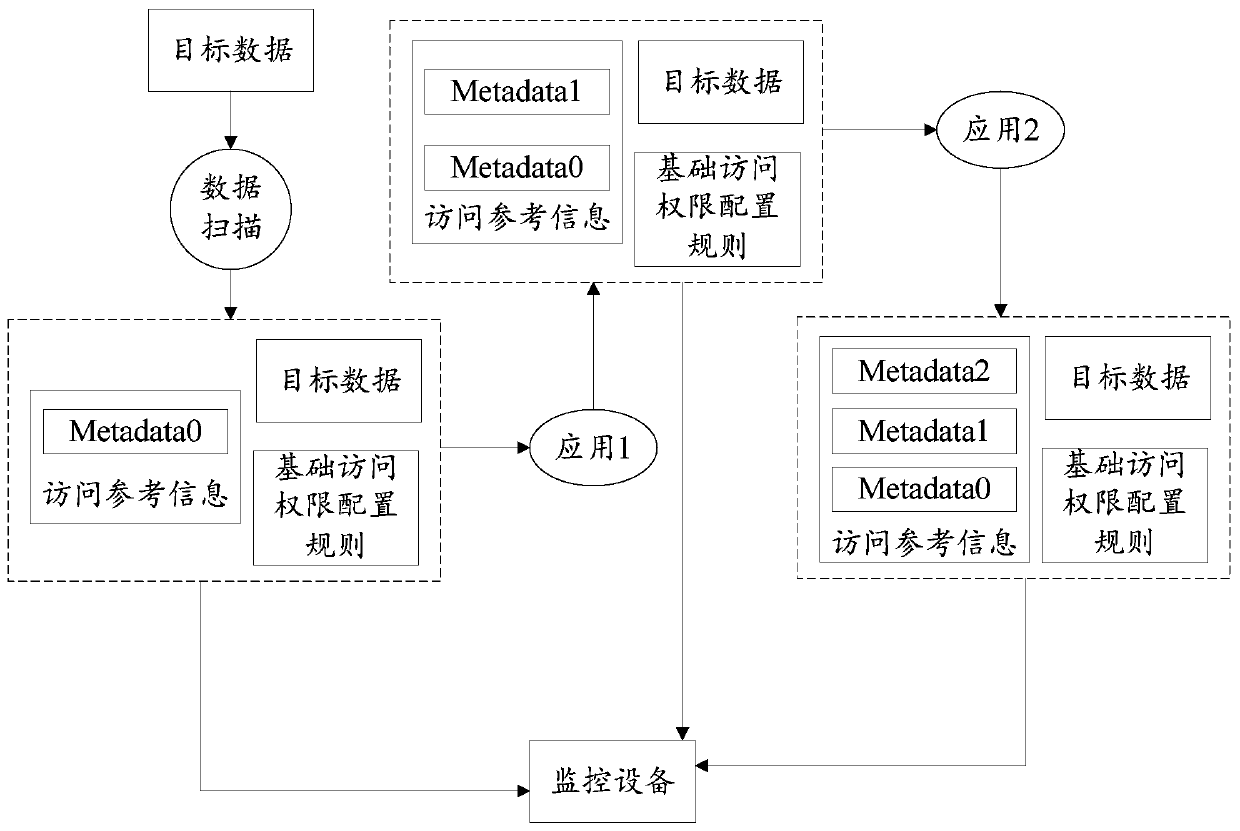
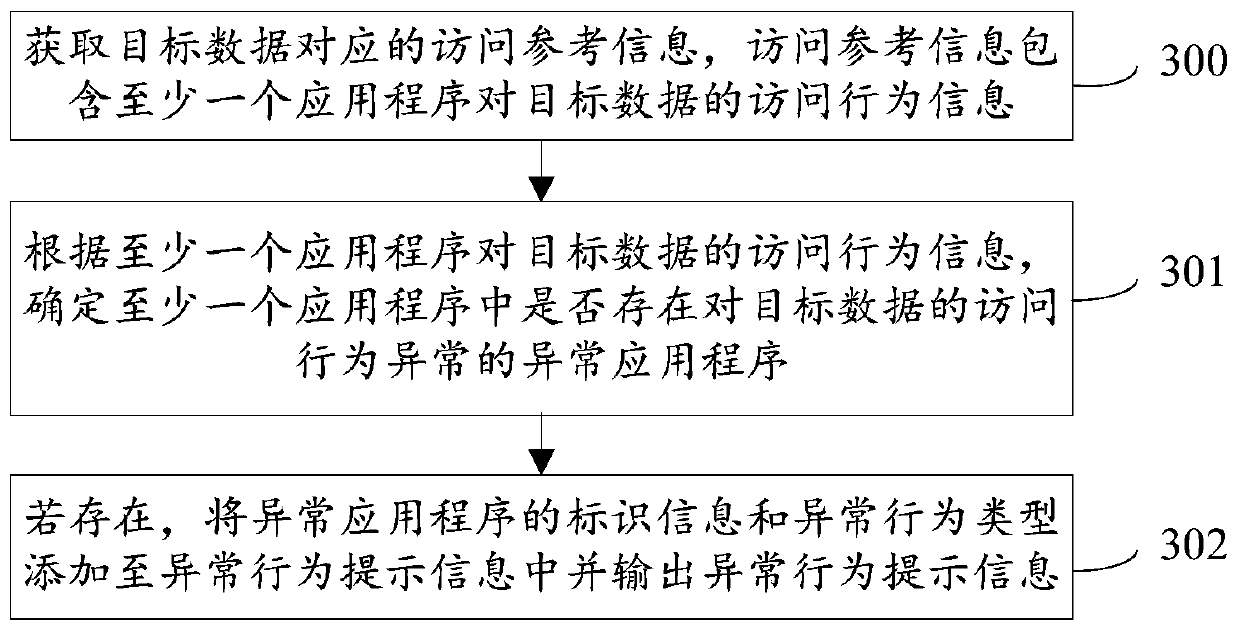
The embodiment of the invention provides an access control method, system and device, an access behavior recognition method, system and device, and a storage medium, and the access control method comprises the steps: receiving an authority obtaining request generated by a current application program when the current application program requests to access target data; obtaining access behavior information of at least one previous application program to the target data from the access reference information corresponding to the target data; adjusting the access permission of the current application program to the target data according to the access behavior information of the at least one previous application program to the target data; and controlling the access of the current application program to the target data according to the adjusted access permission. In the embodiment, when access control is carried out on the target data, data change details in a full link used by the target data are comprehensively considered, and the access permission of the application program can be dynamically adjusted according to the data change details, so that the access control on the target datais more reasonable and more flexible.
Owner:ALIBABA GRP HLDG LTD
Broadcast control authority control method
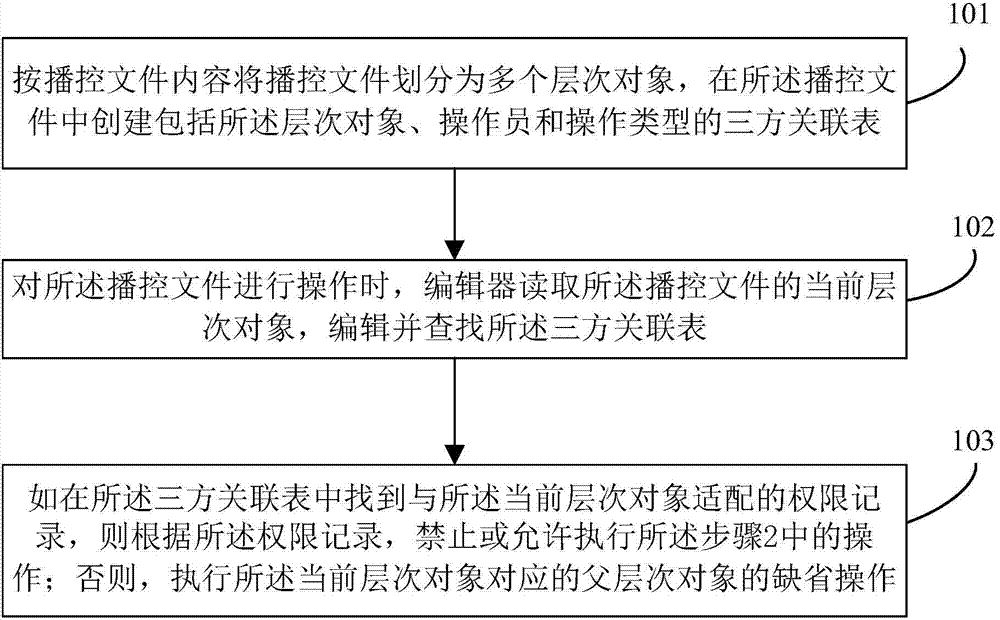
ActiveCN103702236AImprove control efficiencyConvenient access controlSelective content distributionAuthority controlUser group
The invention discloses a broadcast control authority control method, which belongs to the field of file management. The method has the principle that a broadcast control file content is divided into multiple level objects, and each level object has corresponding operation; three-way associated records of an operation, a level object and an operator are stored in a broadcast control file; when a playlist is edited, judgment is carried out according to the three-way associated records once the associated level objects or corresponding operations are met; if an authority record exists, an operation is passed or prohibited according to the authority record; if no authority record exists, the operation is carried out according to default authority of a parent hierarchy. Convenient, quick and flexible authority control can be realized by combining a user or a user group according to different file contents and structures, so that system demand can be further realized.
Owner:北京九华互联科技有限公司
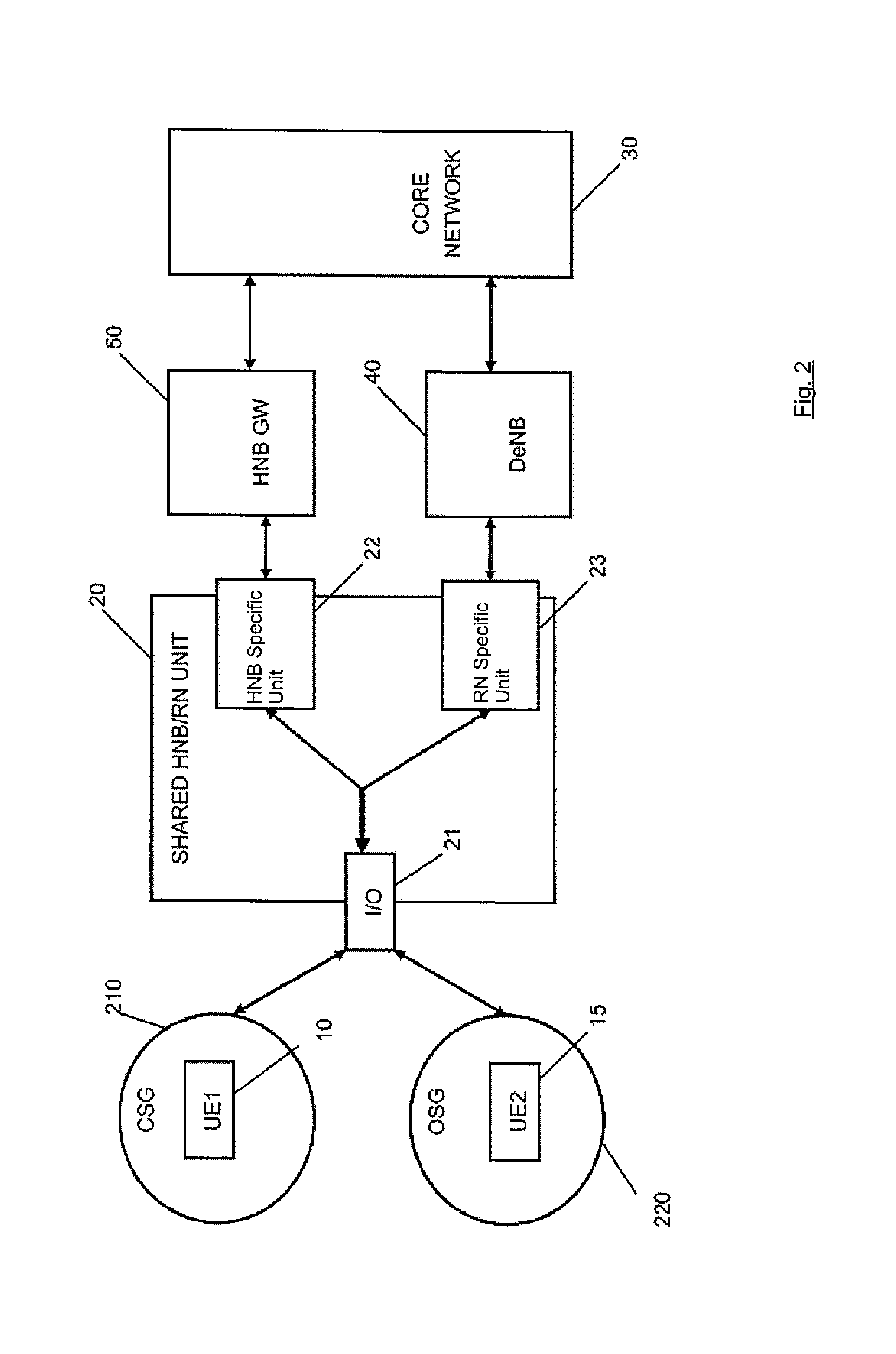
Methods and apparatus for supporting multiple types of connections to a core network
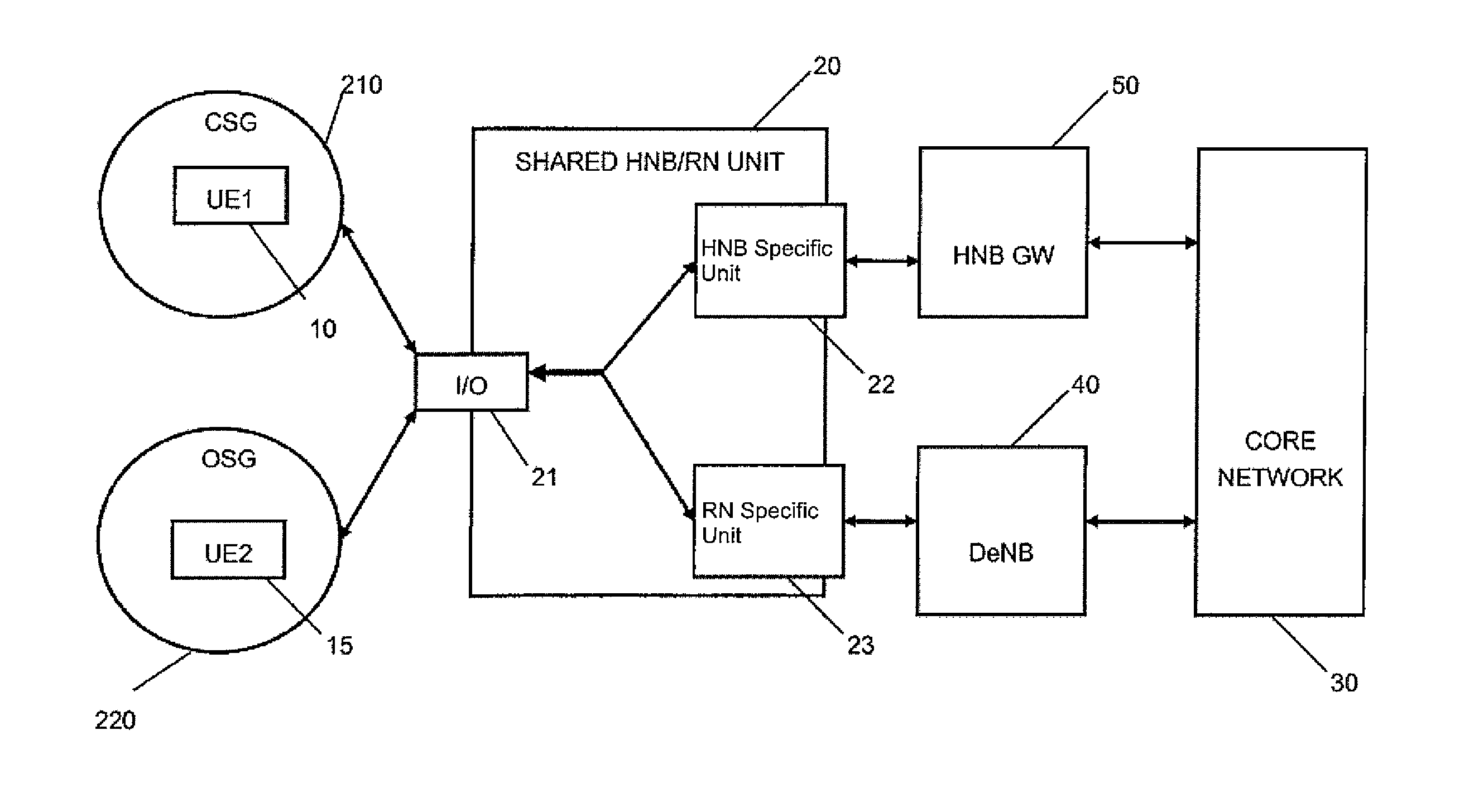
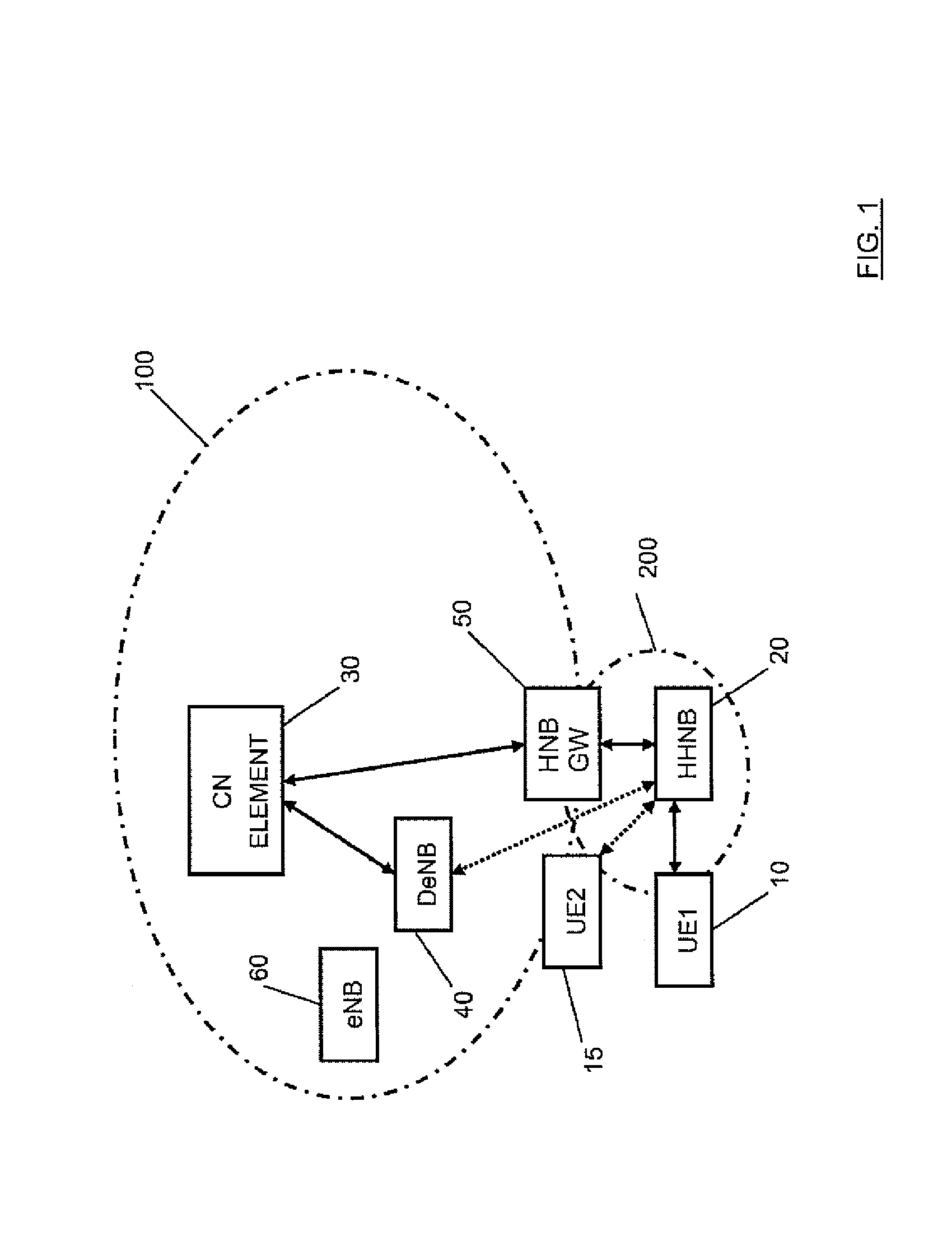
ActiveUS9113405B2Avoid problemsFlexible Access ControlAssess restrictionNetwork topologiesHome Node BGPRS core network
There is proposed a mechanism providing functions of a so-called hybrid home node B (HHNB) where subscribers, depending on their belonging to a specific subscriber group, such as a closed subscriber group or an open subscriber group, are admitted for a connection to the communication network via different connection routes and systems. After a request for connecting a subscriber is received, an identification process is performed whether the subscriber belongs to a first subscriber group (CSG) or to a second subscriber group (OSG). On the basis of this identification, the subscriber is assigned to a first connection route or a second connection route. It is then checked whether available resources on the assigned connection route are sufficient, wherein on the basis of this check the request for connecting is allowed or rejected.
Owner:WSOU INVESTMENTS LLC
Course selection system based on attribute passwords
PendingCN110599376ATo achieve the purpose of attribute combinationConvenient access controlData processing applicationsDatabase management systemsAccess structureManagement unit
The invention belongs to the technical field of teaching equipment, and particularly relates to a course selection system based on attribute passwords. The system comprises a login management unit, ateacher unit, a student unit and a teacher unit. The teacher unit comprises a course selection student viewing module and a course information modification module; the student unit comprises a courseinformation query module, a course selection module, a course quitting module and a personal repair and reading condition query module; the educator unit comprises a course management module, a student management module and a teacher management module; the login management unit is responsible for carrying out identity verification on students, teachers and administrators and carrying out corresponding function operations; according to the system, identity information of a user is described by using a group of attributes, an encryption party encrypts the information by using the same public keyand a specific access structure, and the information can be decrypted only when the user has an attribute combination meeting the requirements of the access structure; according to the system, the safety and privacy of course data can be guaranteed, and the time cost can be reduced.
Owner:FUDAN UNIV
Internet of Things private data segmentation encryption method and block chain system
PendingCN114500103AFlexible Access ControlGuaranteed privacy and securitySecuring communicationInstrumentsInternet privacyThe Internet
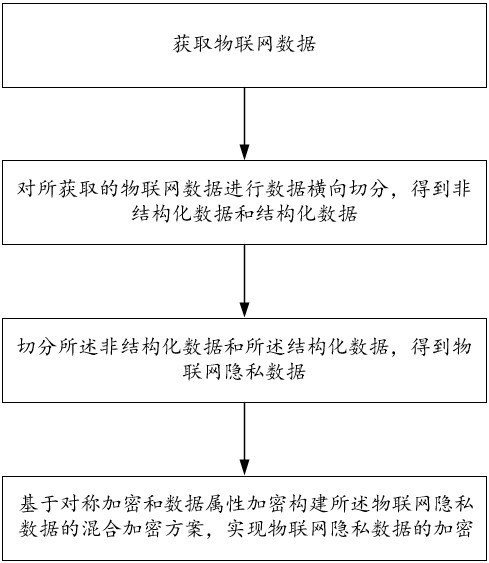
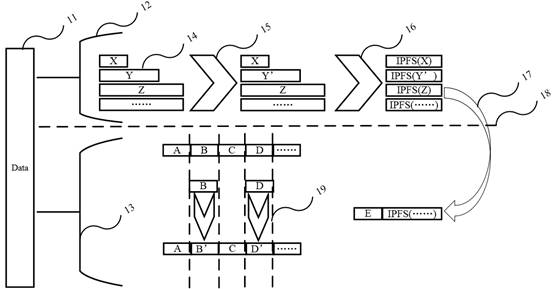
The invention belongs to the technical field of block chains, and particularly relates to an Internet of Things private data segmentation encryption method and a block chain system, and the method comprises the following steps: obtaining Internet of Things data; performing data transverse segmentation on the acquired Internet of Things data to obtain unstructured data and structured data; segmenting the unstructured data and the structured data to obtain privacy data of the Internet of Things; and constructing a hybrid encryption scheme of the Internet of Things private data based on symmetric encryption and data attribute encryption to realize encryption of the Internet of Things private data. Through cryptography, IPFS and block chain technologies, fine-grained and flexible access control of data of the Internet of Things is realized, privacy security of chained data on the Internet of Things is ensured, and it is ensured that data collected by the Internet of Things cannot be tampered and is secure and credible.
Owner:TAISHAN UNIV
Satellite network data permission control method and device and storage medium
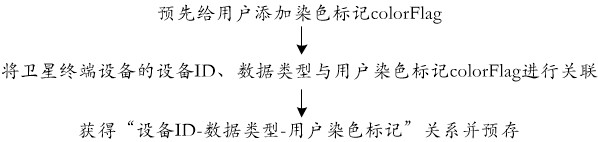
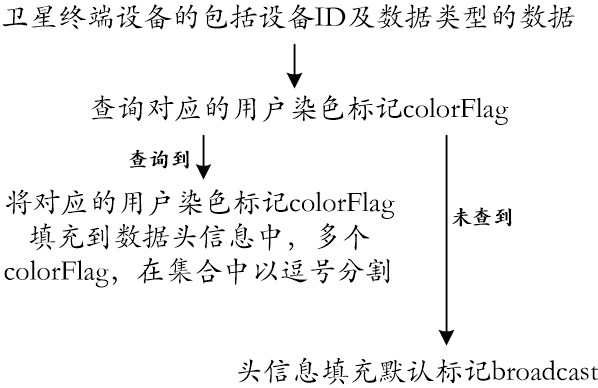
ActiveCN112532595AImprove real-time performanceFlexible handlingTransmissionData transmissionFrequency band
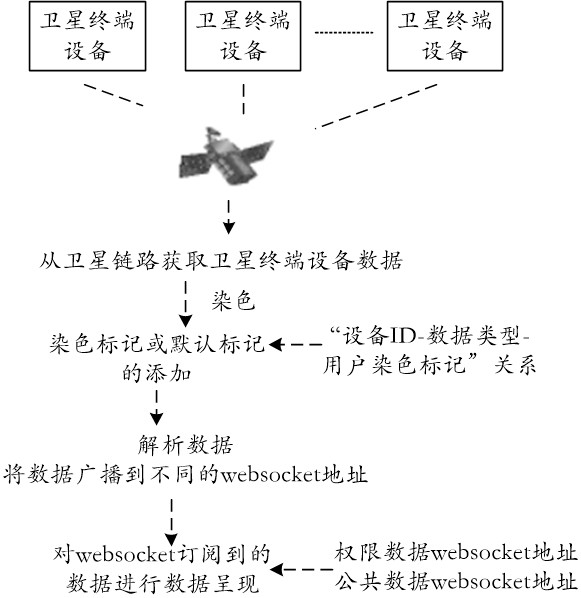
The invention discloses a method and a device for sharing and allocating frequency band resources among satellite communication equipment, and a storage medium, which use a websocket protocol, and comprise the following steps of: adding a corresponding dyeing mark or a default mark to data including an equipment ID (Identity) and a data type of satellite terminal equipment acquired from a satellite link according to an equipment IDdata type user dyeing mark relationship; wherein the two marks are permission marks and public marks; broadcasting the data to different websocket addresses according to the added dyeing marks or default marks; and showing data subscribed by websocket, wherein the websocket subscription refers to an authority data websocket address including an authority mark anda public data websocket address including a public mark which are dynamically subscribed after connection is established between a websocket server and a websocket client. The authority control withhigher real-time performance and more flexible processing mode is realized, and the confidentiality and security of satellite network data transmission are improved.
Owner:四川安迪科技实业有限公司
Application program access control method, device and system and medium
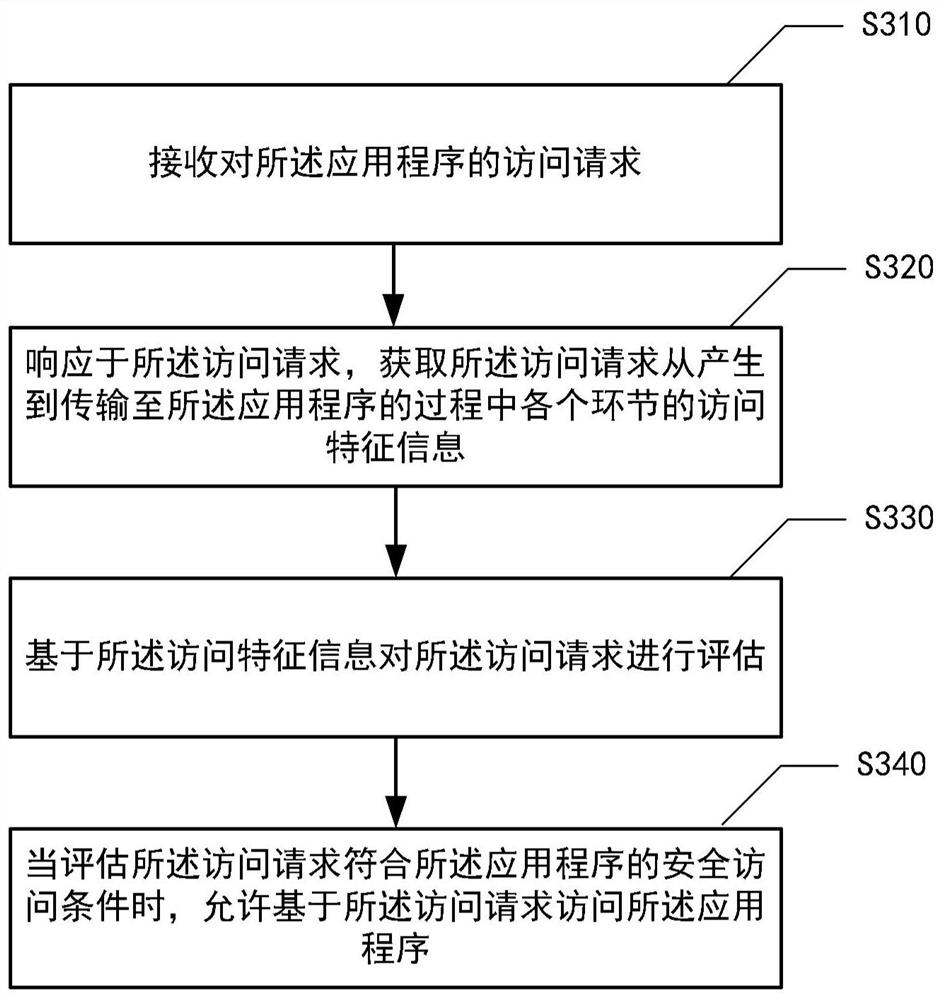
PendingCN112115484ASmall changesFlexible Access ControlPlatform integrity maintainanceDatabaseComputer engineering
The invention provides an application program access control method, device and system and a computer readable storage medium, and belongs to the technical field of information security. The method comprises the following steps of: receiving an access request for an application program; in response to the access request, obtaining access feature information of each link in a process from generation to transmission of the access request to the application program; evaluating the access request based on the access feature information; and under the condition that the access request meets the safety access condition of the application program, allowing the application program to be accessed based on the access request.
Owner:INDUSTRIAL AND COMMERCIAL BANK OF CHINA
A Method of User Authorization on Demand Supporting Least Privilege
Owner:NAT UNIV OF DEFENSE TECH
Dynamic multidimensional space access control method
ActiveCN109063508ARealize a formal descriptionFlexible Access ControlDigital data protectionFirst-order logicRole-based access control
The invention provides a dynamic multi-dimensional space access control method. The dynamic multi-dimensional space access control method comprises the following steps: 1, constructing a static multi-dimensional space access control model based on role access control, wherein that static multi-dimensional space access control model is a three-tuple< P, Dm, Dc>;, wherein P is a set of decision in access control, Dm is a multi-dimensional space set of subject, object and influence factors, and Dc is a result of access control decision; 2, constructing a dynamic multi-dimensional space access control model based on that static multi-dimensional space access control model, The dynamic multi-dimensional space access control model is used to describe the delegation, distribution and reclamationof rights under the dynamic access control policy by adding a first-order logic M to the static multi-dimensional space access control model and acting on the dynamic access control policy.
Owner:ARMY ENG UNIV OF PLA
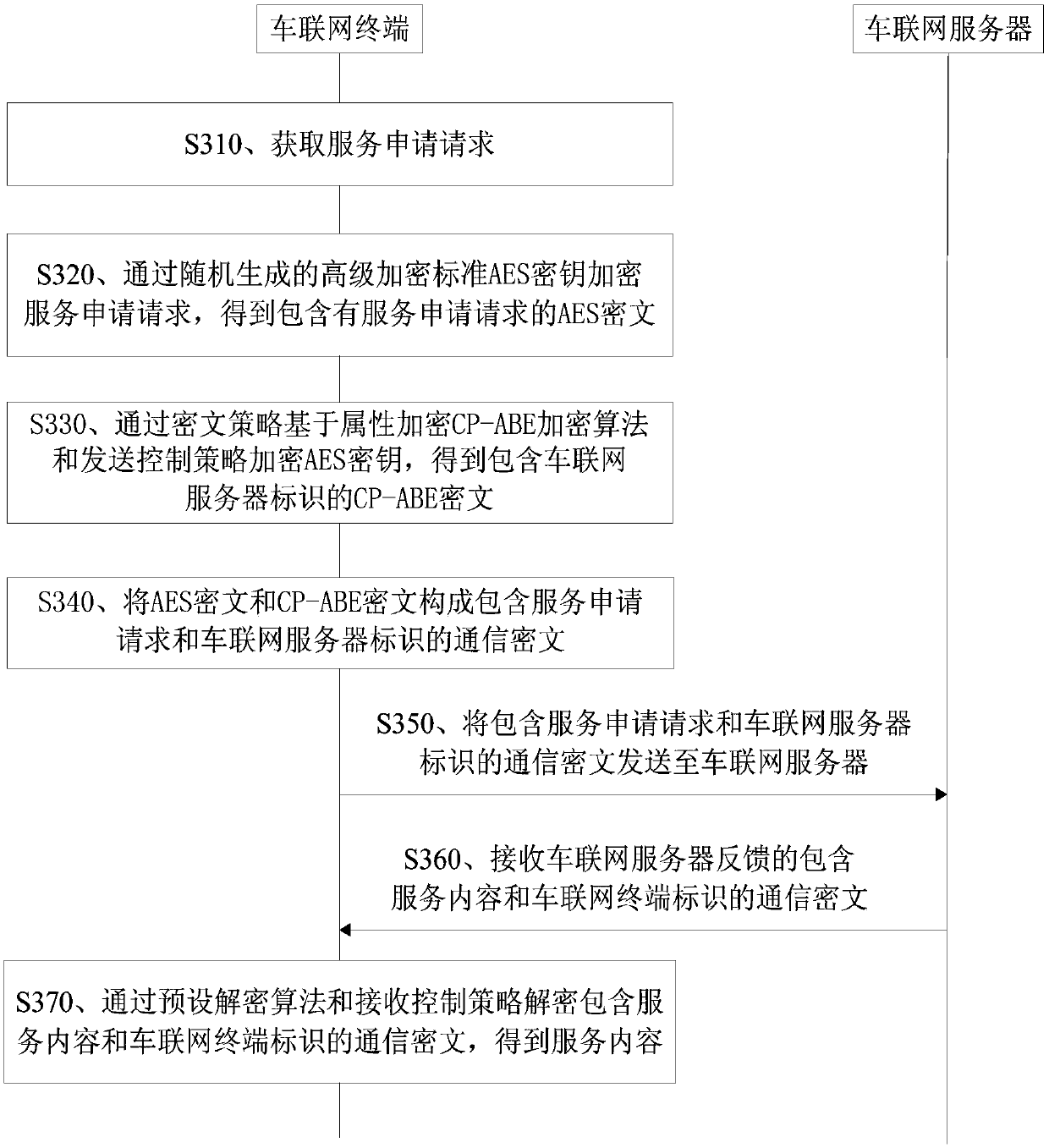
A service request method and device for Internet of Vehicles
ActiveCN109543439BFlexible Access ControlGuaranteed confidentialityDigital data protectionCiphertextConfidentiality
The invention discloses a service request method and device for Internet of Vehicles. The method includes: obtaining a service application request, the service application request including vehicle information and service type; encrypting the service application request by encrypting the CP-ABE encryption algorithm based on the attribute of the ciphertext policy and sending the control strategy, and obtaining the service application request and the Internet of Vehicles The communication ciphertext of the server identification; send the communication ciphertext including the service application request and the IoV server identification to the IOV server; receive the communication ciphertext including the service content and the IOV terminal identification fed back by the IoV server; decrypt by preset The algorithm and receiving control strategy decrypt the communication ciphertext containing the service content and the IOV terminal identification to obtain the service content. The invention realizes the flexible access control to the IoV terminal and the IOV server while ensuring data confidentiality.
Owner:RUN TECH CO LTD BEIJING
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com